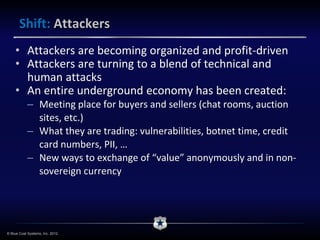
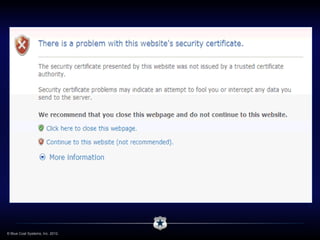
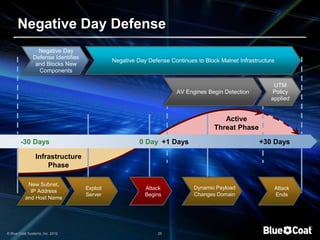
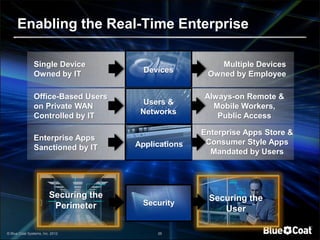
The document discusses the evolving landscape of cybersecurity, highlighting the organized and profit-driven nature of attackers who exploit both technical and human vulnerabilities. It emphasizes the challenges posed by the consumerization of technology and the complexity of modern threats that mislead users into making poor security decisions. Proactive measures to prevent harmful user behavior are essential for an effective security strategy.