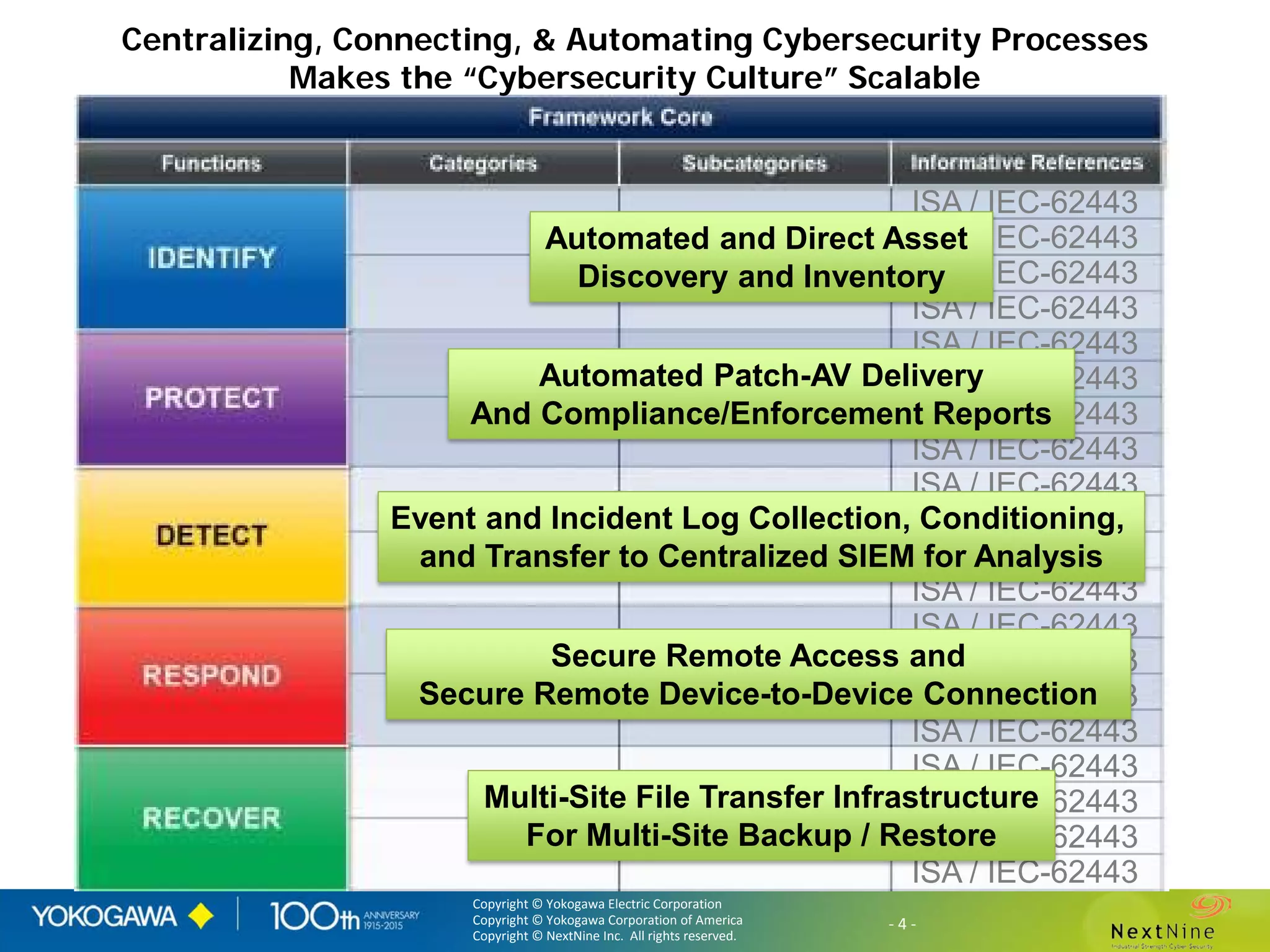
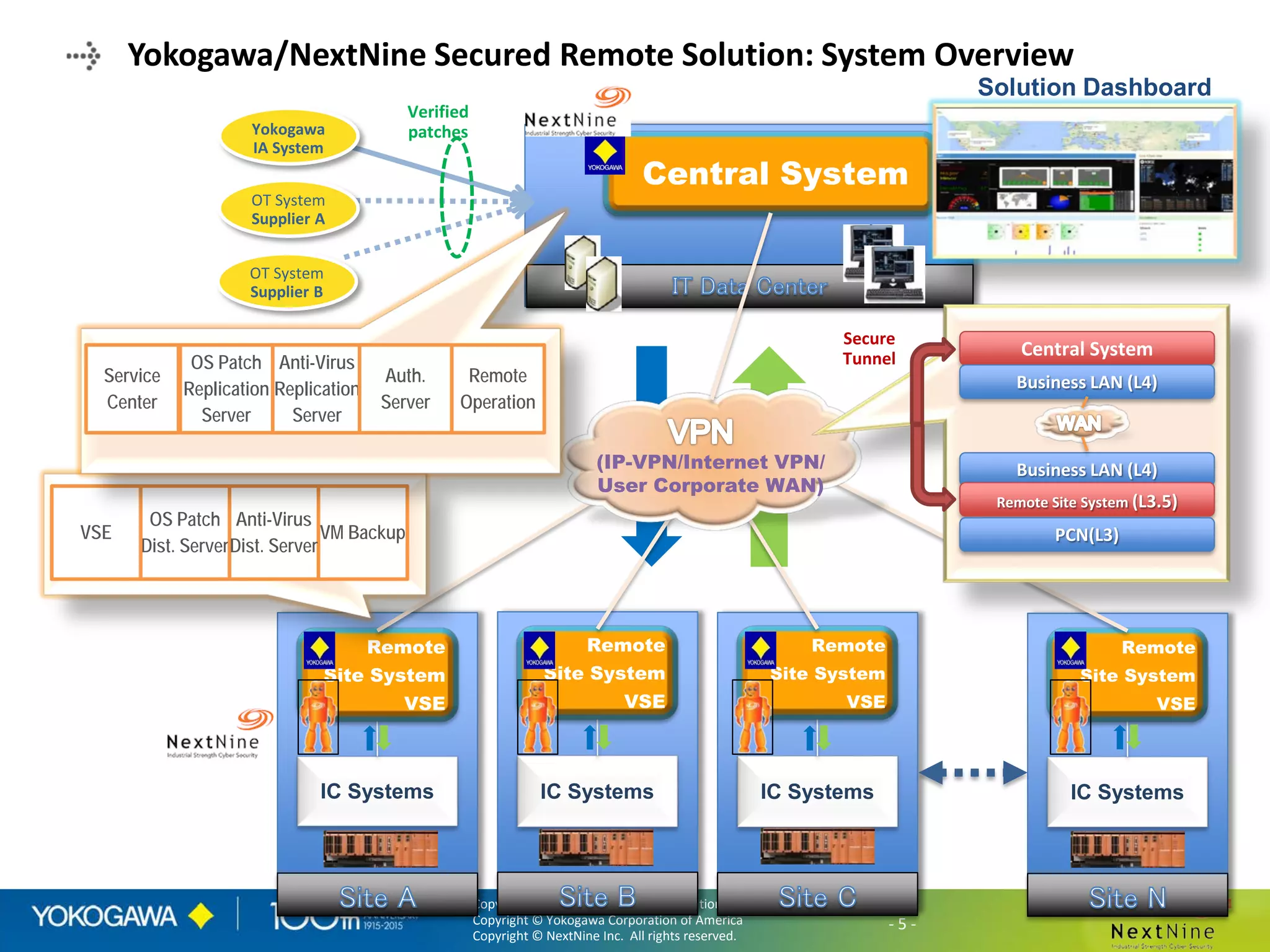
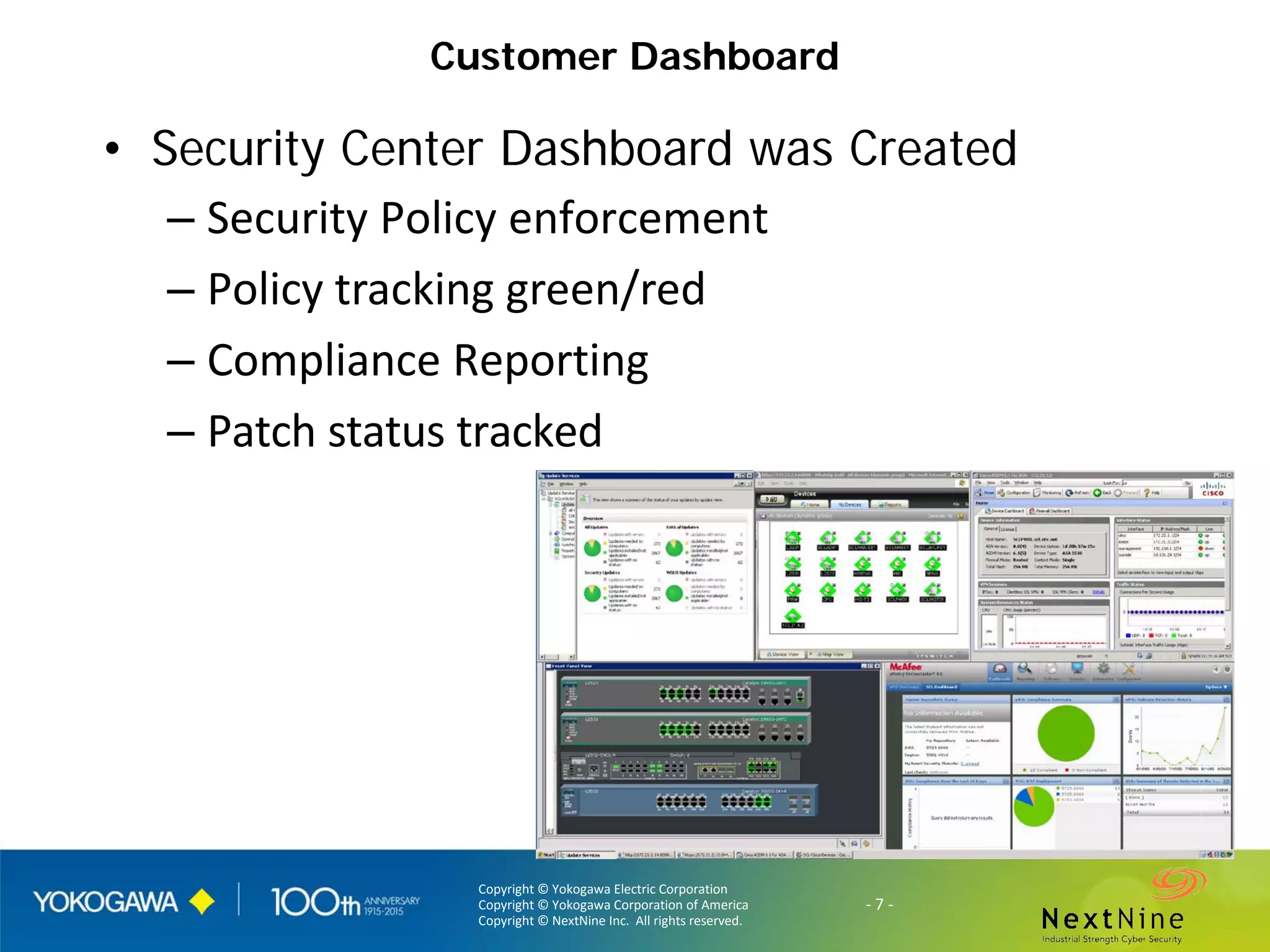
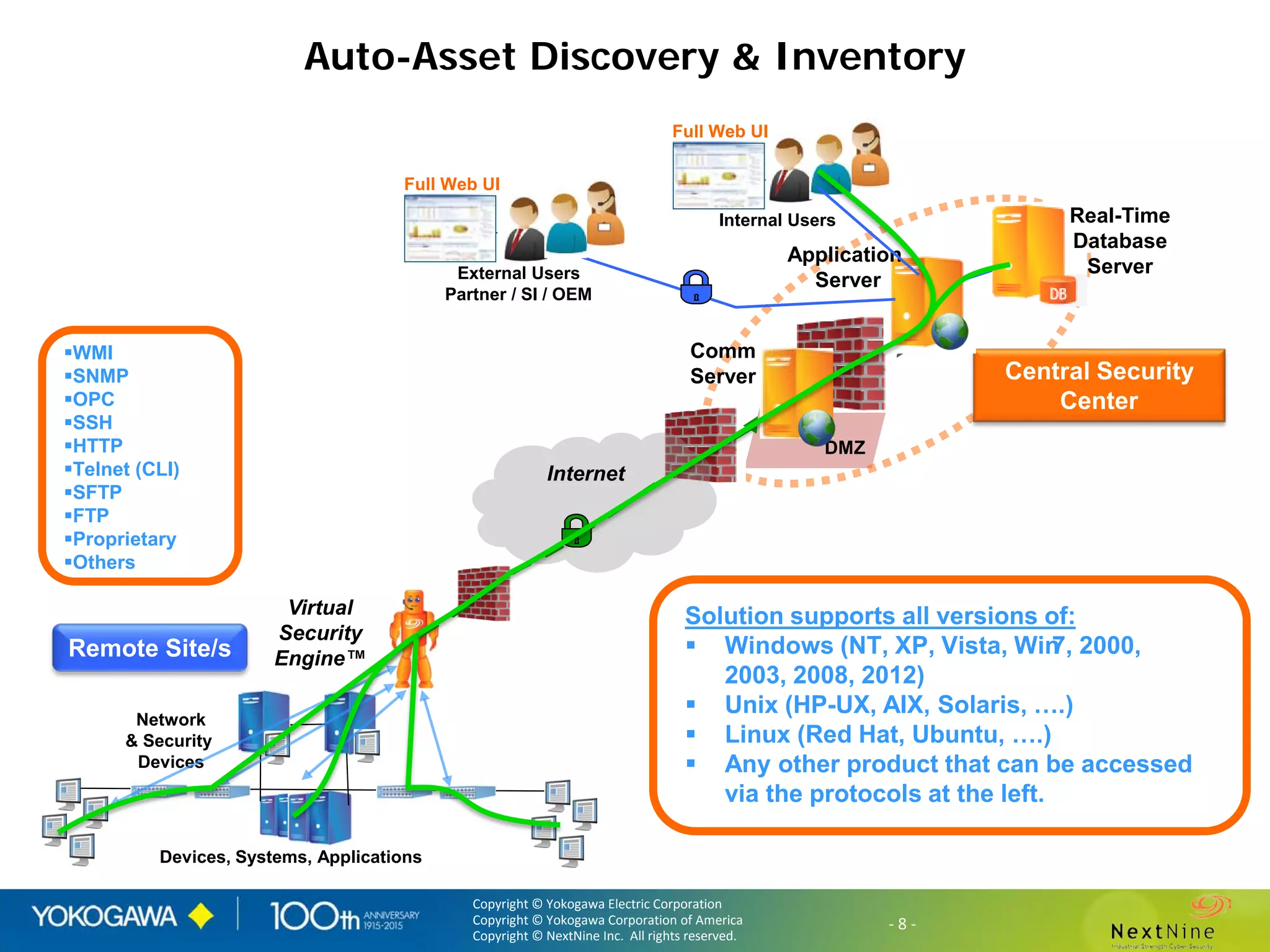
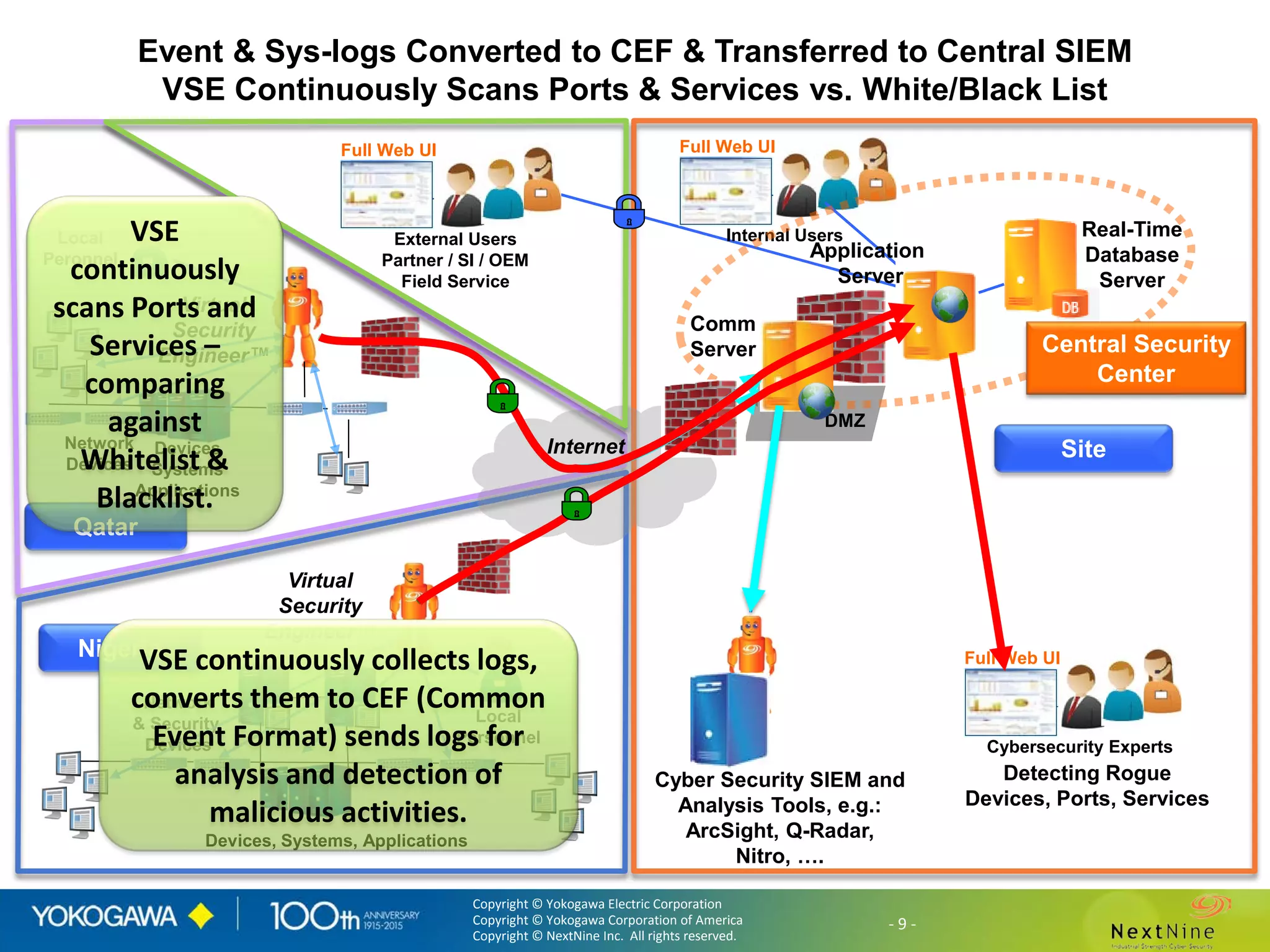
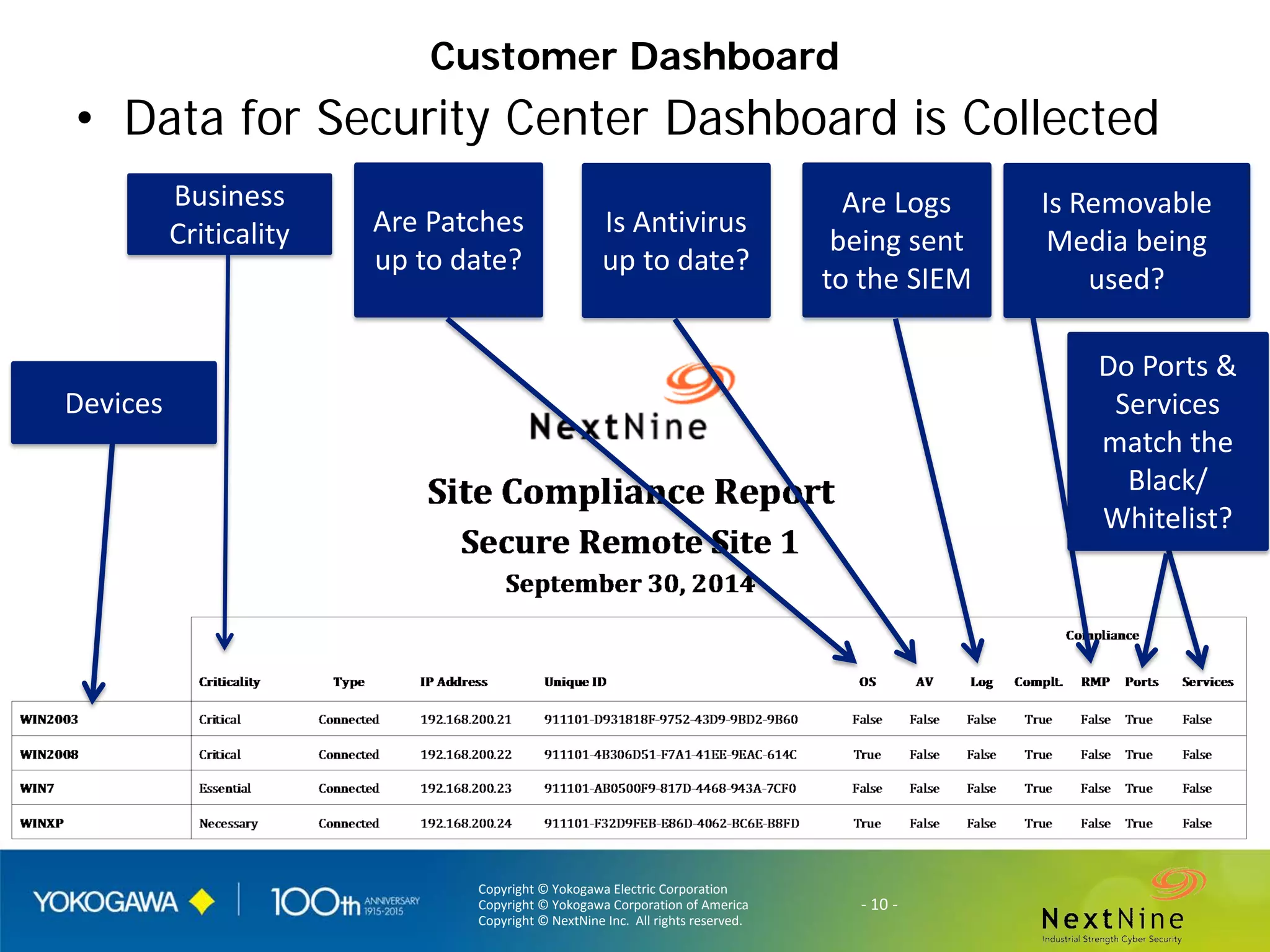
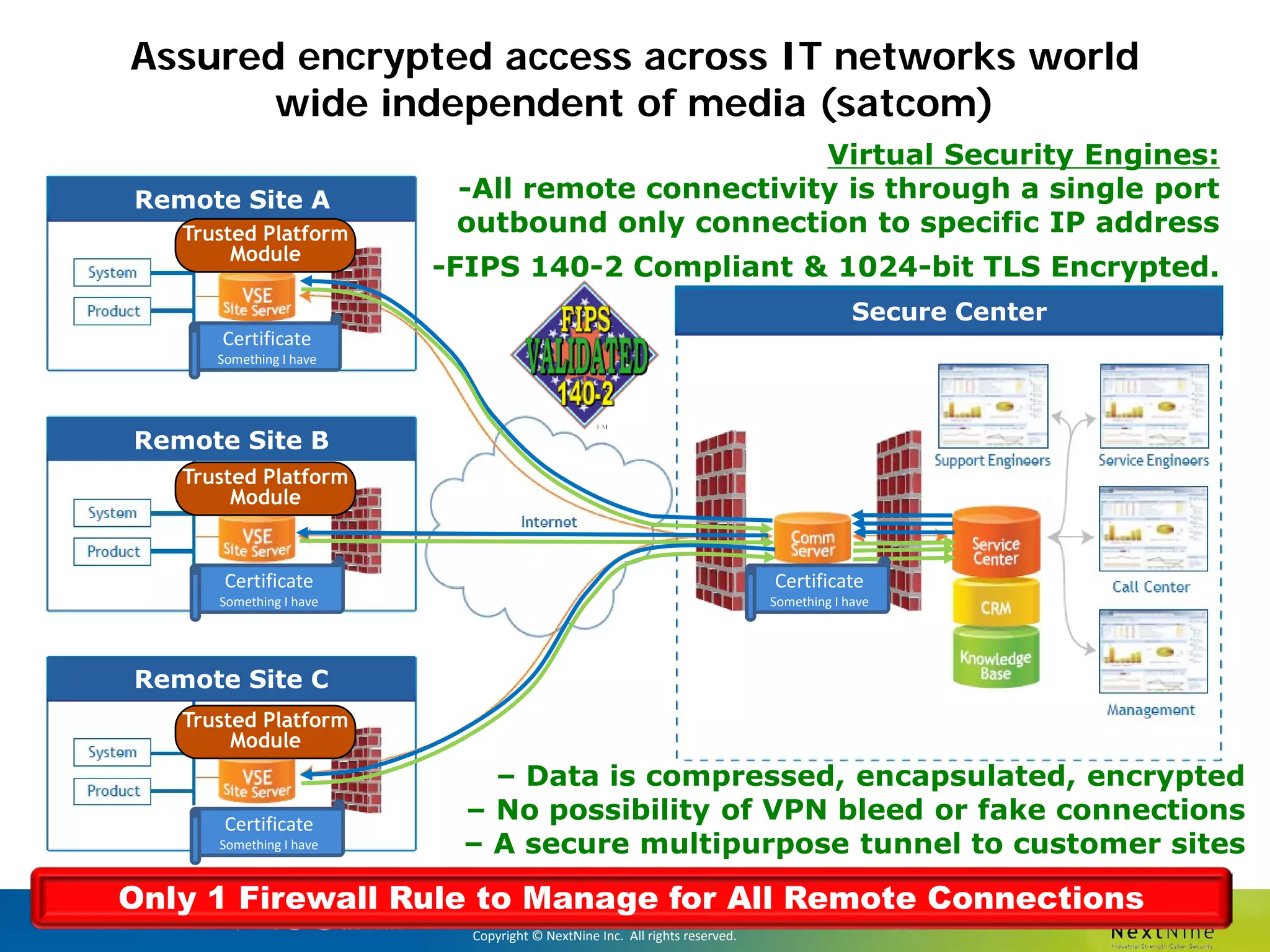
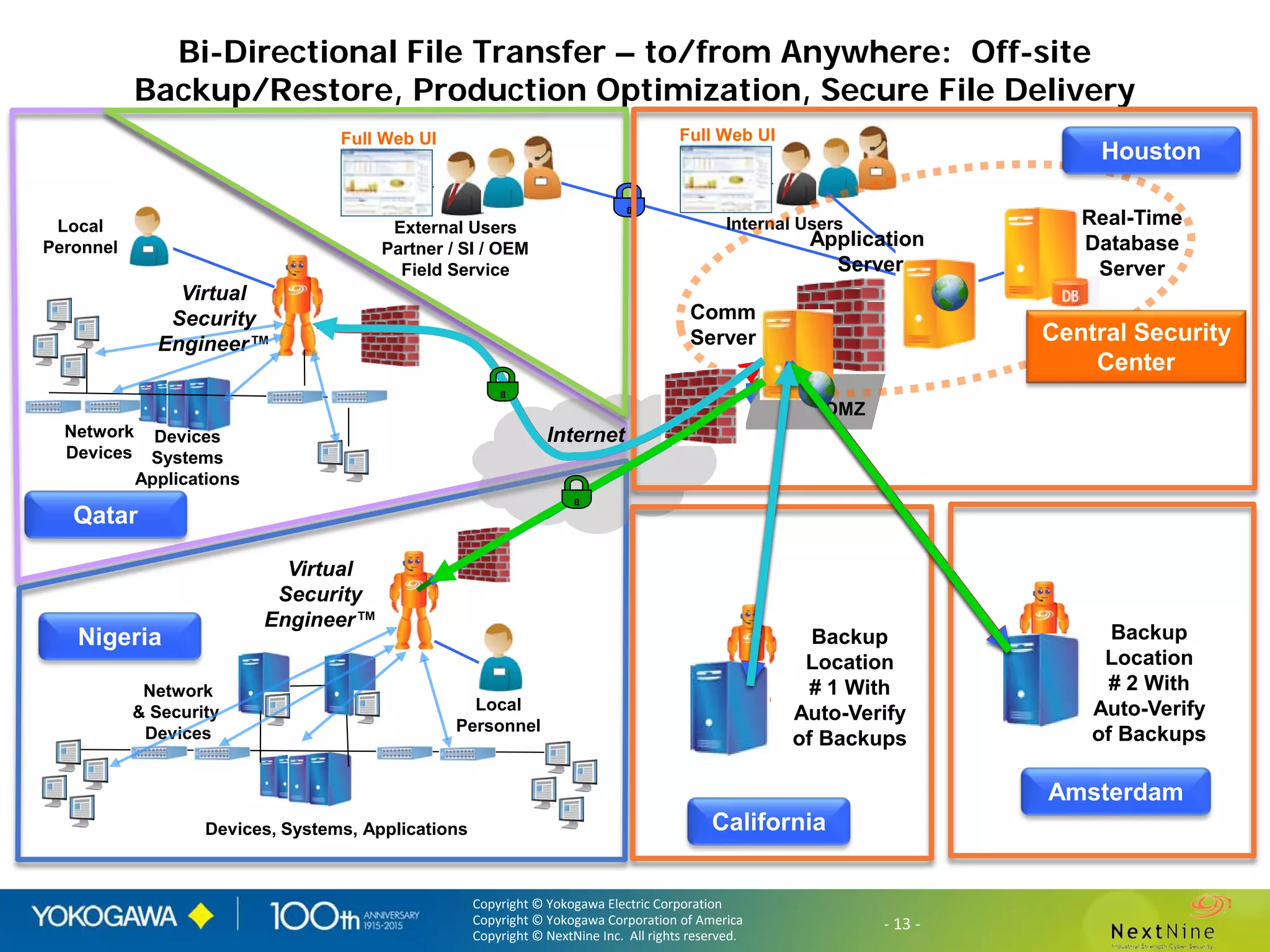
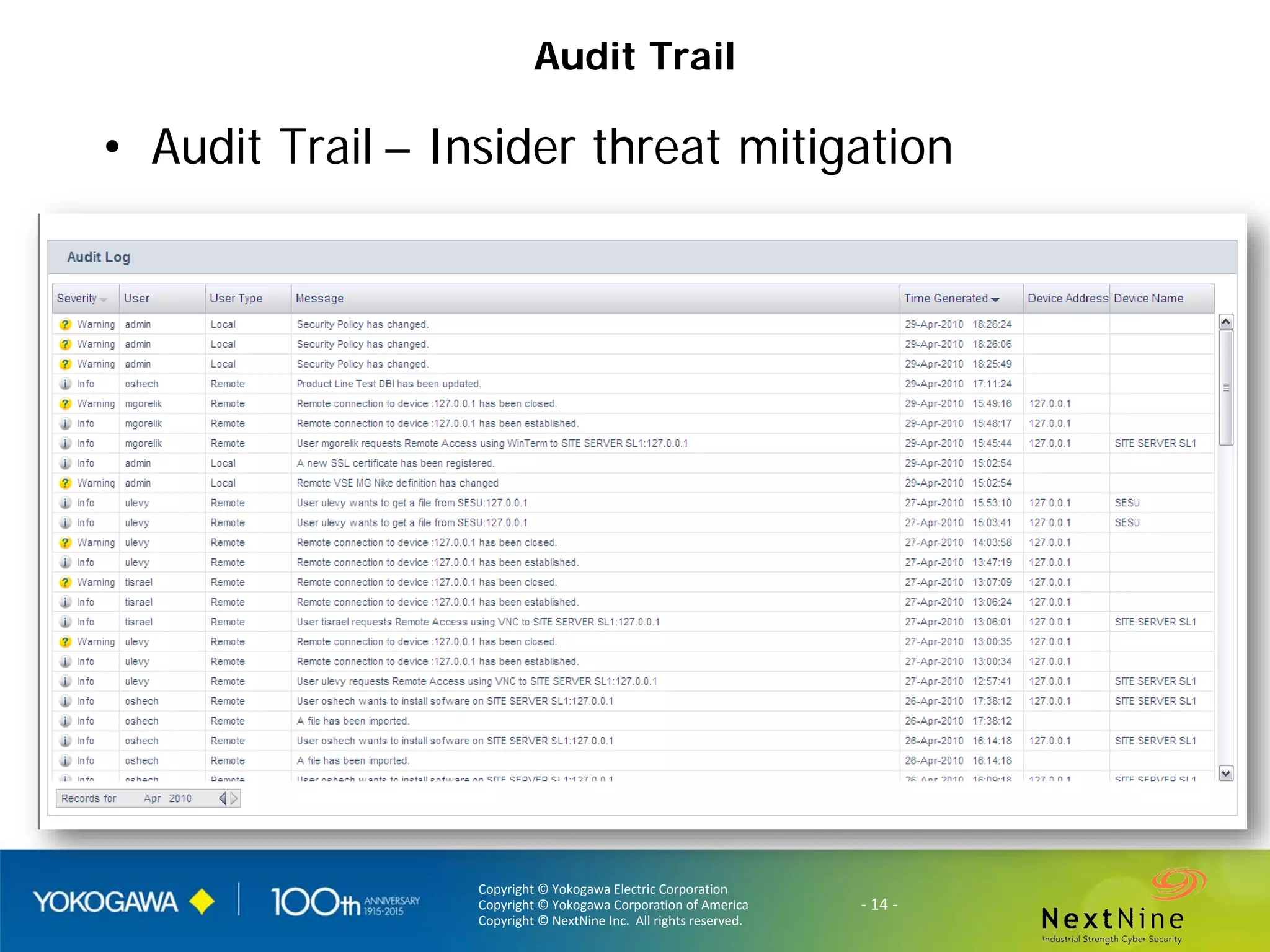
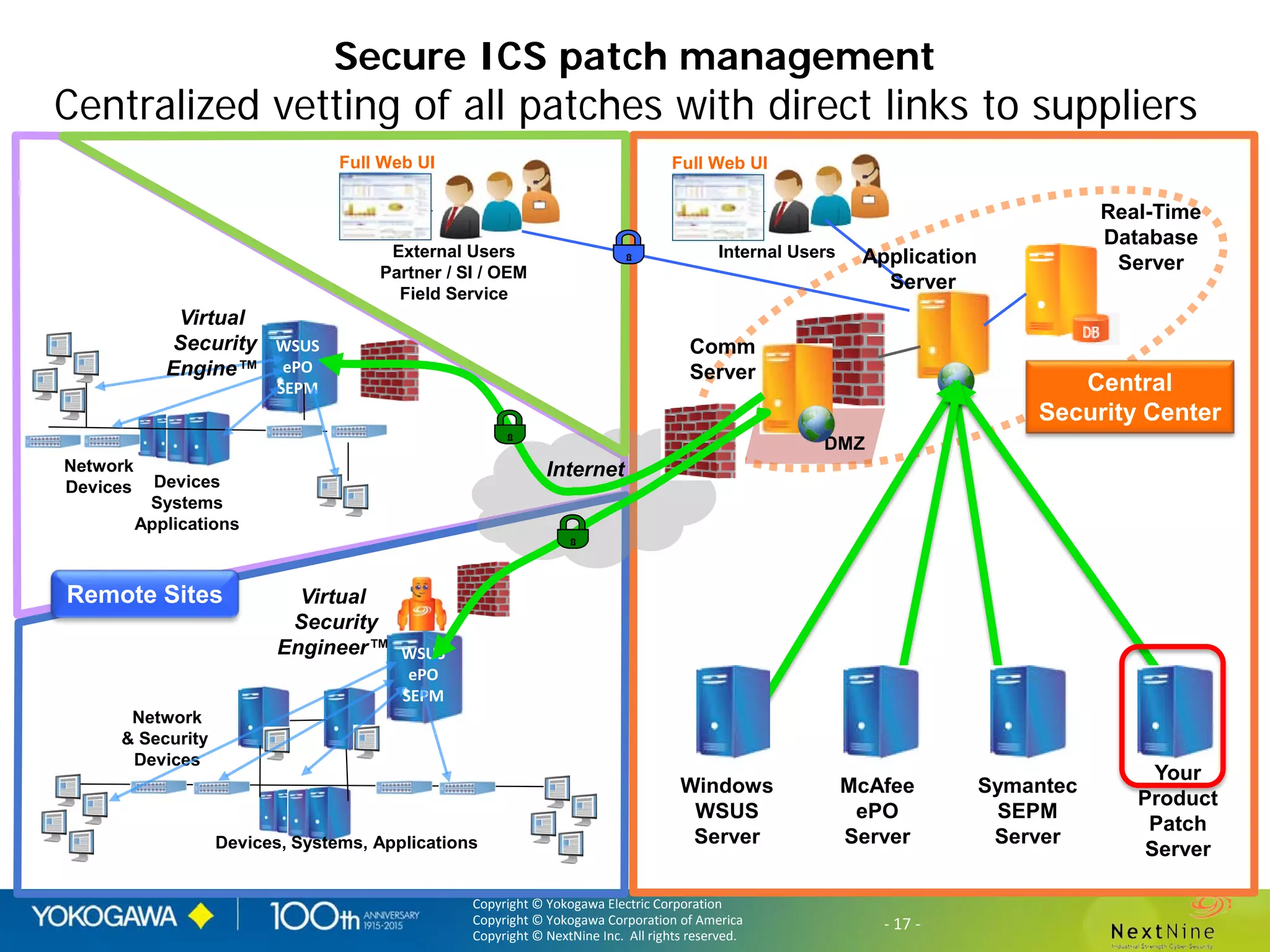
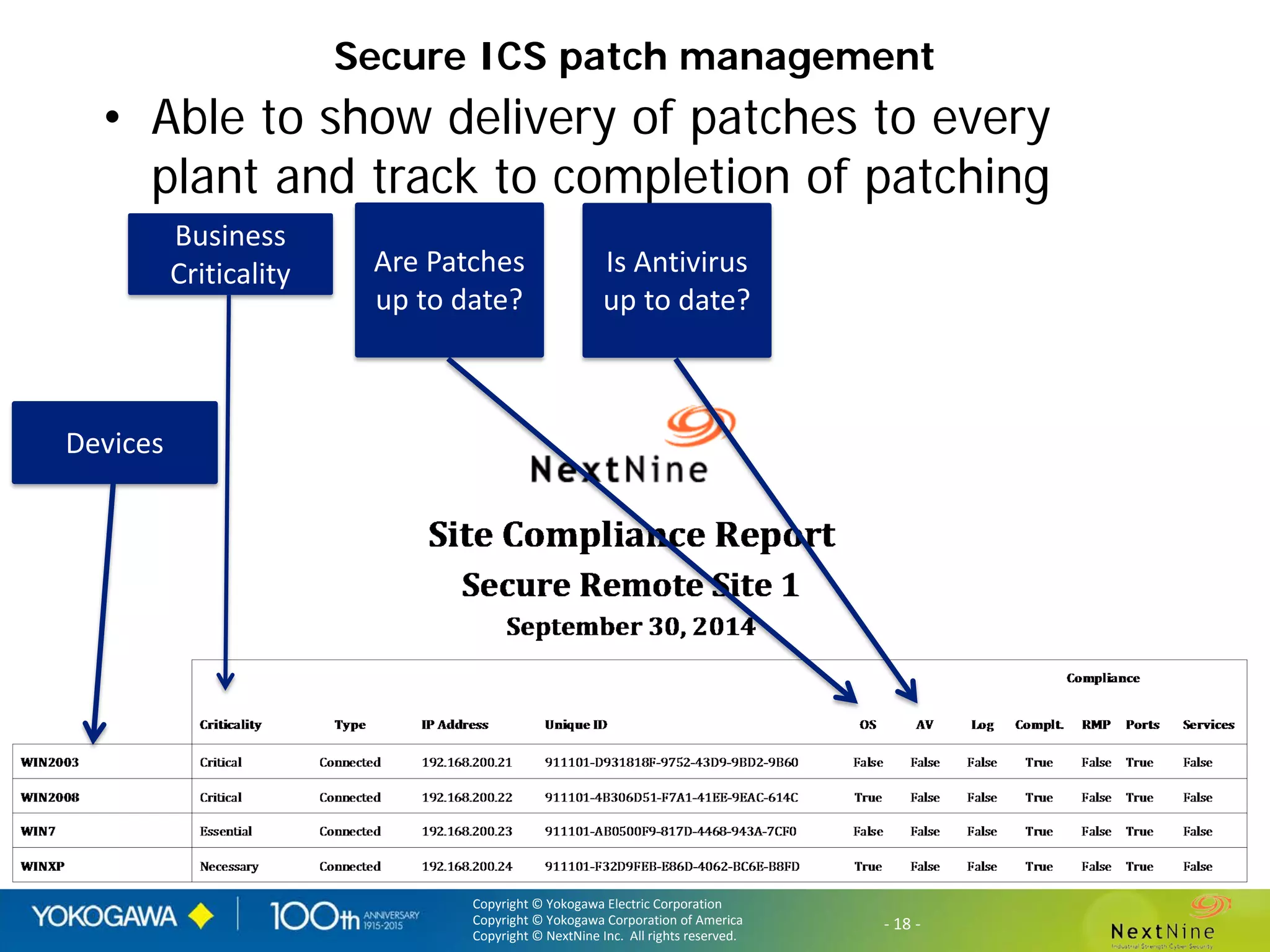
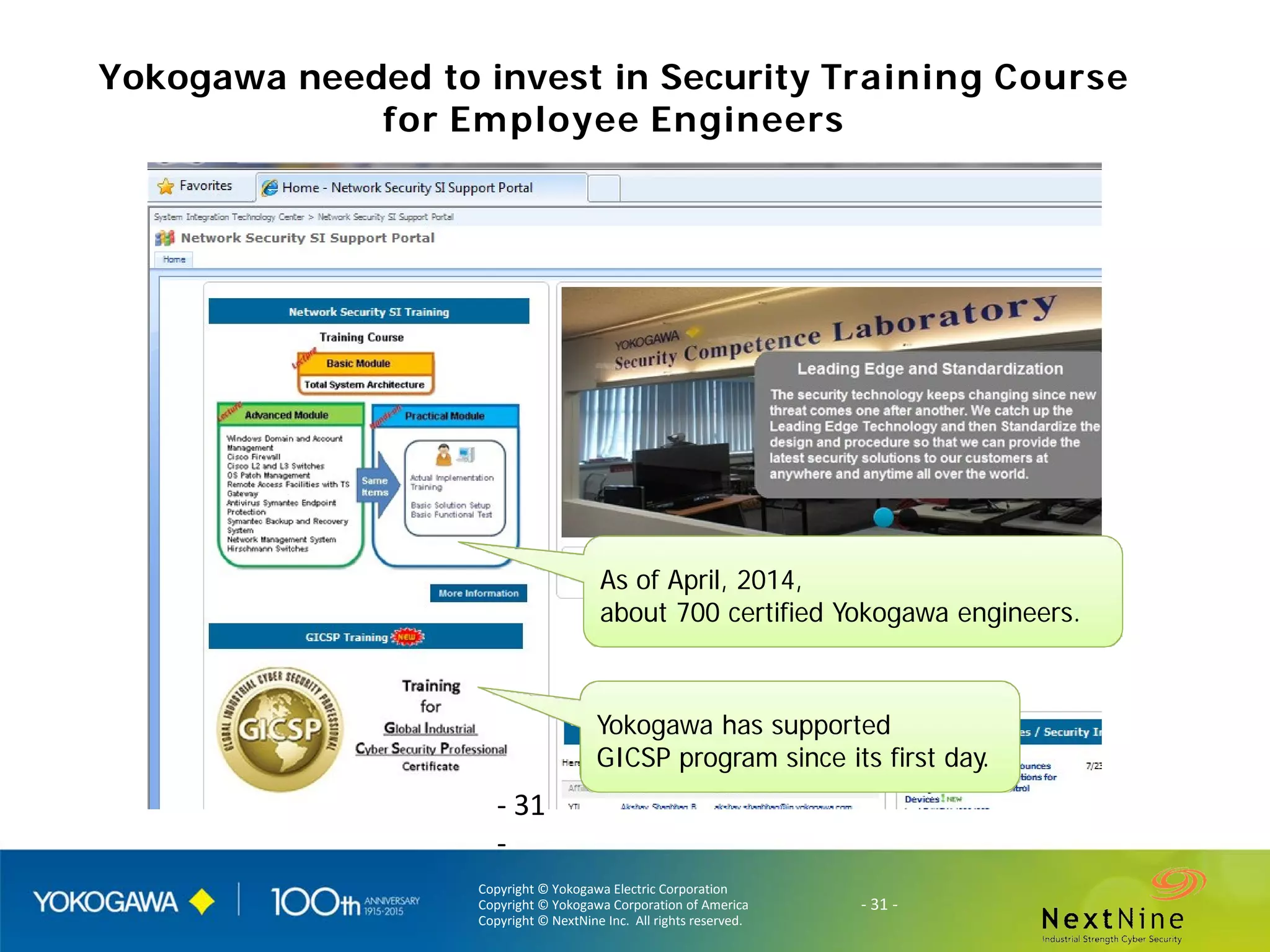
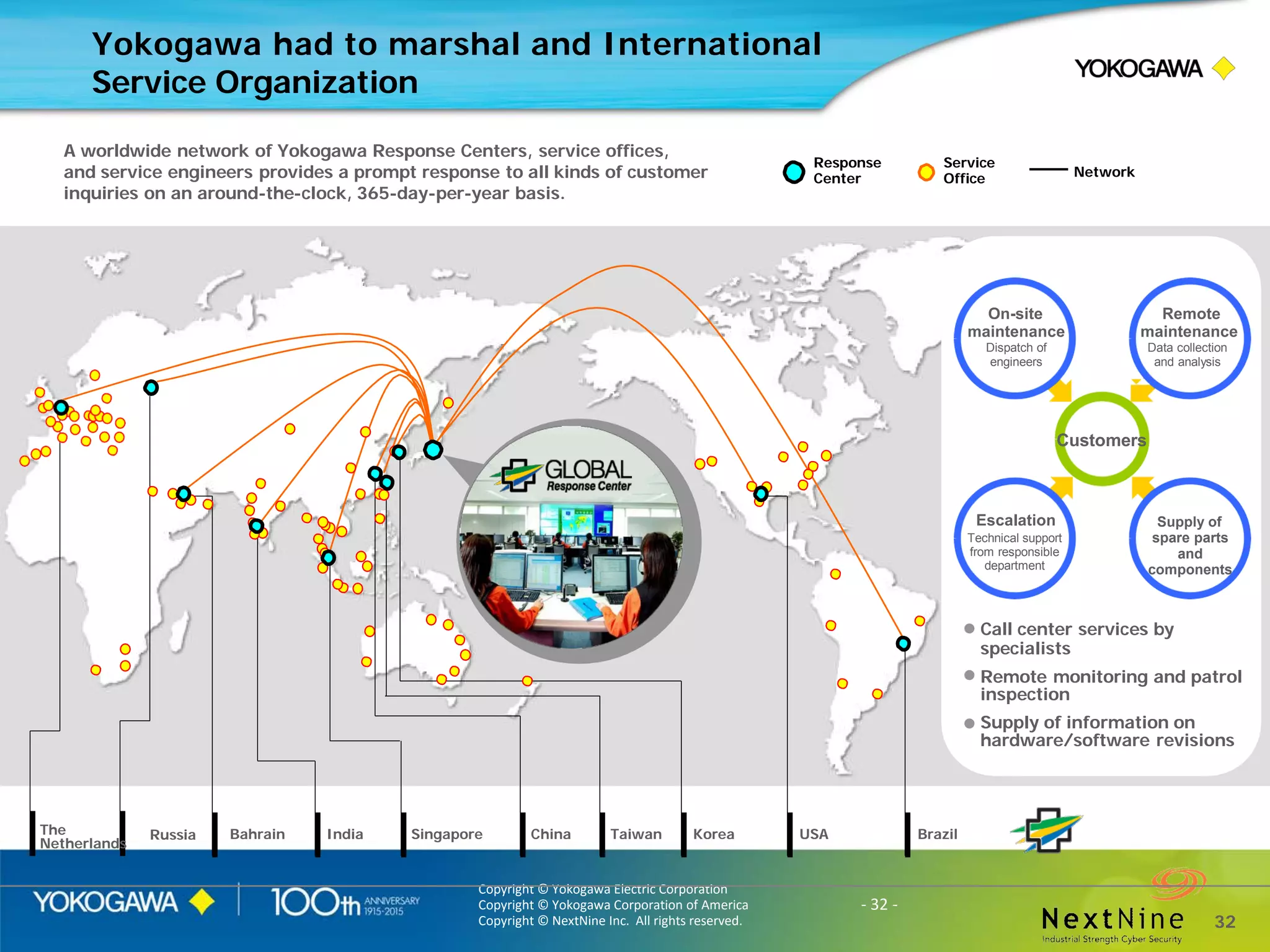
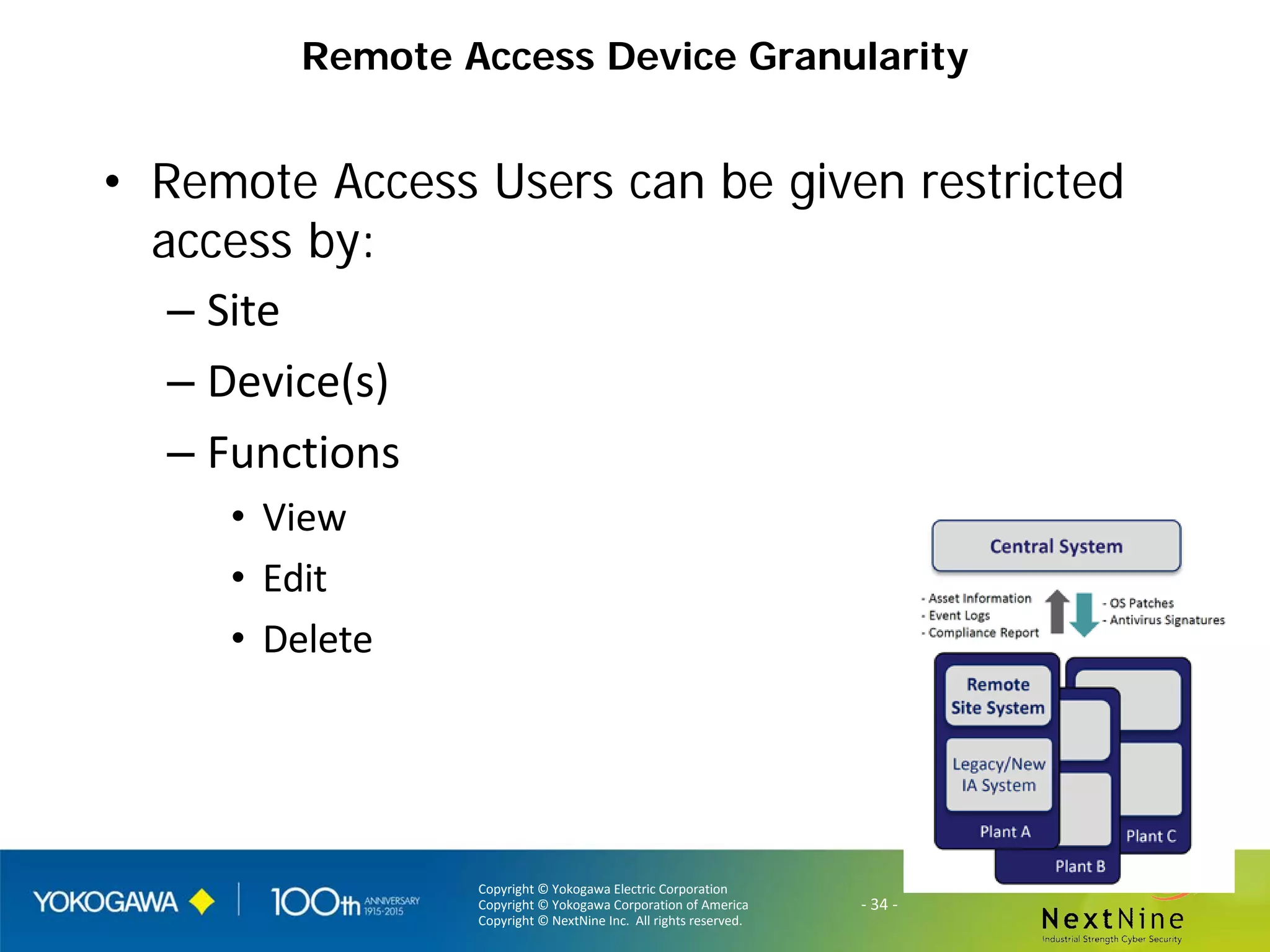
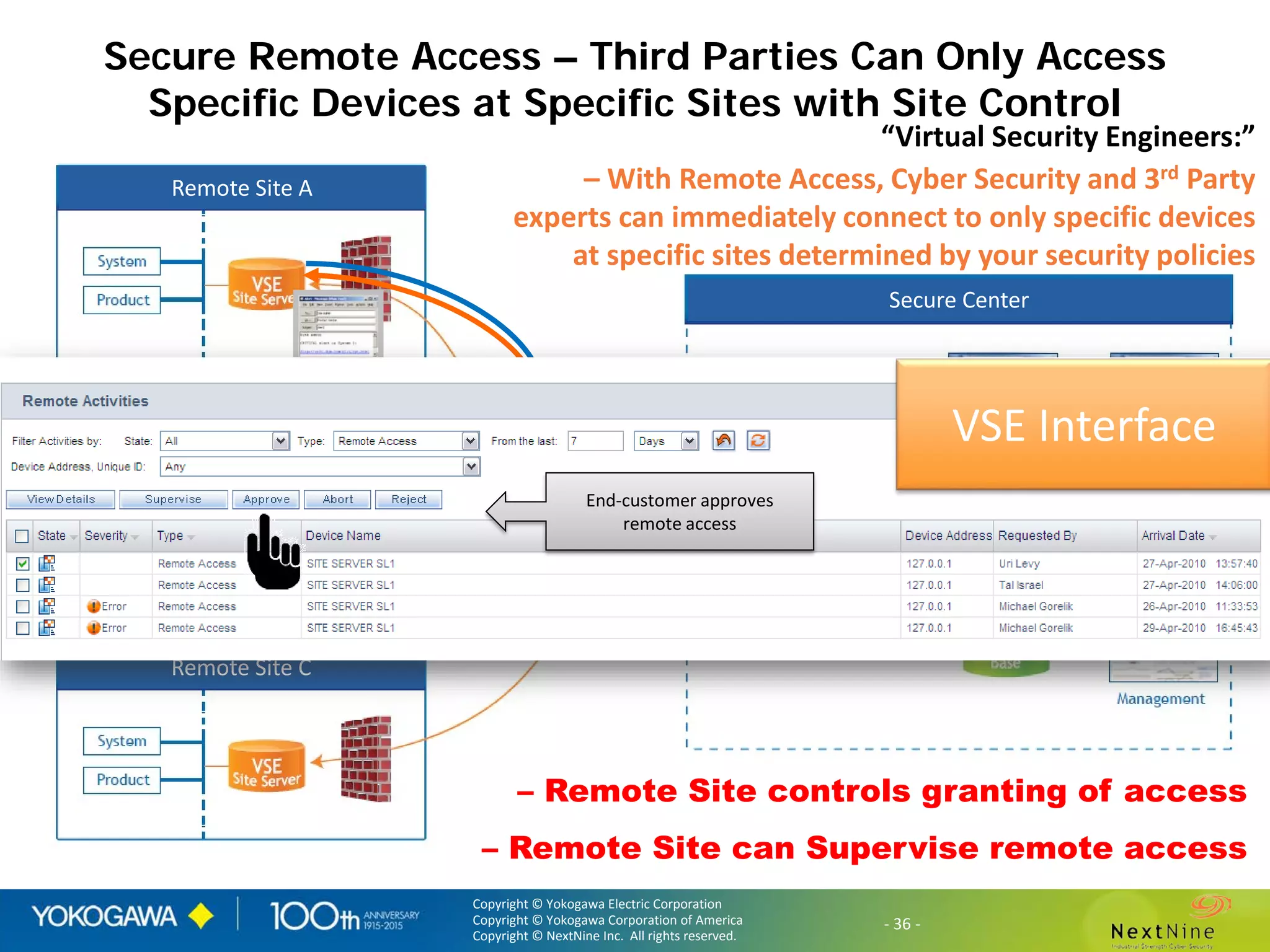
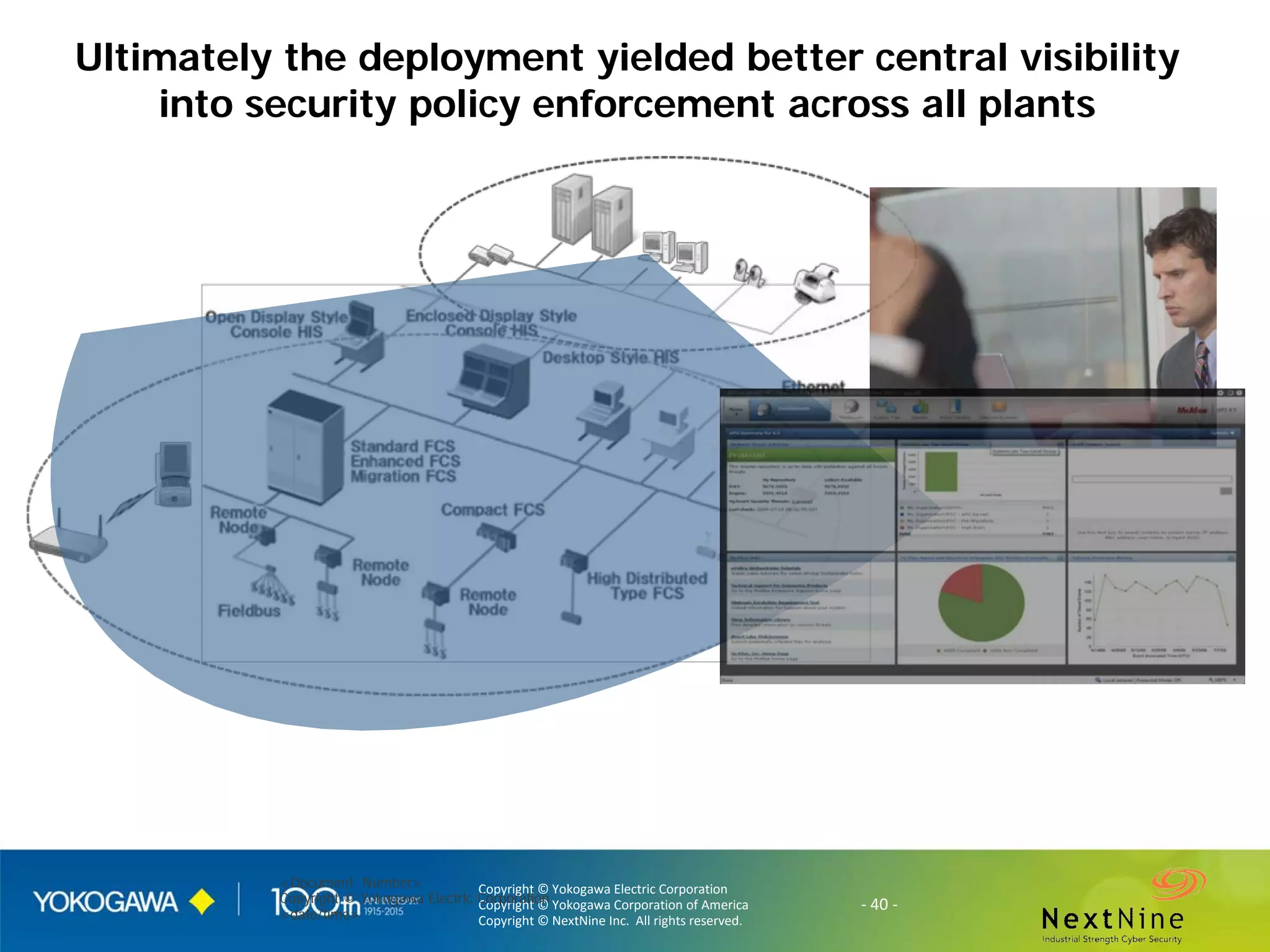
The document discusses lessons learned from a year of deploying and operating a global cybersecurity management system at a major oil and gas company, including both successes and challenges faced during the process. Key highlights include the establishment of automated asset discovery, patch management, and centralized governance, as well as issues related to IT integration with operational technology. The document also outlines necessary process and technology changes that emerged from the experience, emphasizing the need for improved communication and training among staff.