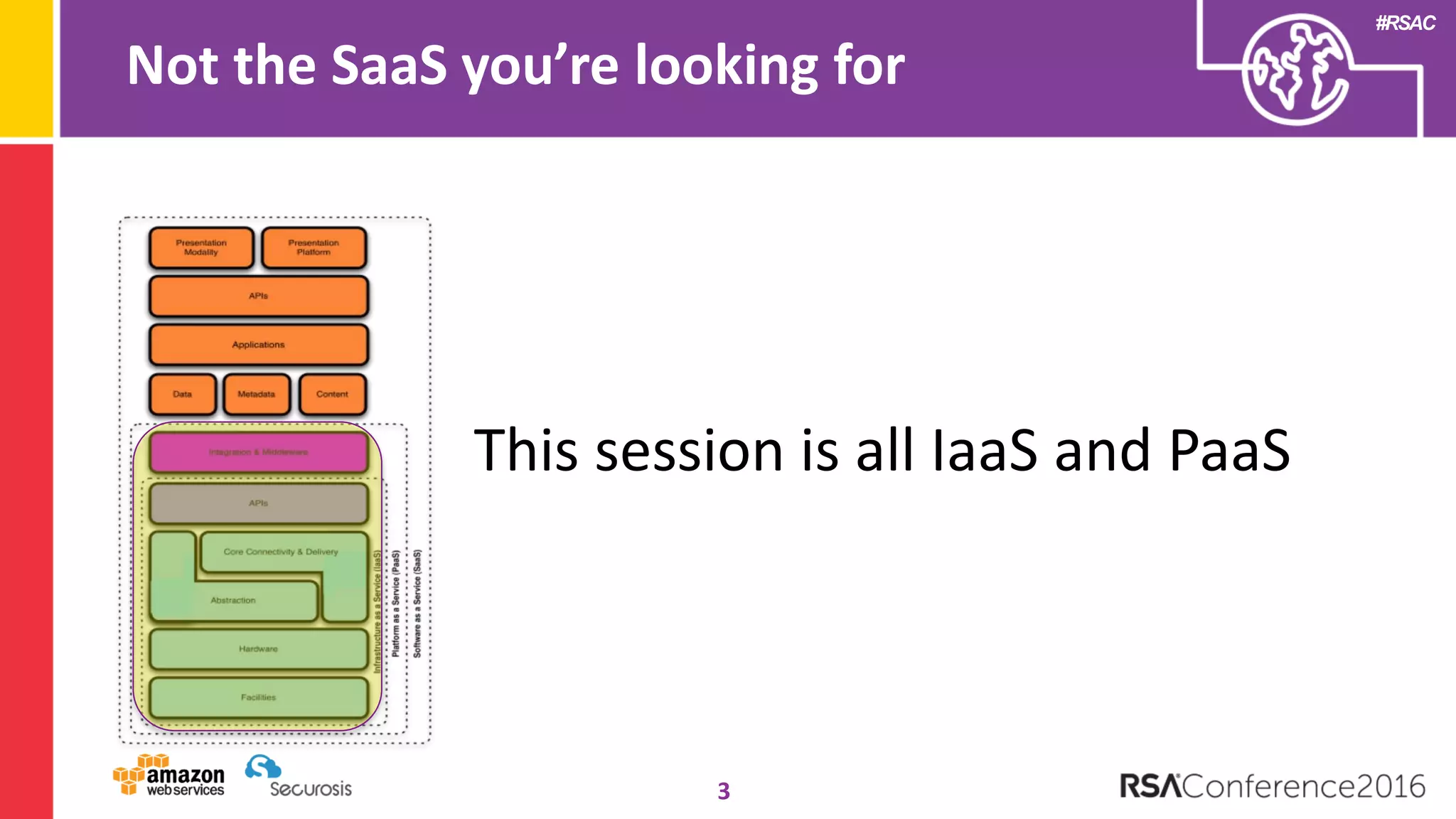
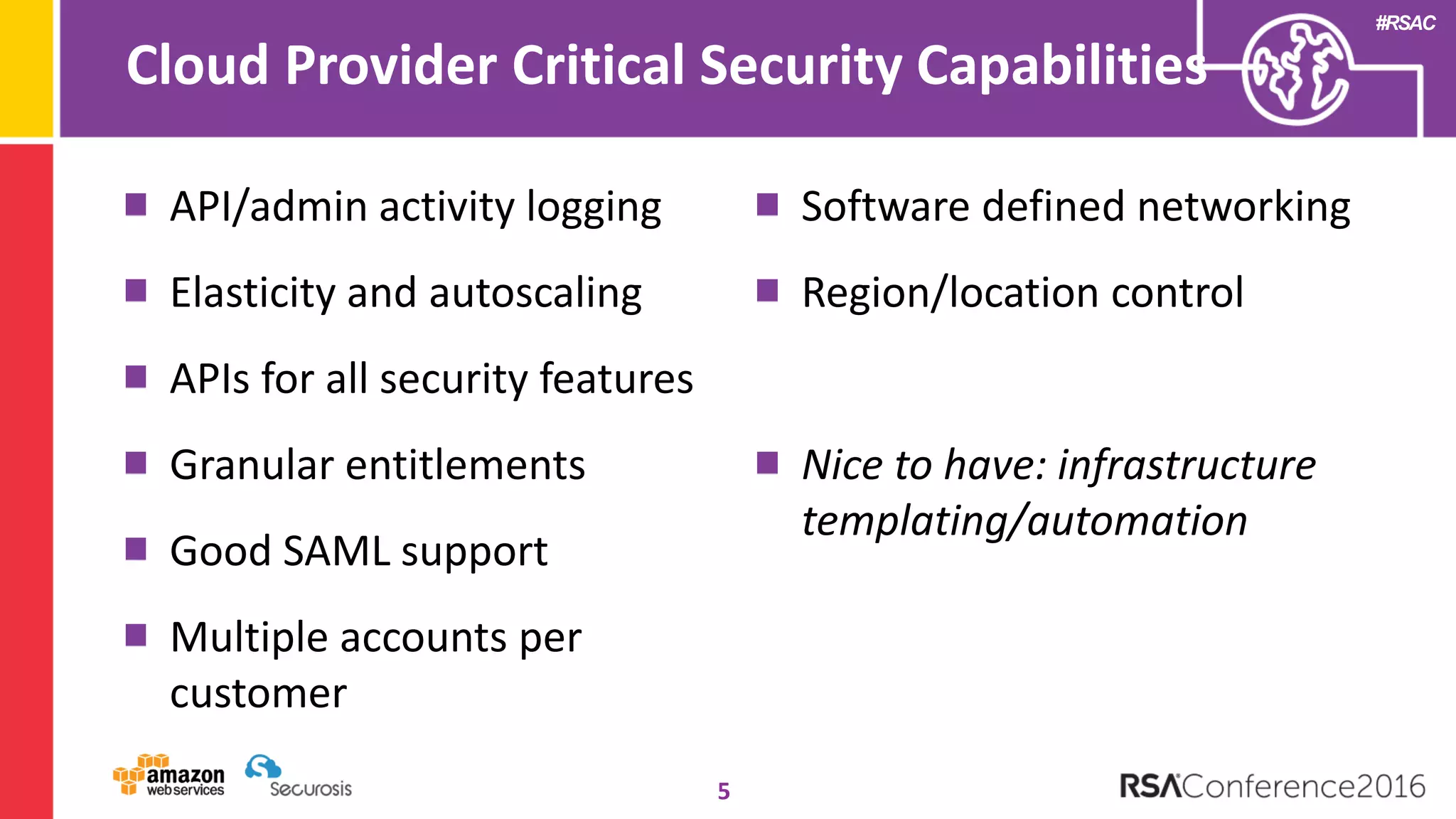
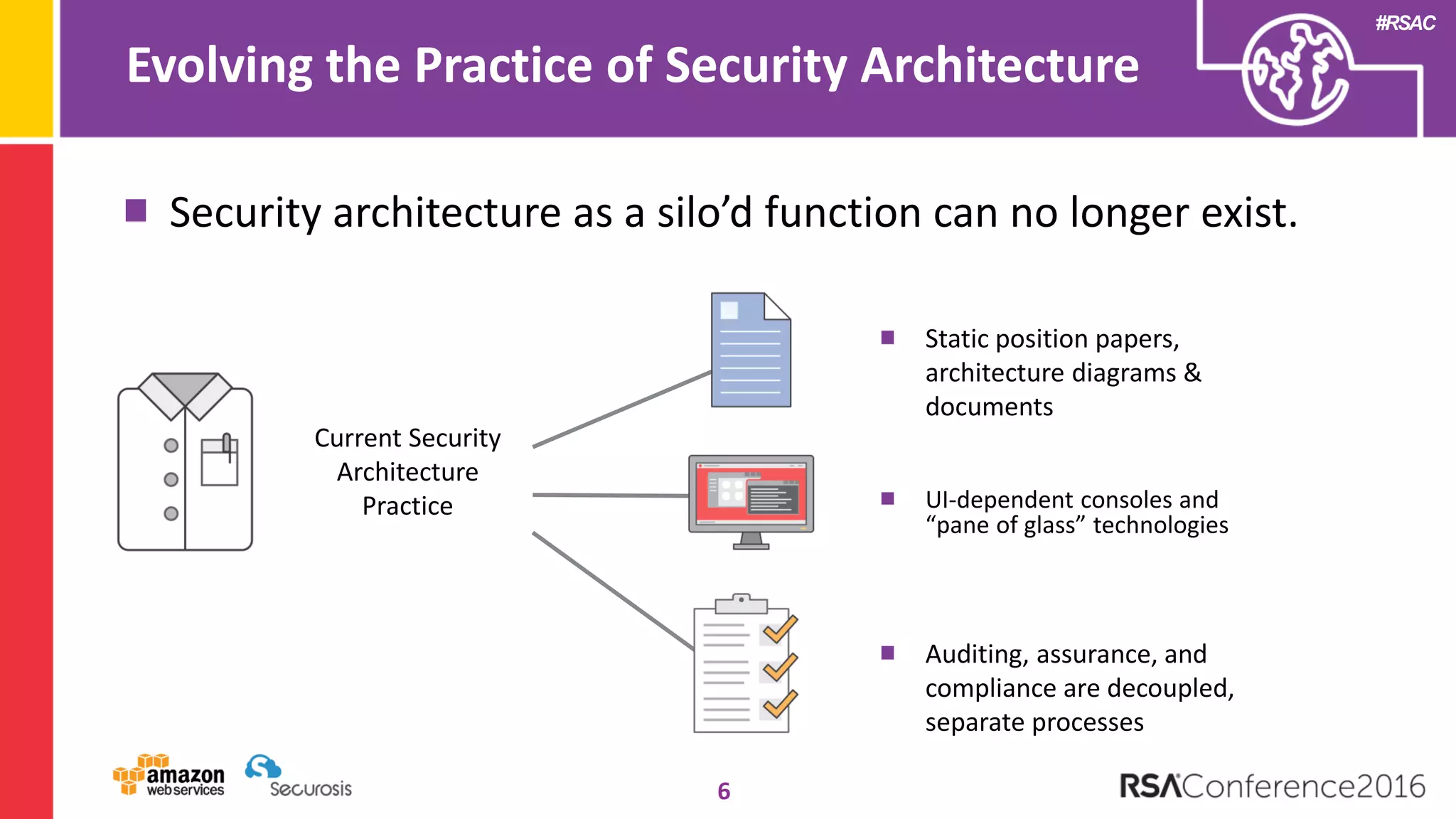
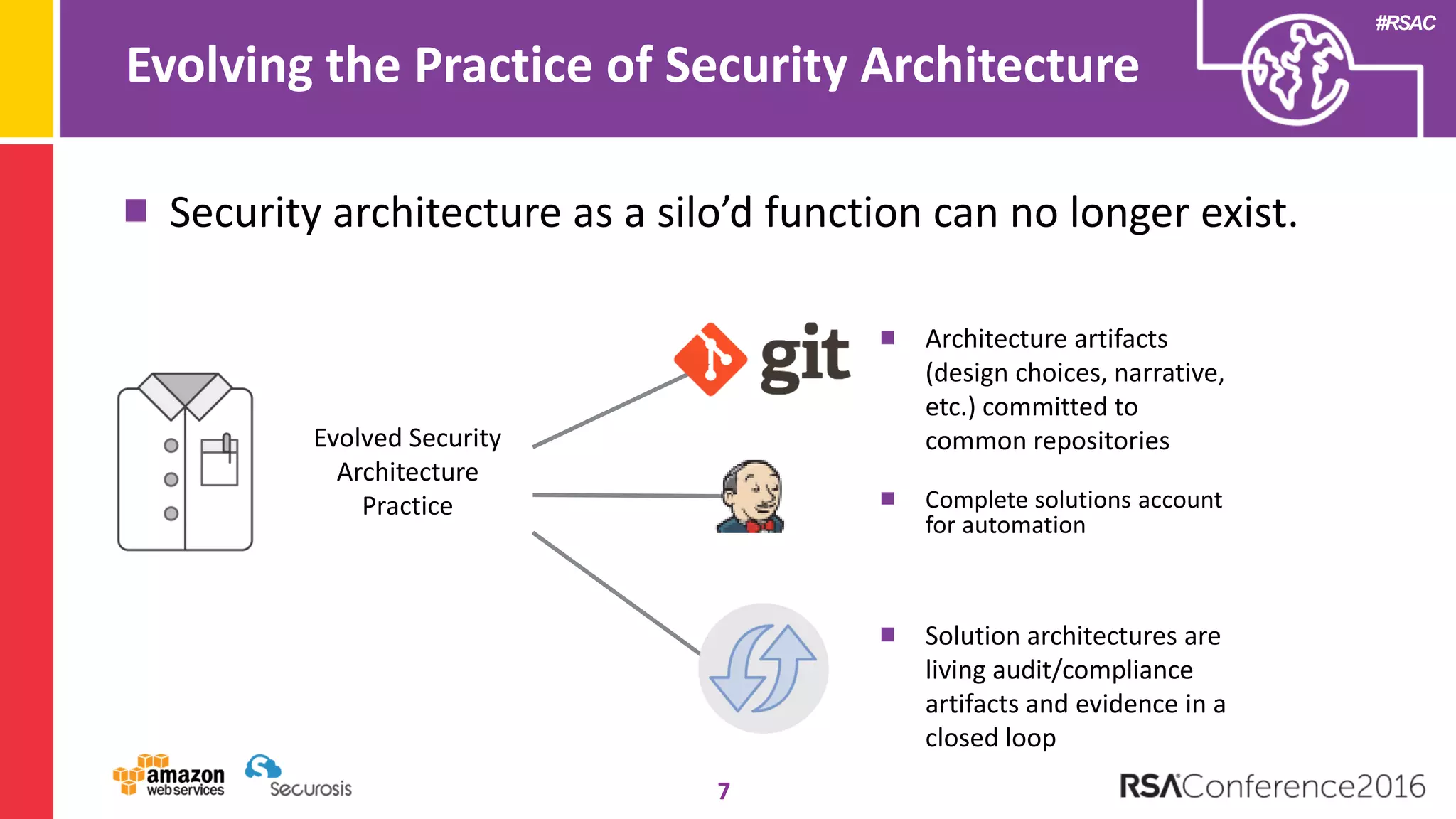
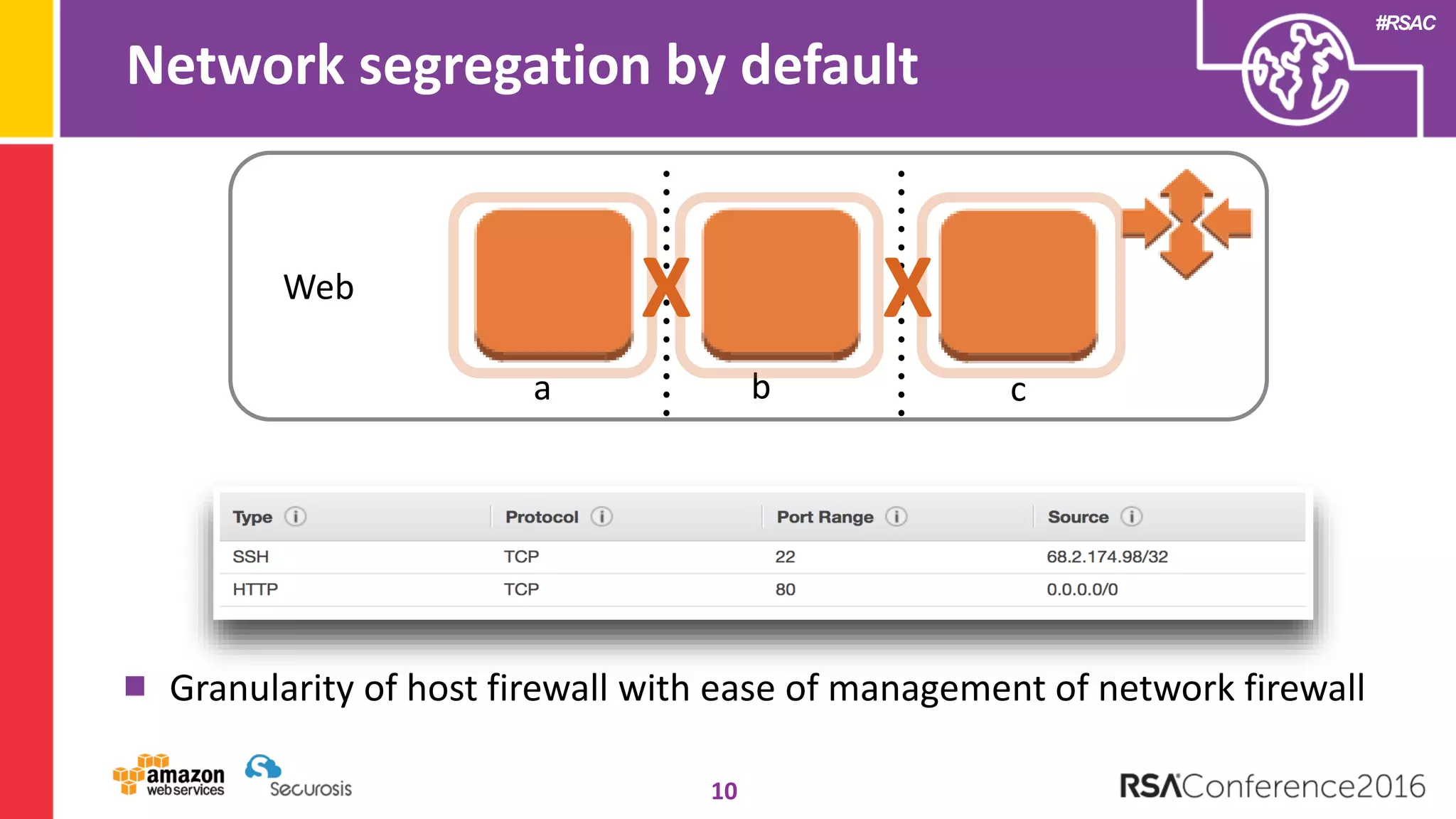
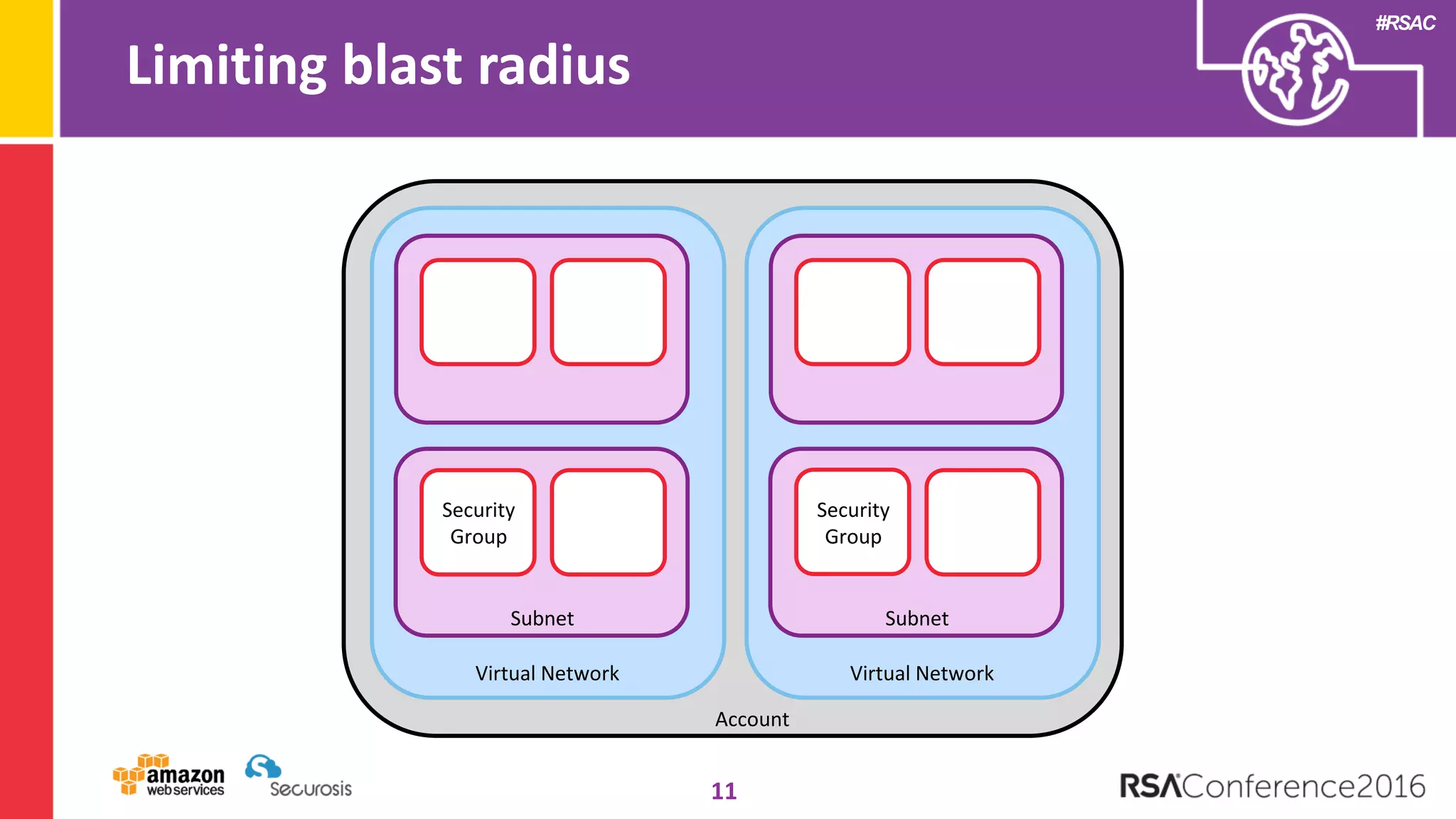
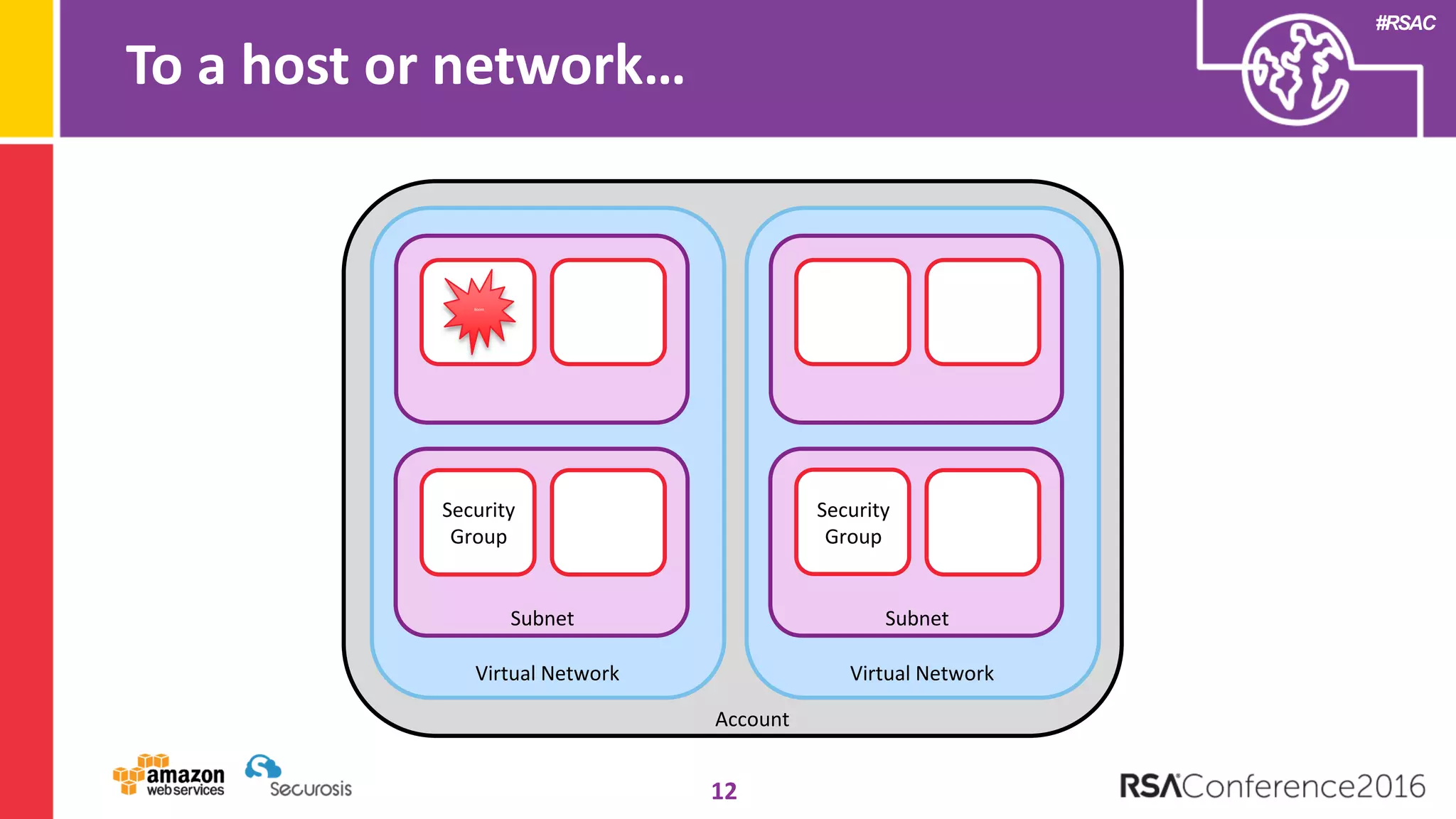
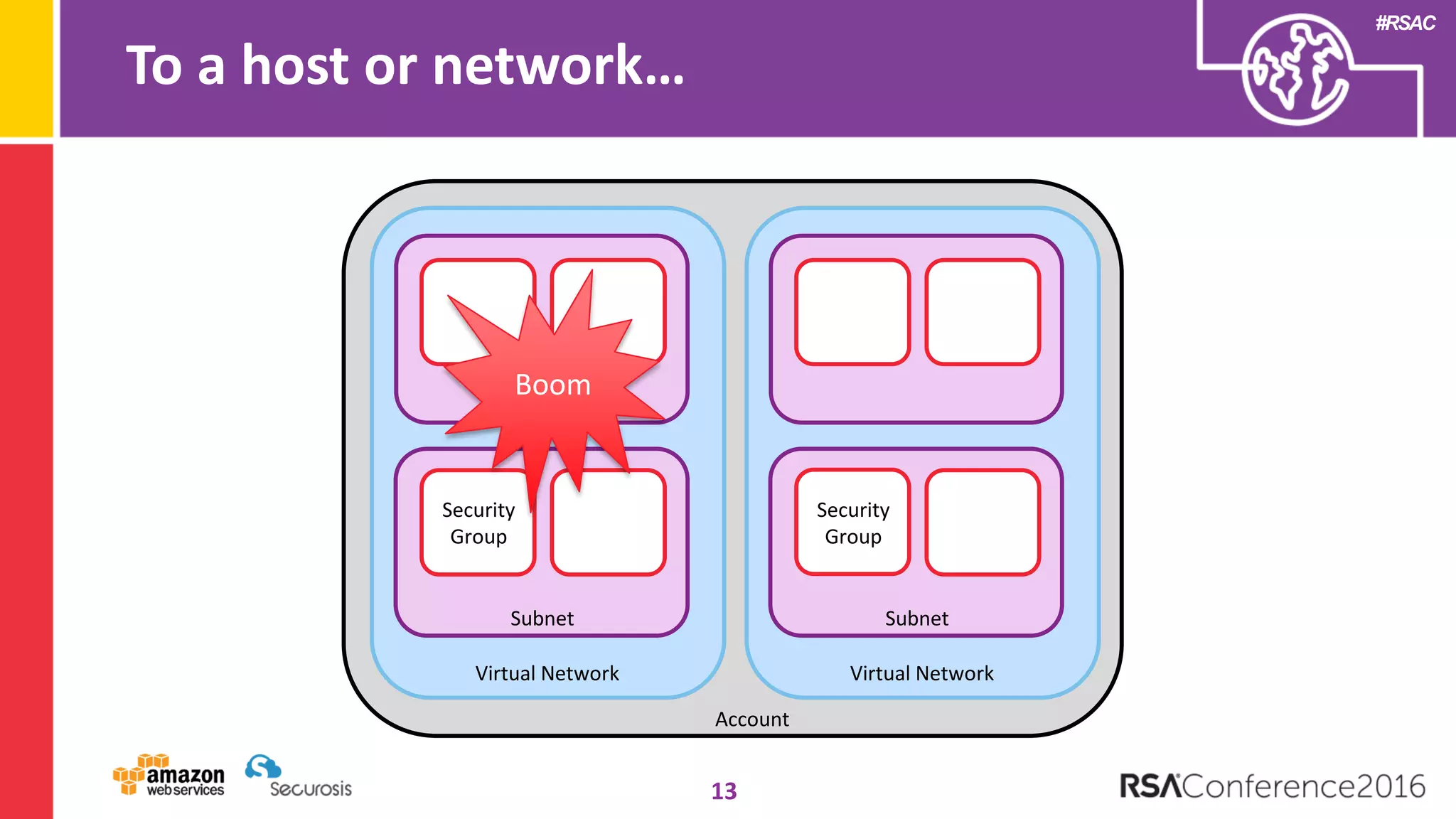
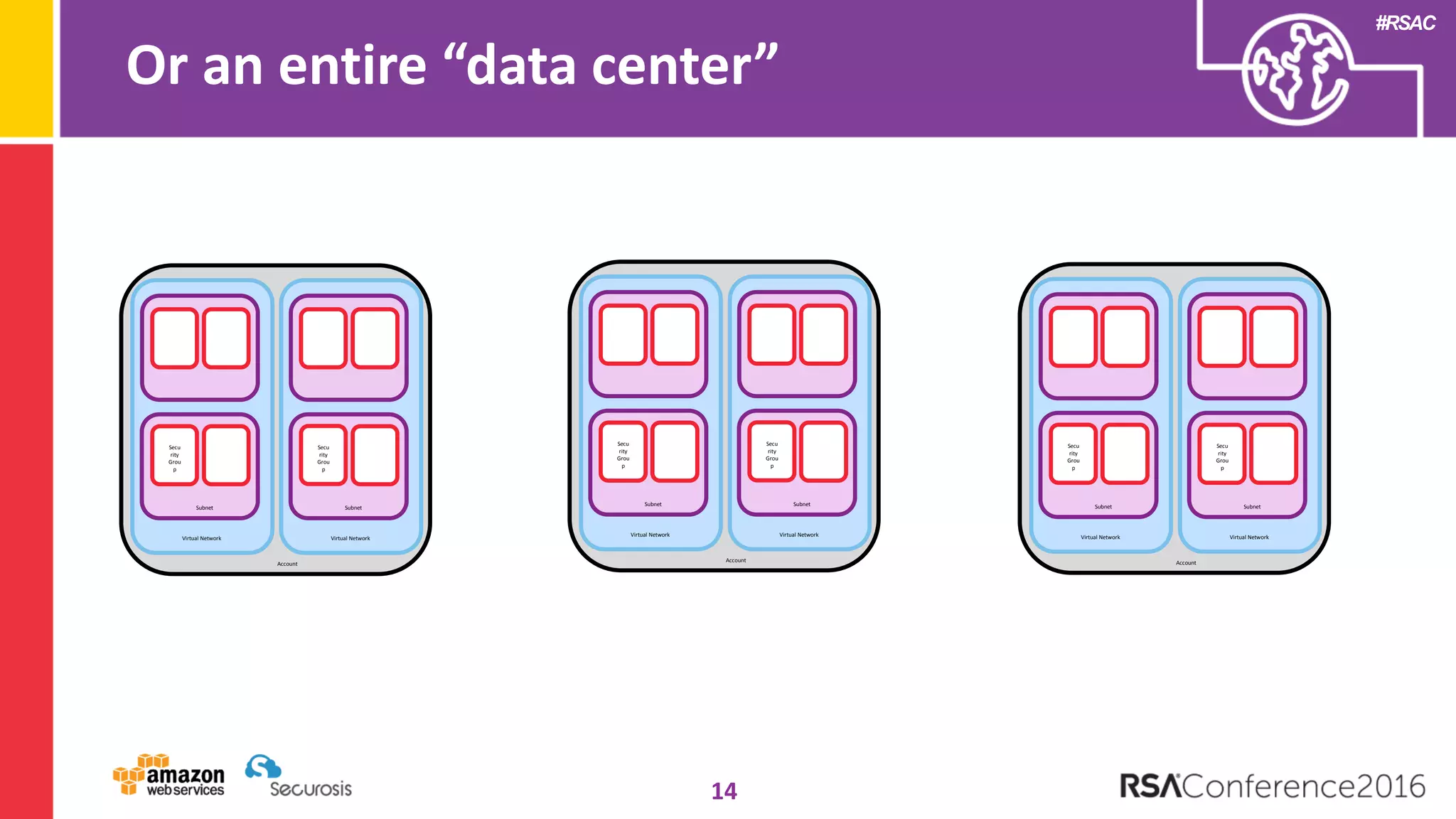
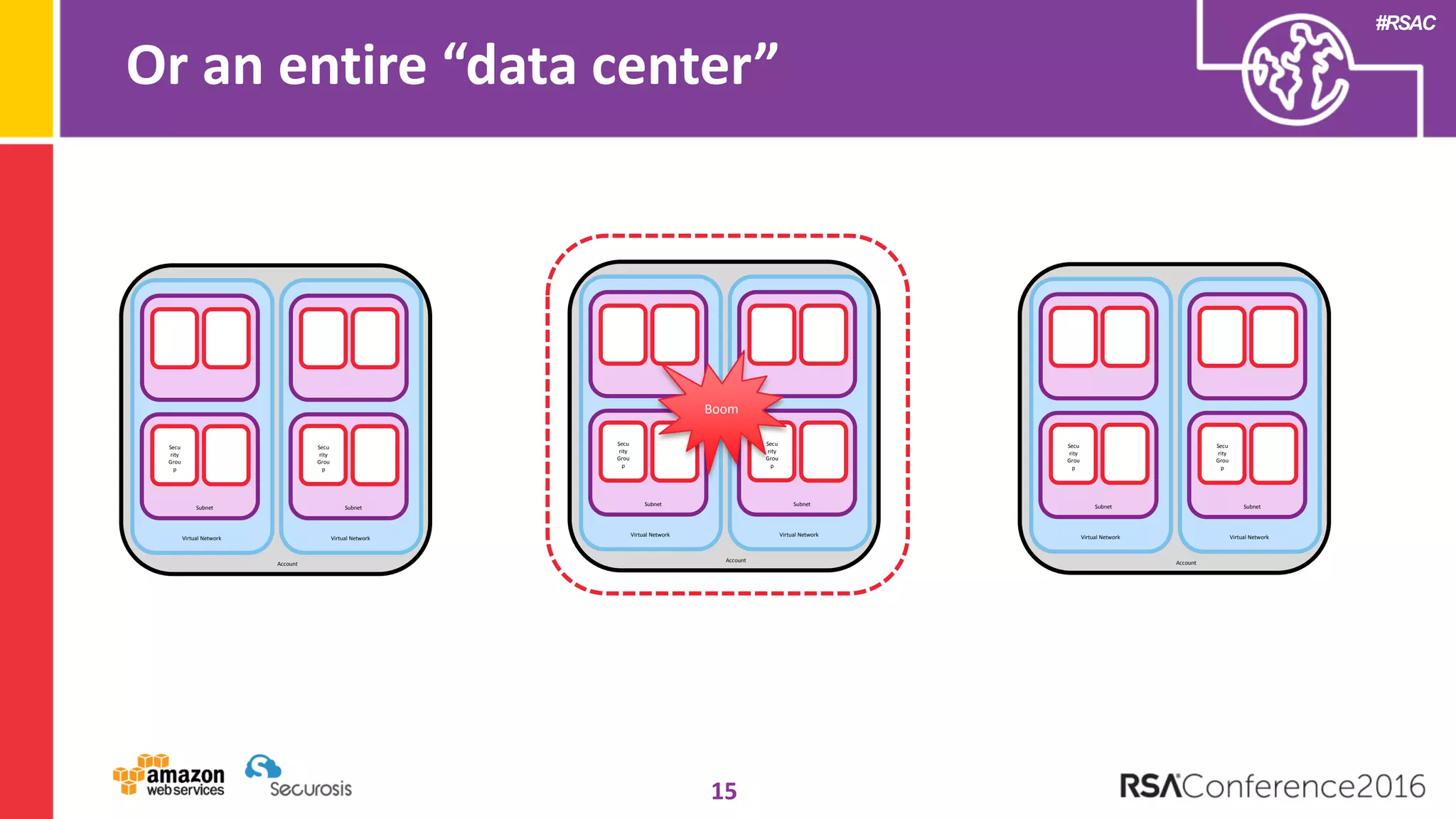
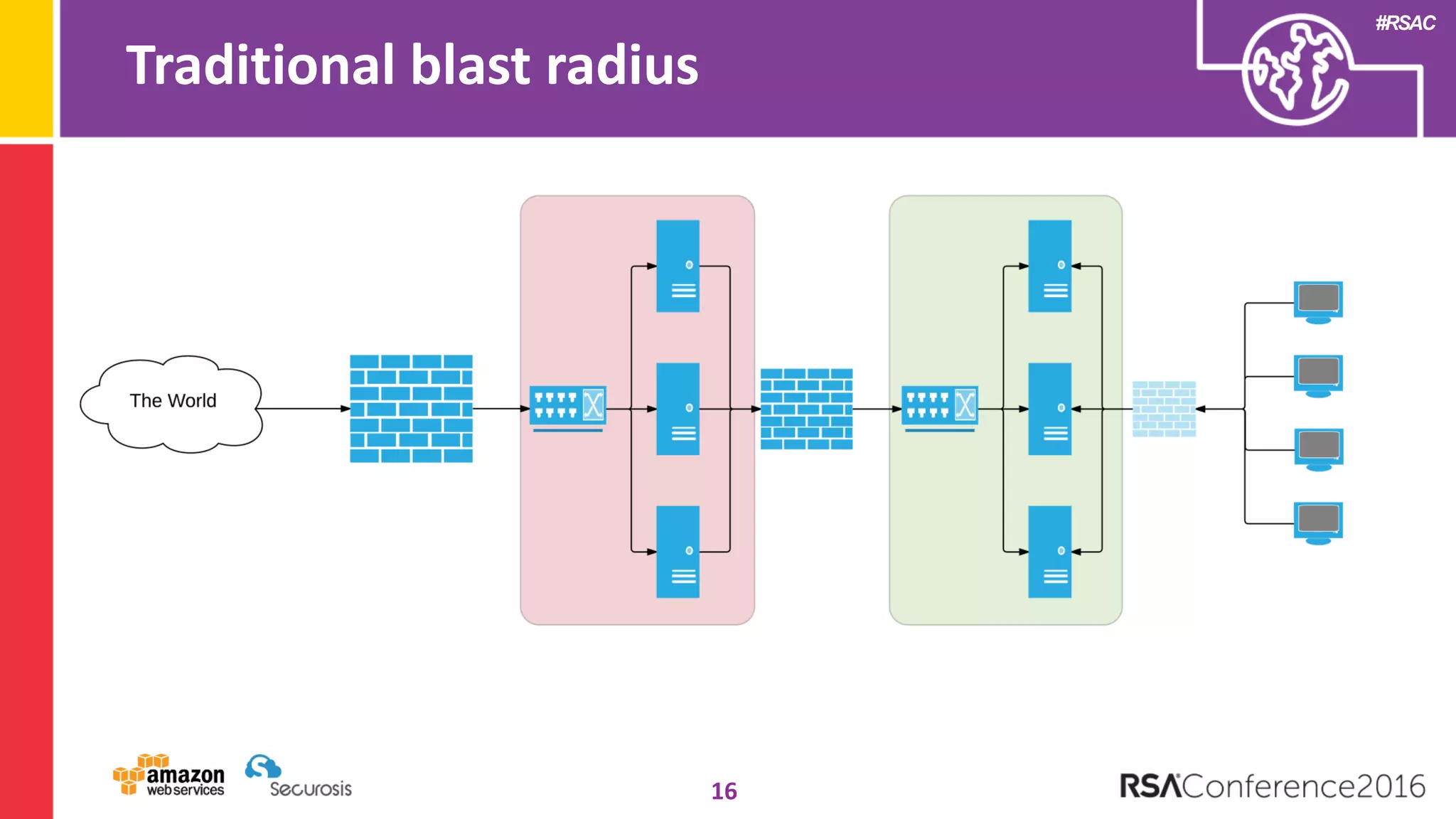
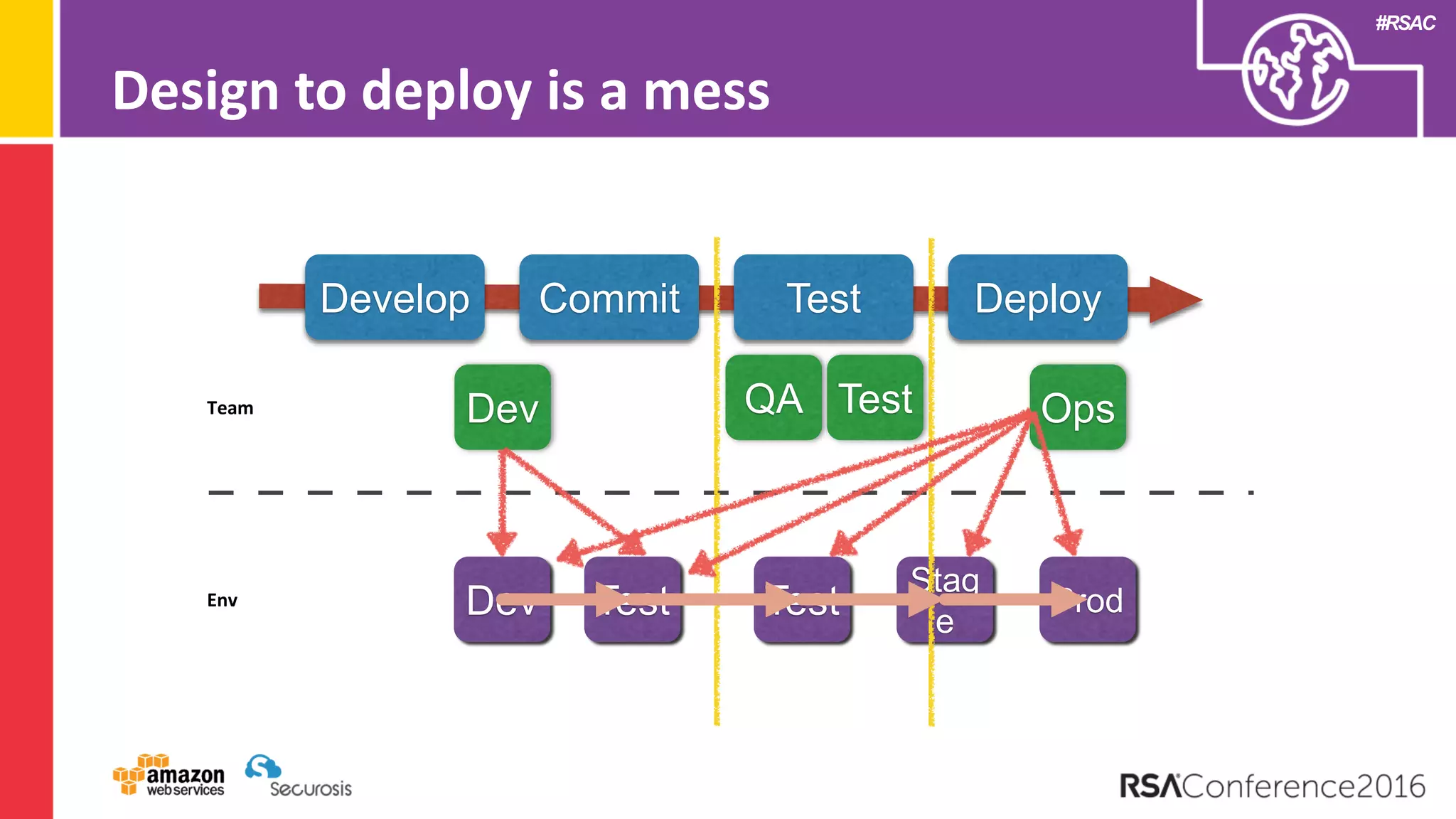
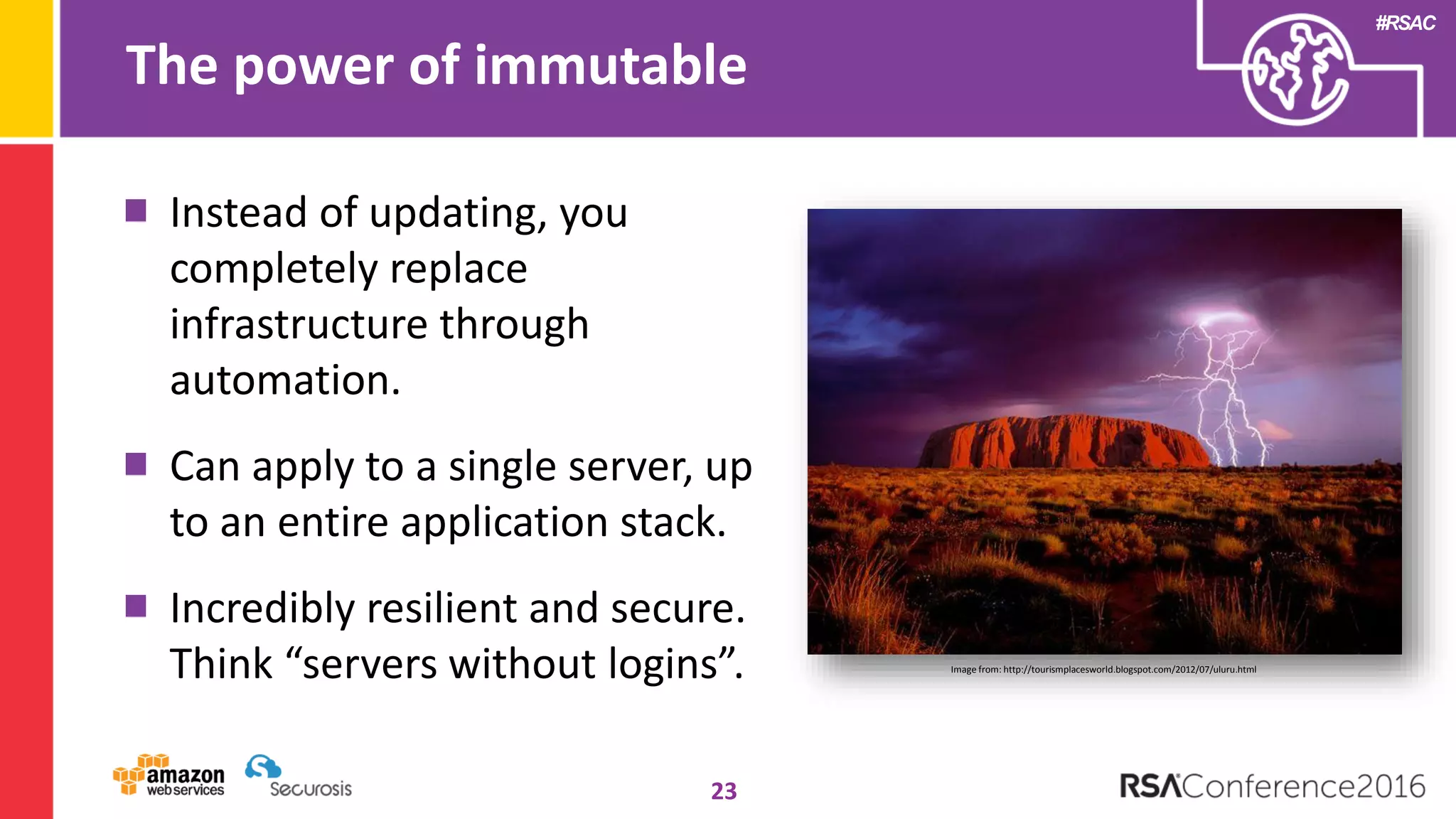
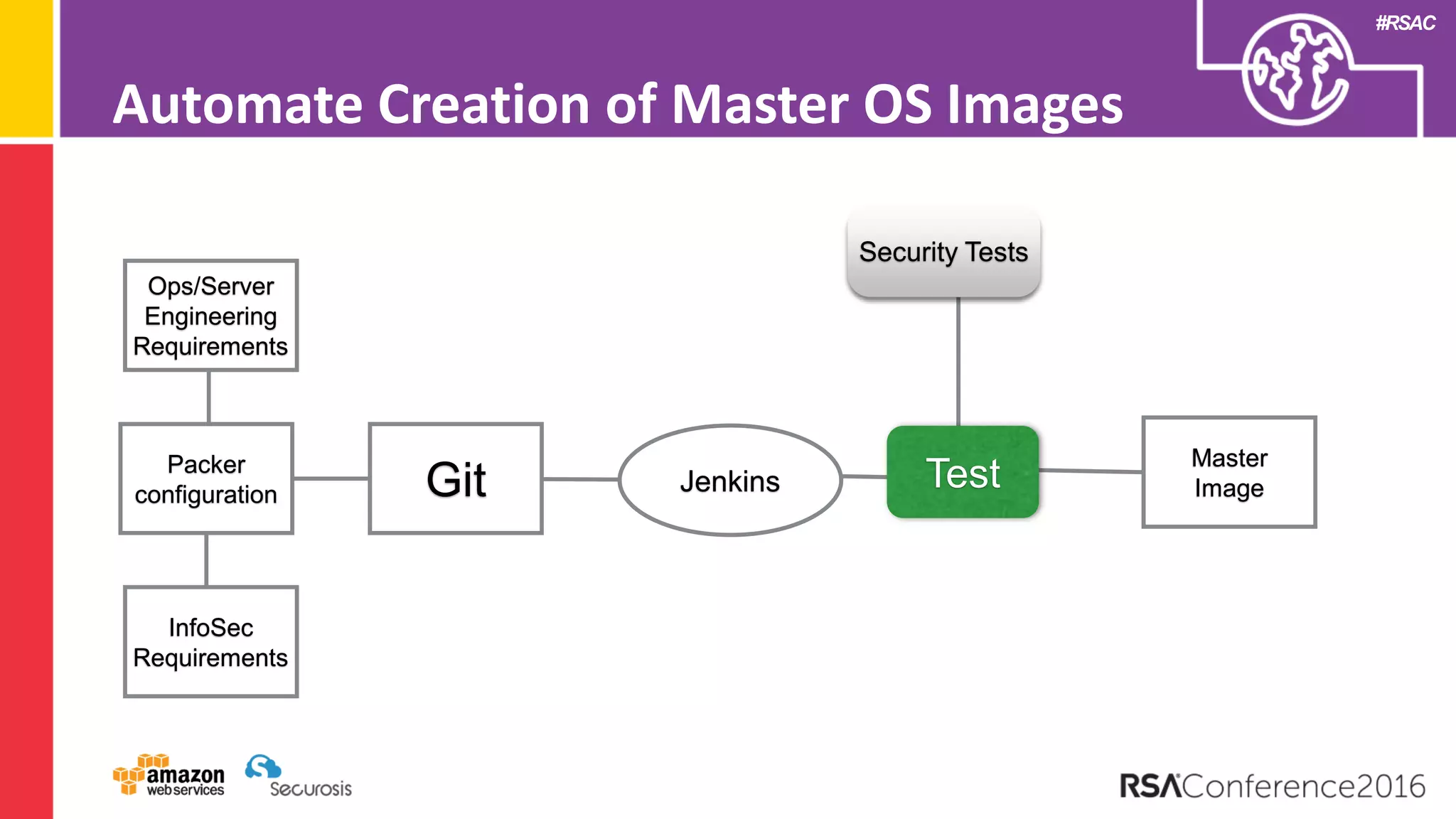
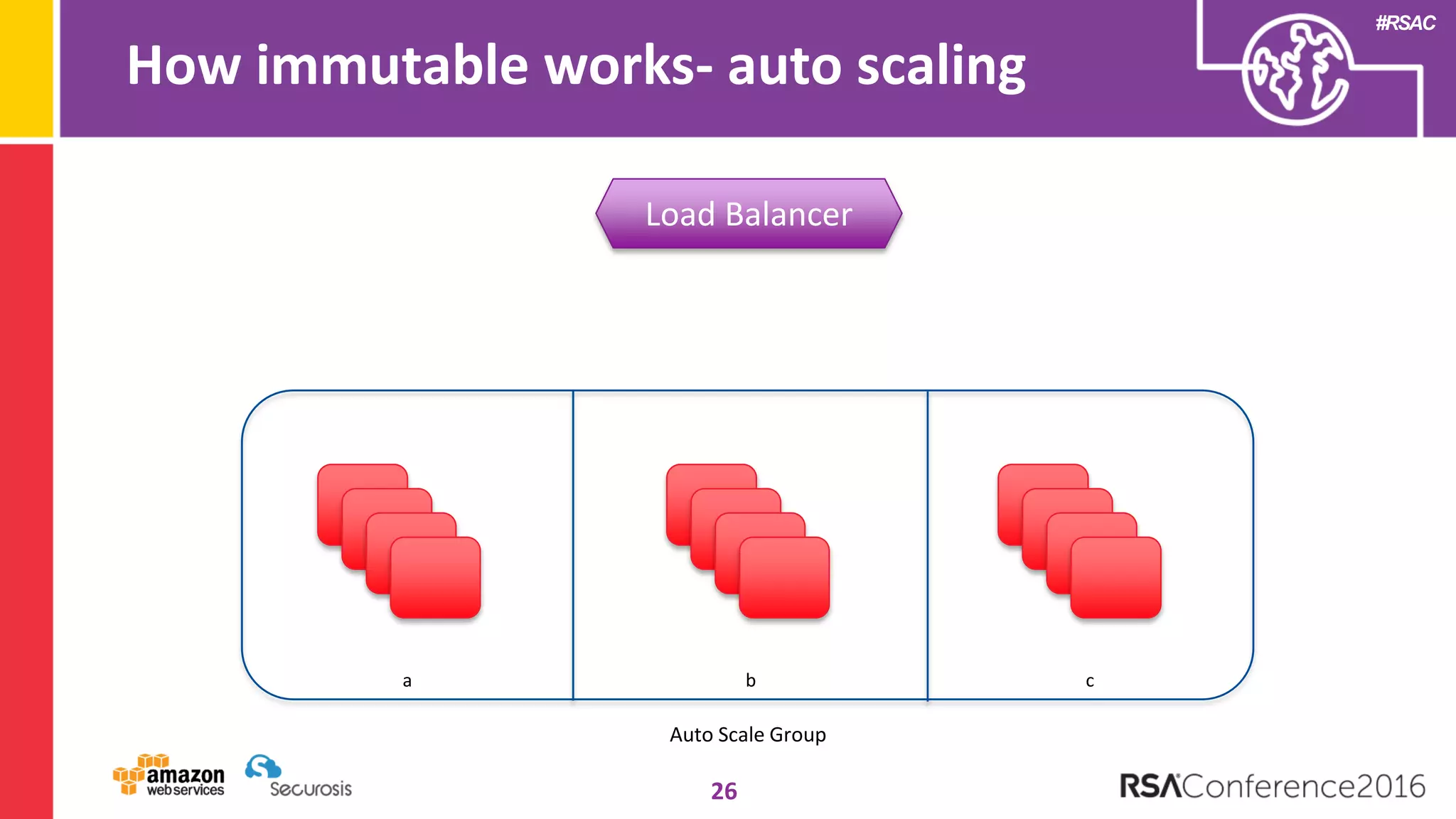
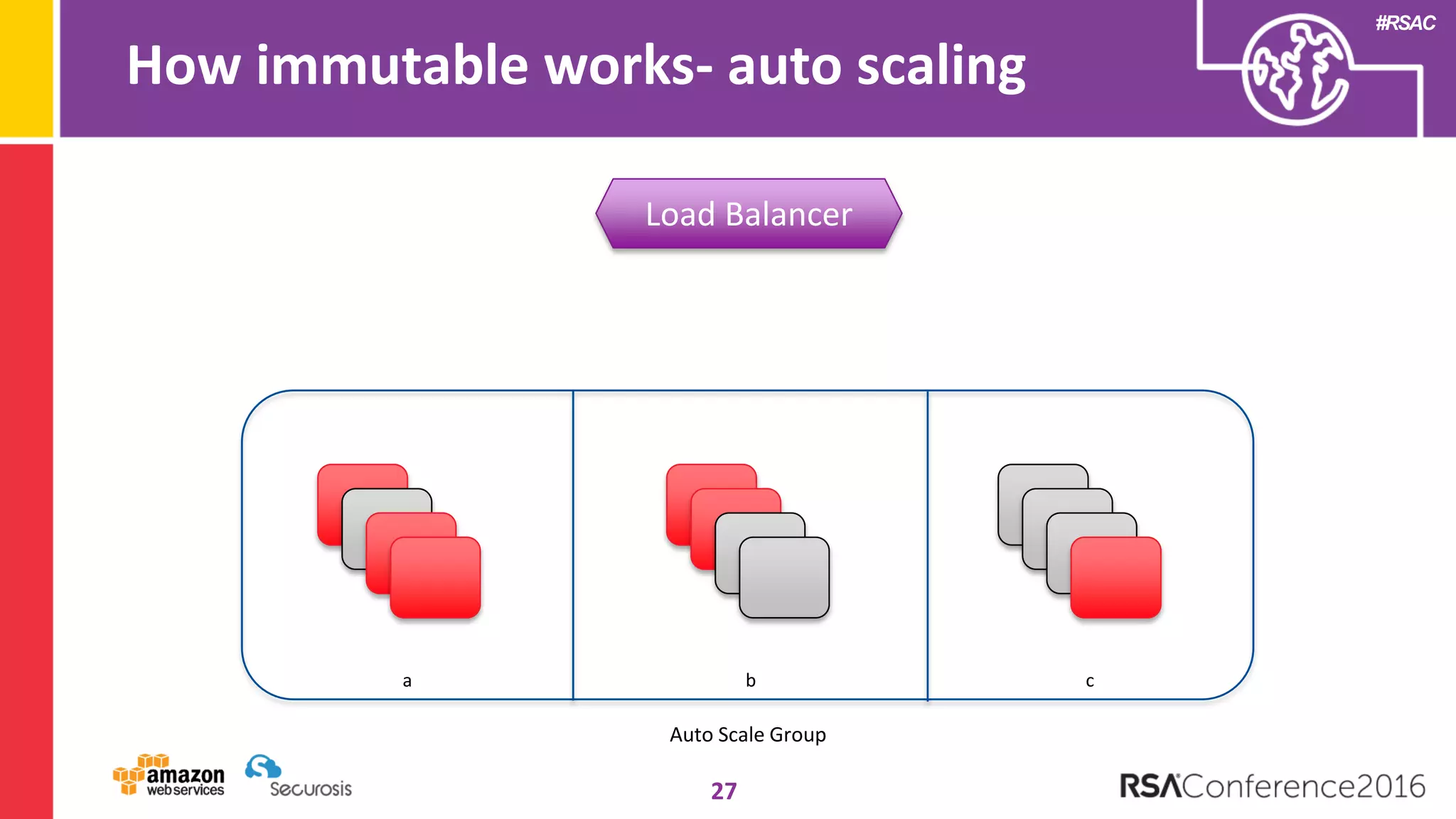
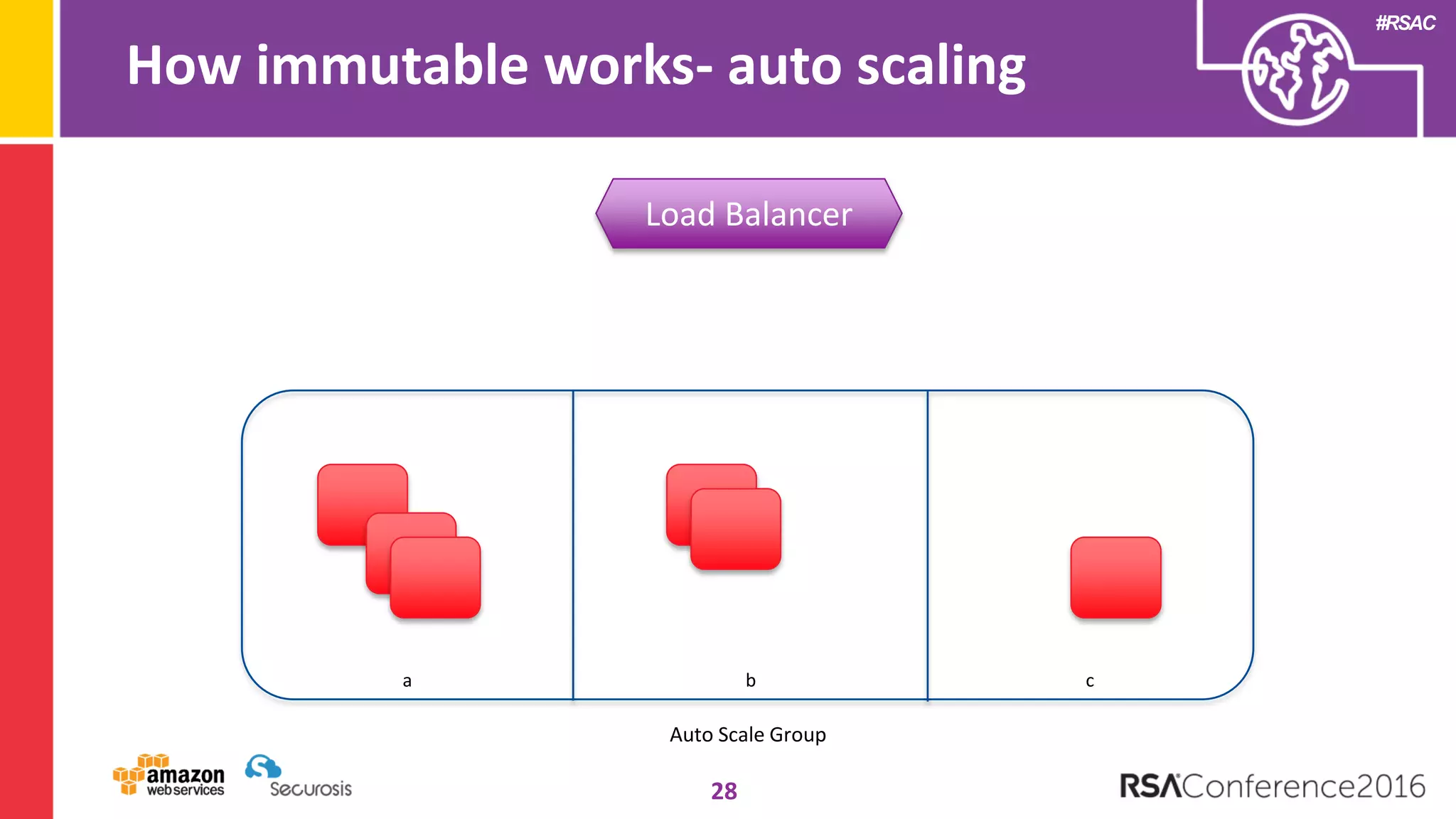
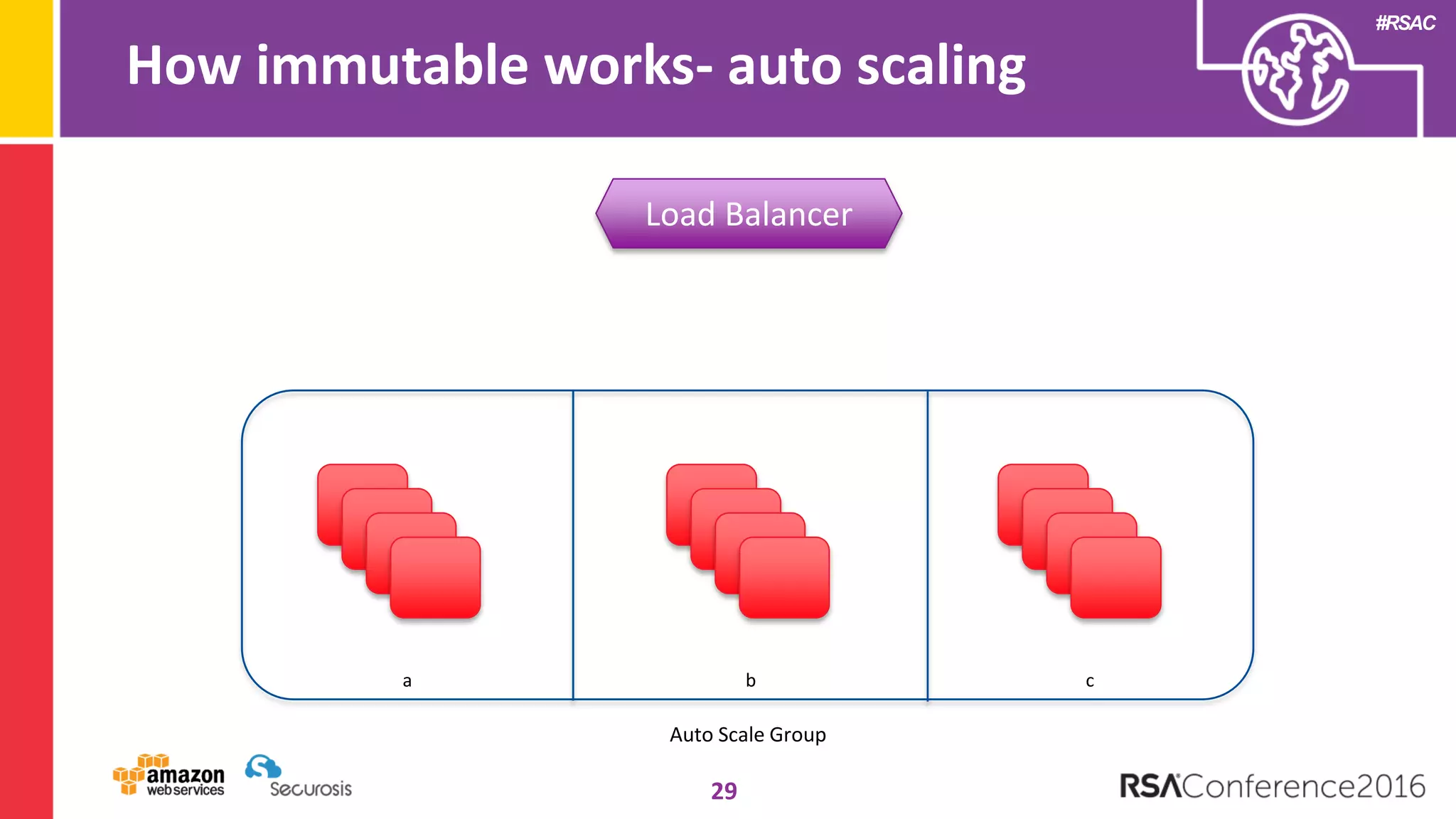
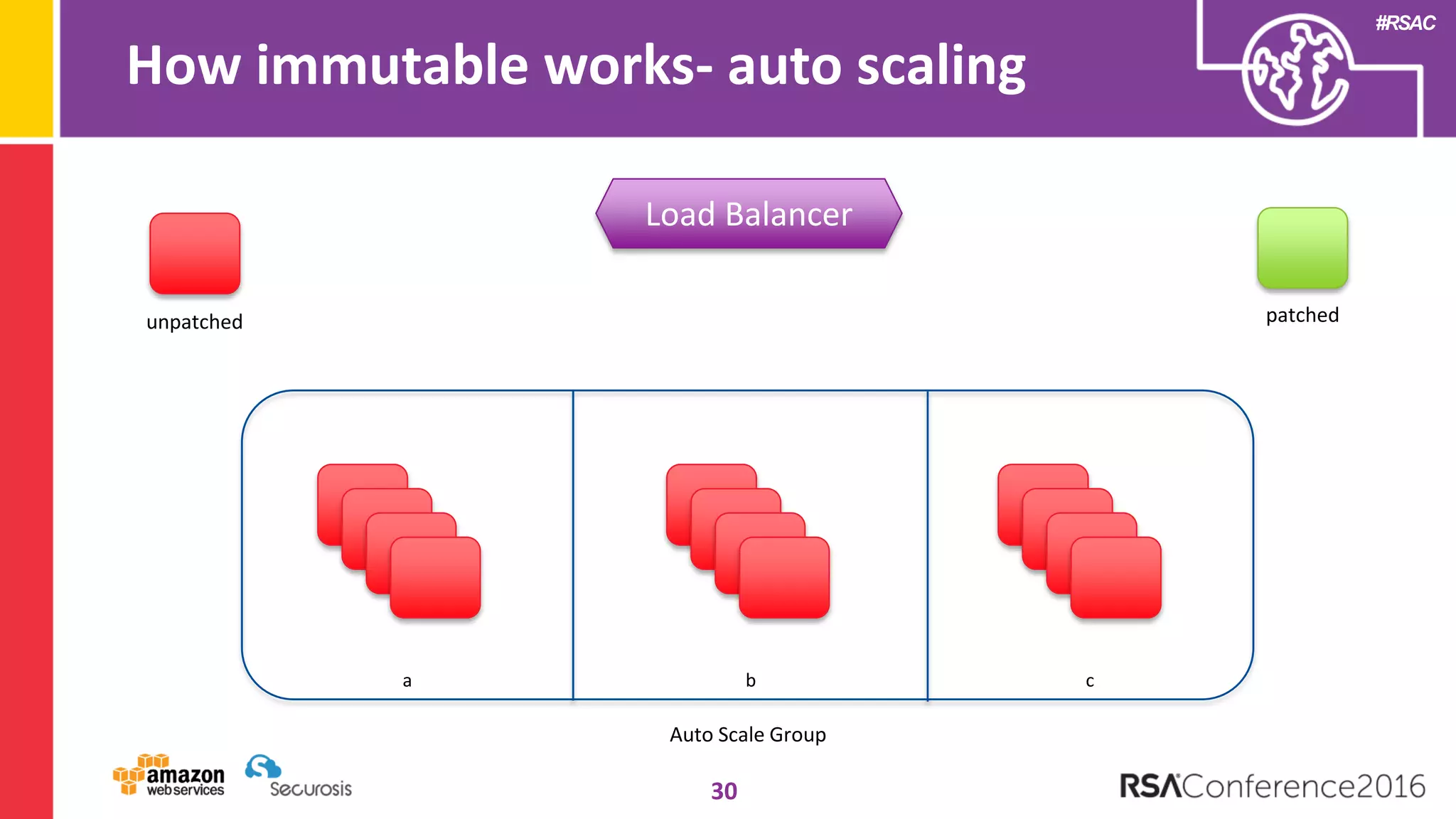
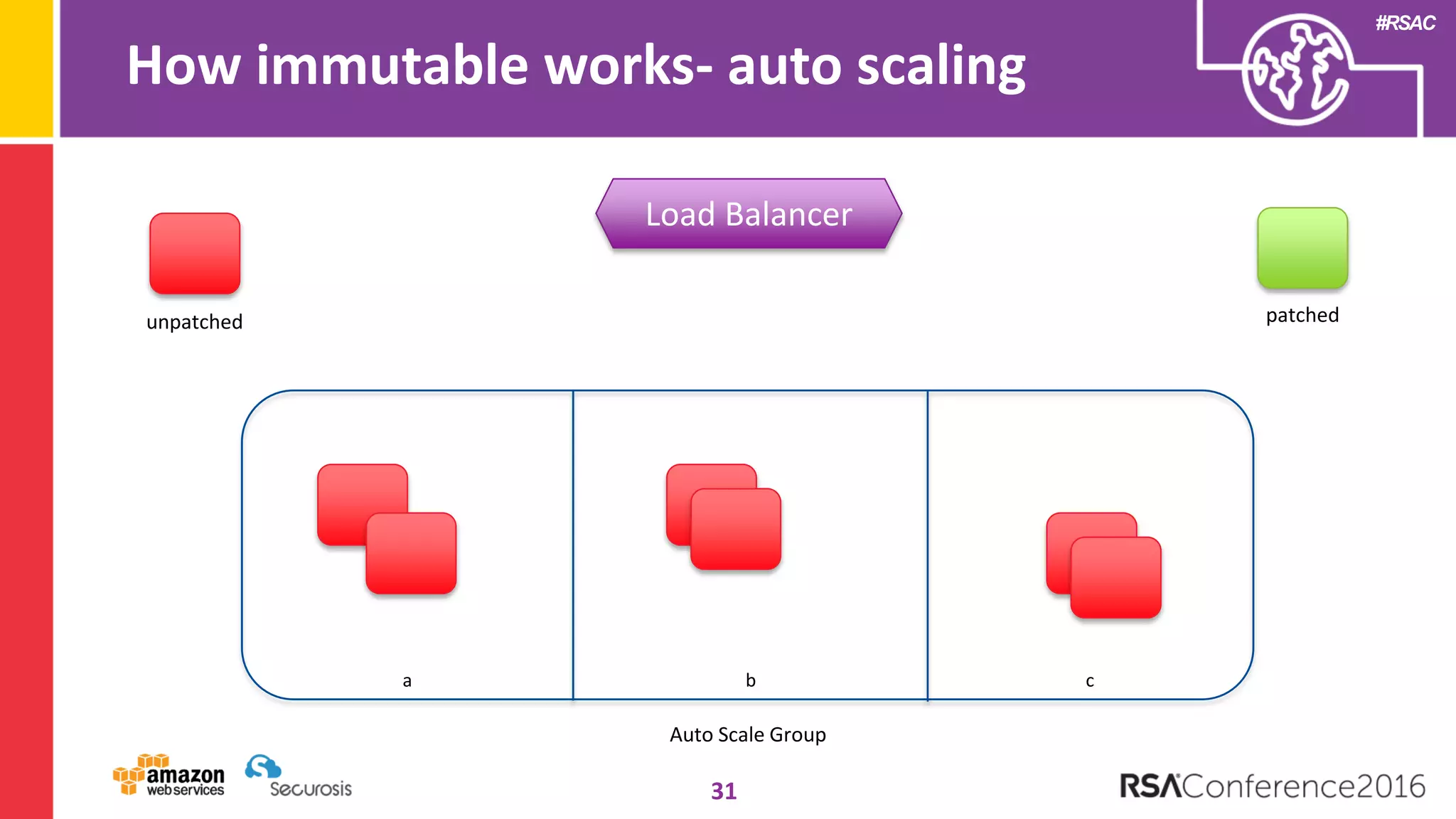
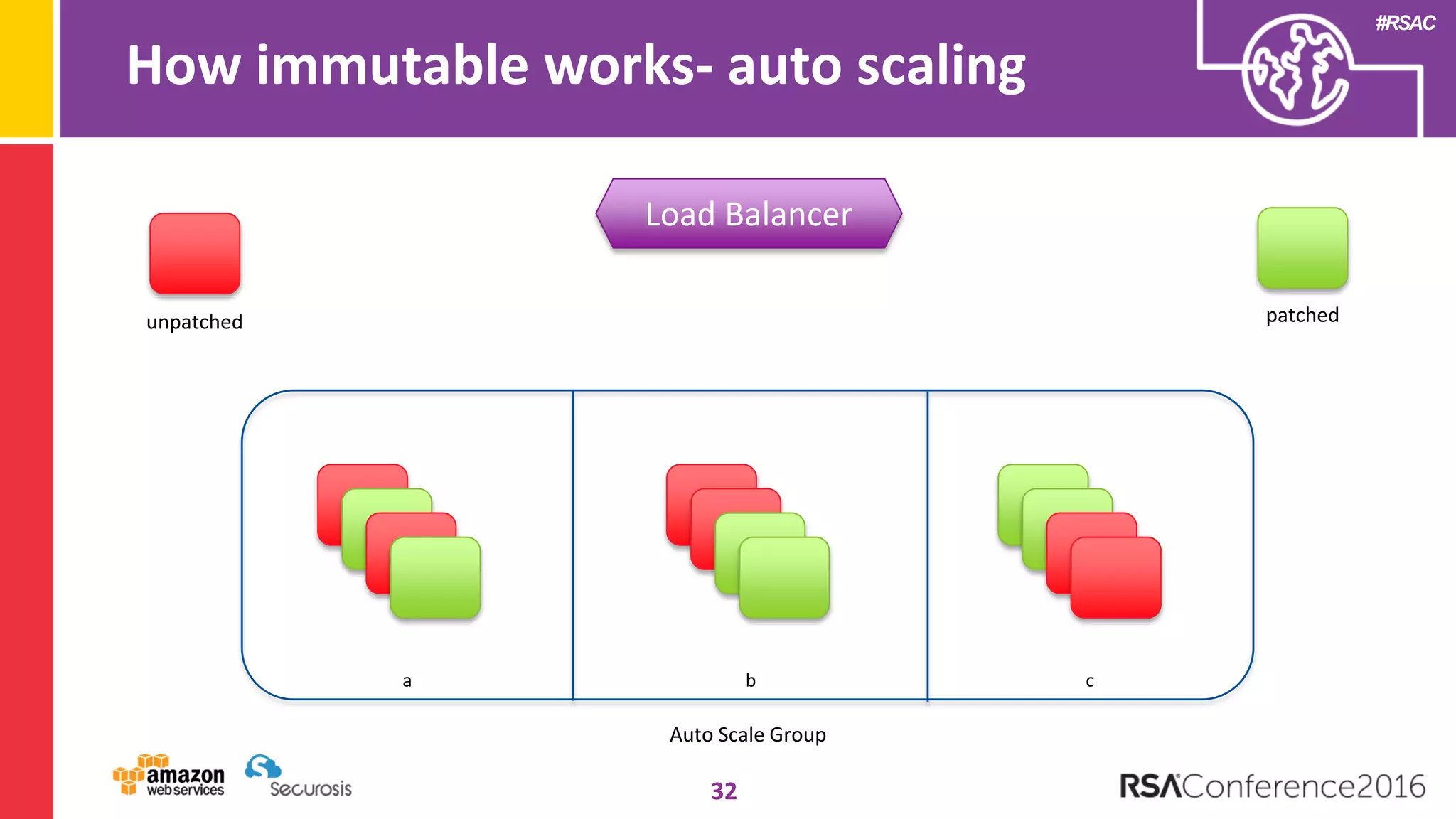
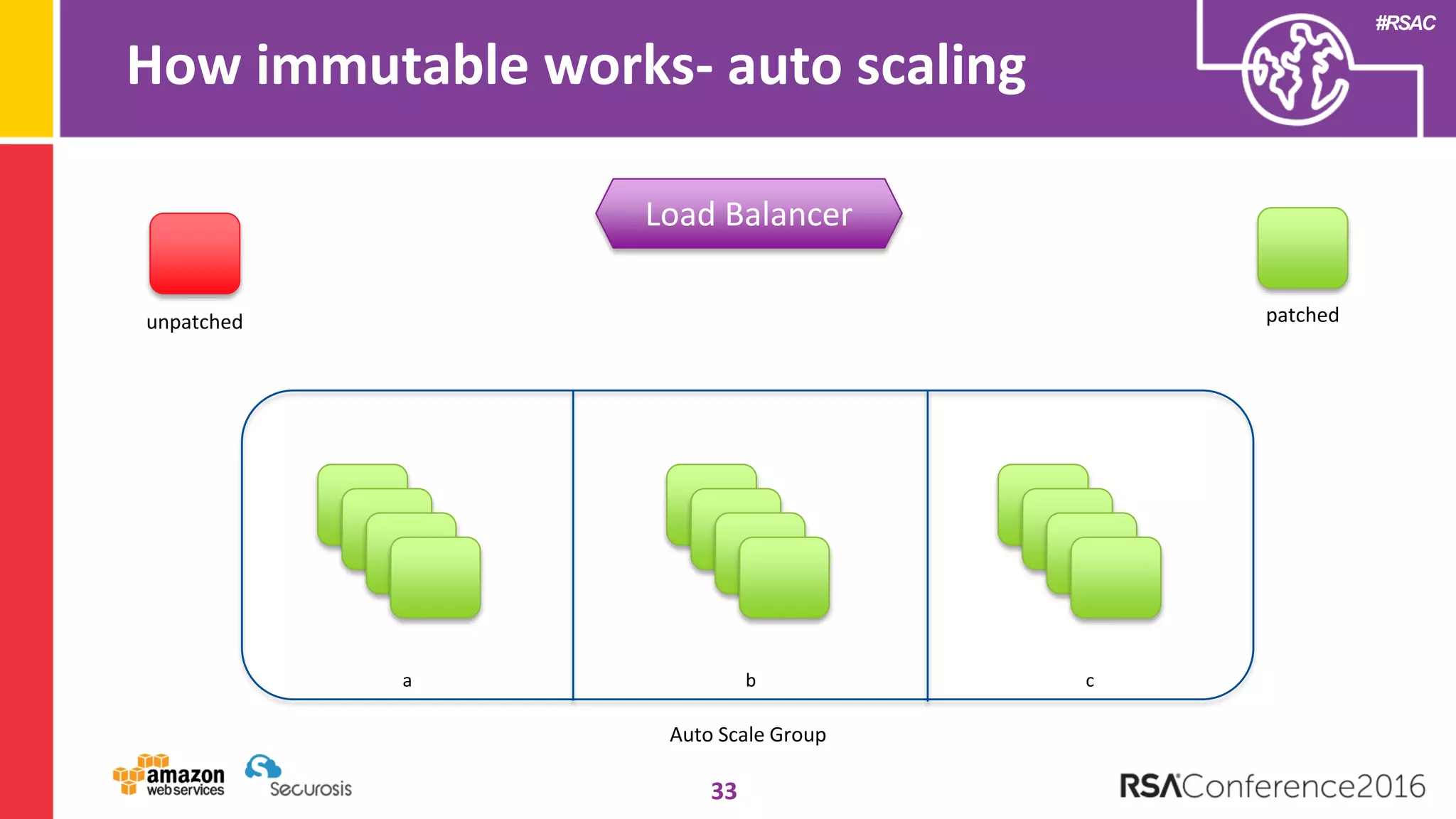
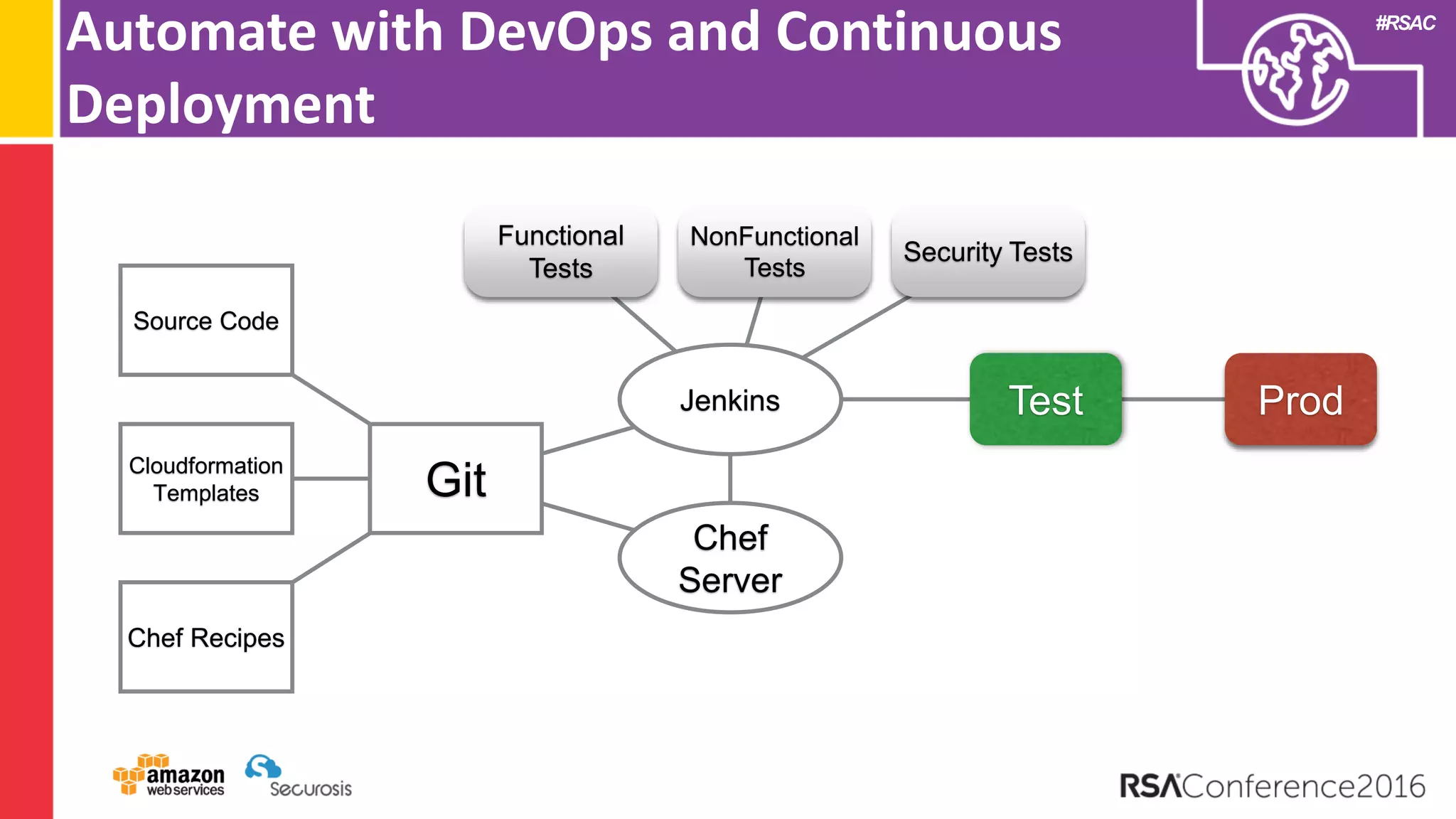
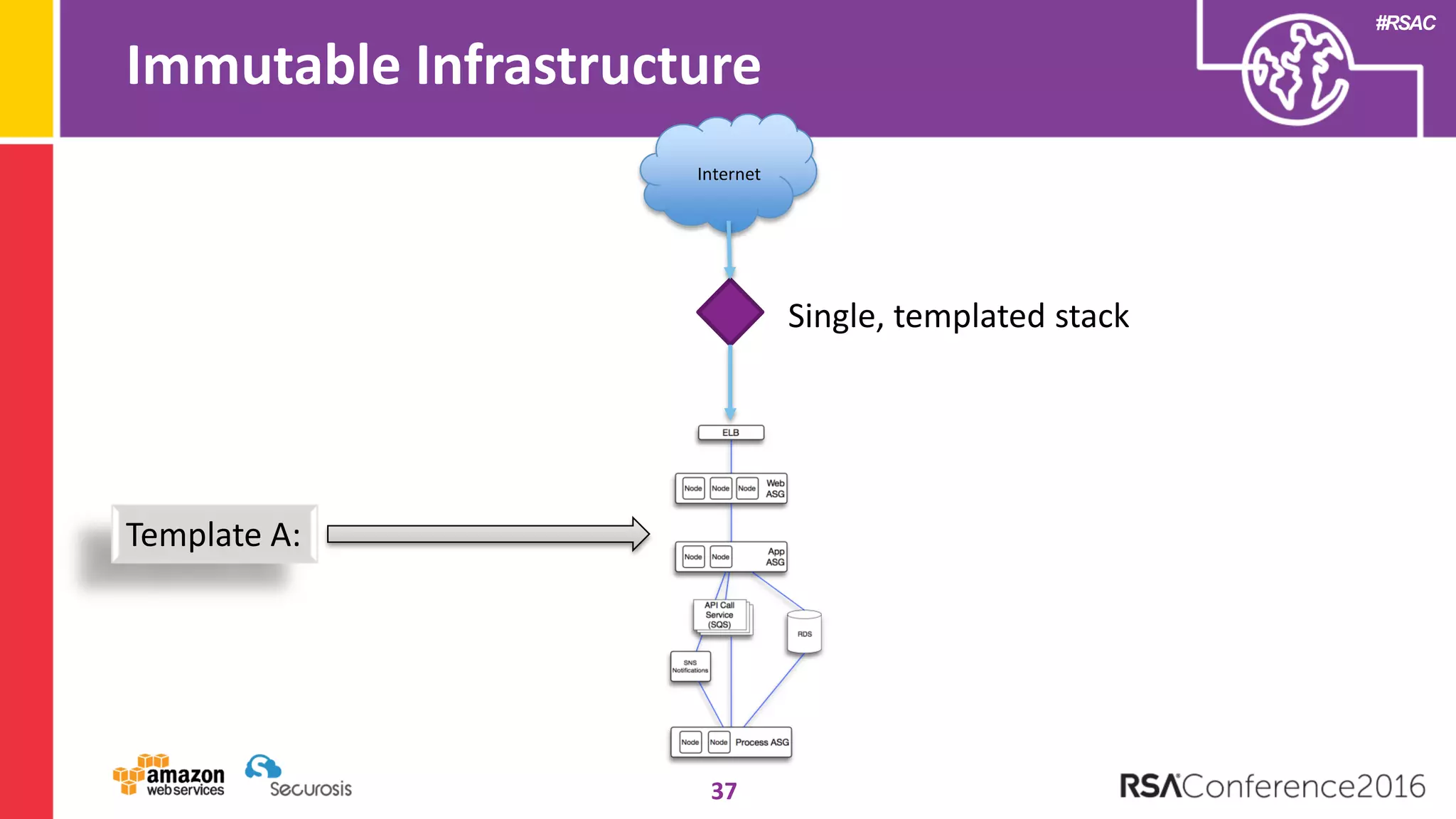
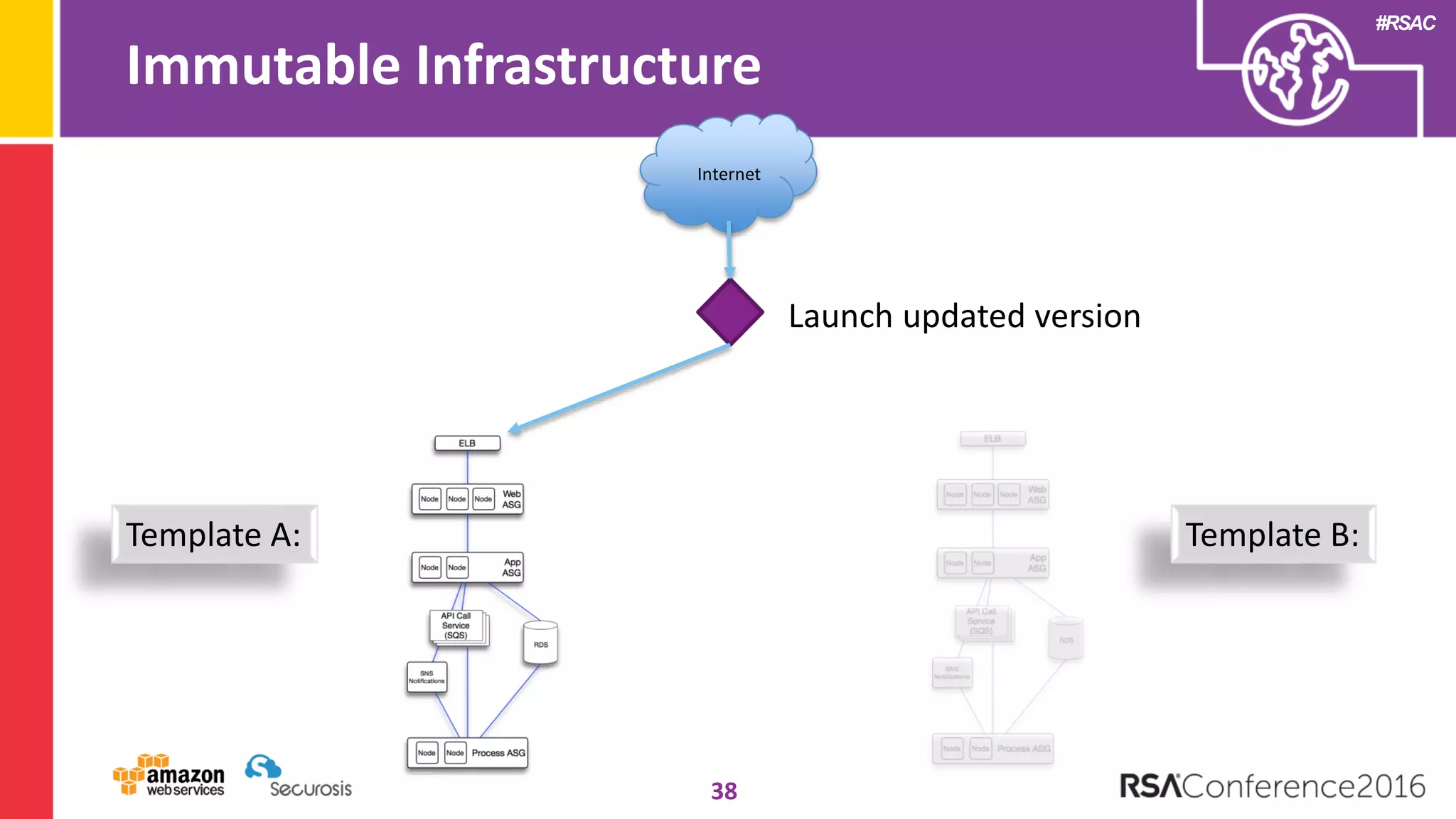
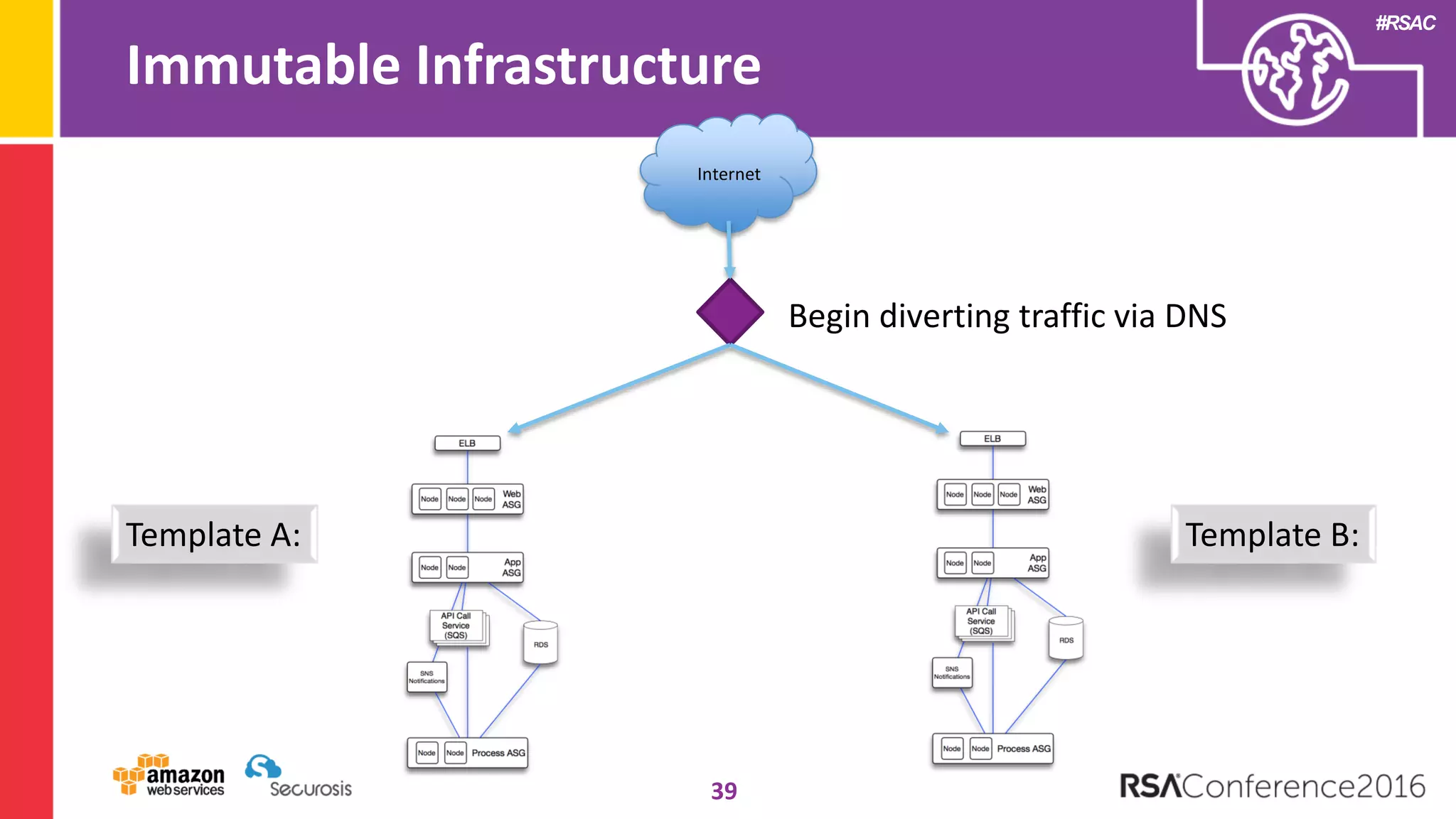
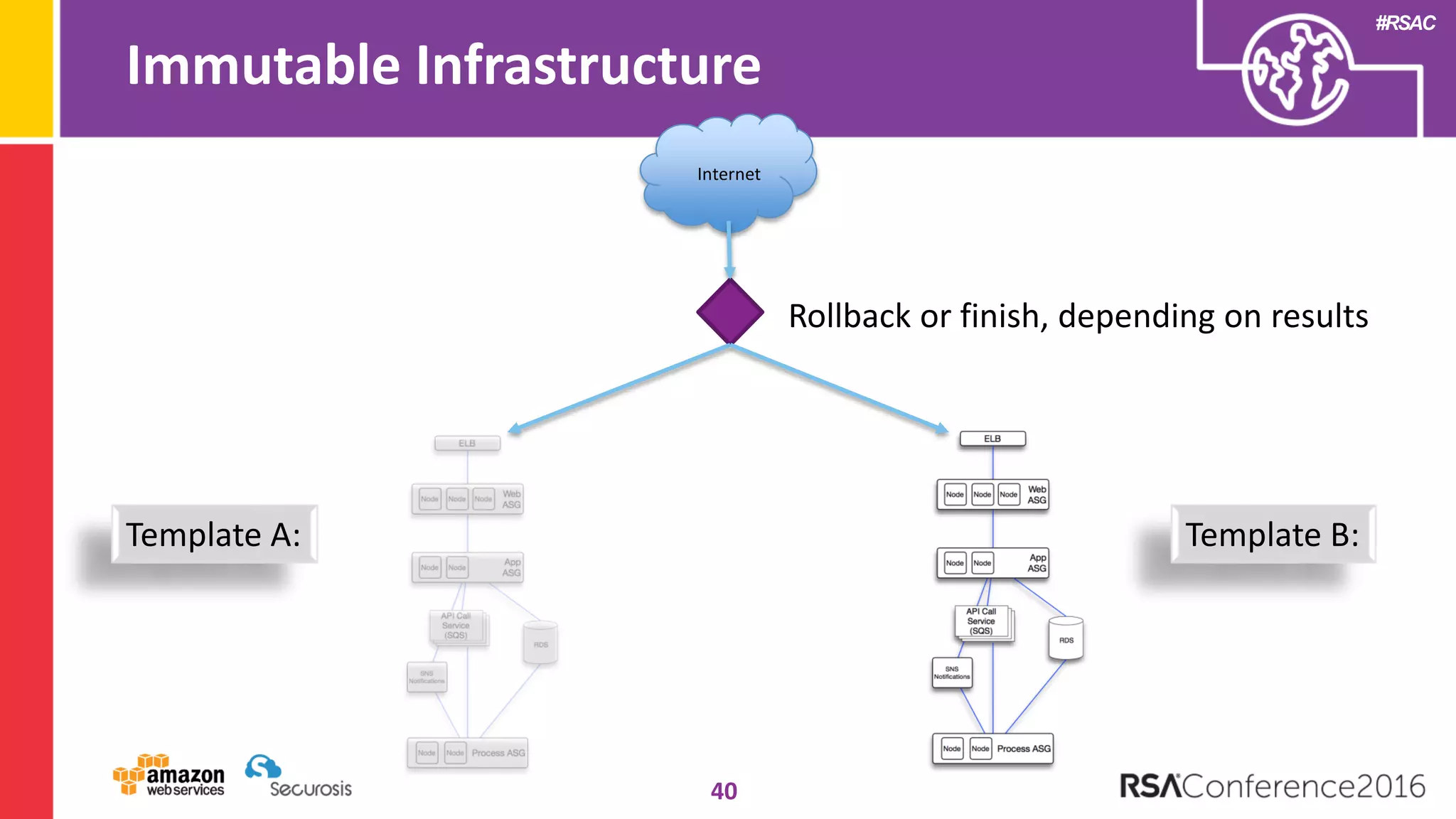
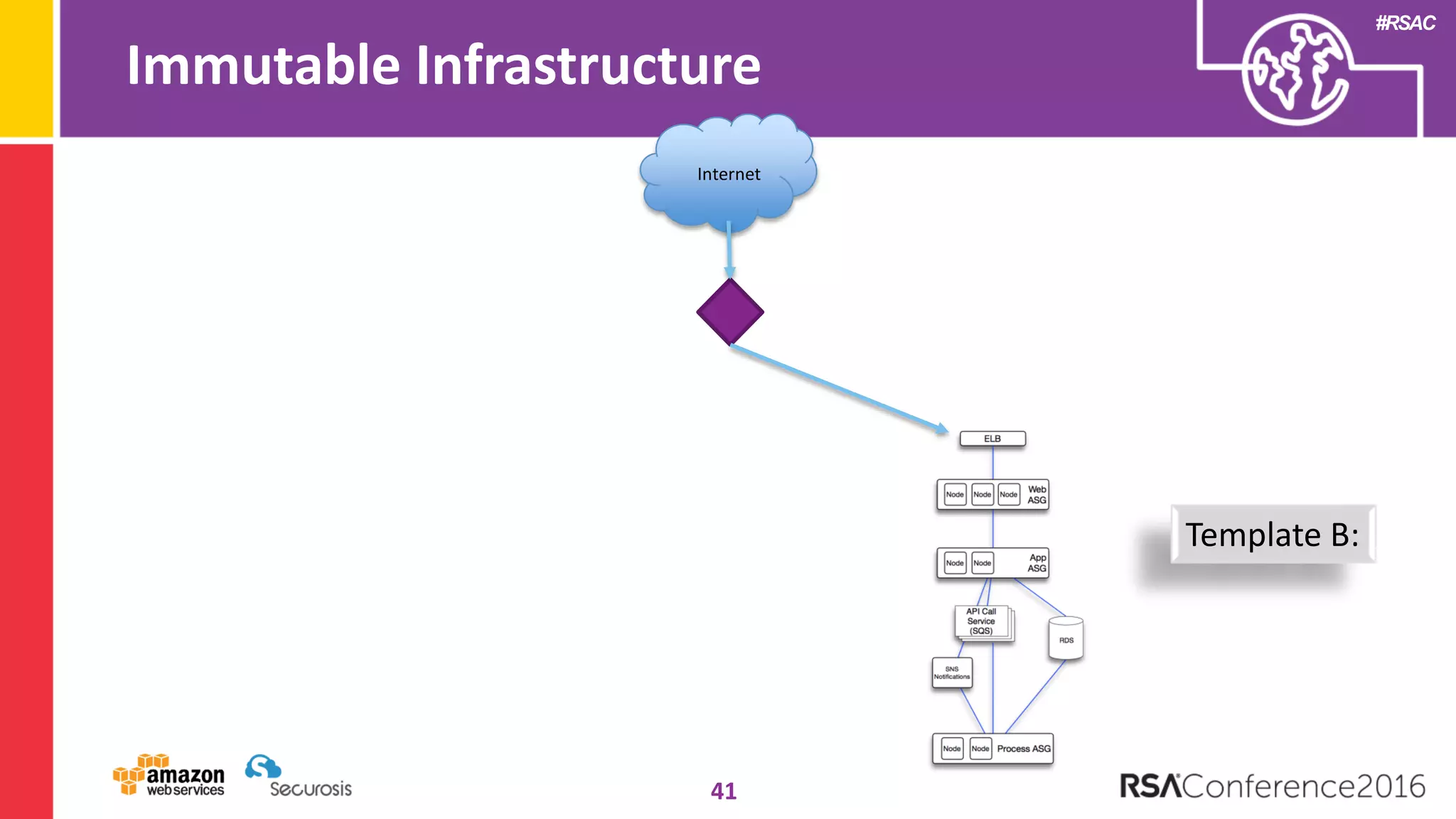
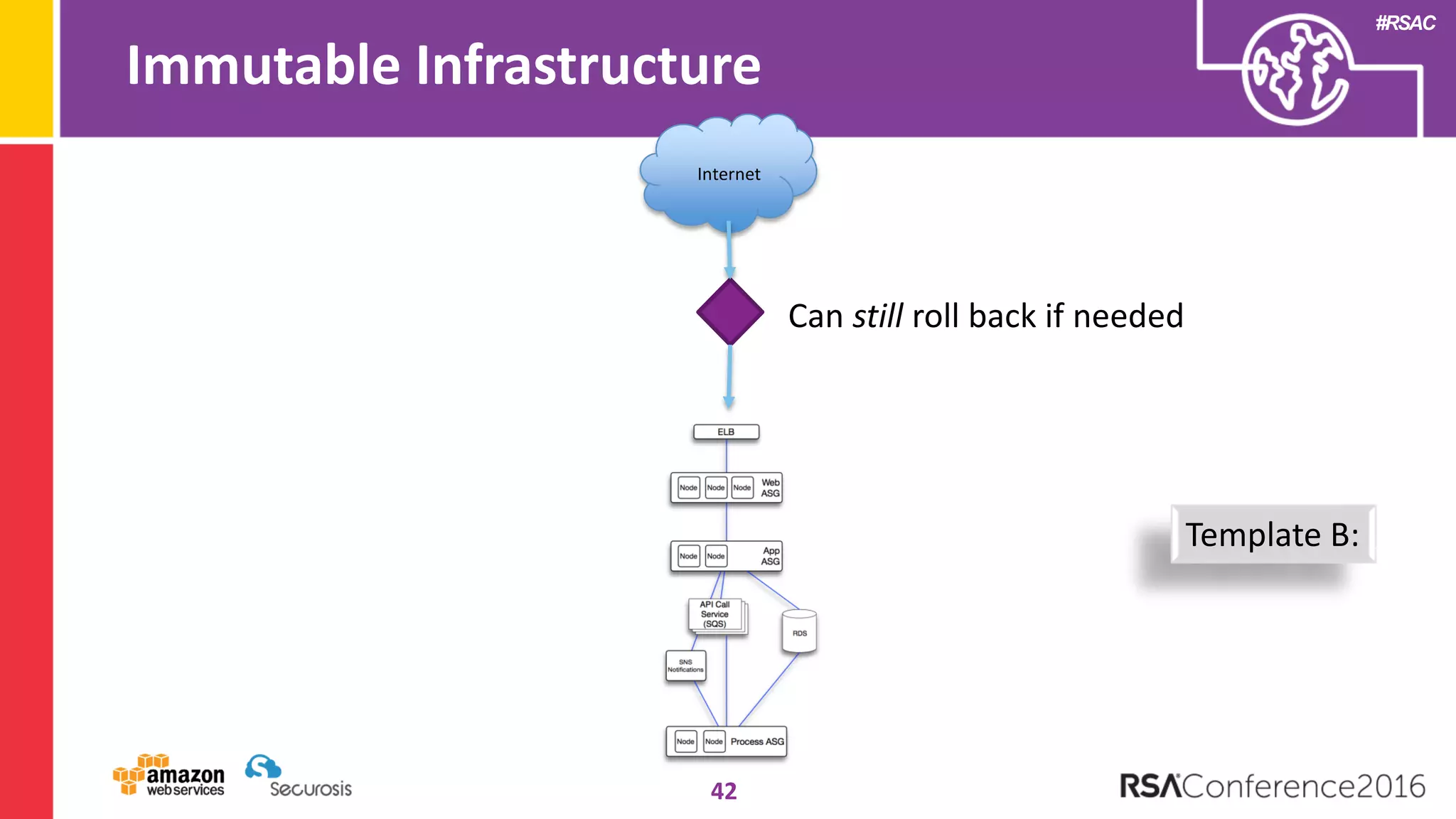
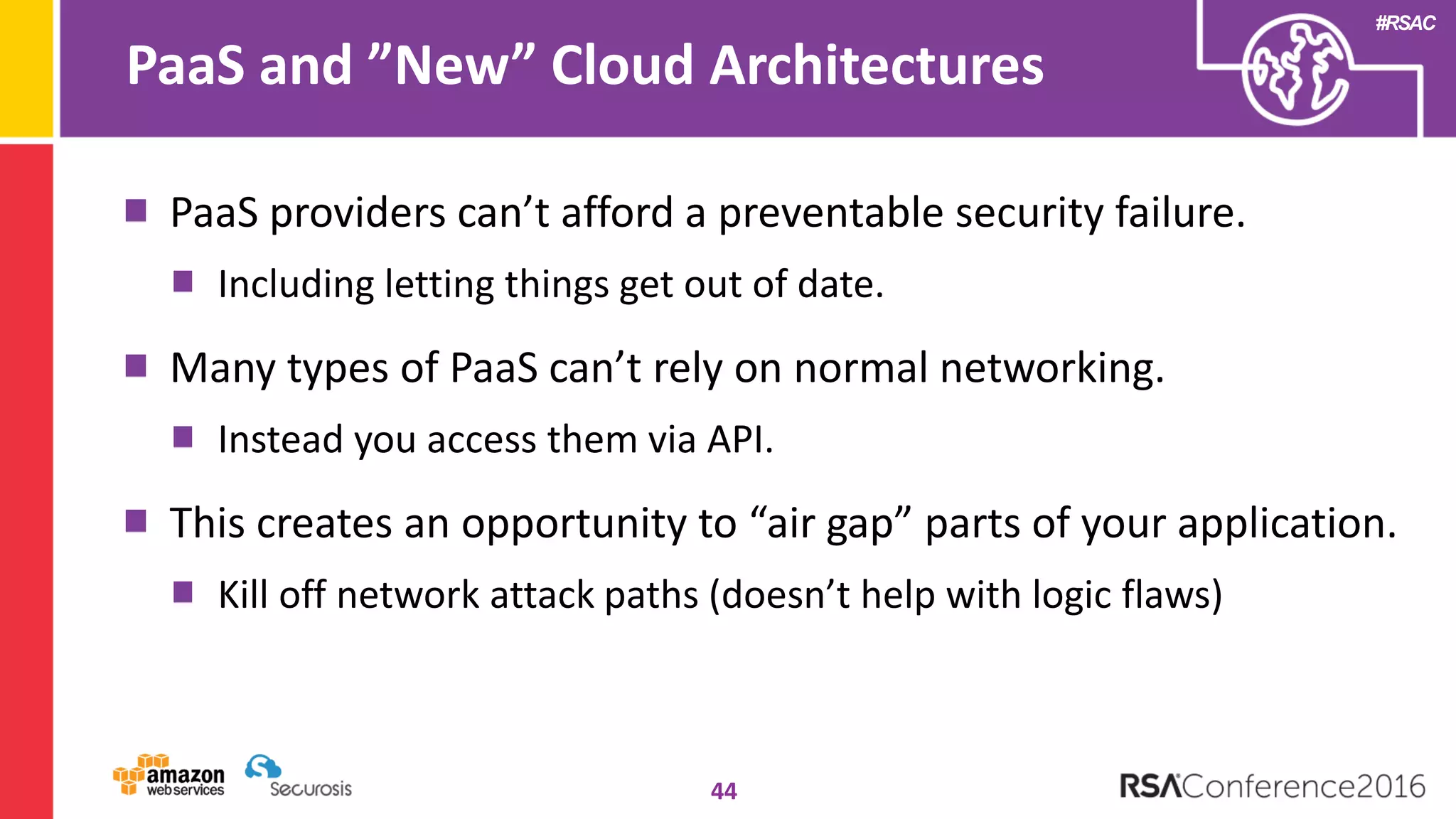
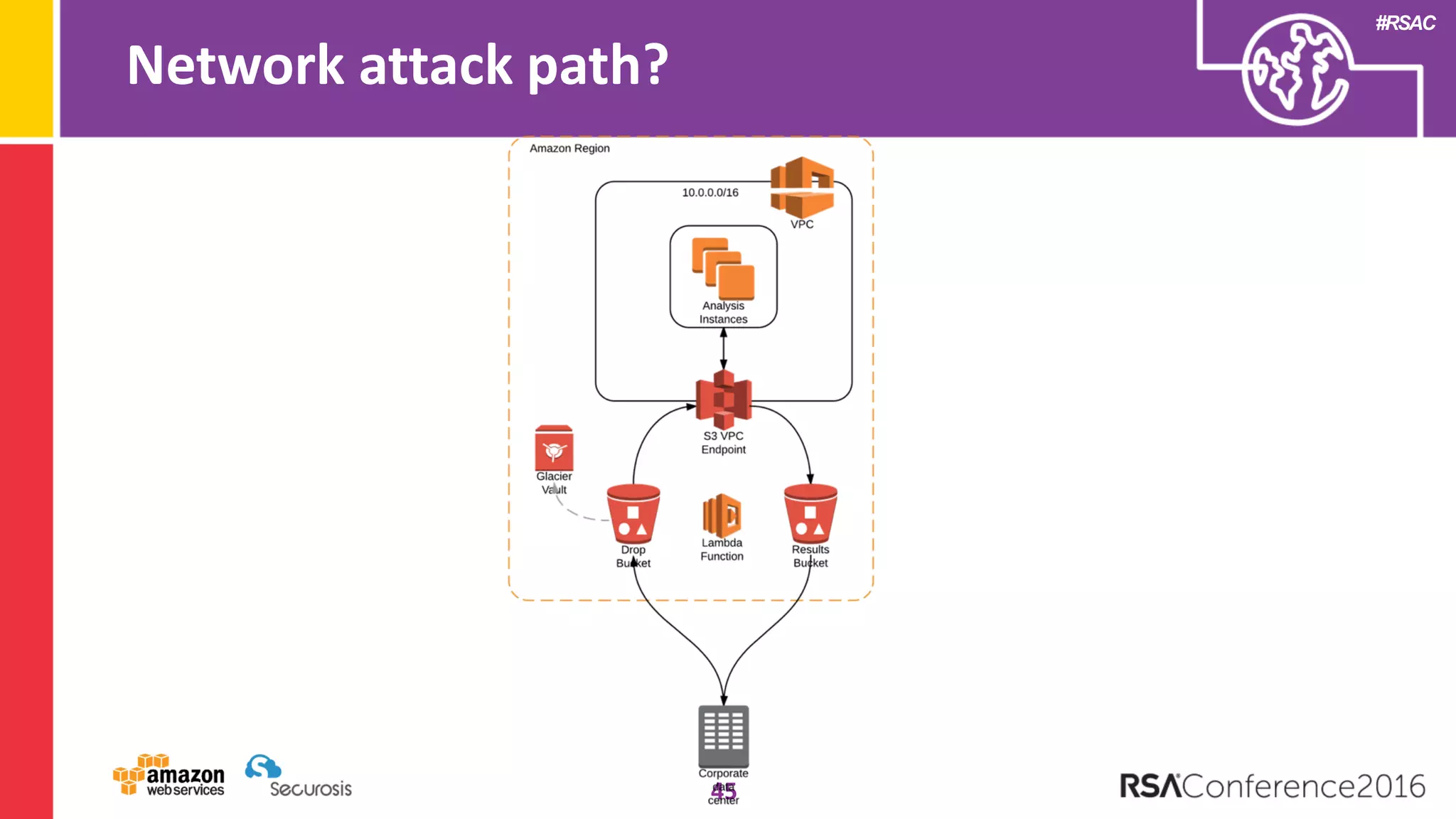
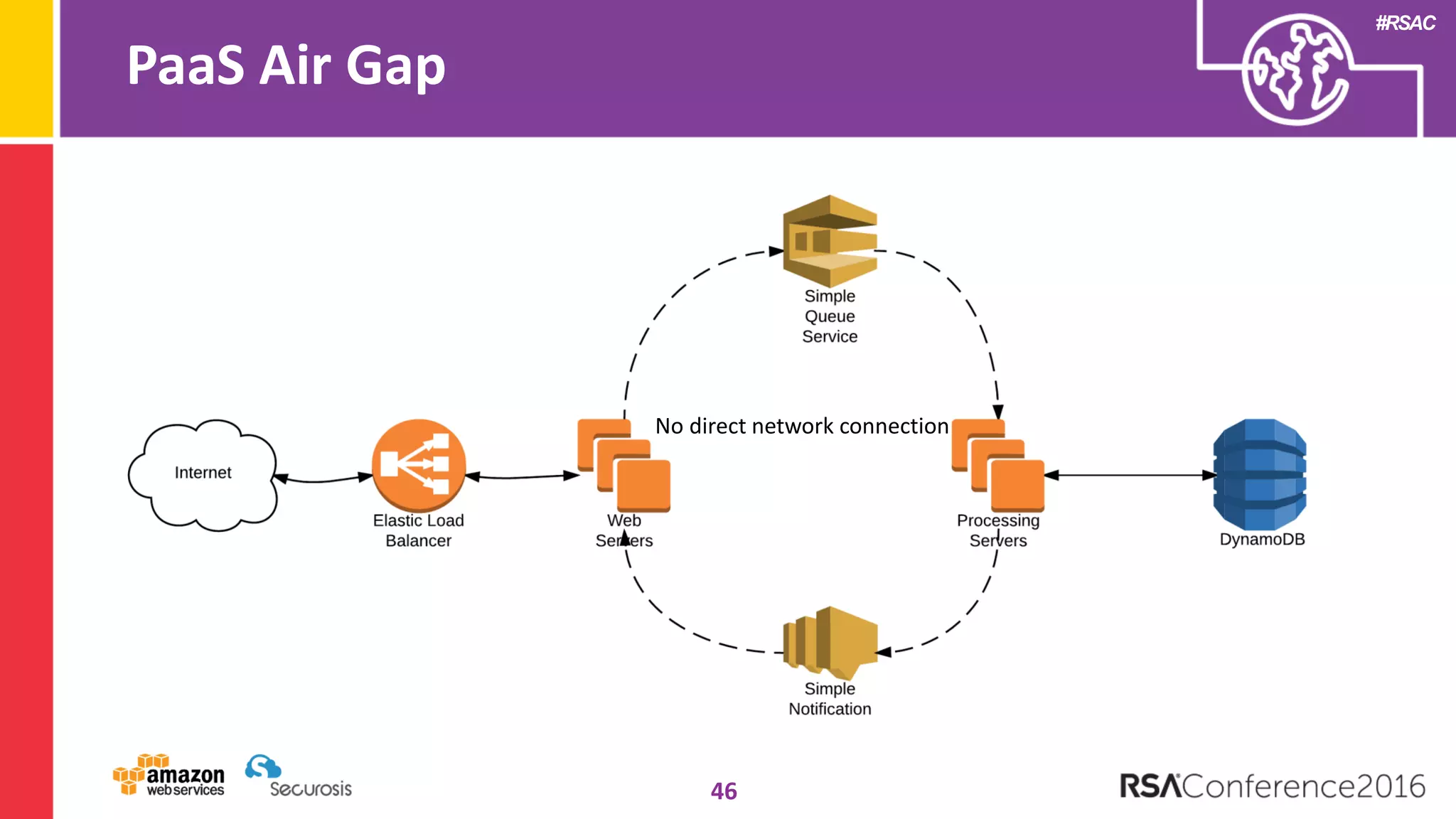
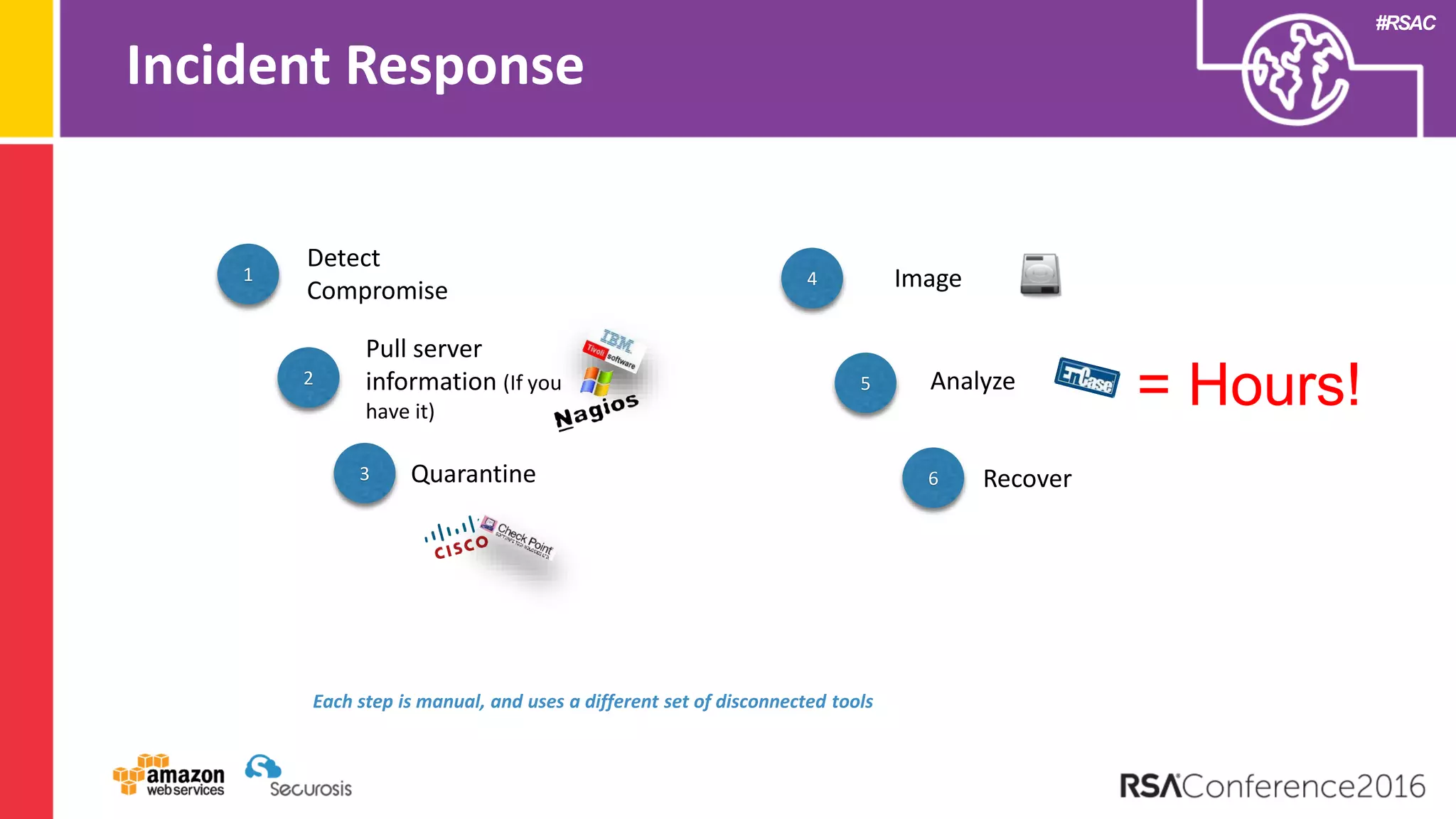
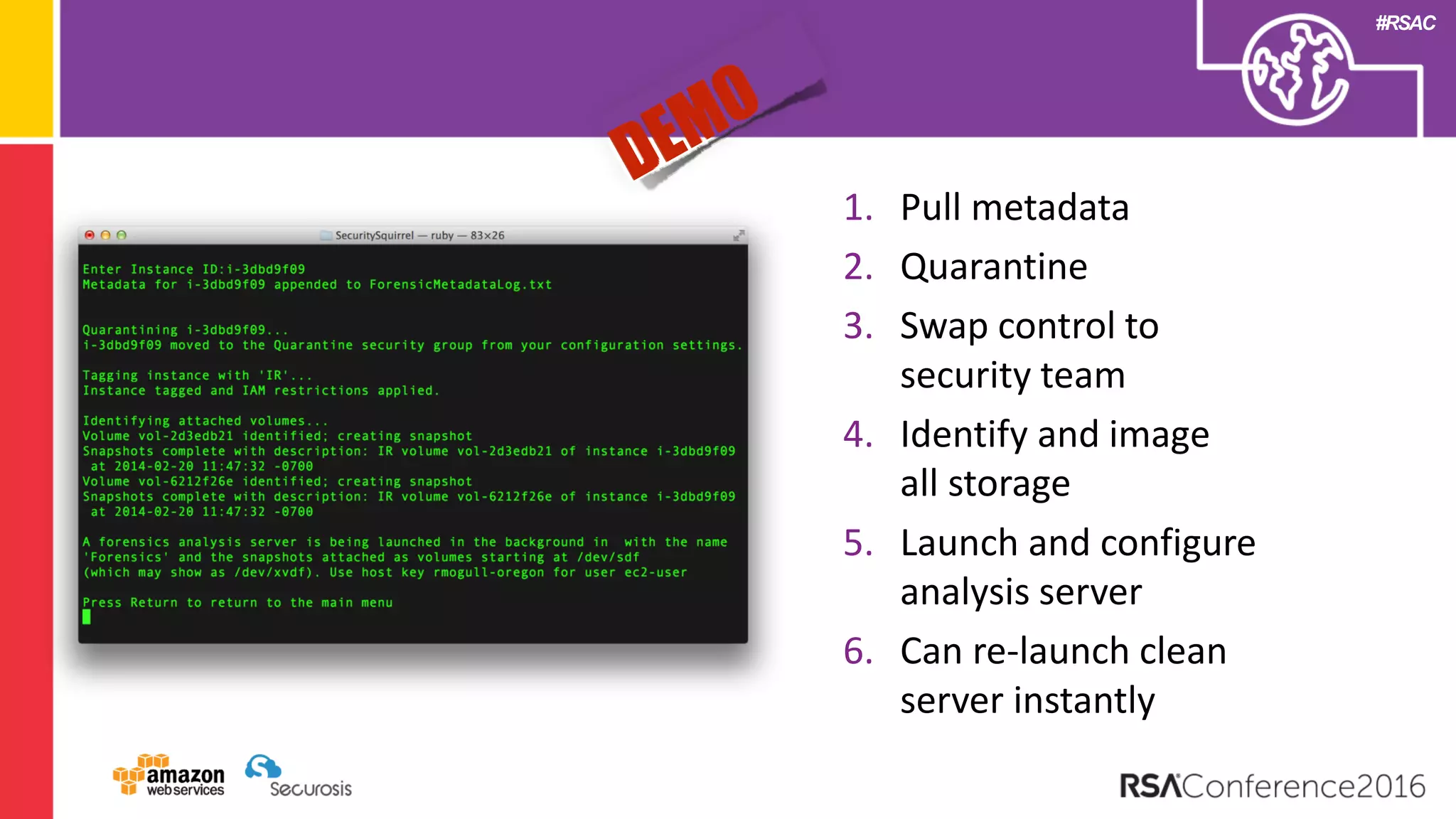
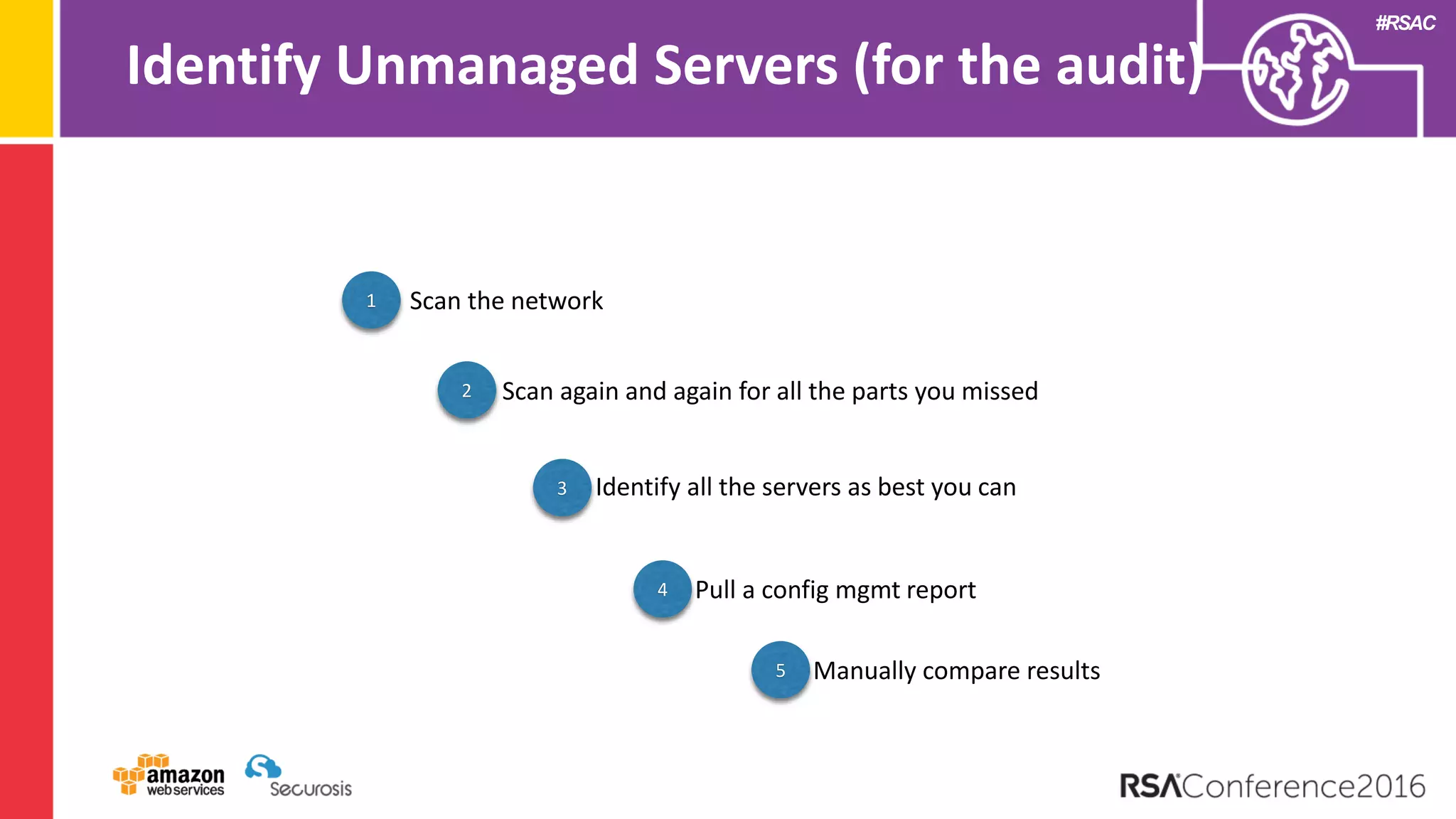
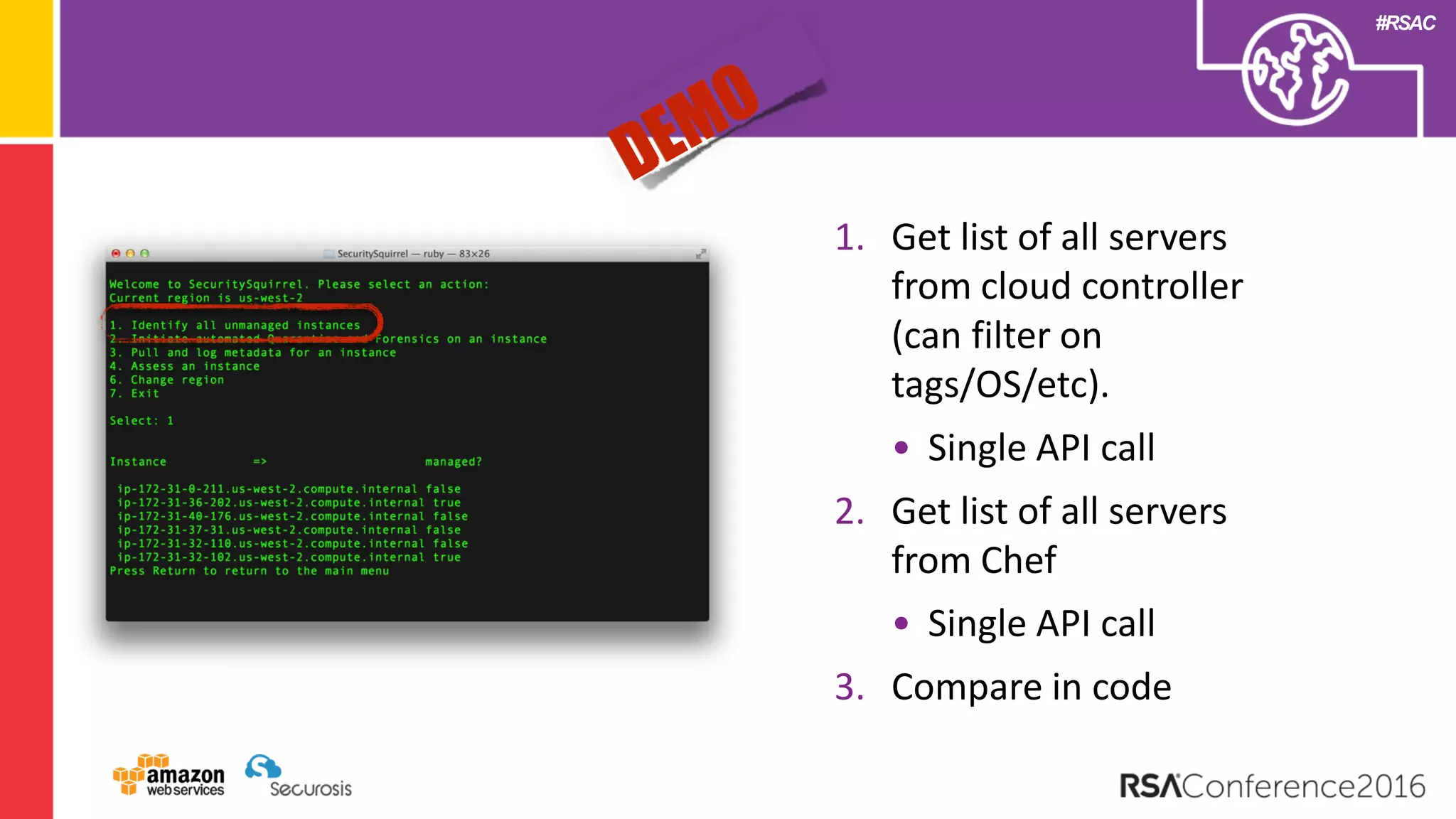
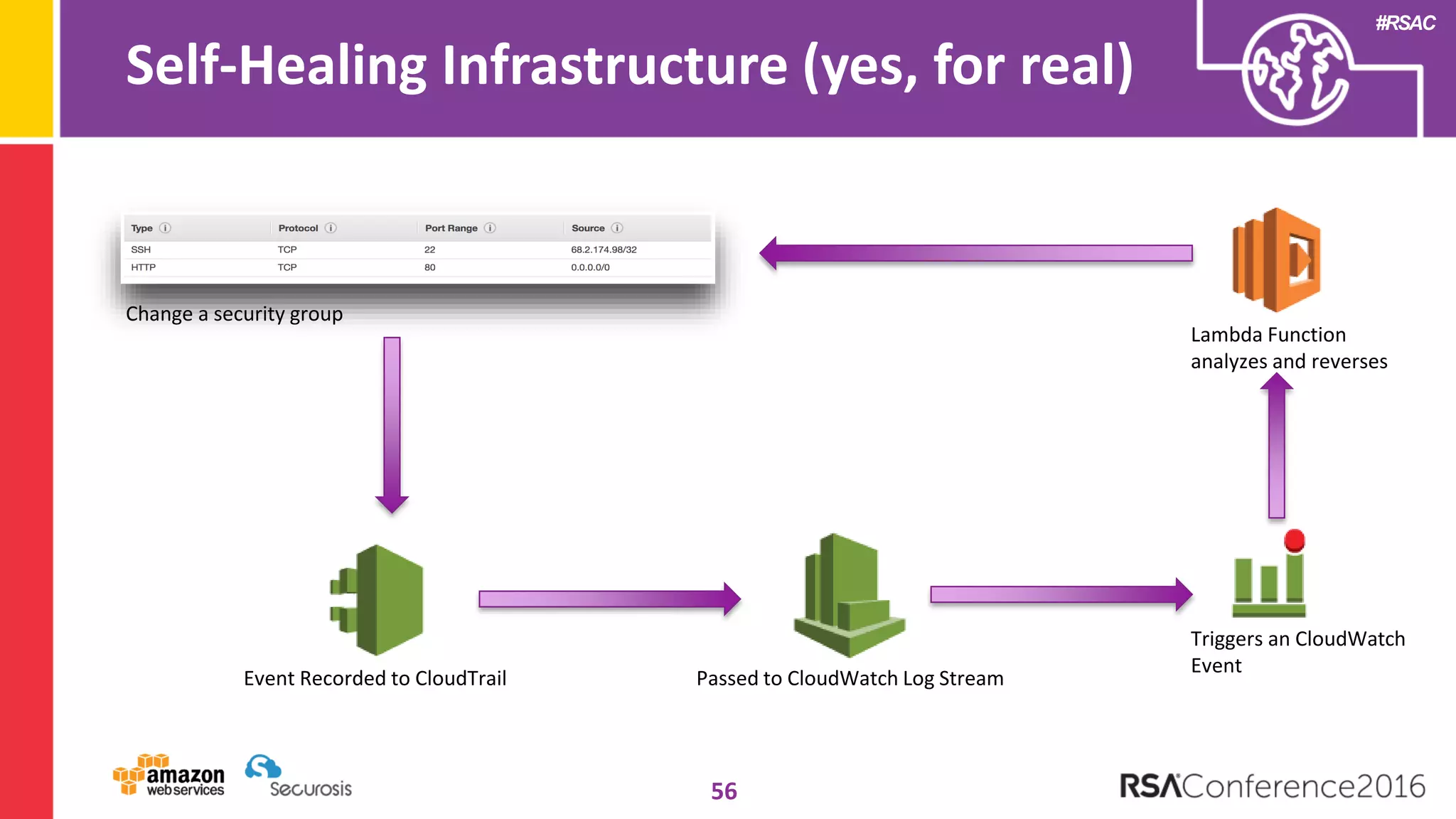
The document discusses the transition to cloud computing and its potential for enhanced security compared to traditional data centers, emphasizing the necessity of trusting cloud providers with sensitive data. Key topics include evolving security architecture, the significance of immutable infrastructure, and automation tools for incident response and security workflows in cloud environments. The presentation encourages collaboration between development, operations, and security teams to leverage cloud capabilities effectively.