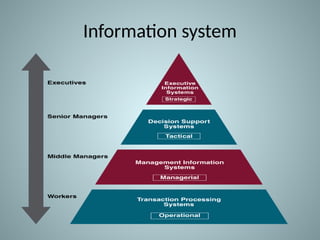
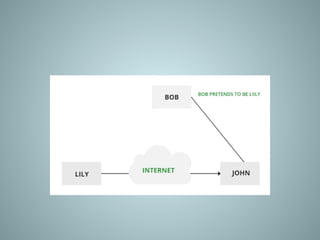
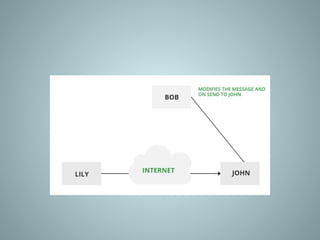
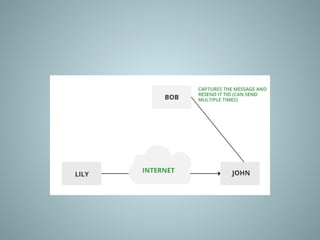
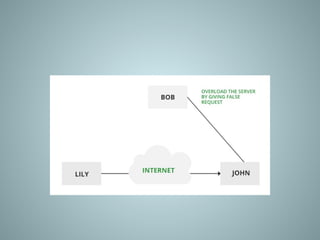
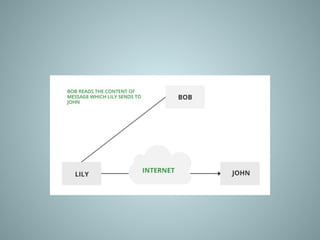
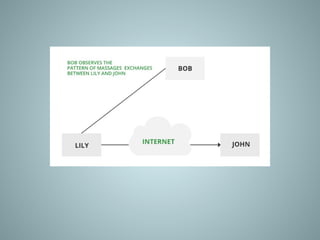
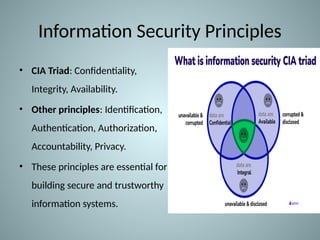
The document provides an overview of information system security, covering essential concepts such as threats, vulnerabilities, risks, and mitigation strategies. It emphasizes the importance of safeguarding data confidentiality, integrity, and availability while detailing various types of attacks, including active and passive methods. Additionally, it outlines the risk assessment process, security principles, and best practices for maintaining secure information systems.