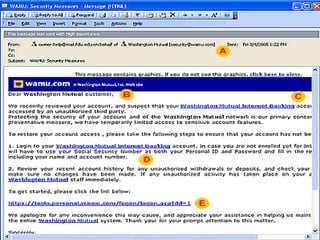
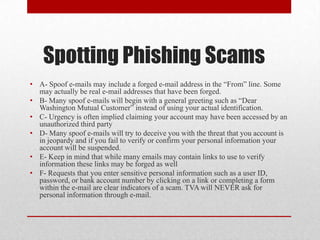
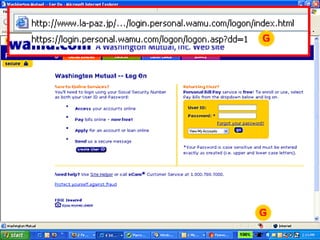
The document discusses various methods of social engineering such as phishing, baiting, and ransomware that aim to manipulate people into divulging private information. It provides examples of common social engineering scams like phishing emails and explains how to identify potential scams and protect personal information. The document also offers advice on what to do if a social engineering attempt was successful, such as immediately contacting IT security and changing passwords.