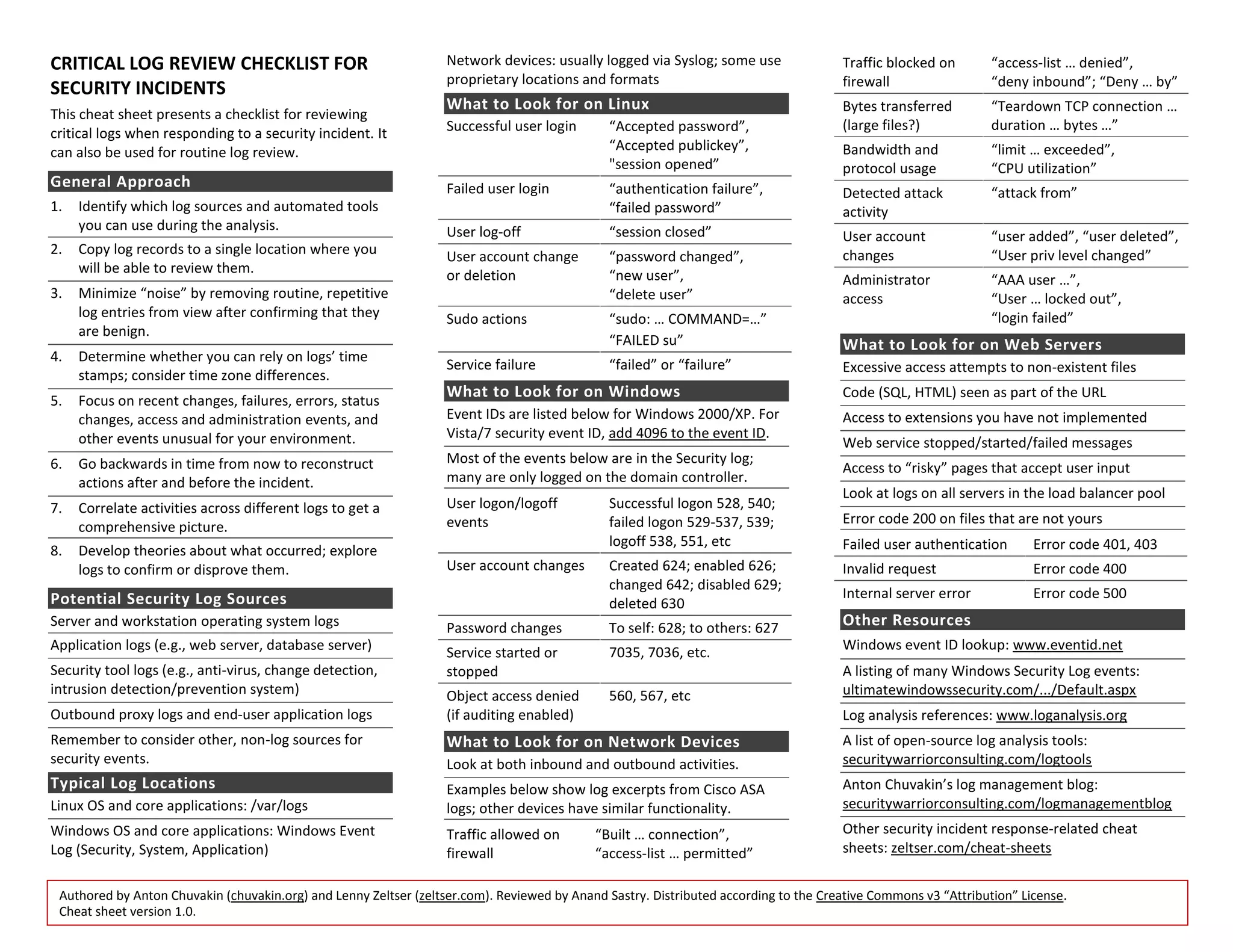
This document is a cheat sheet designed for reviewing critical logs during security incidents, outlining a systematic approach to log analysis. It details various log sources and provides specific log entries to look for across different operating systems and network devices. Additionally, it includes references for further log analysis resources and tools.