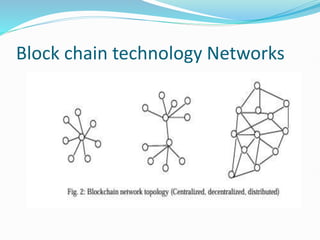
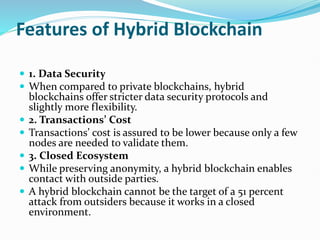
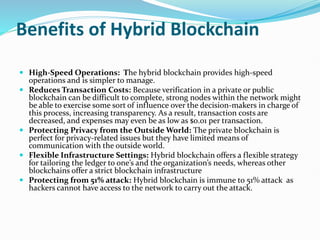
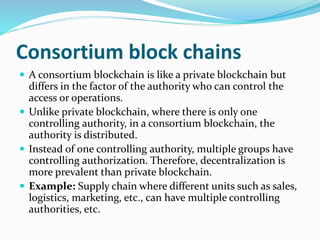
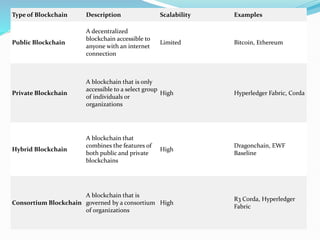
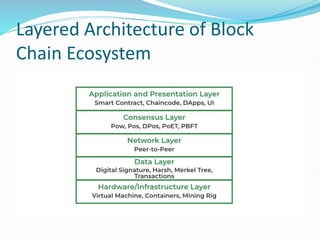
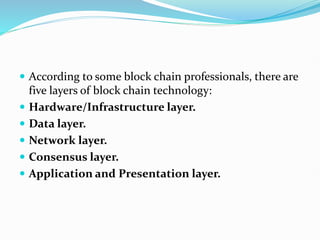
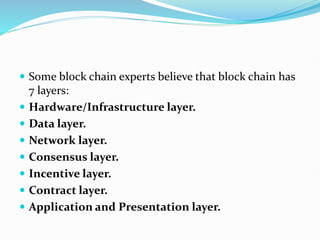
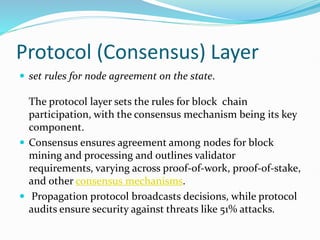
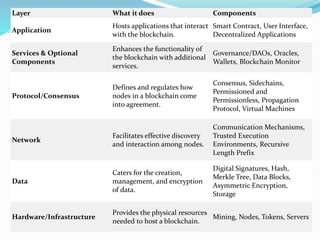
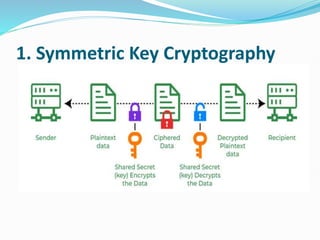
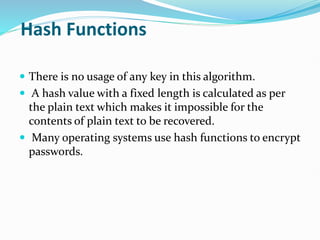
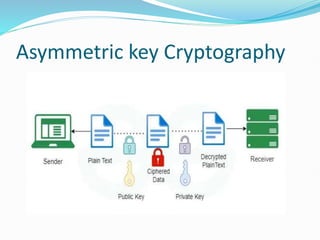
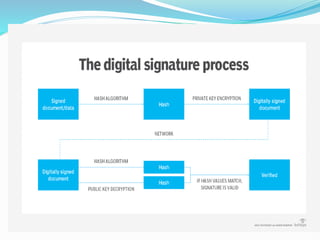
The document provides an overview of blockchain technology, discussing the various types of blockchain networks, including public, private, and hybrid models, their characteristics, advantages, and disadvantages. It elaborates on the layered architecture of the blockchain ecosystem, highlighting components such as consensus mechanisms, data storage, and application layers. Additionally, it explores the implications of decentralization, security, and scalability in different blockchain environments, along with the concept of consortium blockchains and their governance structures.