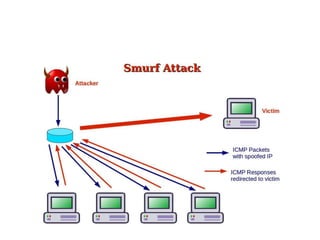
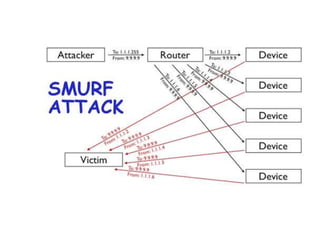
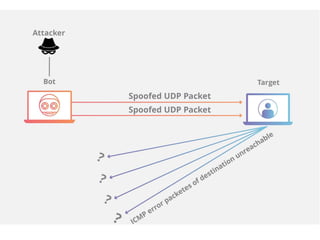
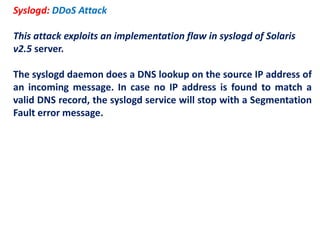
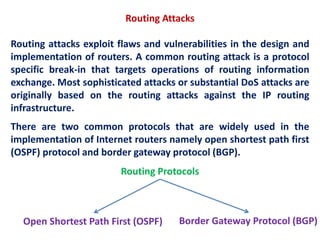
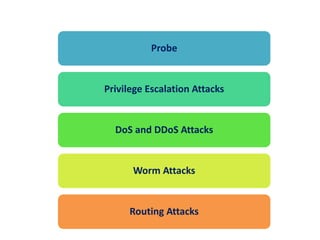
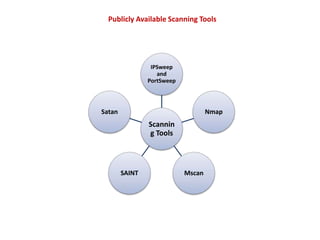
1. Network probes scan computer networks to gather information about services and vulnerabilities which can enable future attacks.
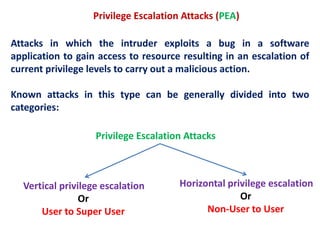
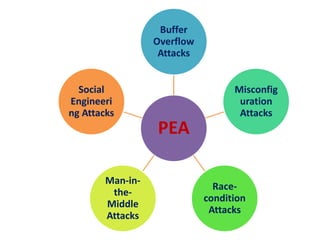
2. Privilege escalation attacks exploit software bugs to gain higher levels of access on a system, such as ordinary users accessing root privileges.
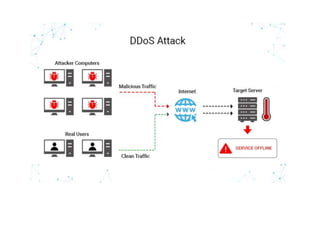
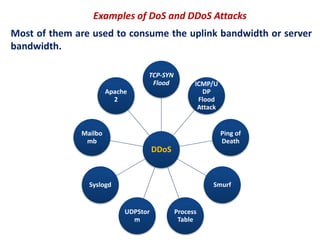
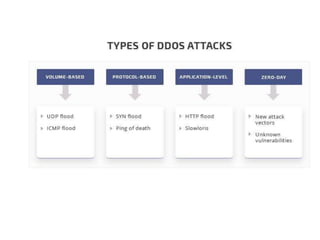
3. Denial of service (DoS) and distributed denial of service (DDoS) attacks aim to overwhelm network or system resources to interfere with normal operations.






















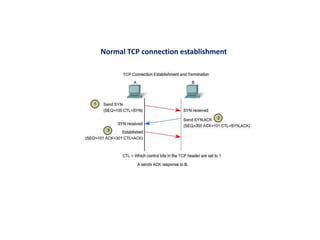
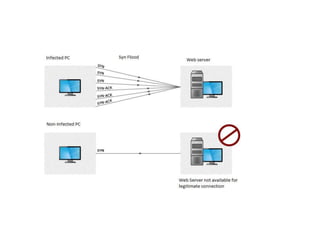
![• SYN Flood attack generates a large number of half-open TCP
connections to fill up the TCP control blockin order to exhaust the
available resources.
• As such, the target host becomes unable to accept any more
incoming TCP connections.
• This creates a denial of service for legitimate requests.
• Some existing tools that can execute TCP-SYN flood attacks include
Phatbot/Agobot, TFN2K, Stacheldraht, Trinity, TFN and Shaft [8].
TCP-ACK flood attack
An attacker sends one SYN and multiple ACKs with a spoofed source IP address to overload
the server.
This attack can be simply filtered by a SPI firewall since the flooding packets do not belong
to an established TCP connection.
An example of existing tools to execute TCP-ACK flood attack is Mstream .](https://image.slidesharecdn.com/ids009networkattacks-210728100208/85/Ids-009-network-attacks-32-320.jpg)