1. Introduction
2. Activities of SDLC
• Preliminary Investigation
(Request Clarification, Feasibility Study, Request Approval)
• Determination of System Requirements
• Design of system
• Development of Software
• System Testing (Unit Testing, Integration testing, System Testing)
• System Implementation & Evaluation
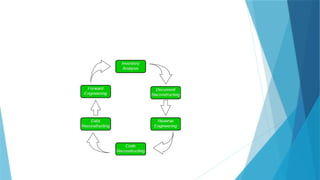
• System Maintenance
o Definition and types
o Software Reengineering
o Reverse Engineering
o Restructuring and forward Engineering