What is Identity (ID) Theft ?
•
0 likes•230 views
Identity theft occurs when a criminal uses someone else's personal information like name, SSN, or credit card numbers without permission to commit fraud. Thieves can steal information directly by taking wallets, mail, or online data, or indirectly through dumpster diving or changing addresses. Victims should contact credit bureaus, close fraudulent accounts, file a police report, and get more information from the FTC website or brochures. Steps to reduce risk include using passwords, securing personal data, being wary of sharing information, and properly disposing of documents with financial information.
Report
Share
Report
Share
Download to read offline
Recommended
Identity Theft: How to Avoid It

This was a presentation by Hewie Poplock on Tuesday, November 15th, 2016 in the Goodwill Manasota (FL) Ranch Lake Community Room, "How to Avoid Identity Theft".
A victim of identity theft himself, Hewie will provide examples of how ID theft can happen as well as suggestions and precautions on how to prevent you and your family from becoming victims of identity theft yourselves. Topics covered included:
• What is Identity Theft
• How ID Theft Happens
• How to Protect Yourself
• Phishing
• Data Breaches
• Facebook Spoofing
• Skimmers
• Security Freeze
• On Line Shopping Safety
• Credit Card Chips
• What to Do If You are a Victim
Hewie is a former teacher, college instructor, business owner and manager, IT Manager, and web designer. He is currently semi-retired, but is active in technology user groups and frequently speaks to and teaches groups who are mostly seniors. He holds a monthly Windows Special Interest Group for a group in Orlando and has several videos on YouTube. He is an active member of The Sarasota Technology User Group.
Phishing file pp

This is a cyber crime which include the definition,flow of it and the steps of the crime
Ten things to know about identity theft

Learning you are a victim of identity theft can be a stressful event. Identity theft is also a challenge to businesses, organizations and government agencies, including the IRS. Tax-related identity theft occurs when someone uses your stolen Social Security number to file a tax return claiming a fraudulent refund.
Many times, you may not be aware that someone has stolen your identity. The IRS may be the first to let you know you’re a victim of ID theft after you try to file your taxes.
The IRS combats tax-related identity theft with a strategy of prevention, detection and victim assistance. The IRS is making progress against this crime and it remains one of the agency’s highest priorities.
Here are ten things to know about ID Theft:
Recommended
Identity Theft: How to Avoid It

This was a presentation by Hewie Poplock on Tuesday, November 15th, 2016 in the Goodwill Manasota (FL) Ranch Lake Community Room, "How to Avoid Identity Theft".
A victim of identity theft himself, Hewie will provide examples of how ID theft can happen as well as suggestions and precautions on how to prevent you and your family from becoming victims of identity theft yourselves. Topics covered included:
• What is Identity Theft
• How ID Theft Happens
• How to Protect Yourself
• Phishing
• Data Breaches
• Facebook Spoofing
• Skimmers
• Security Freeze
• On Line Shopping Safety
• Credit Card Chips
• What to Do If You are a Victim
Hewie is a former teacher, college instructor, business owner and manager, IT Manager, and web designer. He is currently semi-retired, but is active in technology user groups and frequently speaks to and teaches groups who are mostly seniors. He holds a monthly Windows Special Interest Group for a group in Orlando and has several videos on YouTube. He is an active member of The Sarasota Technology User Group.
Phishing file pp

This is a cyber crime which include the definition,flow of it and the steps of the crime
Ten things to know about identity theft

Learning you are a victim of identity theft can be a stressful event. Identity theft is also a challenge to businesses, organizations and government agencies, including the IRS. Tax-related identity theft occurs when someone uses your stolen Social Security number to file a tax return claiming a fraudulent refund.
Many times, you may not be aware that someone has stolen your identity. The IRS may be the first to let you know you’re a victim of ID theft after you try to file your taxes.
The IRS combats tax-related identity theft with a strategy of prevention, detection and victim assistance. The IRS is making progress against this crime and it remains one of the agency’s highest priorities.
Here are ten things to know about ID Theft:
You Have the Power to Stop Identity Theft

All product and company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
You Can Fight Identity Theft

company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
Internet scams

I had amde this ppt for my college presentation. It doesnt cover the various faruds in minute detail but this presentation is a very good overview! Enjoy!
Identity Theft: How to Reduce Your Risk

Dr. Barbara O'Neill and Carol Kando-Pineda, of the Federal Trade Commission, will present this 90-minute webinar on behalf of the Military Families Learning Network. This 90-minute webinar will include two sections: a general overview of identity theft and discussion about military-specific scams. Topics covered during the first section, presented by Dr. O’Neill, include a definition of identity theft, signs of identity theft, an identity theft risk assessment quiz, types of identity theft, how identity theft occurs, ways to reduce identity theft risk, phishing scams, proactive and reactive identity theft actions, and identity theft resources. Ms. Kando-Pineda plans to discuss getting help for identity theft victims, including the steps they need to take immediately, walking through the new features for consumers on Identitytheft.gov and how they help victims develop a recovery plan, get a heads-up on the latest “imposter” scams, and an update on the Military Consumer campaign and new resources on the way for the military community.
Identity theft fraud laws how the legal system can protect you

In the no so distant past, individuals didn't stress much when they lost a charge card or discarded a bill. They knew they could contact their loan bosses and rectify it before long. In any case, today, you might be a casualty of Identity theft fraud and not know it. This pernicious wrongdoing is likewise difficult to indict on the grounds that it's hard to distinguish and find the culprit.
Senior Audience Presentation

Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
17 U.S. Code § 107 - Limitations on exclusive rights: Fair use
Notwithstanding the provisions of sections 106 and 106A, the fair use of a copyrighted work, including such use by reproduction in copies or phonorecords or by any other means specified by that section, for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright.
Identity Fraud Precautions

Visit http://internethomebusinessopportunityreview.info/form.php?id=54624 for more info
Tax Filing Fraud Rampant This Tax Season

Robin Bell, Partner, Tax Services, discusses the signs of tax filing identity fraud, how to prevent it and what a victim of tax fraud can do.
Identity Theft and How to Prevent Them in the Digital Age 

Mr. Jamshed Masood who is a telecom sector executive provided information about how to identity thefts and how to prevent them in the digital age. He discussed the real definition of identity theft, its impact. Not only limited to this, respected speaker also gave the complete information of different types of identity thefts and their methods such as hacking, shoulder surfing. While discussing these thefts, light on prevention methodology to treat these kind of thefts was also given to the audience.
Identity Privacy 101 - Quicken Loans Zing Blog

Protecting your privacy, identity and financial information online is critically important in today’s Internet economy. Last year, 13.1 million Americans were victims of identity theft. I have no plans on joining this group, which is what inspired us to create our latest Zing blog guide – Identity 101.
What You Need to Know to Avoid Identity Theft

company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
Social networking and identity theft 

Presentation my daughter drafted for a class assignment; discusses social networking and risks of identity theft
Identity Theft and Phishing - Canadian Resource Centre for Victims

company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
Fifth Annual Study on Medical Identity Theft

Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
17 U.S. Code § 107 - Limitations on exclusive rights: Fair use
Notwithstanding the provisions of sections 106 and 106A, the fair use of a copyrighted work, including such use by reproduction in copies or phonorecords or by any other means specified by that section, for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright.
Identity Theft - Proactive / Reactive First Steps 

Seven Types of Criminal Fraud Types related to Identity Theft
More Related Content
What's hot
You Have the Power to Stop Identity Theft

All product and company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
You Can Fight Identity Theft

company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
Internet scams

I had amde this ppt for my college presentation. It doesnt cover the various faruds in minute detail but this presentation is a very good overview! Enjoy!
Identity Theft: How to Reduce Your Risk

Dr. Barbara O'Neill and Carol Kando-Pineda, of the Federal Trade Commission, will present this 90-minute webinar on behalf of the Military Families Learning Network. This 90-minute webinar will include two sections: a general overview of identity theft and discussion about military-specific scams. Topics covered during the first section, presented by Dr. O’Neill, include a definition of identity theft, signs of identity theft, an identity theft risk assessment quiz, types of identity theft, how identity theft occurs, ways to reduce identity theft risk, phishing scams, proactive and reactive identity theft actions, and identity theft resources. Ms. Kando-Pineda plans to discuss getting help for identity theft victims, including the steps they need to take immediately, walking through the new features for consumers on Identitytheft.gov and how they help victims develop a recovery plan, get a heads-up on the latest “imposter” scams, and an update on the Military Consumer campaign and new resources on the way for the military community.
Identity theft fraud laws how the legal system can protect you

In the no so distant past, individuals didn't stress much when they lost a charge card or discarded a bill. They knew they could contact their loan bosses and rectify it before long. In any case, today, you might be a casualty of Identity theft fraud and not know it. This pernicious wrongdoing is likewise difficult to indict on the grounds that it's hard to distinguish and find the culprit.
Senior Audience Presentation

Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
17 U.S. Code § 107 - Limitations on exclusive rights: Fair use
Notwithstanding the provisions of sections 106 and 106A, the fair use of a copyrighted work, including such use by reproduction in copies or phonorecords or by any other means specified by that section, for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright.
Identity Fraud Precautions

Visit http://internethomebusinessopportunityreview.info/form.php?id=54624 for more info
Tax Filing Fraud Rampant This Tax Season

Robin Bell, Partner, Tax Services, discusses the signs of tax filing identity fraud, how to prevent it and what a victim of tax fraud can do.
Identity Theft and How to Prevent Them in the Digital Age 

Mr. Jamshed Masood who is a telecom sector executive provided information about how to identity thefts and how to prevent them in the digital age. He discussed the real definition of identity theft, its impact. Not only limited to this, respected speaker also gave the complete information of different types of identity thefts and their methods such as hacking, shoulder surfing. While discussing these thefts, light on prevention methodology to treat these kind of thefts was also given to the audience.
Identity Privacy 101 - Quicken Loans Zing Blog

Protecting your privacy, identity and financial information online is critically important in today’s Internet economy. Last year, 13.1 million Americans were victims of identity theft. I have no plans on joining this group, which is what inspired us to create our latest Zing blog guide – Identity 101.
What You Need to Know to Avoid Identity Theft

company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
Social networking and identity theft 

Presentation my daughter drafted for a class assignment; discusses social networking and risks of identity theft
Identity Theft and Phishing - Canadian Resource Centre for Victims

company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
What's hot (20)
Identity theft fraud laws how the legal system can protect you

Identity theft fraud laws how the legal system can protect you
Identity Theft and How to Prevent Them in the Digital Age 

Identity Theft and How to Prevent Them in the Digital Age
Identity Theft and Phishing - Canadian Resource Centre for Victims

Identity Theft and Phishing - Canadian Resource Centre for Victims
Viewers also liked
Fifth Annual Study on Medical Identity Theft

Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
17 U.S. Code § 107 - Limitations on exclusive rights: Fair use
Notwithstanding the provisions of sections 106 and 106A, the fair use of a copyrighted work, including such use by reproduction in copies or phonorecords or by any other means specified by that section, for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright.
Identity Theft - Proactive / Reactive First Steps 

Seven Types of Criminal Fraud Types related to Identity Theft
Consumer Sentinel Data Book 2015

Company names mentioned herein are the property of, and may be trademarks of, their respective owners.
DATA BREACH CHARTS

All information, data, and material contained, presented, or provided on is for educational purposes only.
Company names mentioned herein are the property of, and may be trademarks of, their respective owners.
It is not to be construed or intended as providing legal advice.
What's Next in Growth? 2016

Gave a talk at StartCon about the future of Growth. I touch on viral marketing / referral marketing, fake news and social media, and marketplaces. Finally, the slides go through future technology platforms and how things might evolve there.
The Six Highest Performing B2B Blog Post Formats

If your B2B blogging goals include earning social media shares and backlinks to boost your search rankings, this infographic lists the size best approaches.
The Outcome Economy

Each technological age has been marked by a shift in how the industrial platform enables companies to rethink their business processes and create wealth. In the talk I argue that we are limiting our view of what this next industrial/digital age can offer because of how we read, measure and through that perceive the world (how we cherry pick data). Companies are locked in metrics and quantitative measures, data that can fit into a spreadsheet. And by that they see the digital transformation merely as an efficiency tool to the fossil fuel age. But we need to stretch further…
32 Ways a Digital Marketing Consultant Can Help Grow Your Business

How can a digital marketing consultant help your business? In this resource we'll count the ways. 24 additional marketing resources are bundled for free.
Viewers also liked (8)
32 Ways a Digital Marketing Consultant Can Help Grow Your Business

32 Ways a Digital Marketing Consultant Can Help Grow Your Business
Similar to What is Identity (ID) Theft ?
How to Prevent ID Theft

Presentation on ID Theft for BCUG on Friday, October 21, 2016 by Hewie Poplock
Identity Theft - Canada

company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
Youth Protection Guide - Canada

company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
DONCEAP - May - About Identity Theft

Learn all there is to know about Identity Theft and what you can do to prevent it from happening to you.
Credit card frauds 

Presentaion on Credit Card frauds. These prsentation covers legal as well as general aspect related to credit card frauds.
Special Report for Retail Businesses on IDENTITY THEFT - ca

• Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
Identity Theft Overview

This mini course provides an explanation of Identity Theft in terms of what is, how it happens and the ways to prevent it.
7 Tips For Preventing Identity Theft

NewsUSA offers syndicate news features that are guaranteed to give your company exposure and media placements. This print sample shows how those placements look once picked up. syndicate news features http://about.newsusa.com/corporate/what_we_do.asp
Identity Theft Prevention

View our presentation on how to protect yourself against identity theft, and what to do if you become a victim.
Protecting Yourself Against Identity Theft

You do not have to be victimized by hackers, be proactive in protecting your identity! Lifelock is what I use, check it out before it is too late.
Similar to What is Identity (ID) Theft ? (20)
Special Report for Retail Businesses on IDENTITY THEFT - ca

Special Report for Retail Businesses on IDENTITY THEFT - ca
More from - Mark - Fullbright
ISTR Internet Security Threat Report 2019

This report solely belongs to Symantec. Credit is due to all original authors and no financial gain was made from the report, Simply sharing for educational purposes,
IC3 2019 Internet Crime Report

The FBI is the lead federal agency for investigating malicious cyber activity by criminals, nation-state adversaries, and terrorists. To fulfill this mission, the FBI often develops resources to enhance operations and collaboration. One such resource is the FBI’s Internet Crime Complaint Center (IC3) which provides the public with a trustworthy and convenient mechanism for reporting information concerning suspected Internet-facilitated criminal activity. At the end of every year, the IC3 collates information collected into an annual report.
Credit is due to all original authors and no financial gain was made from the blog, Simply sharing an interesting story for educational purposes,
Police, Protesters, Press, 2020

This guide aims to help journalists understand their rights at protests and avoid arrest when reporting on these events. It summarizes the legal landscape and provides strategies and tools to help journalists avoid incidents with police and navigate them successfully should they arise. Credit RCFP.Org
Credit is due to all original authors and no financial gain was made from the blog, Simply sharing an interesting story for educational purposes,
2020 Data Breach Investigations Report (DBIR)

Verizon Publishes 2020 Data Breach Investigation Report (DBIR) With Insights From Thousands of Confirmed Breaches. Verizon's 2020 Data Breach Investigations Report (DBIR) is the most extensive yet, with 81 contributing organizations, and more than 32,000 incidents analyzed (of which 3,950 were confirmed breaches). Credit:Verizon
Credit is due to all original authors and no financial gain was made from the report, Simply sharing an interesting story for educational purposes,
FCPA Guidance 2020

A Resource Guide to theU.S. Foreign Corrupt Practices Act
Credit is due to all original authors and no financial gain was made from the report, Simply sharing an interesting story for educational purposes,
Consumer Sentinel Network Data Book 2019

The FTC takes in reports from consumers about problems they experience in the marketplace. The reportsare stored in the Consumer Sentinel Network (Sentinel), a secure online database available only to lawenforcement. While the FTC does not intervene in individual consumer disputes, its law enforcementpartners – whether they are down the street, across the nation, or around the world – can use informationin the database to spot trends, identify questionable business practices and targets, and enforce the law.
Credit is due to all original authors and no financial gain was made from the report, Simply sharing an interesting story for educational purposes,
CFPB Consumer Reporting Companies 2019

Below is a list of consumer reporting companies updated for 2019.1 Consumer reporting companies collect information and provide reports to other companies about you. These companies use these reports to inform decisions about providing you with credit, employment, residential rental housing, insurance, and in other decision making situations. The list below includes the three nationwide consumer reporting companies and several other reporting companies that focus on certain market areas and consumer segments. The list gives you tips so you can determine which of these companies may be important to you. It also makes it easier for you to take advantage of your legal rights to (1) obtain the information in your consumer reports, and (2) dispute suspected inaccuracies in your reports with companies as needed.
Advisory to Financial Institutions on Illicit Financial Schemes and Methods R...

Transnational criminal organizations (TCOs), foreign fentanyl suppliers, and Internet purchasers located in the United States engage in the trafficking of fentanyl, fentanyl analogues, and other synthetic opioids and the subsequent laundering of the proceeds from such illegal sales.
2018 IC3 Report

The mission of the IC3 is to provide the public with a reliable and convenient reporting mechanism to submit information to the FBI concerning suspected Internet-facilitated criminal activity, and to develop effective alliances with industry partners. Information is analyzed and disseminated for investigative and intelligence purposes, for law enforcement, and for public awareness.
Credit is due to all original authors and no financial gain was made from the report, Simply sharing an interesting story for educational purposes,
2019 Data Breach Investigations Report (DBIR)

This report is built upon analysis of 41,686 security incidents, of which 2,013 were confirmed data breaches. We will take a look at how results are changing (or not) over the years as well as digging into the overall threat landscape and the actors, actions, and assets that are present in breaches. Windows into the most common pairs of threat actions and affected assets also are provided.
2018 Privacy & Data Security Report

The Federal Trade Commission (FTC or Commission) is an independent U.S. law enforcement agency charged with protecting consumers and enhancing competition across broad sectors of the economy. The FTC’s primary legal authority comes from Section 5 of the Federal Trade Commission Act, which prohibits unfair or deceptive practices in the marketplace. The FTC also has authority to enforce a variety of sector specific laws, including the Truth in Lending Act, the CAN-SPAM Act, the Children’s Online Privacy Protection Act, the Equal Credit Opportunity Act, the Fair Credit Reporting Act, the Fair Debt Collection Practices Act, and the Telemarketing and Consumer Fraud and Abuse Prevention Act. This broad authority allows the Commission
to address a wide array of practices affecting consumers, including those that emerge with the development of new technologies and business models.
Consumer Sentinel Network Data Book 2018 

Sentinel sorts consumer reports into 29 top categories. Appendices B1 – B3 describe the categories,providing details, and three year figures. To reflect marketplace changes, new categories or subcategories are created or deleted over time.The Consumer Sentinel Network Data Book excludes the National Do Not Call Registry. A separate report about these complaint statistics is available at: https://www.ftc.gov/reports/national-do-not-call-registry-data-book-fiscal-year-2018. The Sentinel Data Book also excludes reports about unsolicited commercial email.Consumers can report as much or as little detail as they wish when they file a report. For the Sentinel Data Book graphics, percentages are based on the total number of Sentinel fraud, identity theft, and other report types in 2018 in which consumers provided the information displayed on each chart.Reports to Sentinel sometimes indicate money was lost, and sometimes indicate no money was lost.Often, people make these reports after they experience something problematic in the marketplace,avoid losing any money, and wish to alert others. Except where otherwise stated, numbers are based on reports both from people who indicated a loss and people who did not.Calculations of dollar amounts lost are based on reports in which consumers indicated they lost between $1 and $999,999. Prior to 2017, reported “amount paid” included values of $0 to $999,999.States and Metropolitan Areas are ranked based on the number of reports per 100,000 population.State rankings are based on 2017 U.S. Census population estimates (Annual Estimates of the Resident Population: April 1, 2010 to July 1, 2017). Metropolitan Area rankings are based on 2016 U.S. Census population estimates (Annual Estimates of the Resident Population: April 1, 2010 to July 1, 2016).This Sentinel Data Book identifies Metropolitan Areas (Metropolitan and Micropolitan Statistical Areas)with a population of 100,000 or more except where otherwise noted. Metropolitan areas are defined by Office of Management and Budget Bulletin No. 15-01, “Revised Delineations of Metropolitan Statistical Areas, Micropolitan Statistical Areas, and Combined Statistical Areas, and Guidance on Uses of the Delineations of These Areas” (July 15, 2015). Numbers change over time. The Sentinel Data Book sorts consumer reports by year, based on the date of the consumer’s report. Some data contributors transfer their complaints to Sentinel after the end of the calendar year, and new data providers often contribute reports from prior years. As a result, the total number of reports for 2018 will likely change during the next few months, and totals from previous years may differ from prior Consumer Sentinel Network Data Books. The most up to date information can be found online at ftc.gov/data
Credit Score Explainer

A credit score is a three -digit number that predicts how likely you are to pay back a loan on time, based on information from your credit reports.
Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
The Geography of Medical Identity Theft

Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only. - Medical identity theft has existed in various forms for decades, but it was in 2006 that World Privacy Forum published the first major report about the crime. The report called for medical data breach notification laws and more research about medical identity theft and its impacts. Since that time, medical data breach notification laws have been enacted, and other progress has been made, particularly in the quality of consumer complaint datasets gathered around identity theft, including medical forms of the crime. This report uses new data arising from consumer medical identity theft complaint reporting and medical data breach reporting to analyze and document the geography of medical identity theft and its growth patterns. The report also discusses new aspects of consumer harm resulting from the crime that the data has brought to light
Consumer Sentinel Data Book 2017

The FTC takes in reports from consumers about problems they experience in the marketplace. The reports are stored in the Consumer Sentinel Network (Sentinel), a secure online database available only to law enforcement. While the FTC does not intervene in individual consumer disputes, its law enforcement partners – whether they are down the street, across the nation, or around the world – can use information in the database to spot trends, identify questionable business practices and targets, and enforce the law.
Since 1997, Sentinel has collected tens of millions of reports from consumers about fraud, identity theft, and other consumer protection topics. During 2017, Sentinel received nearly 2.7 million consumer reports, which the FTC has sorted into 30 top categories. The 2017 Consumer Sentinel Network Data Book (Sentinel Data Book) has a vibrant new look, and a lot more information about what consumers told us last year. You'll know more about how much money people lost in the aggregate, the median amount they paid, and what frauds were most costly. And you'll know much more about complaints of identity theft, fraud, and other types of problems in each state, too. The Sentinel Data Book is based on unverified reports filed by consumers. The data is not based on a consumer survey. Sentinel has a five-year data retention policy, with reports older than five years purged biannually.
Protecting Personal Information: A Guide for Business

*Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
Data Breach Response: A Guide for Business

This guide addresses the steps to take once a
breach has occured. For advice on implementing a
plan to protect consumers’ personal information, to
prevent breaches and unauthorized access, check
out the FTC’s Protecting Personal Information: A
Guide for Business and Start with Security: A Guide
for Business.
*Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
2017 Data Breach Investigations Report

Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
Consumer Sentinel Network Data Book for January 2016 - December 2016

FTC Consumer Sentinel Network Law enforcement's source for consumer complaints.
All information, data, and material contained, presented, or provided on is for educational purposes only.
Company names mentioned herein are the property of, and may be trademarks of, their respective owners.
It is not to be construed or intended as providing legal advice.
Consumer Sentinel Network Report 2014

Company names mentioned herein are the property of, and may be trademarks of, their respective owners.
More from - Mark - Fullbright (20)
Advisory to Financial Institutions on Illicit Financial Schemes and Methods R...

Advisory to Financial Institutions on Illicit Financial Schemes and Methods R...
Protecting Personal Information: A Guide for Business

Protecting Personal Information: A Guide for Business
Consumer Sentinel Network Data Book for January 2016 - December 2016

Consumer Sentinel Network Data Book for January 2016 - December 2016
Recently uploaded
Chapter 3 - Islamic Banking Products and Services.pptx

Chapter 3 - Islamic Banking Products and Services.pptxMohd Adib Abd Muin, Senior Lecturer at Universiti Utara Malaysia
This slide is prepared for master's students (MIFB & MIBS) UUM. May it be useful to all.Students, digital devices and success - Andreas Schleicher - 27 May 2024..pptx

Andreas Schleicher presents at the OECD webinar ‘Digital devices in schools: detrimental distraction or secret to success?’ on 27 May 2024. The presentation was based on findings from PISA 2022 results and the webinar helped launch the PISA in Focus ‘Managing screen time: How to protect and equip students against distraction’ https://www.oecd-ilibrary.org/education/managing-screen-time_7c225af4-en and the OECD Education Policy Perspective ‘Students, digital devices and success’ can be found here - https://oe.cd/il/5yV
CLASS 11 CBSE B.St Project AIDS TO TRADE - INSURANCE

Class 11 CBSE Business Studies Project ( AIDS TO TRADE - INSURANCE)
Welcome to TechSoup New Member Orientation and Q&A (May 2024).pdf

In this webinar you will learn how your organization can access TechSoup's wide variety of product discount and donation programs. From hardware to software, we'll give you a tour of the tools available to help your nonprofit with productivity, collaboration, financial management, donor tracking, security, and more.
Digital Tools and AI for Teaching Learning and Research

This Presentation in details discusses on Digital Tools and AI for Teaching Learning and Research
How to Break the cycle of negative Thoughts

We all have good and bad thoughts from time to time and situation to situation. We are bombarded daily with spiraling thoughts(both negative and positive) creating all-consuming feel , making us difficult to manage with associated suffering. Good thoughts are like our Mob Signal (Positive thought) amidst noise(negative thought) in the atmosphere. Negative thoughts like noise outweigh positive thoughts. These thoughts often create unwanted confusion, trouble, stress and frustration in our mind as well as chaos in our physical world. Negative thoughts are also known as “distorted thinking”.
Supporting (UKRI) OA monographs at Salford.pptx

How libraries can support authors with open access requirements for UKRI funded books
Wednesday 22 May 2024, 14:00-15:00.
The Art Pastor's Guide to Sabbath | Steve Thomason

What is the purpose of the Sabbath Law in the Torah. It is interesting to compare how the context of the law shifts from Exodus to Deuteronomy. Who gets to rest, and why?
Home assignment II on Spectroscopy 2024 Answers.pdf

Answers to Home assignment on UV-Visible spectroscopy: Calculation of wavelength of UV-Visible absorption
The approach at University of Liverpool.pptx

How libraries can support authors with open access requirements for UKRI funded books
Wednesday 22 May 2024, 14:00-15:00.
Polish students' mobility in the Czech Republic

Polish students mobility to the Czech Republic within eTwinning project "Medieval adventures with Marco Polo"
Synthetic Fiber Construction in lab .pptx

Synthetic fiber production is a fascinating and complex field that blends chemistry, engineering, and environmental science. By understanding these aspects, students can gain a comprehensive view of synthetic fiber production, its impact on society and the environment, and the potential for future innovations. Synthetic fibers play a crucial role in modern society, impacting various aspects of daily life, industry, and the environment. ynthetic fibers are integral to modern life, offering a range of benefits from cost-effectiveness and versatility to innovative applications and performance characteristics. While they pose environmental challenges, ongoing research and development aim to create more sustainable and eco-friendly alternatives. Understanding the importance of synthetic fibers helps in appreciating their role in the economy, industry, and daily life, while also emphasizing the need for sustainable practices and innovation.
How to Create Map Views in the Odoo 17 ERP

The map views are useful for providing a geographical representation of data. They allow users to visualize and analyze the data in a more intuitive manner.
The Challenger.pdf DNHS Official Publication

Read| The latest issue of The Challenger is here! We are thrilled to announce that our school paper has qualified for the NATIONAL SCHOOLS PRESS CONFERENCE (NSPC) 2024. Thank you for your unwavering support and trust. Dive into the stories that made us stand out!
TESDA TM1 REVIEWER FOR NATIONAL ASSESSMENT WRITTEN AND ORAL QUESTIONS WITH A...

TESDA TM1 REVIEWER FOR NATIONAL ASSESSMENT WRITTEN AND ORAL QUESTIONS WITH ANSWERS.
How to Make a Field invisible in Odoo 17

It is possible to hide or invisible some fields in odoo. Commonly using “invisible” attribute in the field definition to invisible the fields. This slide will show how to make a field invisible in odoo 17.
Mule 4.6 & Java 17 Upgrade | MuleSoft Mysore Meetup #46

Mule 4.6 & Java 17 Upgrade | MuleSoft Mysore Meetup #46
Event Link:-
https://meetups.mulesoft.com/events/details/mulesoft-mysore-presents-exploring-gemini-ai-and-integration-with-mulesoft/
Agenda
● Java 17 Upgrade Overview
● Why and by when do customers need to upgrade to Java 17?
● Is there any immediate impact to upgrading to Mule Runtime 4.6 and beyond?
● Which MuleSoft products are in scope?
For Upcoming Meetups Join Mysore Meetup Group - https://meetups.mulesoft.com/mysore/
YouTube:- youtube.com/@mulesoftmysore
Mysore WhatsApp group:- https://chat.whatsapp.com/EhqtHtCC75vCAX7gaO842N
Speaker:-
Shubham Chaurasia - https://www.linkedin.com/in/shubhamchaurasia1/
Priya Shaw - https://www.linkedin.com/in/priya-shaw
Organizers:-
Shubham Chaurasia - https://www.linkedin.com/in/shubhamchaurasia1/
Giridhar Meka - https://www.linkedin.com/in/giridharmeka
Priya Shaw - https://www.linkedin.com/in/priya-shaw
Shyam Raj Prasad-
https://www.linkedin.com/in/shyam-raj-prasad/
Model Attribute Check Company Auto Property

In Odoo, the multi-company feature allows you to manage multiple companies within a single Odoo database instance. Each company can have its own configurations while still sharing common resources such as products, customers, and suppliers.
The Roman Empire A Historical Colossus.pdf

The Roman Empire, a vast and enduring power, stands as one of history's most remarkable civilizations, leaving an indelible imprint on the world. It emerged from the Roman Republic, transitioning into an imperial powerhouse under the leadership of Augustus Caesar in 27 BCE. This transformation marked the beginning of an era defined by unprecedented territorial expansion, architectural marvels, and profound cultural influence.
The empire's roots lie in the city of Rome, founded, according to legend, by Romulus in 753 BCE. Over centuries, Rome evolved from a small settlement to a formidable republic, characterized by a complex political system with elected officials and checks on power. However, internal strife, class conflicts, and military ambitions paved the way for the end of the Republic. Julius Caesar’s dictatorship and subsequent assassination in 44 BCE created a power vacuum, leading to a civil war. Octavian, later Augustus, emerged victorious, heralding the Roman Empire’s birth.
Under Augustus, the empire experienced the Pax Romana, a 200-year period of relative peace and stability. Augustus reformed the military, established efficient administrative systems, and initiated grand construction projects. The empire's borders expanded, encompassing territories from Britain to Egypt and from Spain to the Euphrates. Roman legions, renowned for their discipline and engineering prowess, secured and maintained these vast territories, building roads, fortifications, and cities that facilitated control and integration.
The Roman Empire’s society was hierarchical, with a rigid class system. At the top were the patricians, wealthy elites who held significant political power. Below them were the plebeians, free citizens with limited political influence, and the vast numbers of slaves who formed the backbone of the economy. The family unit was central, governed by the paterfamilias, the male head who held absolute authority.
Culturally, the Romans were eclectic, absorbing and adapting elements from the civilizations they encountered, particularly the Greeks. Roman art, literature, and philosophy reflected this synthesis, creating a rich cultural tapestry. Latin, the Roman language, became the lingua franca of the Western world, influencing numerous modern languages.
Roman architecture and engineering achievements were monumental. They perfected the arch, vault, and dome, constructing enduring structures like the Colosseum, Pantheon, and aqueducts. These engineering marvels not only showcased Roman ingenuity but also served practical purposes, from public entertainment to water supply.
ESC Beyond Borders _From EU to You_ InfoPack general.pdf

ESC Beyond Borders _From EU to You_ InfoPack general.pdfFundacja Rozwoju Społeczeństwa Przedsiębiorczego
Wolontariat grupowyRecently uploaded (20)
Chapter 3 - Islamic Banking Products and Services.pptx

Chapter 3 - Islamic Banking Products and Services.pptx
Students, digital devices and success - Andreas Schleicher - 27 May 2024..pptx

Students, digital devices and success - Andreas Schleicher - 27 May 2024..pptx
CLASS 11 CBSE B.St Project AIDS TO TRADE - INSURANCE

CLASS 11 CBSE B.St Project AIDS TO TRADE - INSURANCE
Welcome to TechSoup New Member Orientation and Q&A (May 2024).pdf

Welcome to TechSoup New Member Orientation and Q&A (May 2024).pdf
Digital Tools and AI for Teaching Learning and Research

Digital Tools and AI for Teaching Learning and Research
The Art Pastor's Guide to Sabbath | Steve Thomason

The Art Pastor's Guide to Sabbath | Steve Thomason
Home assignment II on Spectroscopy 2024 Answers.pdf

Home assignment II on Spectroscopy 2024 Answers.pdf
TESDA TM1 REVIEWER FOR NATIONAL ASSESSMENT WRITTEN AND ORAL QUESTIONS WITH A...

TESDA TM1 REVIEWER FOR NATIONAL ASSESSMENT WRITTEN AND ORAL QUESTIONS WITH A...
Mule 4.6 & Java 17 Upgrade | MuleSoft Mysore Meetup #46

Mule 4.6 & Java 17 Upgrade | MuleSoft Mysore Meetup #46
ESC Beyond Borders _From EU to You_ InfoPack general.pdf

ESC Beyond Borders _From EU to You_ InfoPack general.pdf
What is Identity (ID) Theft ?
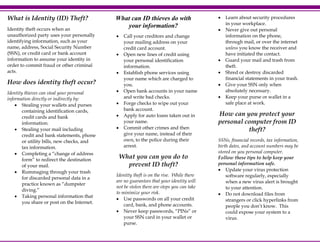
- 1. What is Identity (ID) Theft? Identity theft occurs when an unauthorized party uses your personally identifying information, such as your name, address, Social Security Number (SSN), or credit card or bank account information to assume your identity in order to commit fraud or other criminal acts. What can ID thieves do with your information? • • • How does identity theft occur? Identity thieves can steal your personal information directly or indirectly by: • Stealing your wallets and purses containing identification cards, credit cards and bank information. • Stealing your mail including credit and bank statements, phone or utility bills, new checks, and tax information. • Completing a “change of address form” to redirect the destination of your mail. • Rummaging through your trash for discarded personal data in a practice known as “dumpster diving.” • Taking personal information that you share or post on the Internet. • • • • Call your creditors and change your mailing address on your credit card account. Open new lines of credit using your personal identification information. Establish phone services using your name which are charged to you. Open bank accounts in your name and write bad checks. Forge checks to wipe out your bank account. Apply for auto loans taken out in your name. Commit other crimes and then give your name, instead of their own, to the police during their arrest. What you can you do to prevent ID theft? Identity theft is on the rise. While there are no guarantees that your identity will not be stolen there are steps you can take to minimize your risk. • Use passwords on all your credit card, bank, and phone accounts. • Never keep passwords, “PINs” or your SSN card in your wallet or purse. • • • • • • Learn about security procedures in your workplace. Never give out personal information on the phone, through mail, or over the internet unless you know the receiver and have initiated the contact. Guard your mail and trash from theft. Shred or destroy discarded financial statements in your trash. Give your SSN only when absolutely necessary. Keep your purse or wallet in a safe place at work. How can you protect your personal computer from ID theft? SSNs, financial records, tax information, birth dates, and account numbers may be stored on you personal computer. Follow these tips to help keep your personal information safe. • Update your virus protection software regularly, especially when a new virus alert is brought to your attention. • Do not download files from strangers or click hyperlinks from people you don’t know. This could expose your system to a virus.
- 2. • • Use a firewall program. This will stop uninvited guests from accessing your computer. Use a secure browser to guard the security of your online transactions. What do you do if you are a victim? 1. Contact the fraud departments of each of the three major credit bureaus. (This information can be found on FTC’s ID Theft website or in FTC’s ID Theft booklet) 2. Close the accounts that you know or believe have been tampered with or opened fraudulently. 3. File a police report with your local police and/or the police in the community where the identity theft took place. Where can you find more information on this subject? The information found in this brochure was derived from FTC’s Manual on ID Theft, “ID Theft: When Bad Things Happen to Your Good Name”, which was published in September of 2002. It is available at: www.consumer.gov/idtheft/. You can also access more information in the office of the OIG in Rm. 1135. How can you contact the FTC? Internet www.ftc.gov FTC’s ID Theft Hotline 1-877-IDTHEFT (438-4338) OFFICE OF INSPECTOR GENERAL (OIG) Write Identity Theft Clearinghouse Federal Trade Commission 600 Pennsylvania Avenue, NW Washington, DC 20580 Contact OIG Internet oig.nsf.gov Telephone 703 292-7100 Fax 703 292-9158/9159 Write National Science Foundation Office of Inspector General 4201 Wilson Boulevard Arlington, VA 22230 Identity Theft: What can you do to protect yourself?
