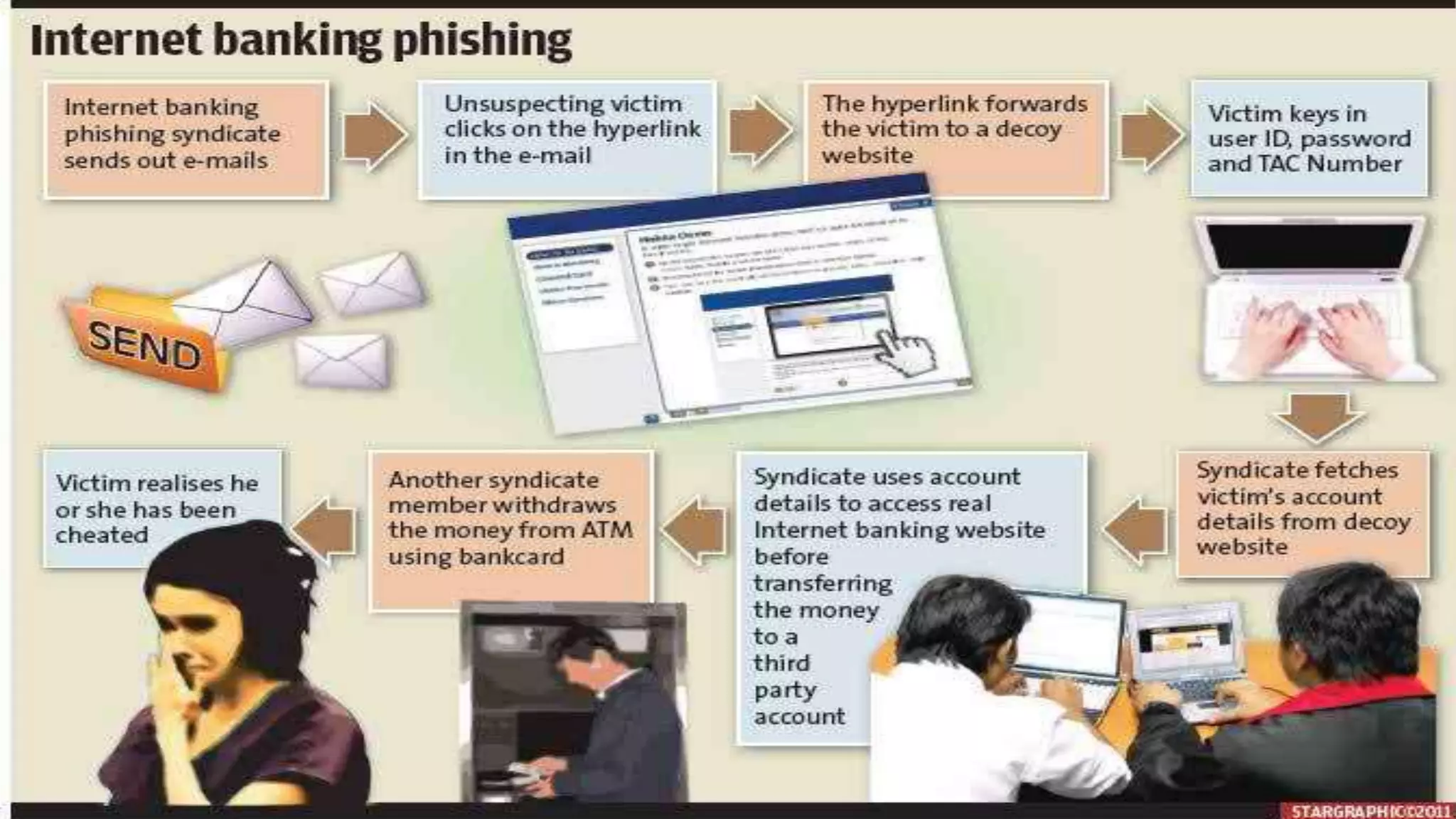
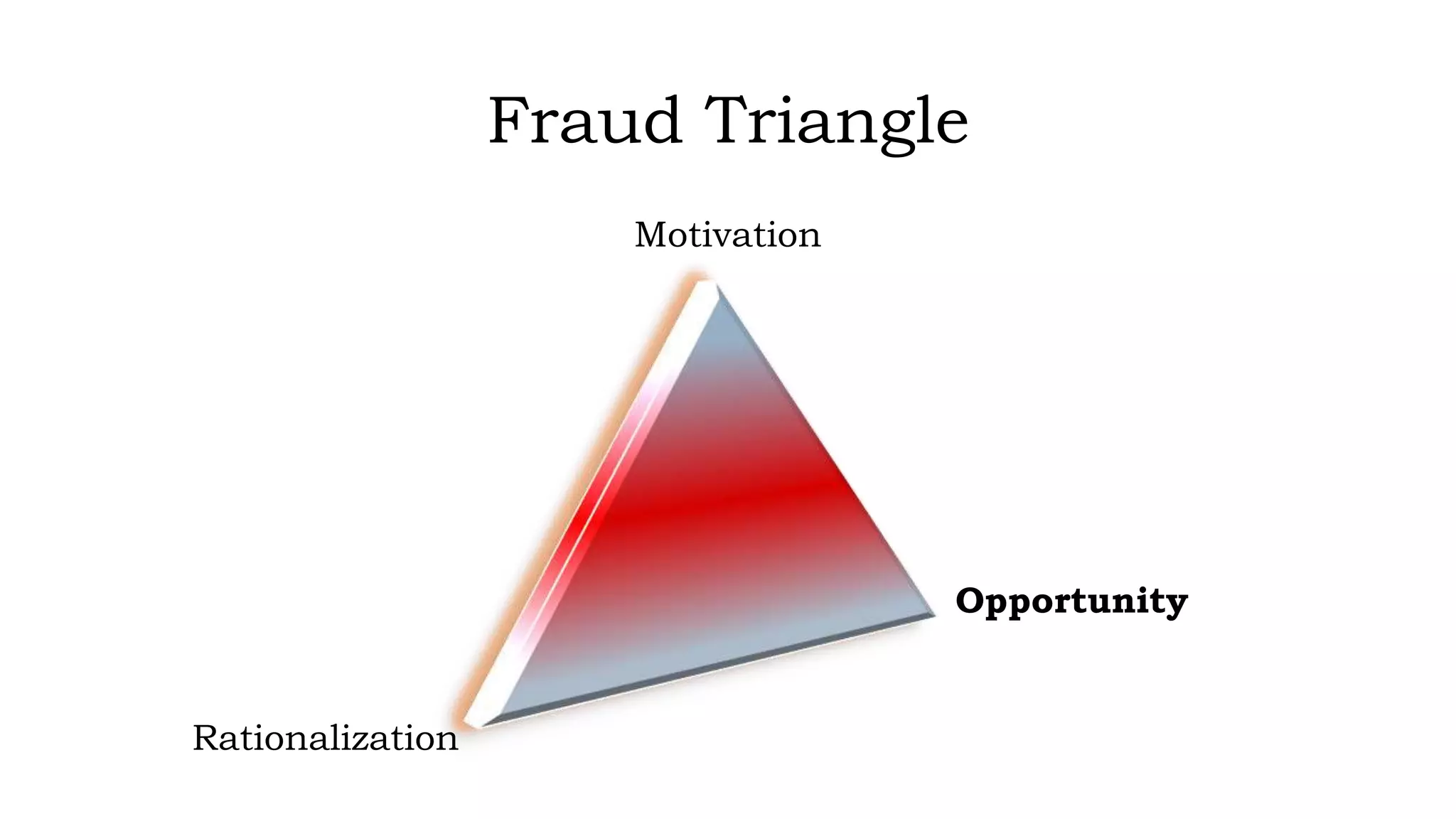
This document discusses prevention of fraud and forgery in internet banking. It begins by defining fraud and forgery, explaining how they differ. It then explains how internet banking fraud often occurs through phishing attacks, where fraudsters steal login credentials through deceptive emails or websites. The document outlines the typical process fraudsters use, from obtaining details to transferring money. It emphasizes that awareness is key to prevention and provides tips for customers to avoid falling victim, such as using strong unique passwords, updating security software, and being wary of unsolicited communications asking for private information.






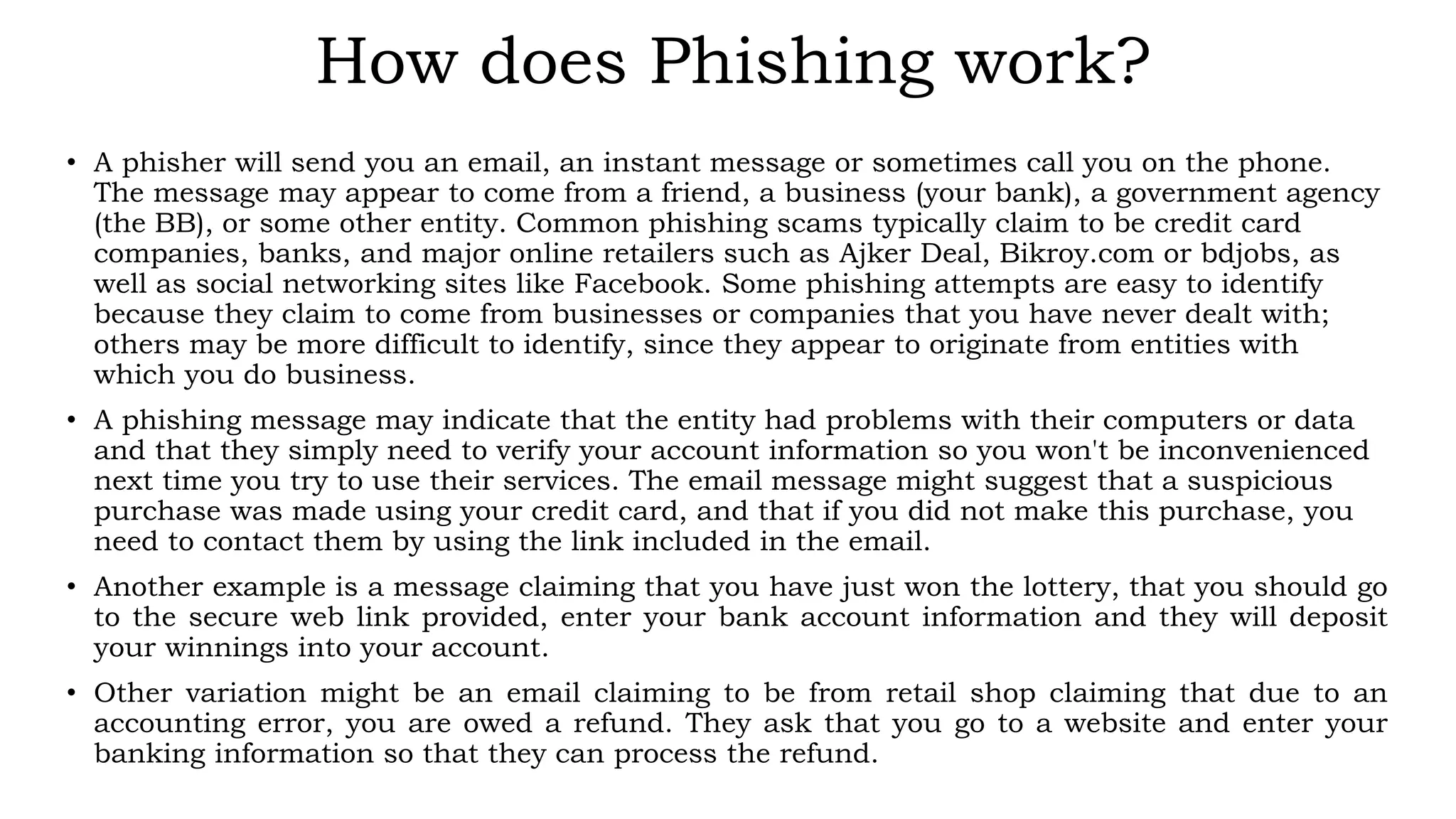
![Example of a Phishing email
From: Altitude Team [rj@calpoly.edu]
Sent: Friday, June 29, 2012 2:42 PM
Subject: Internet Banking Account Deletion Confirmation
Altitude! SERVICE ANNOUNCEMENT
Dear Account Holder,
1. You have requested your Internet Banking Account on June 29, 2012 at 11:02 PM BST to be
deactivated and deleted from a location in with this IP number; 201.130.47.33.
2. Click on (http://localhost/pib.primebank.com.bd/login.html) to cancel this request after log
into your account; else your internet banking account will be deactivated and deleted within 24 hours
3. Do not share your password with anyone for your security purpose.
Thank You for Being A Loyal Altitude User
Altitude Team](https://image.slidesharecdn.com/dec776bd-df80-4be1-afec-c6fc6cb3c972-160703071801/75/IB-Fraud-12-2048.jpg)