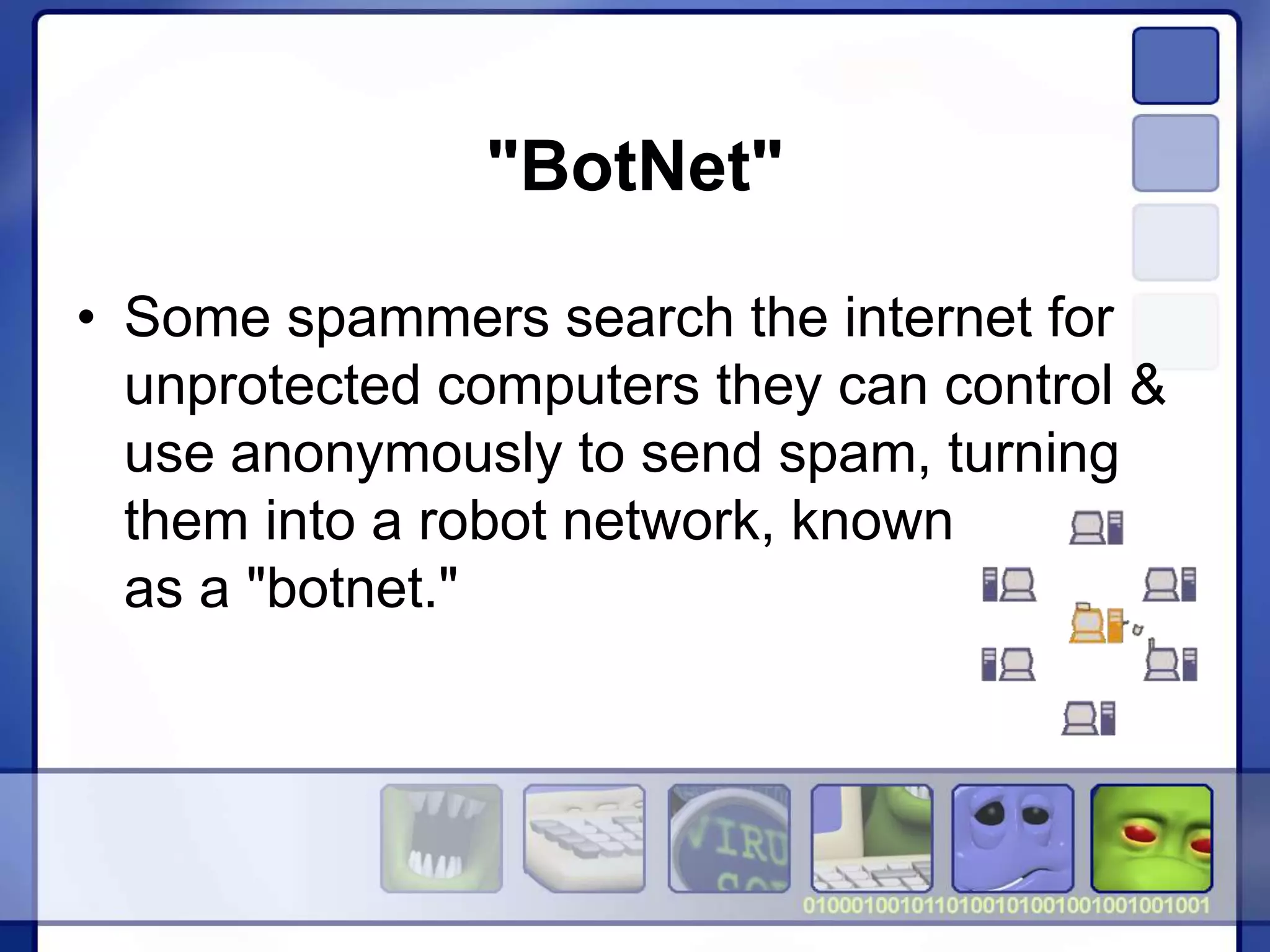
This document provides information and best practices for staying safe online. It discusses avoiding common scams like phishing, identity theft, file sharing risks, and using strong passwords. The key recommendations are to use up-to-date security software like antivirus and firewalls, only share information with known entities, and be wary of unsolicited messages asking for personal details. Backing up files and knowing how to respond if malware is suspected are also advised. The overall message is to be cautious online and protect personal information.