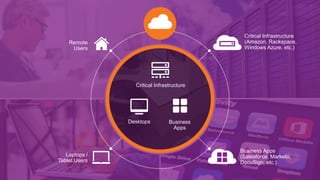
The document discusses the evolution of cloud security architecture, highlighting key threats such as data breaches, account hijacking, and denial of service attacks. It emphasizes the importance of visibility, encryption, and proactive management of cloud applications and vendors to mitigate these risks. Additionally, it suggests actionable steps for organizations to enhance their cloud security posture and integrate it with existing internal workflows.