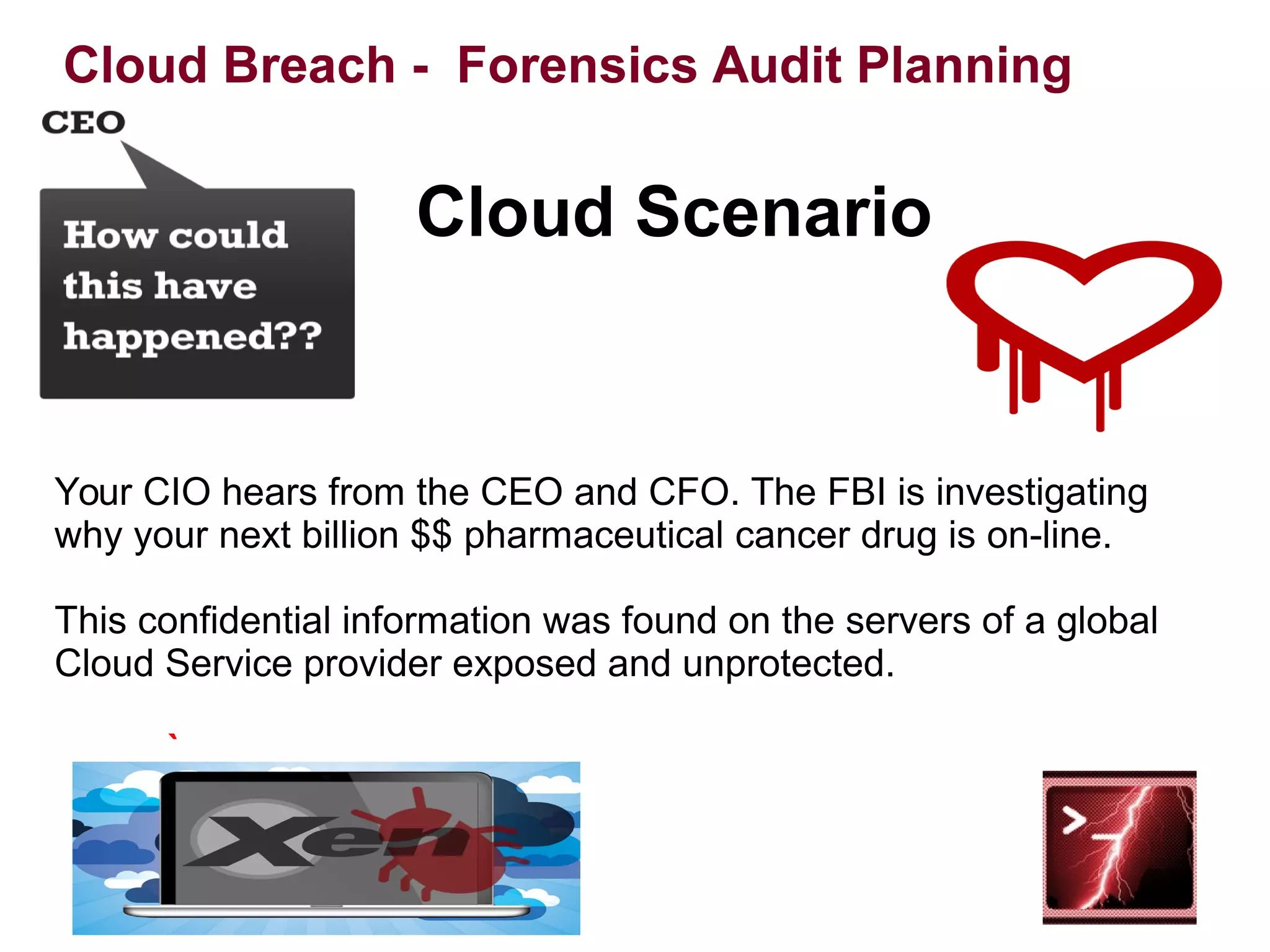
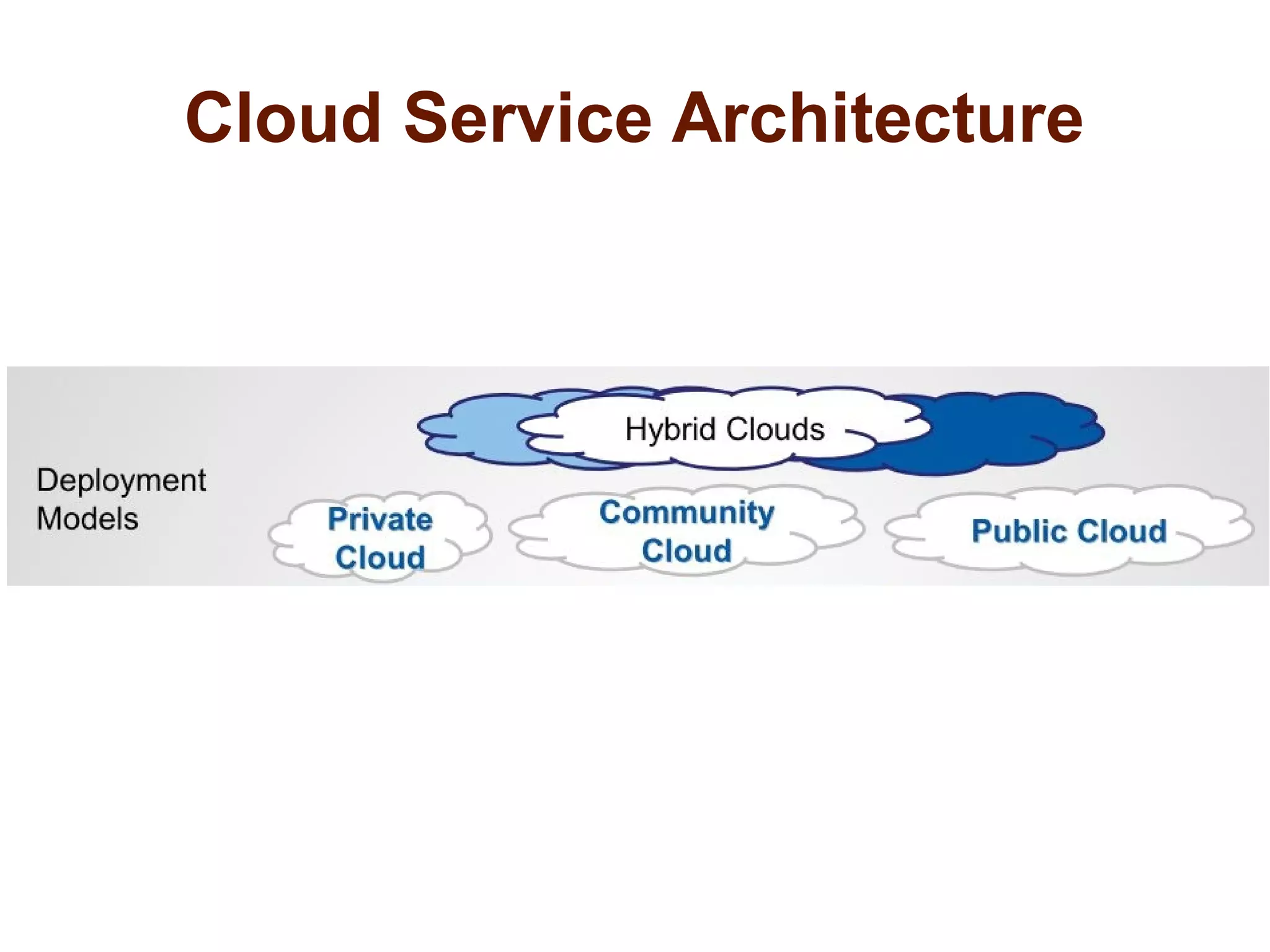
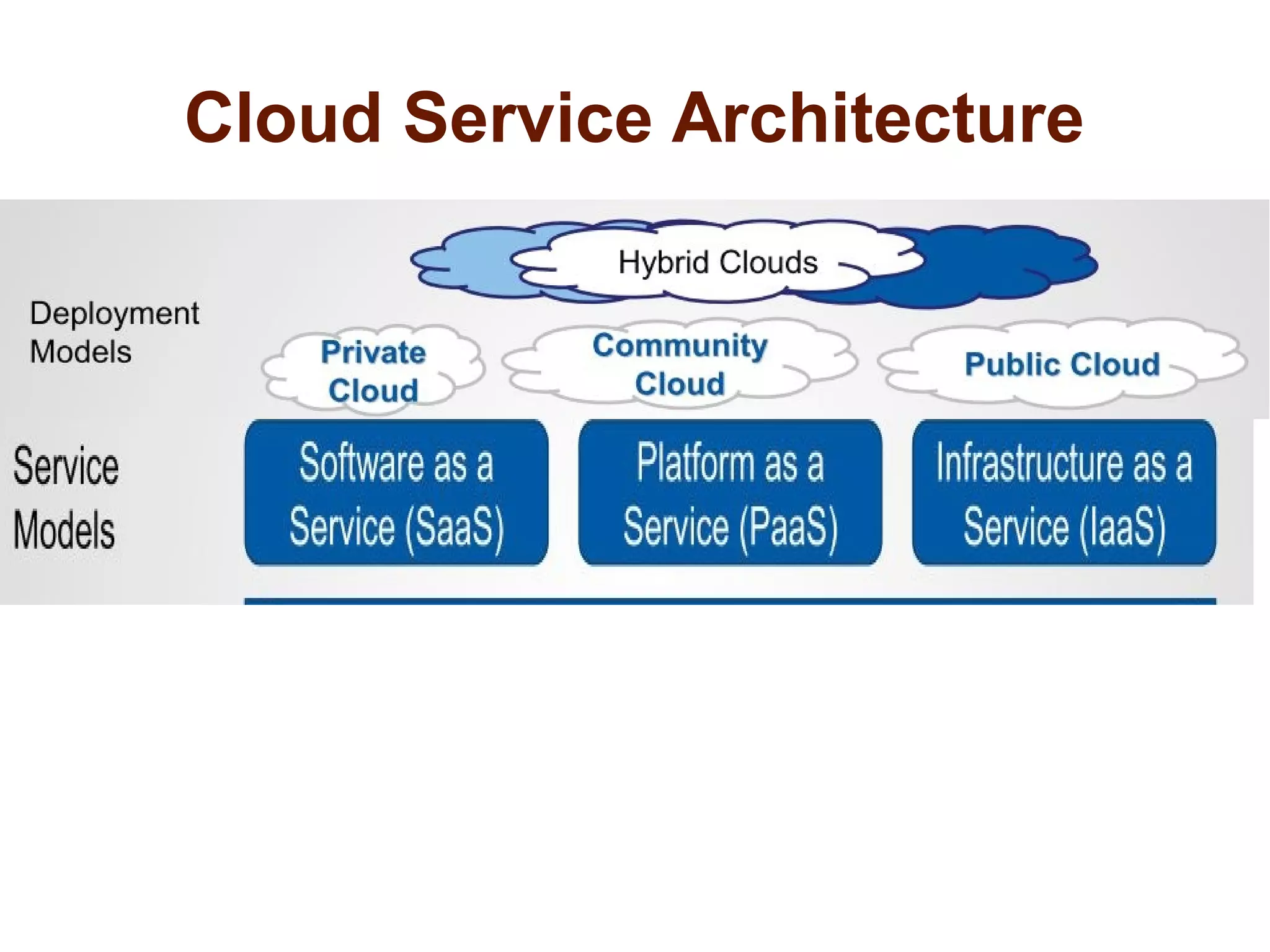
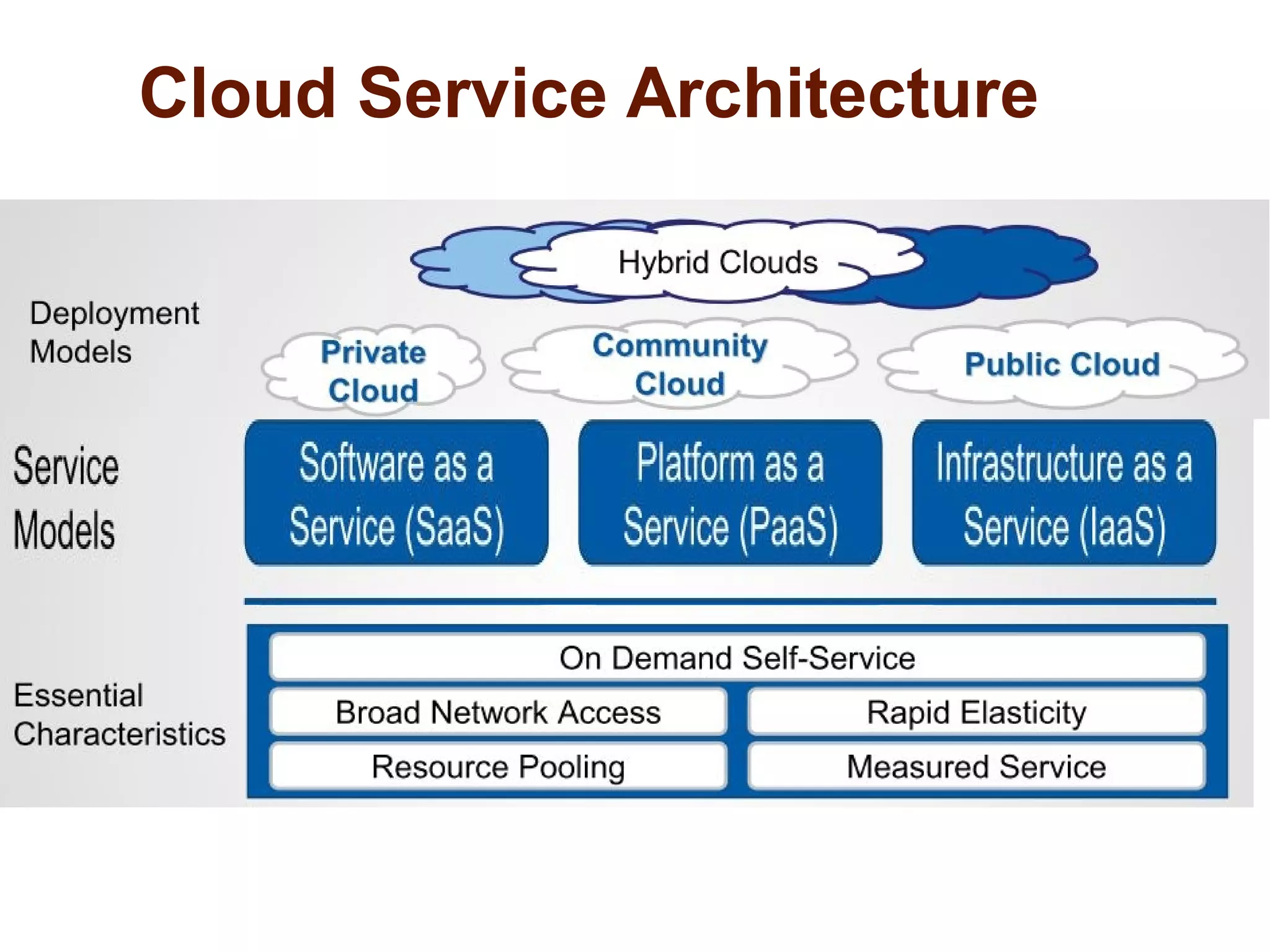
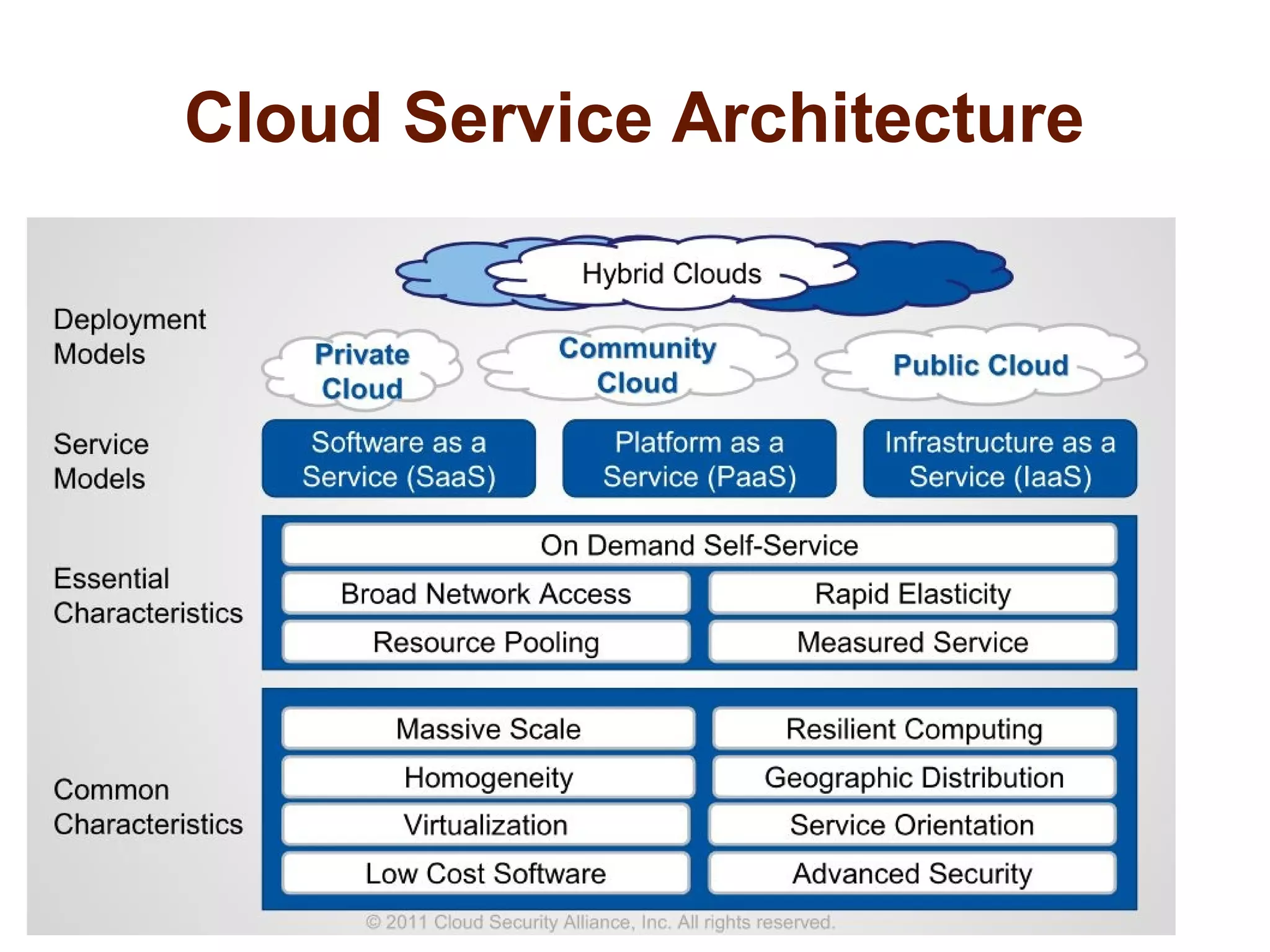
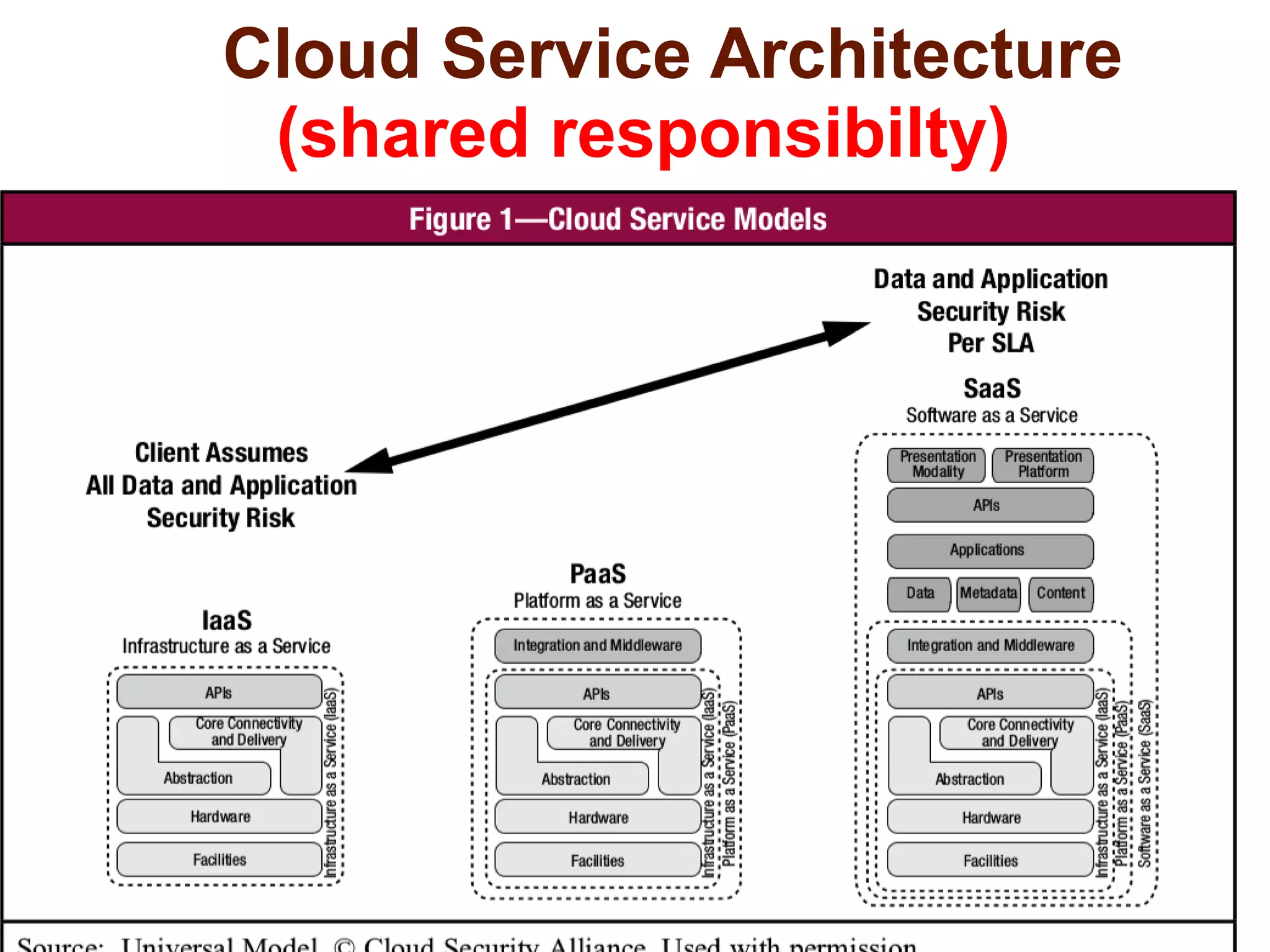
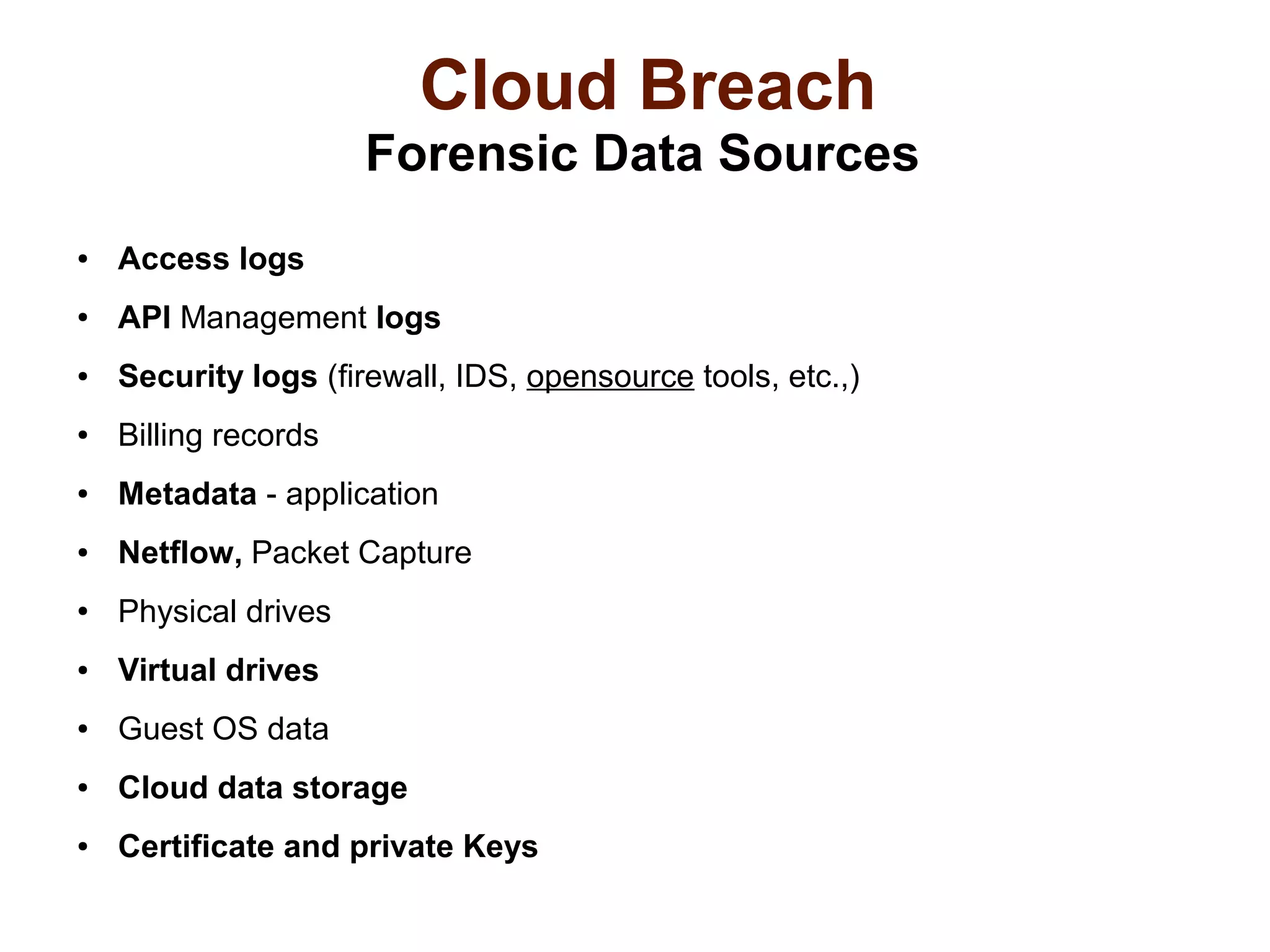
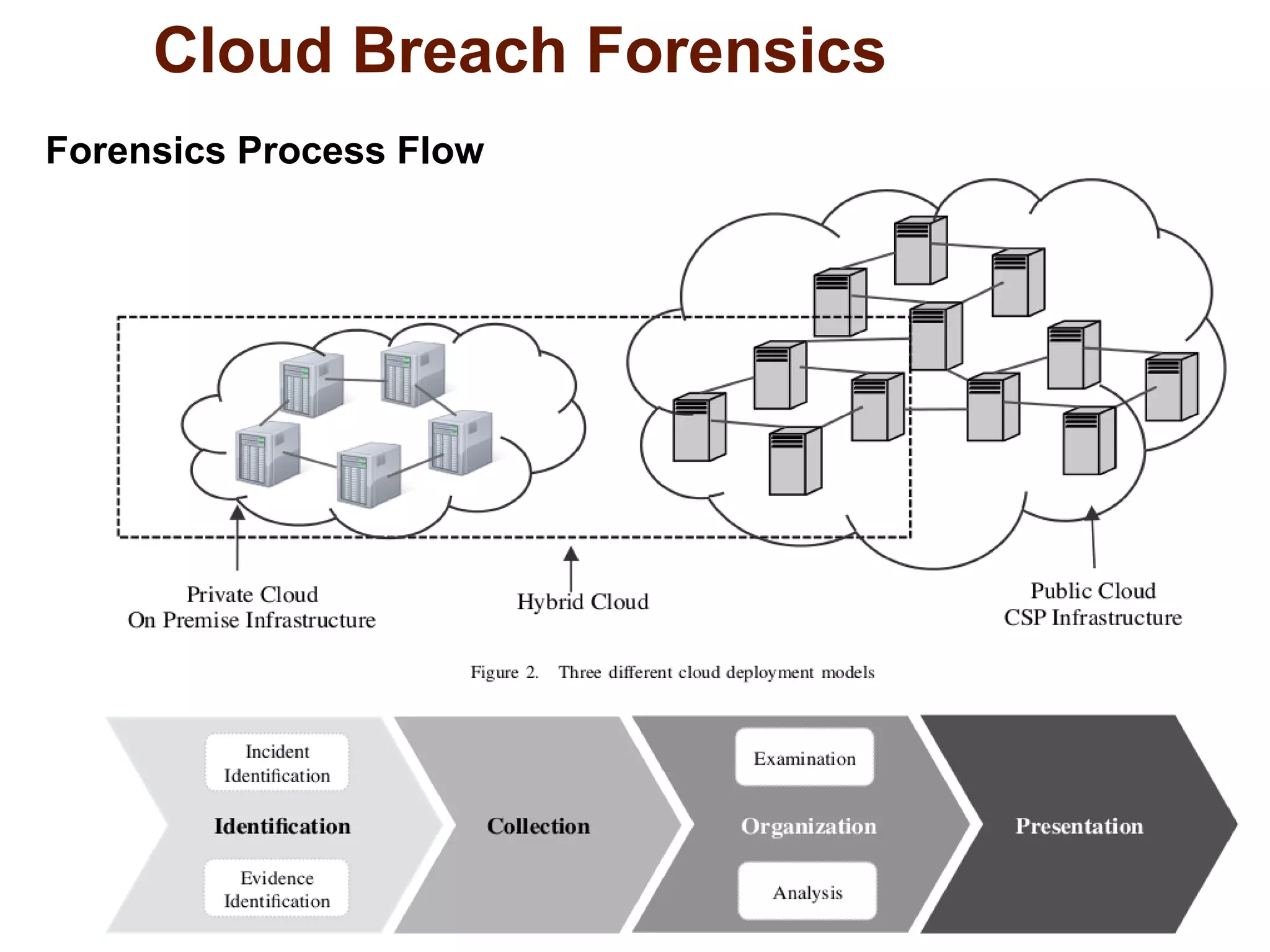
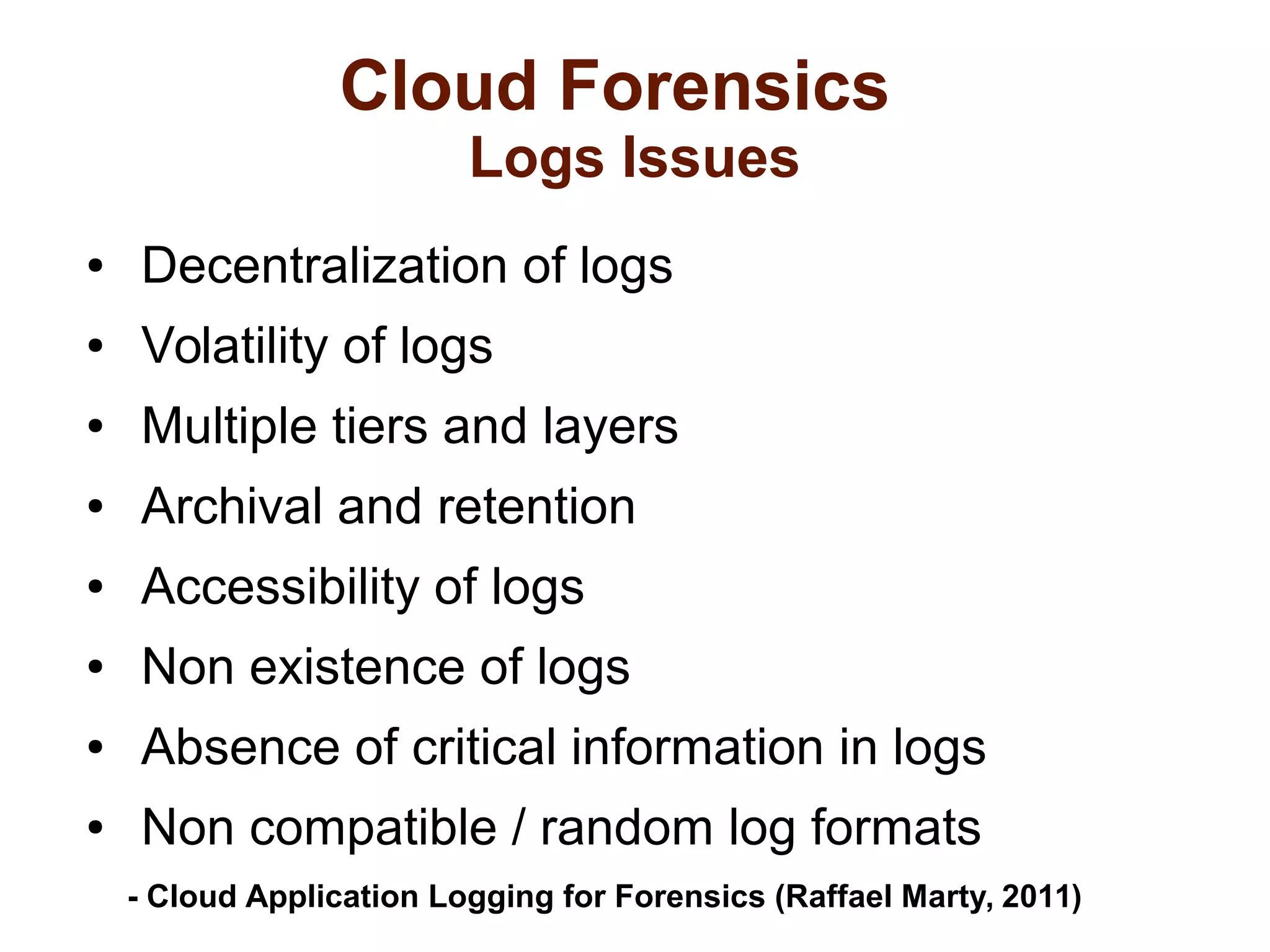
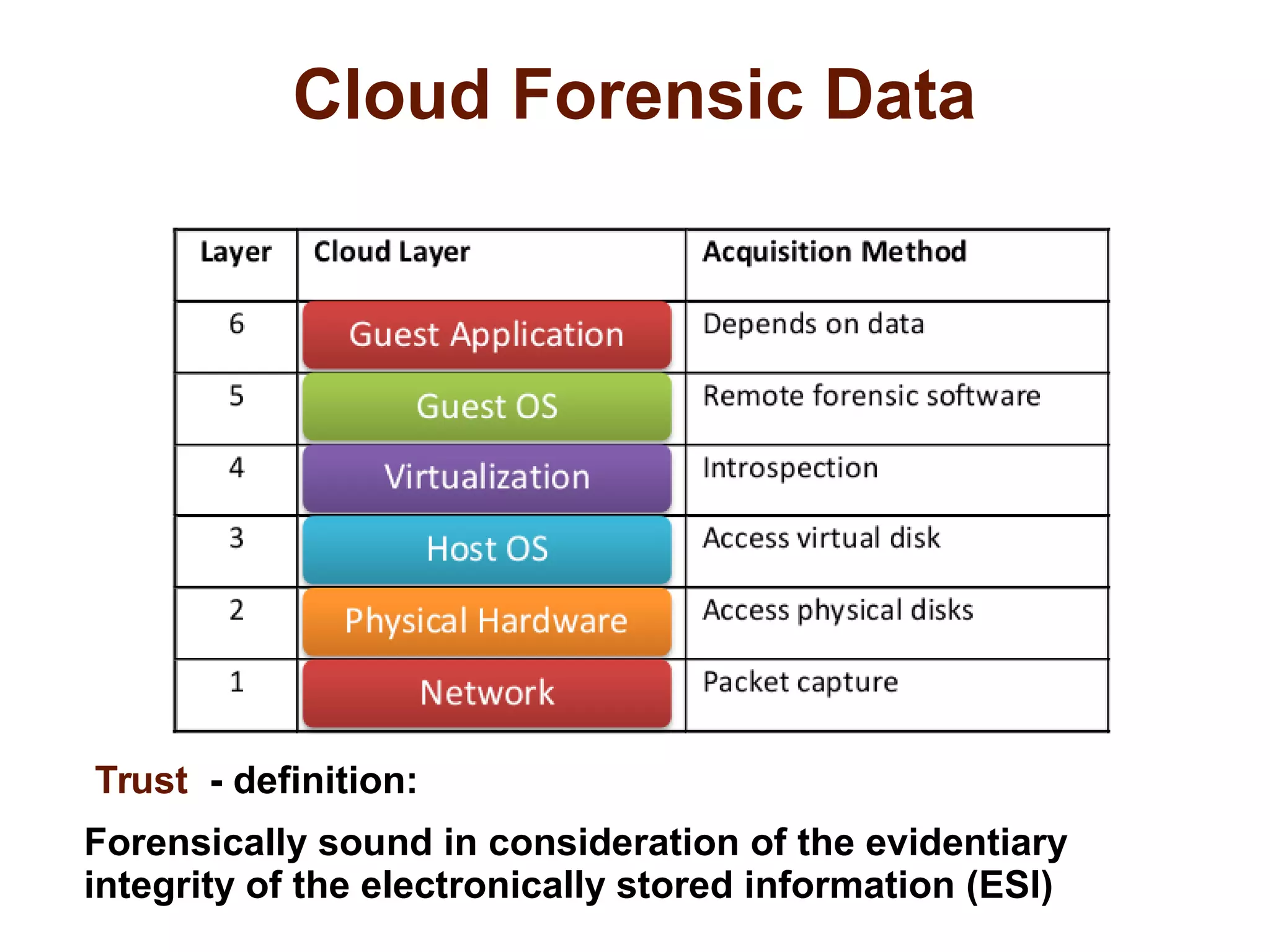
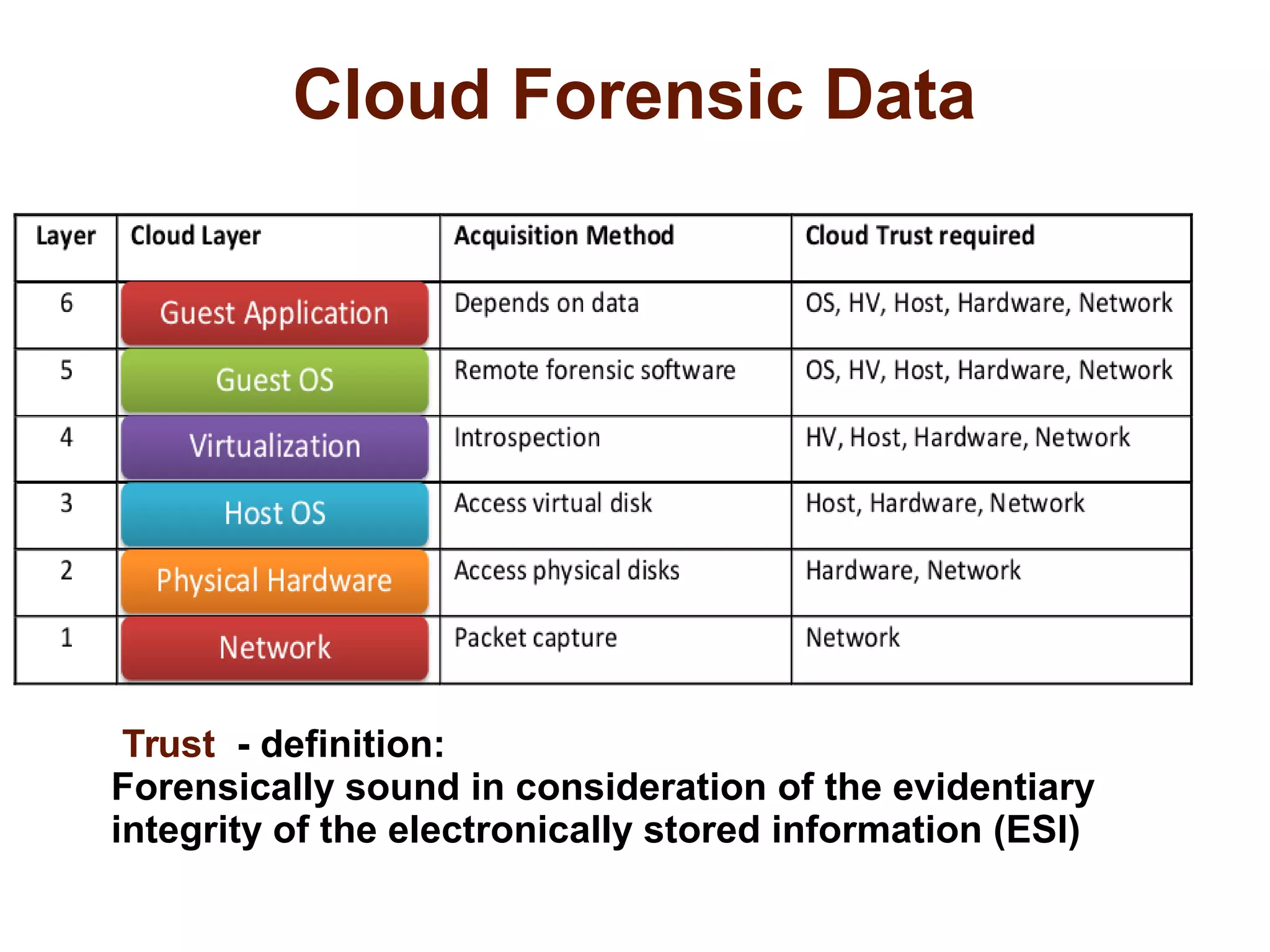
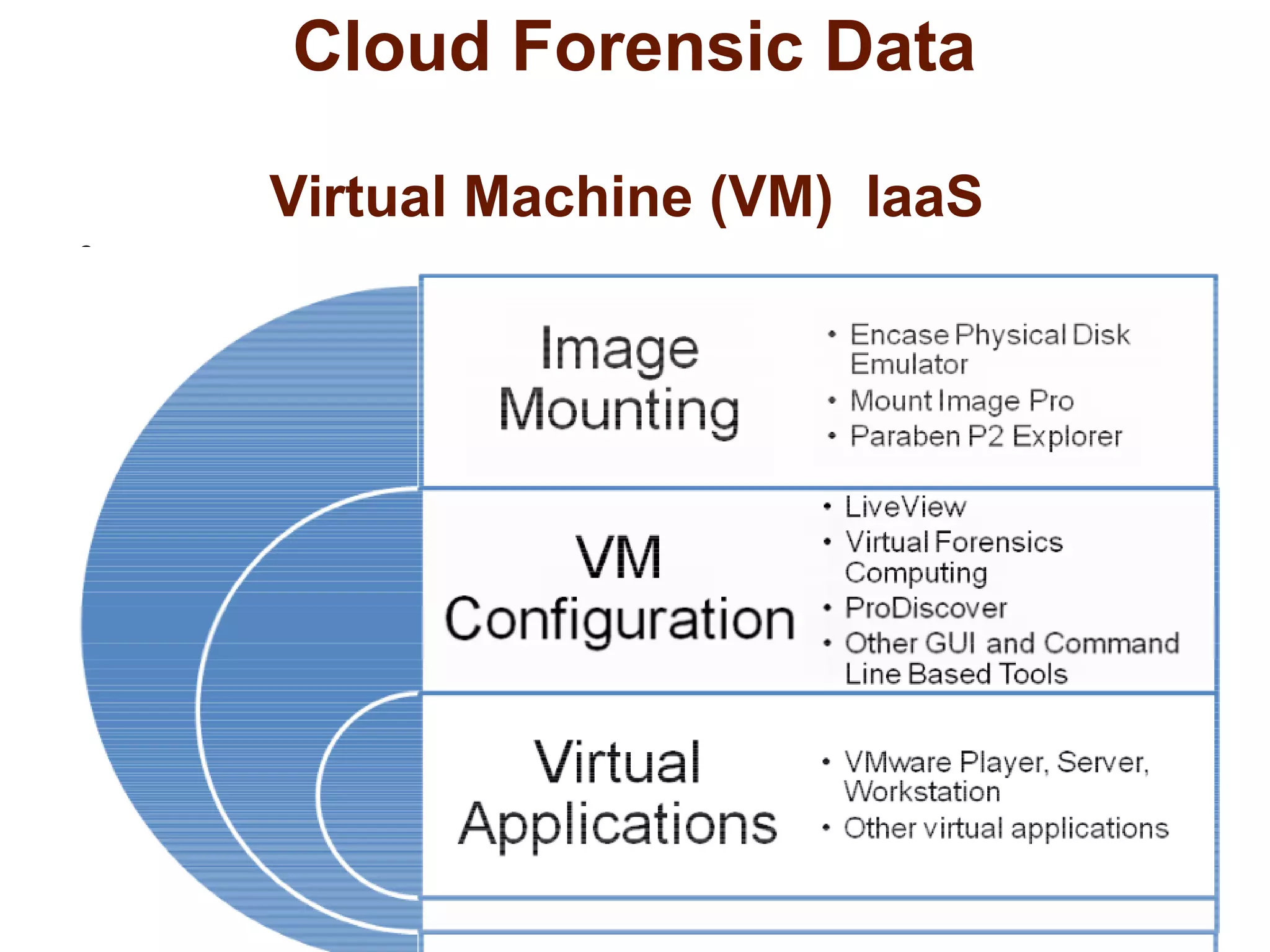
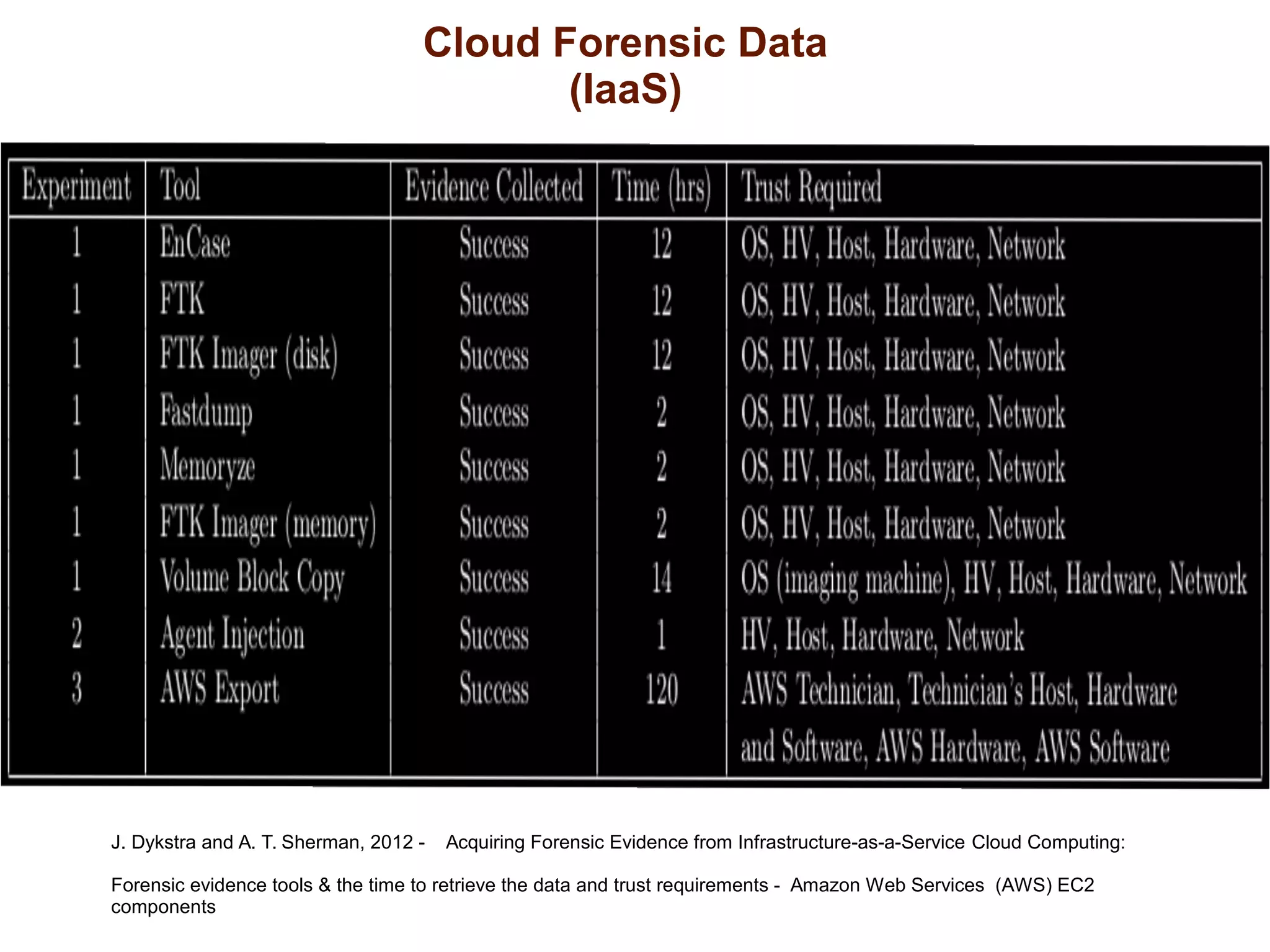
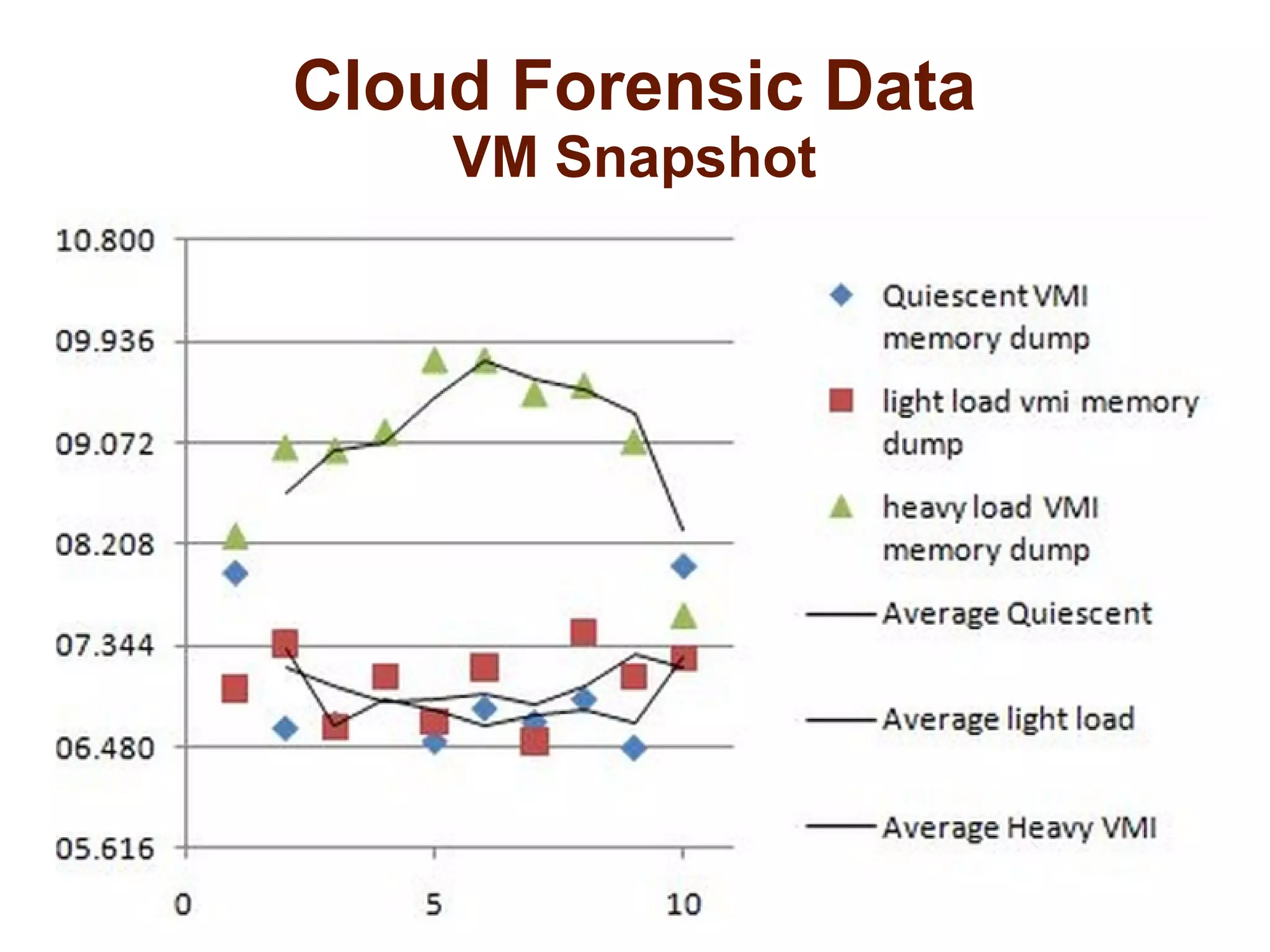
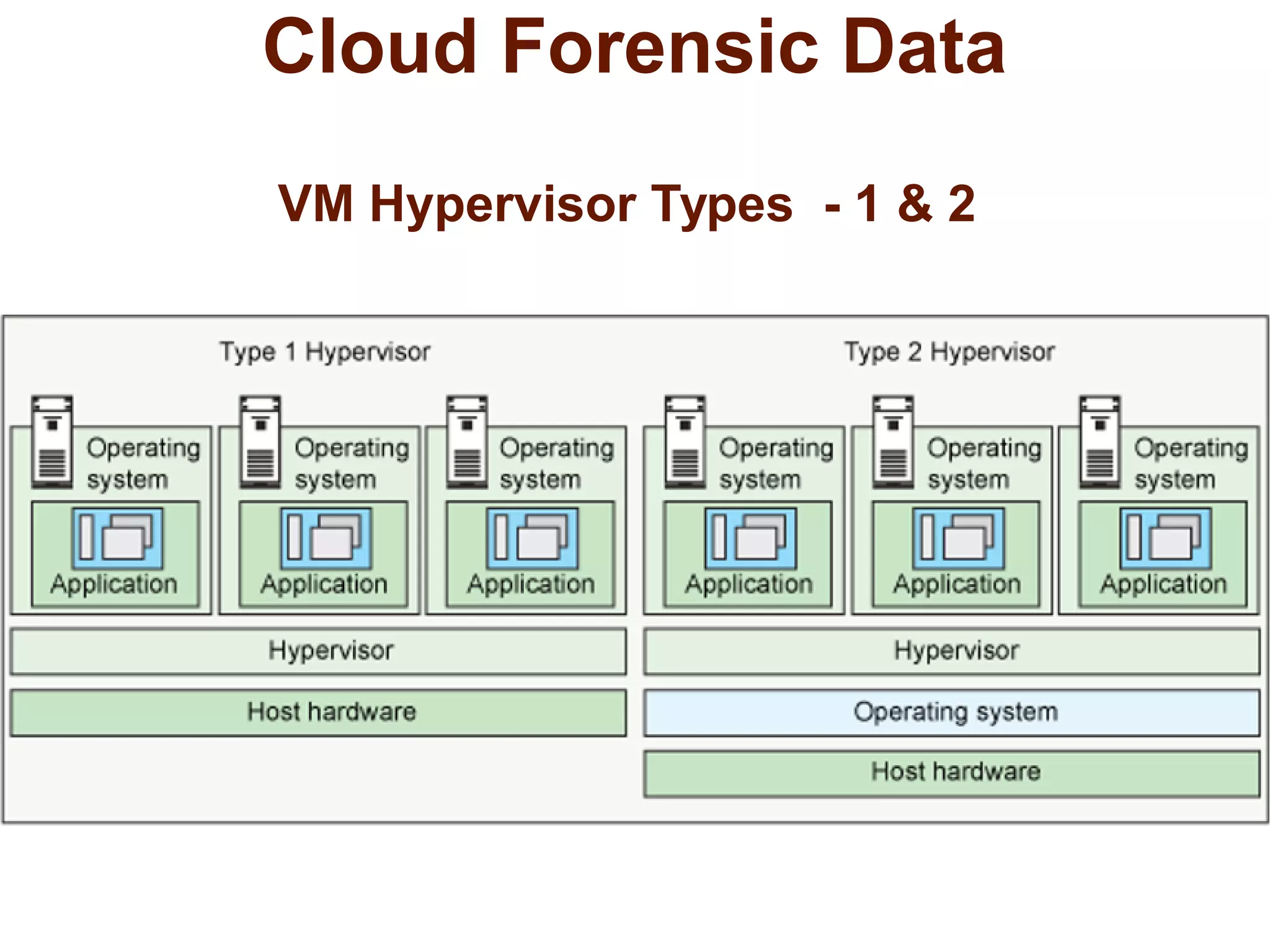
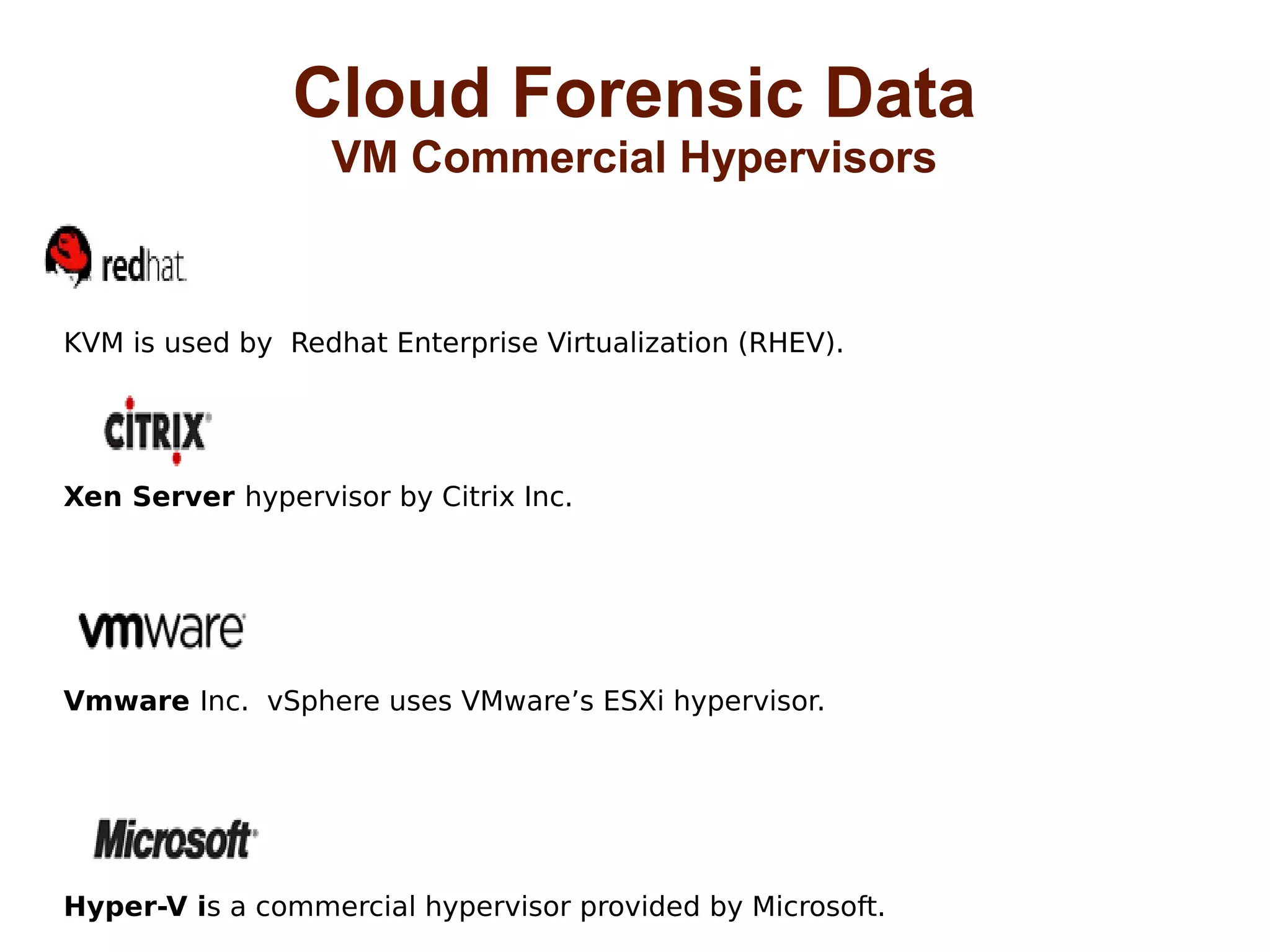
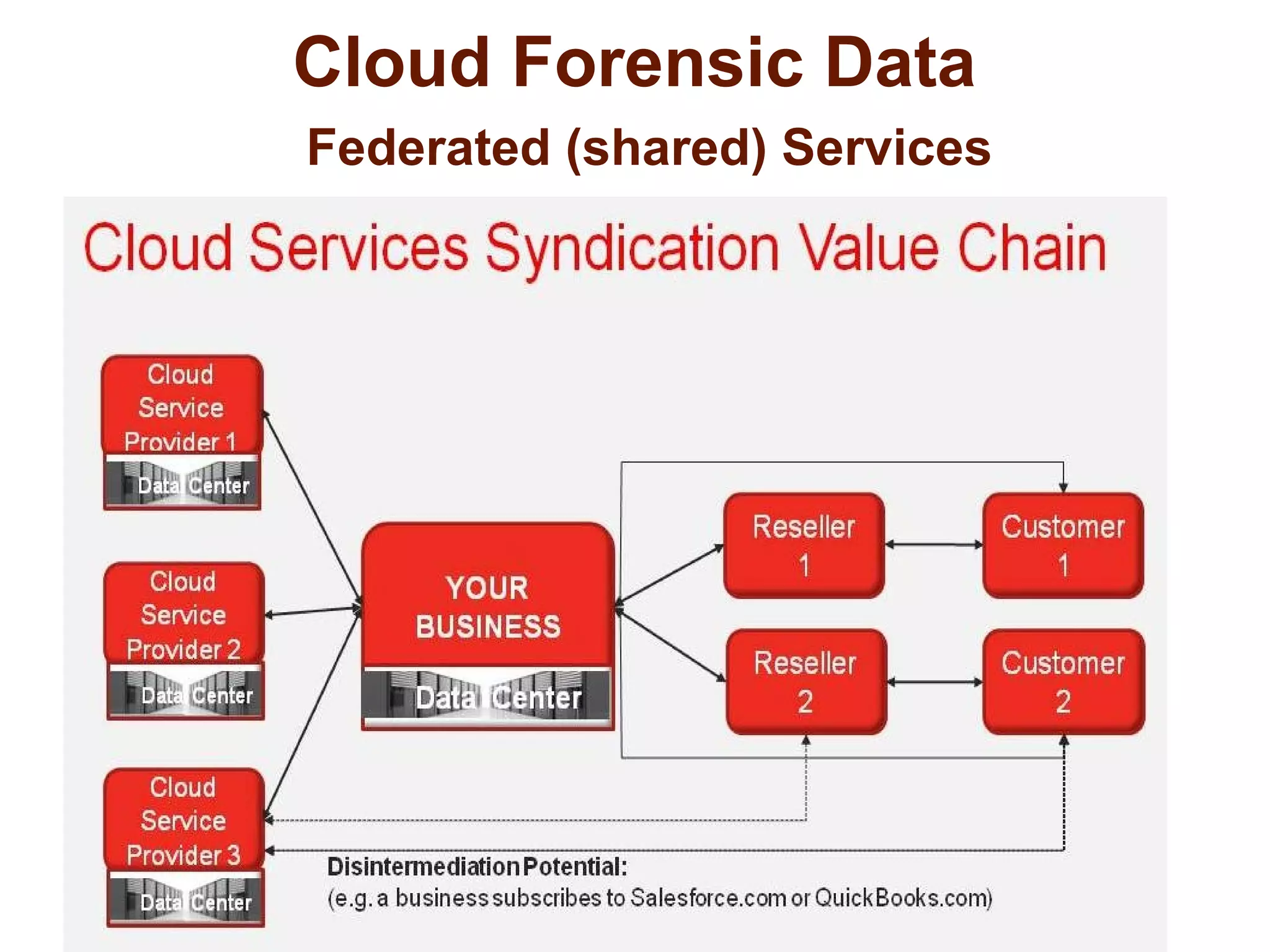
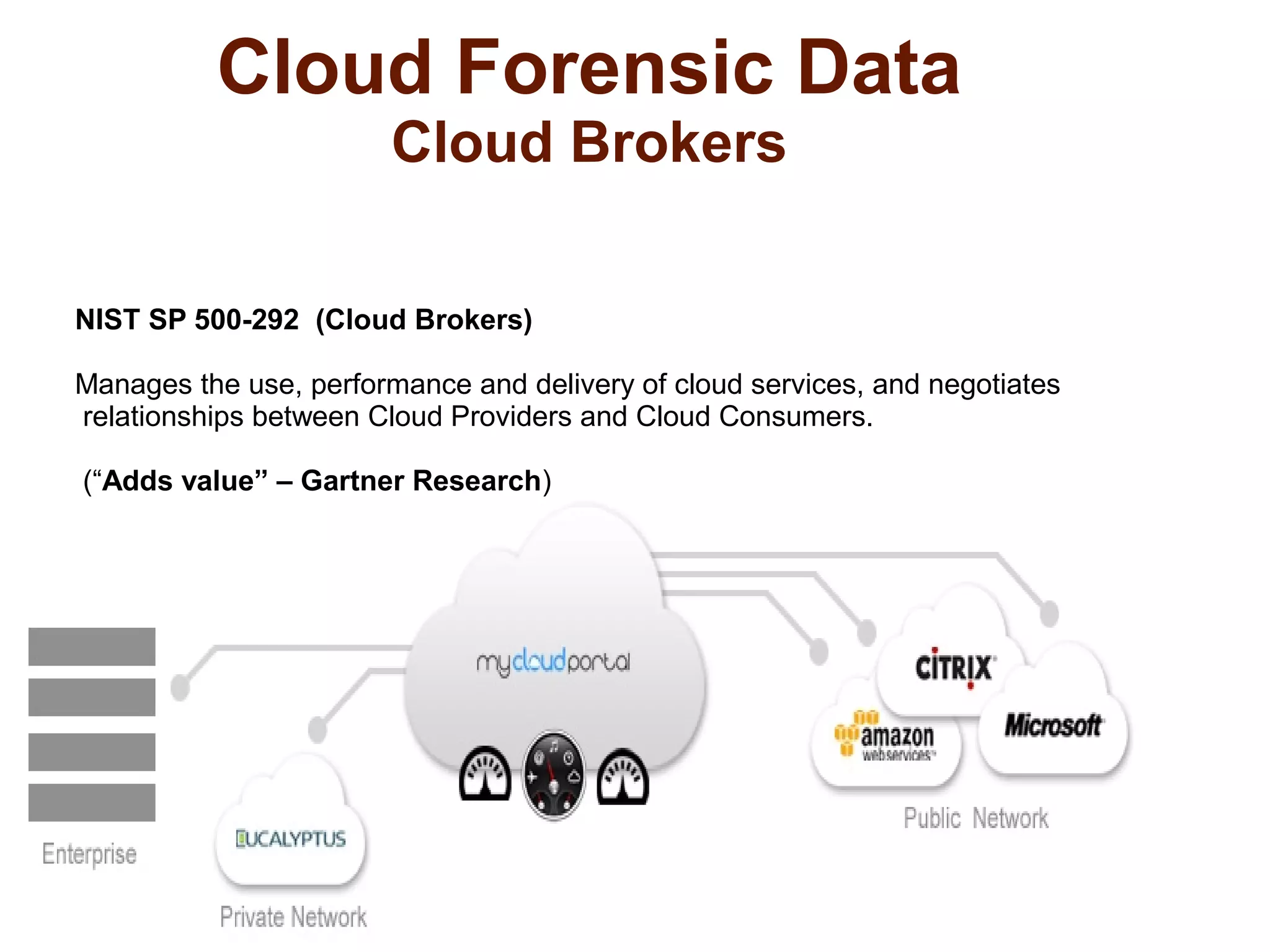
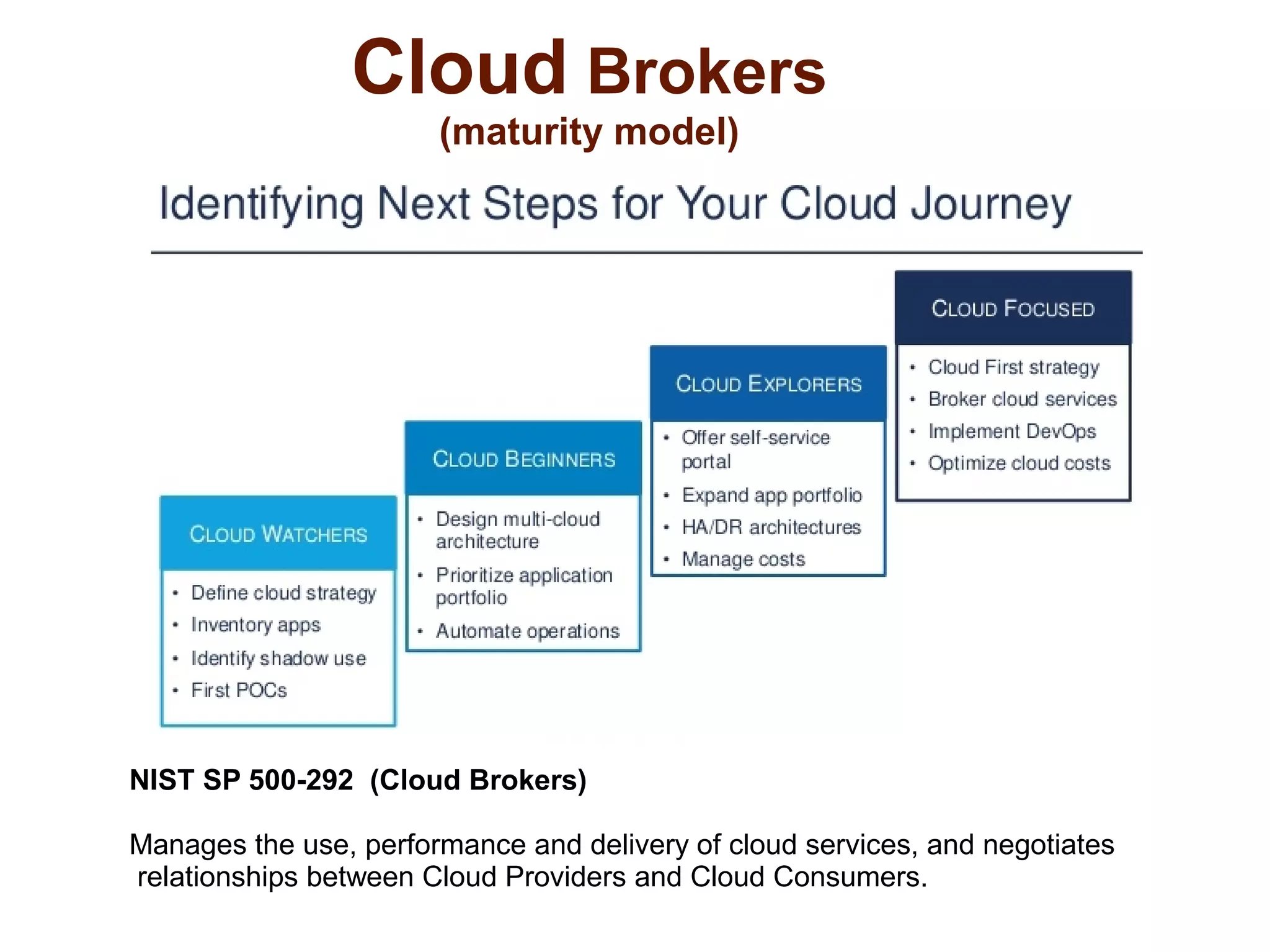
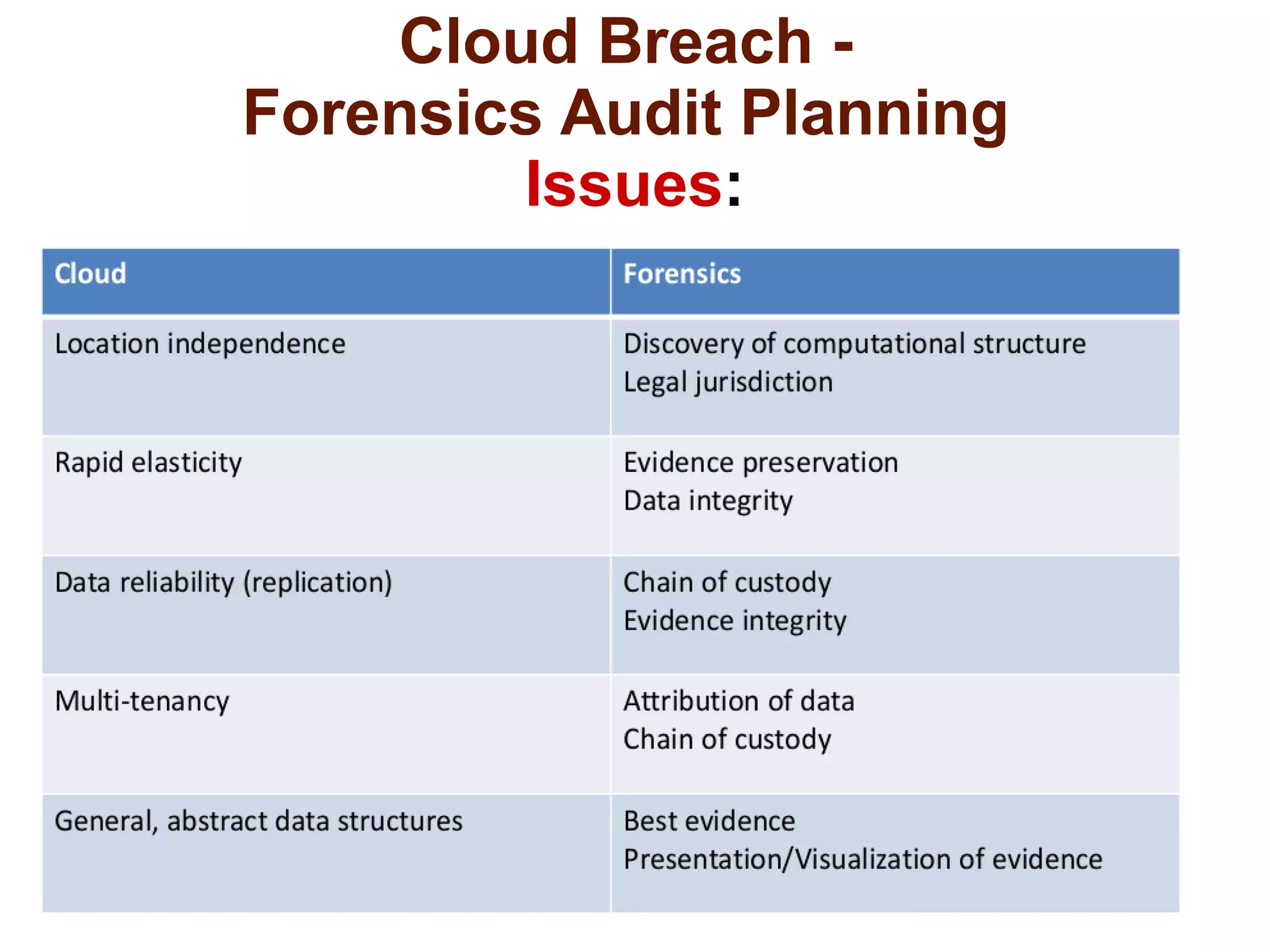
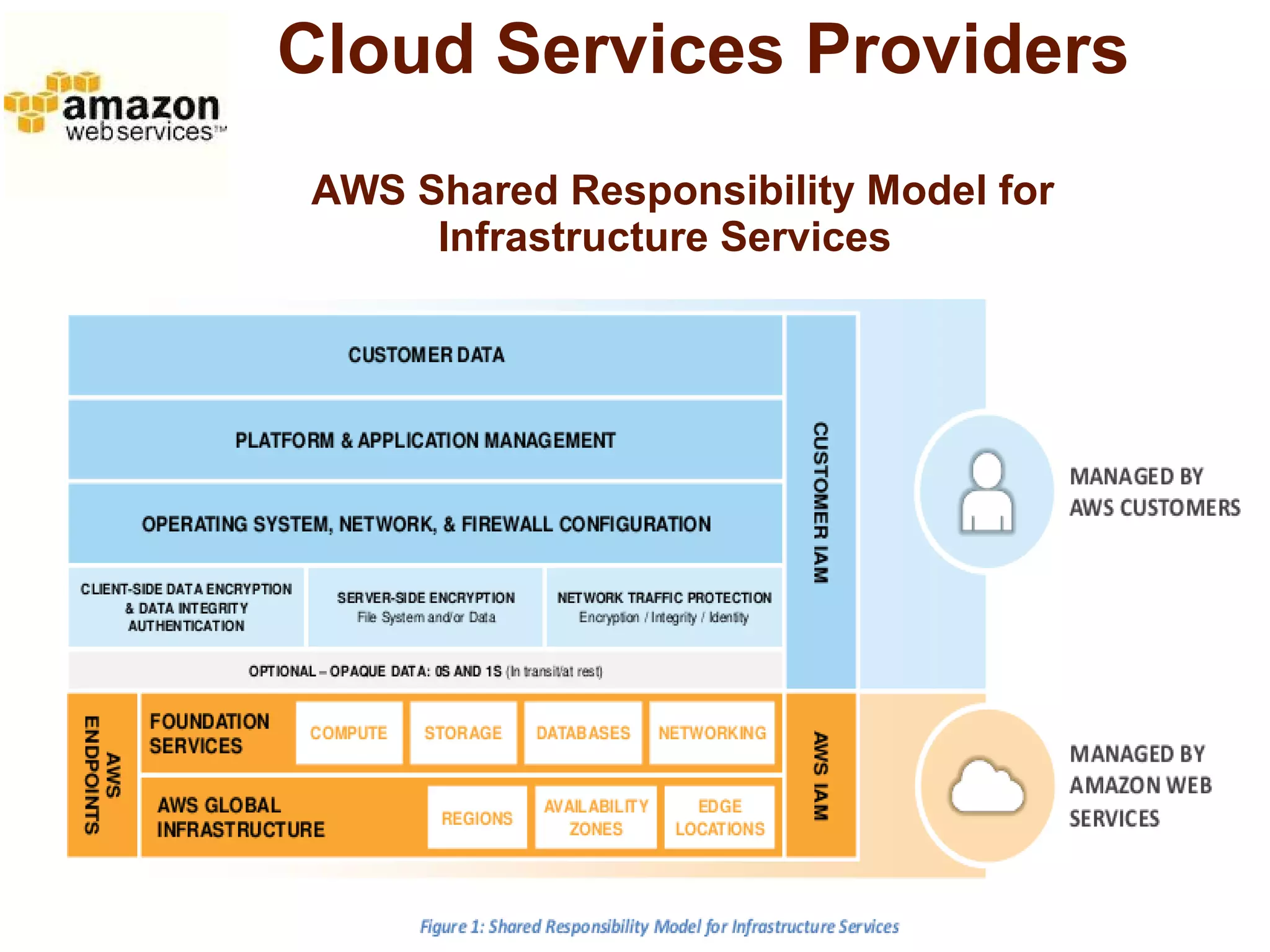
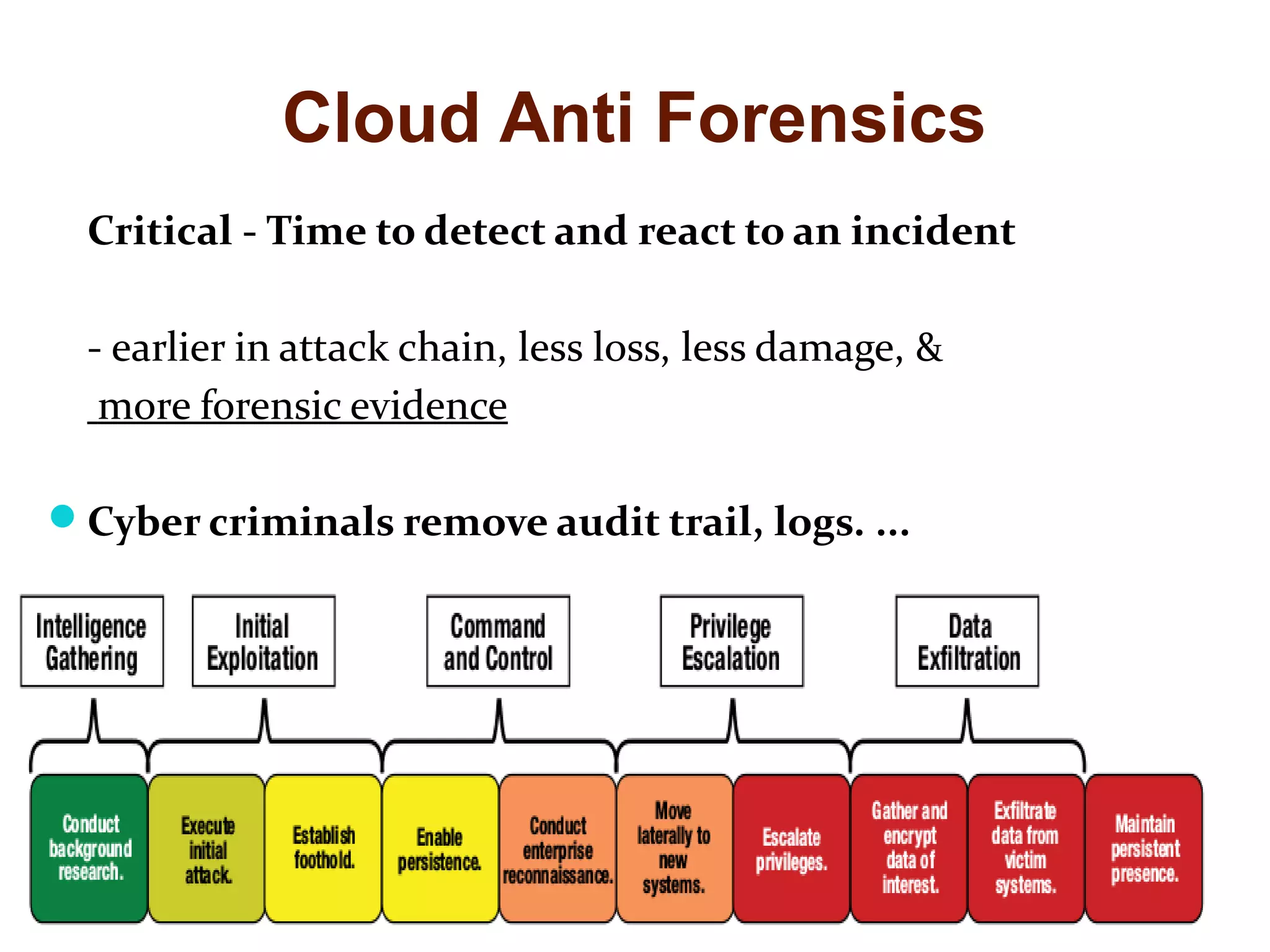
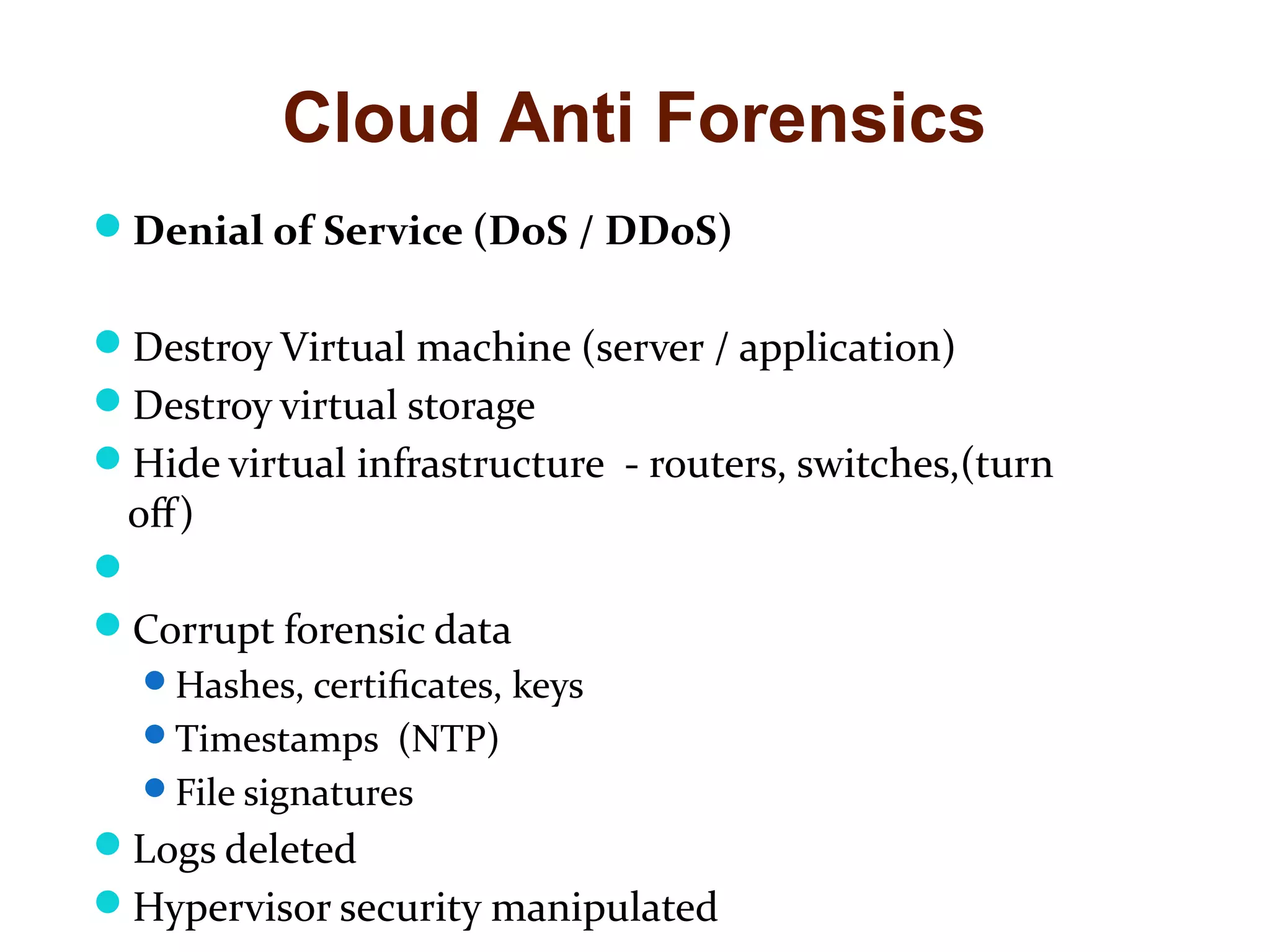
The document discusses the complexities of conducting forensic audits on cloud computing services, highlighting challenges such as data acquisition, cooperation from cloud providers, and the integrity of logs. It details various forensic and anti-forensic processes, emphasizing the importance of security practices for cloud service providers. Additionally, the document identifies essential issues in cloud forensics, including legal considerations and the reliability of forensic tools in processing cloud data.