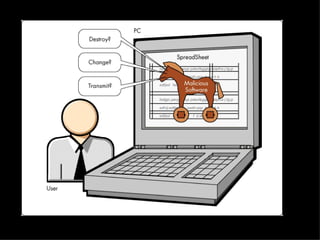
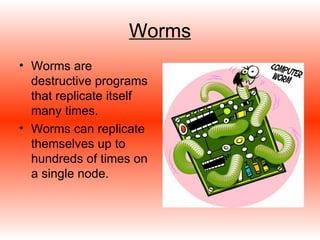
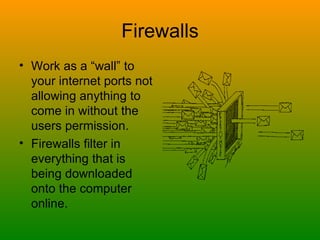
Trojans, worms, spyware, and adware are types of malicious programs that can harm computers. Trojans masquerade as beneficial programs but secretly install harmful code. Worms self-replicate rapidly and consume computer resources. Spyware and adware secretly install to track users' activities and display unwanted ads. These programs are often spread through rogue websites, email attachments, and peer-to-peer file sharing. People can protect themselves using virus scanners, firewalls, and antivirus programs to detect and remove malicious software and prevent intrusions. Norton and AVG are popular choices for antivirus software.