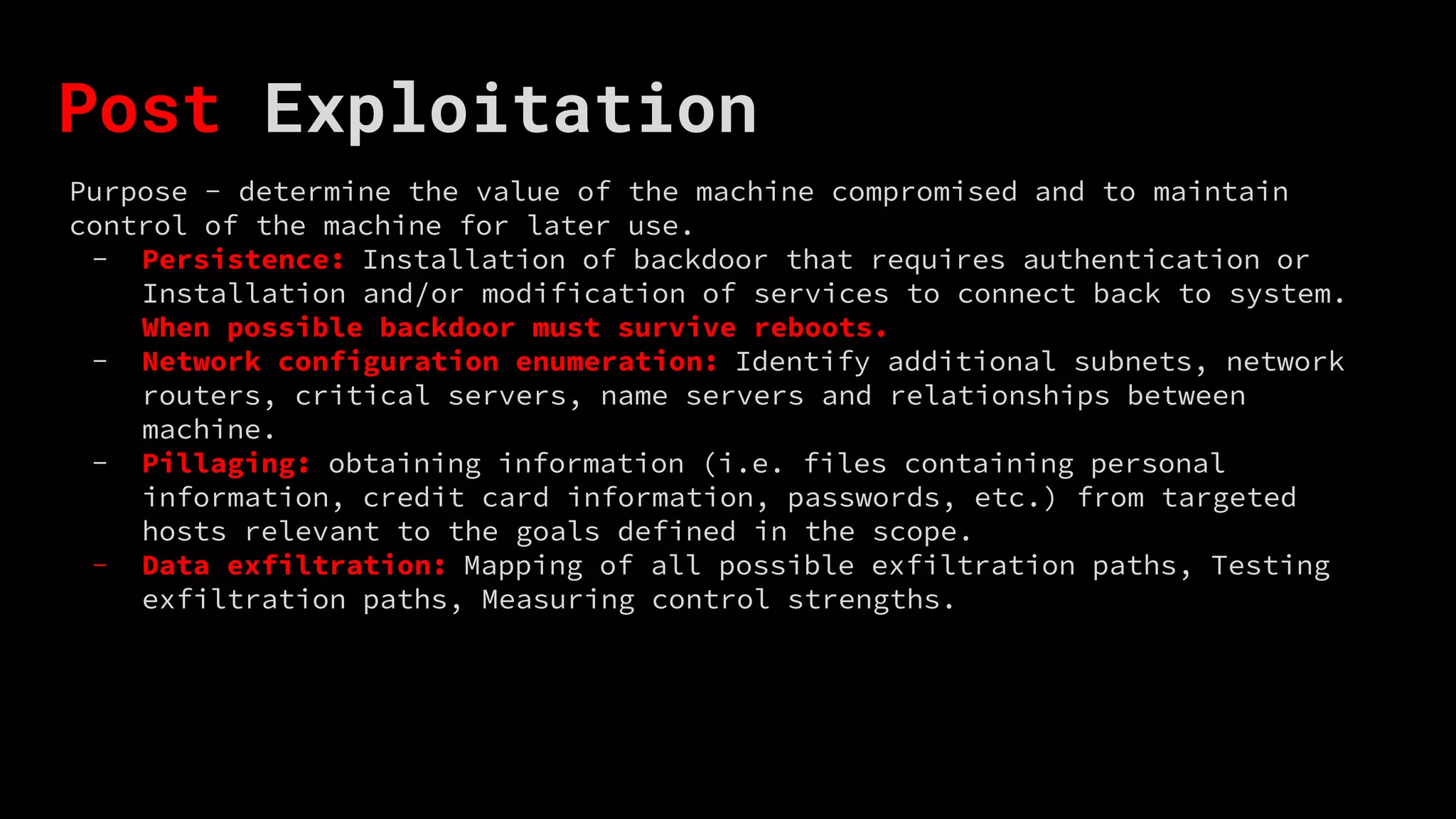
The document outlines the five main steps of a penetration test: information gathering, vulnerability analysis, exploitation, post-exploitation, and reporting. It describes some key activities for each step such as performing reconnaissance, discovering flaws, establishing access by bypassing security, maintaining control of compromised machines, and mapping exfiltration paths. It also discusses how capture the flag (CTF) exercises can help people start learning about these topics and steps of a penetration test.