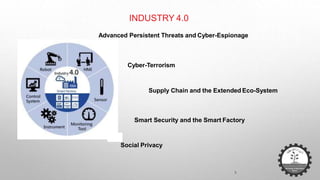
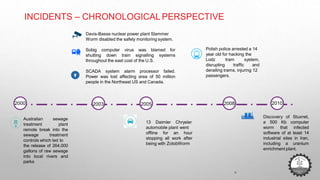
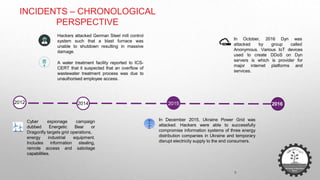
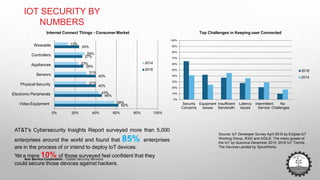
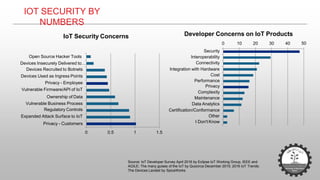
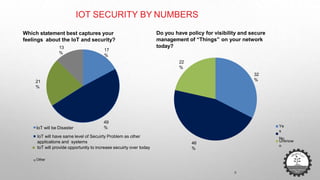
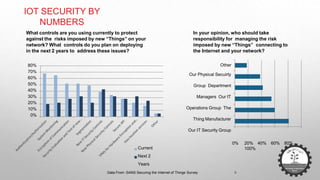
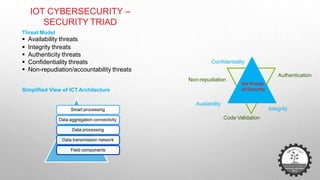
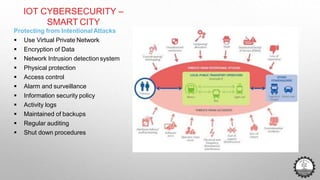
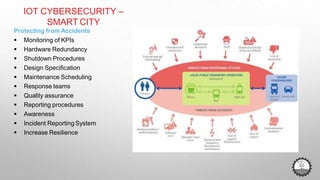
The document discusses cybersecurity challenges related to IoT. It outlines several security incidents involving IoT devices over time. It then discusses inherent security challenges for IoT, including threats from advanced persistent threats, cyber terrorism, and compromised supply chains. The document also summarizes statistics on IoT security concerns and vulnerabilities. It identifies top vulnerabilities according to OWASP and discusses how to secure IoT in different domains like smart cities and homes.