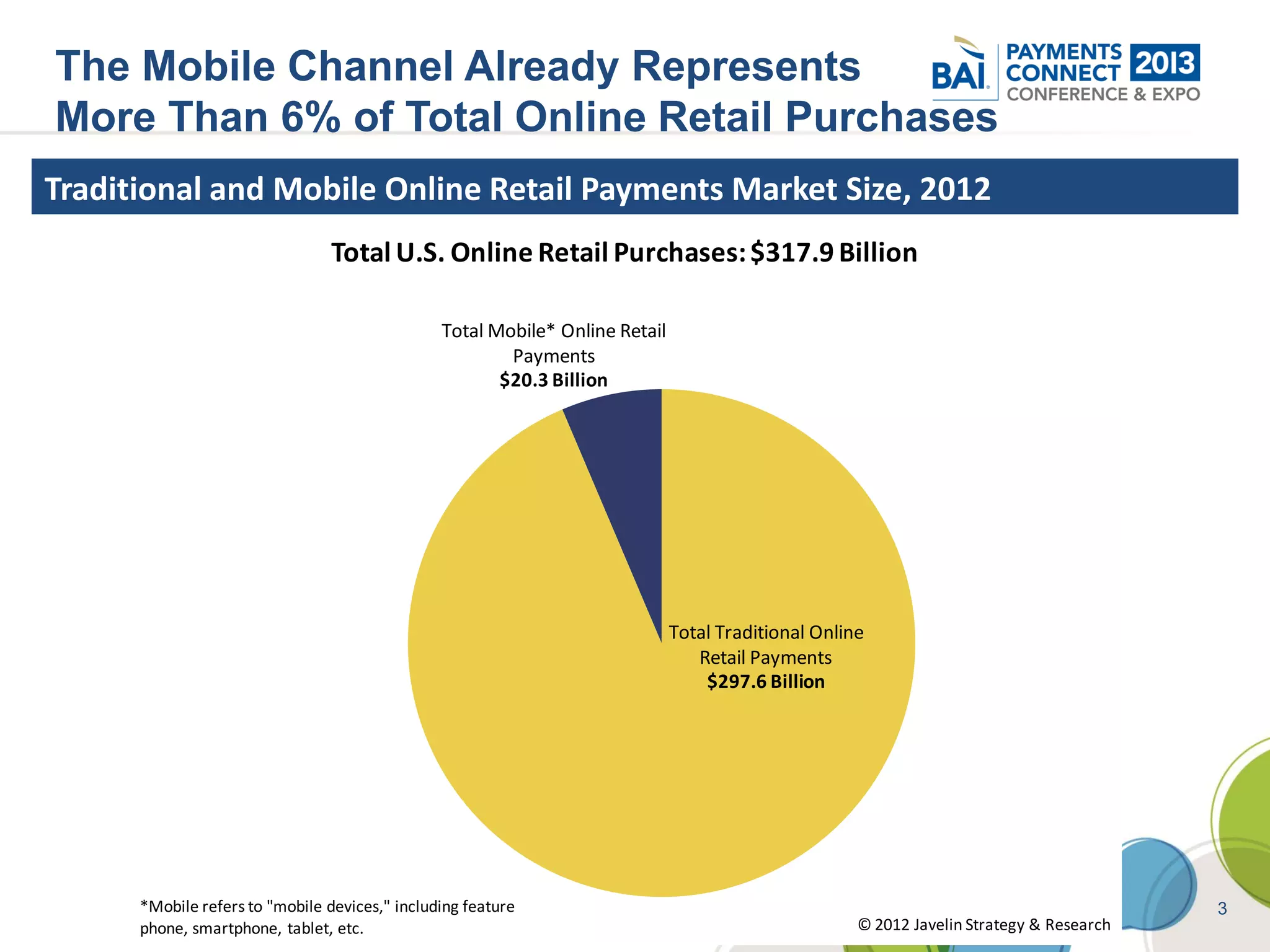
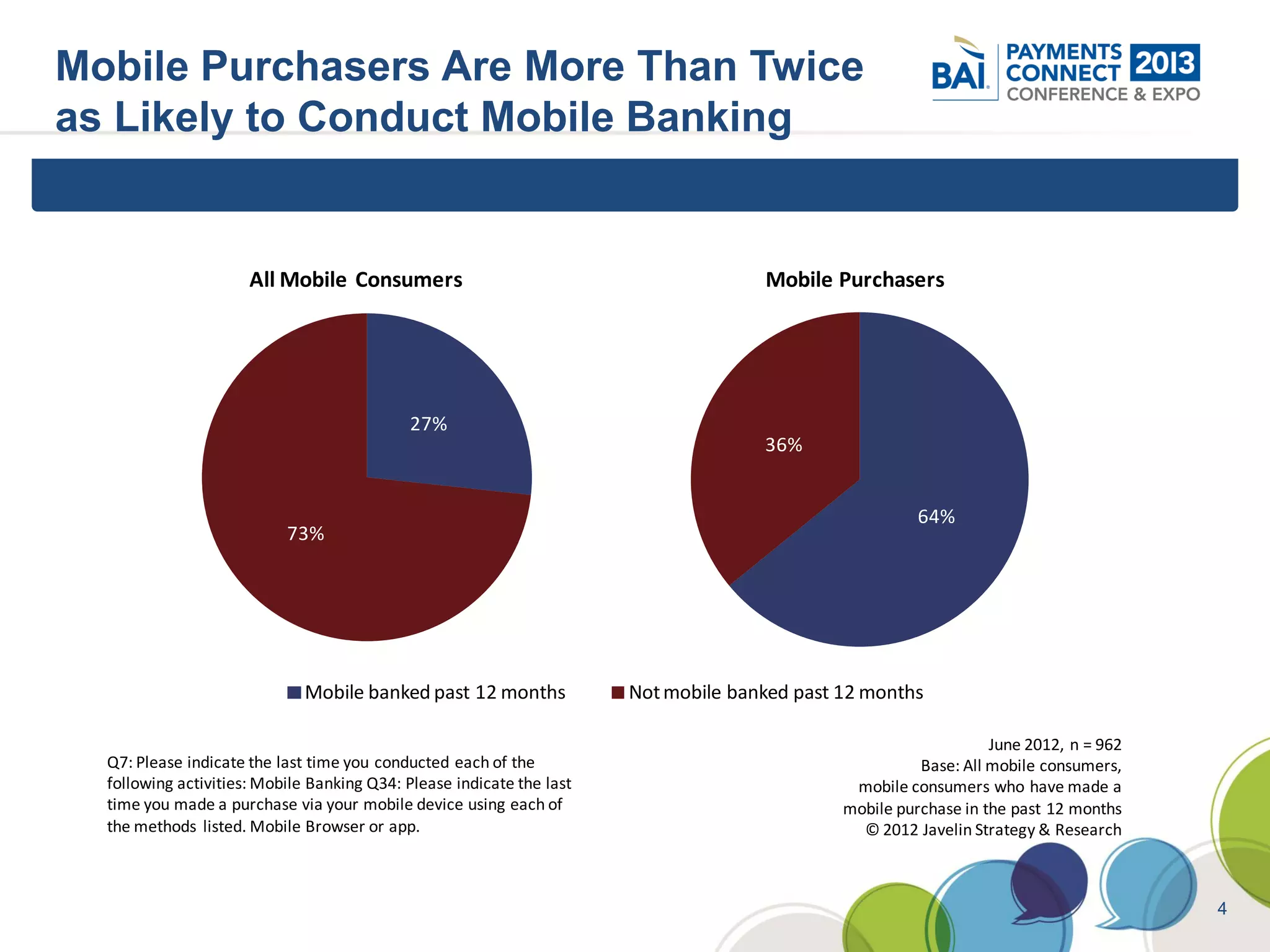
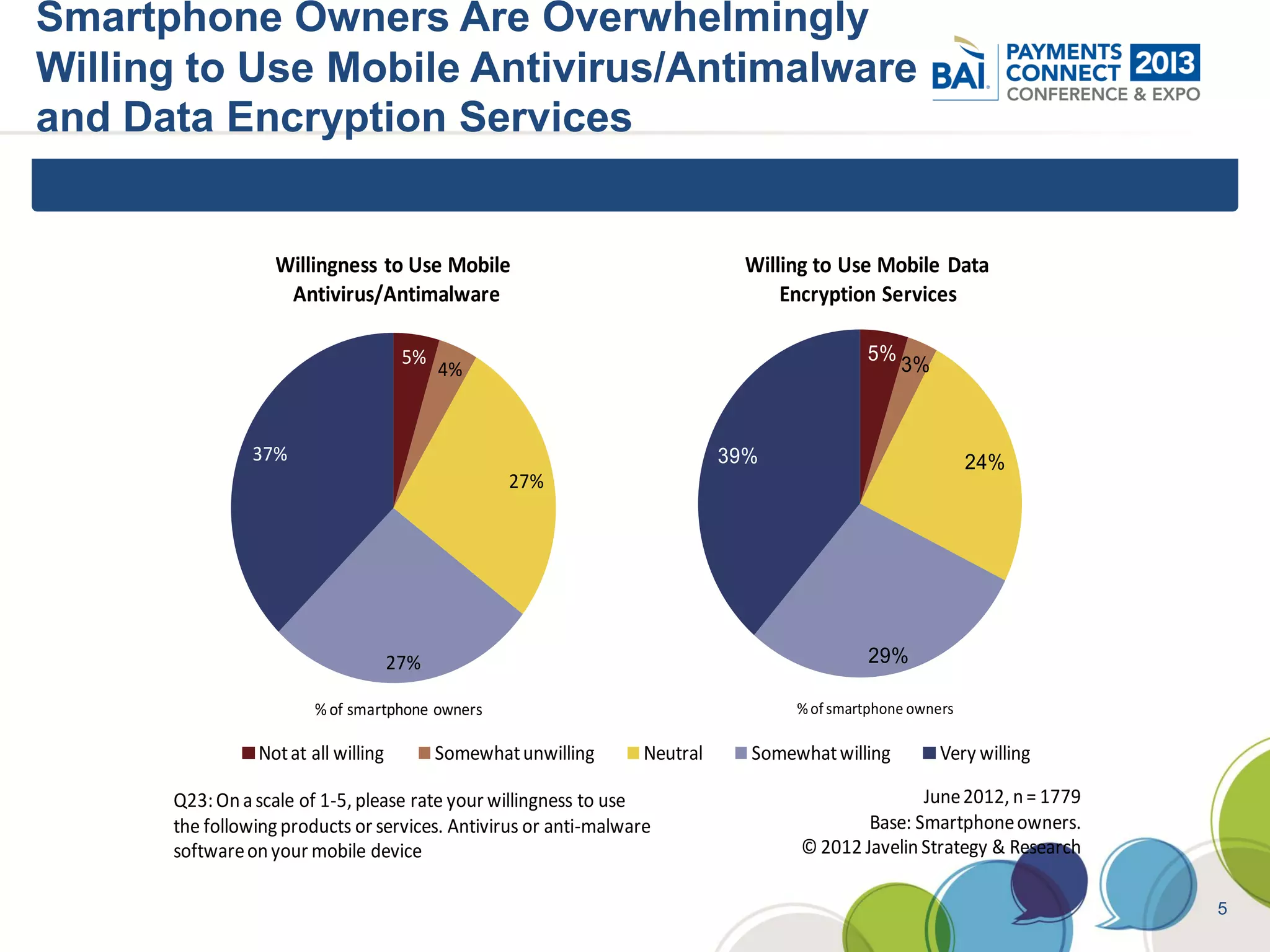
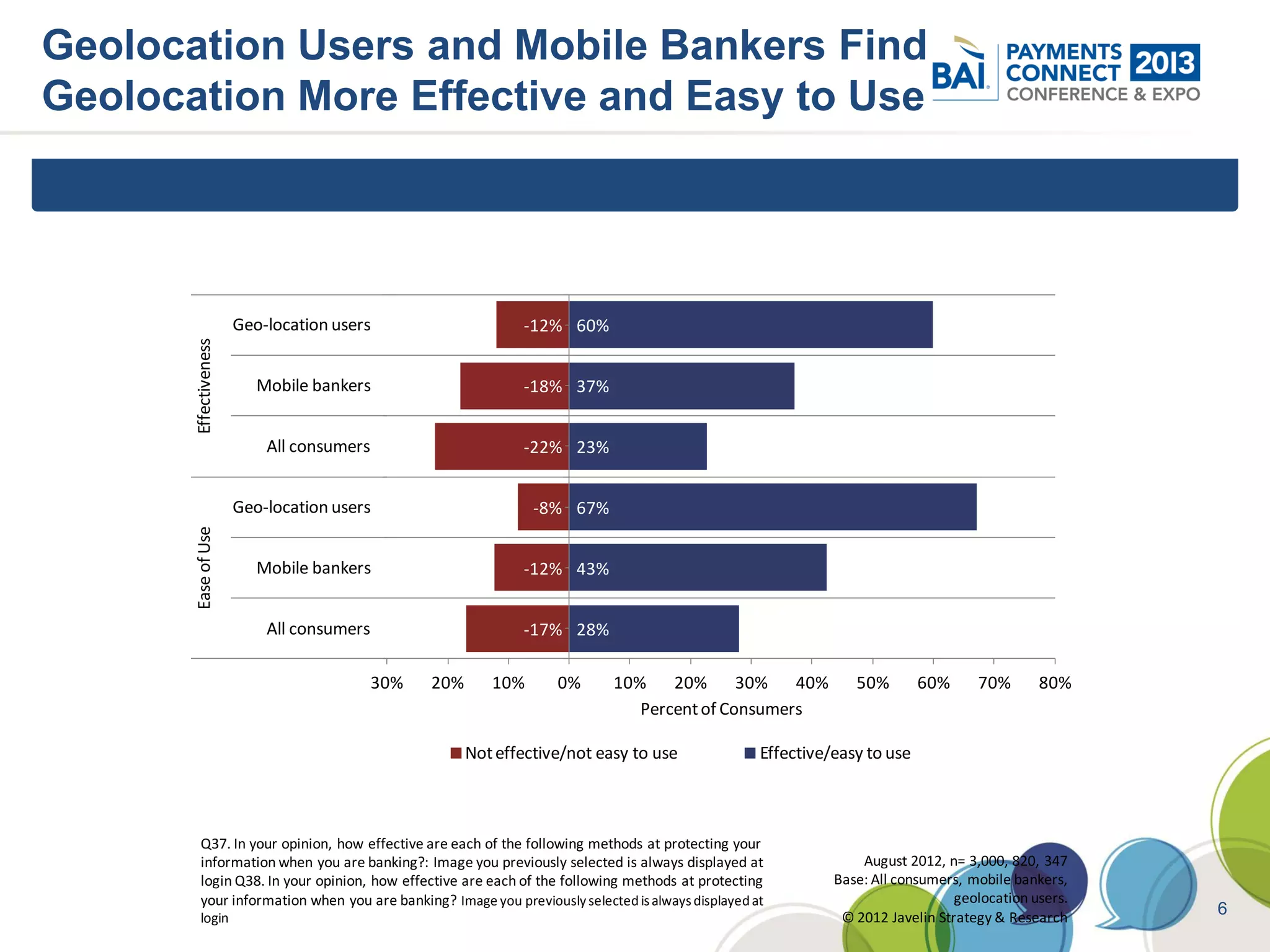
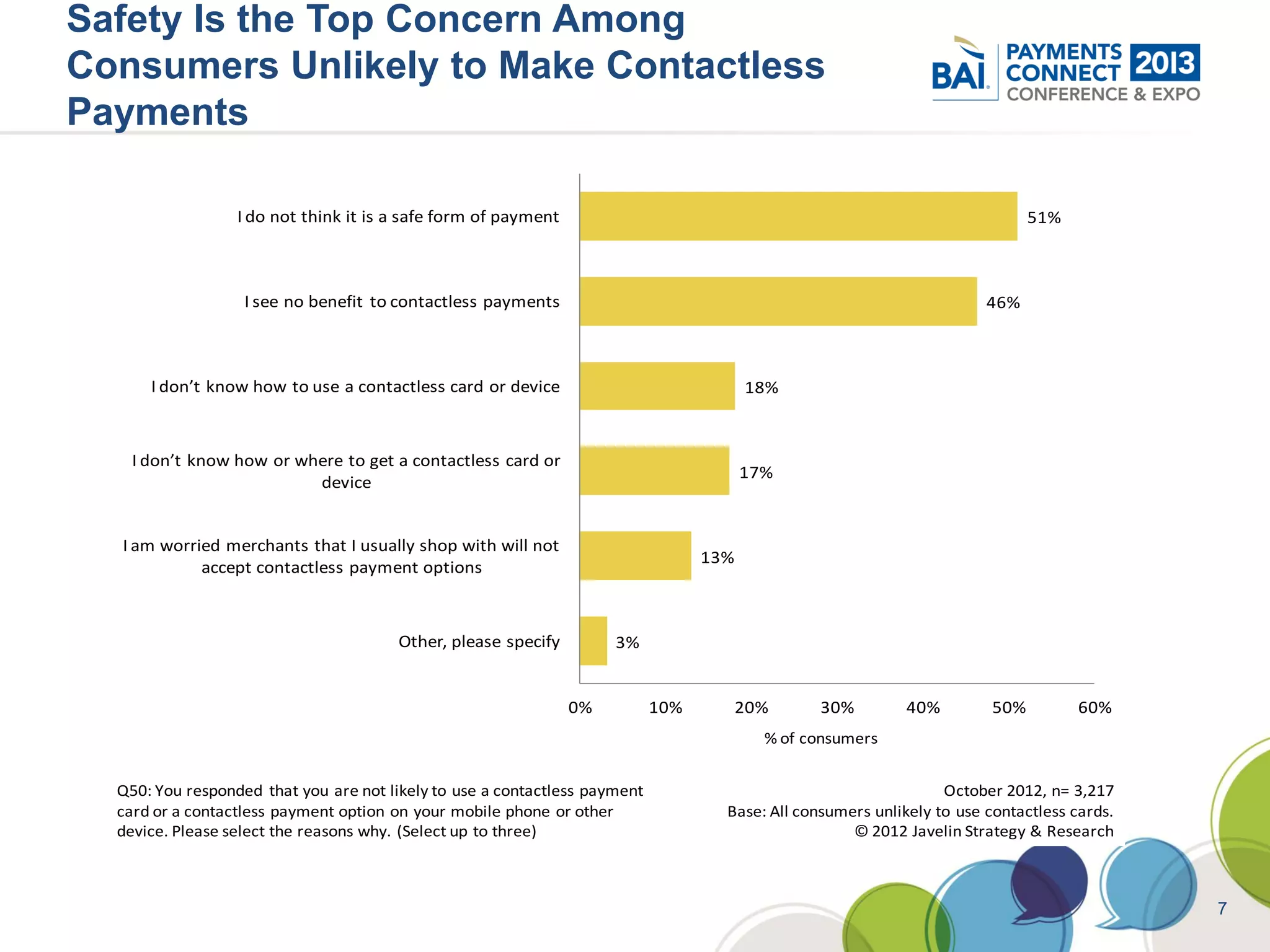
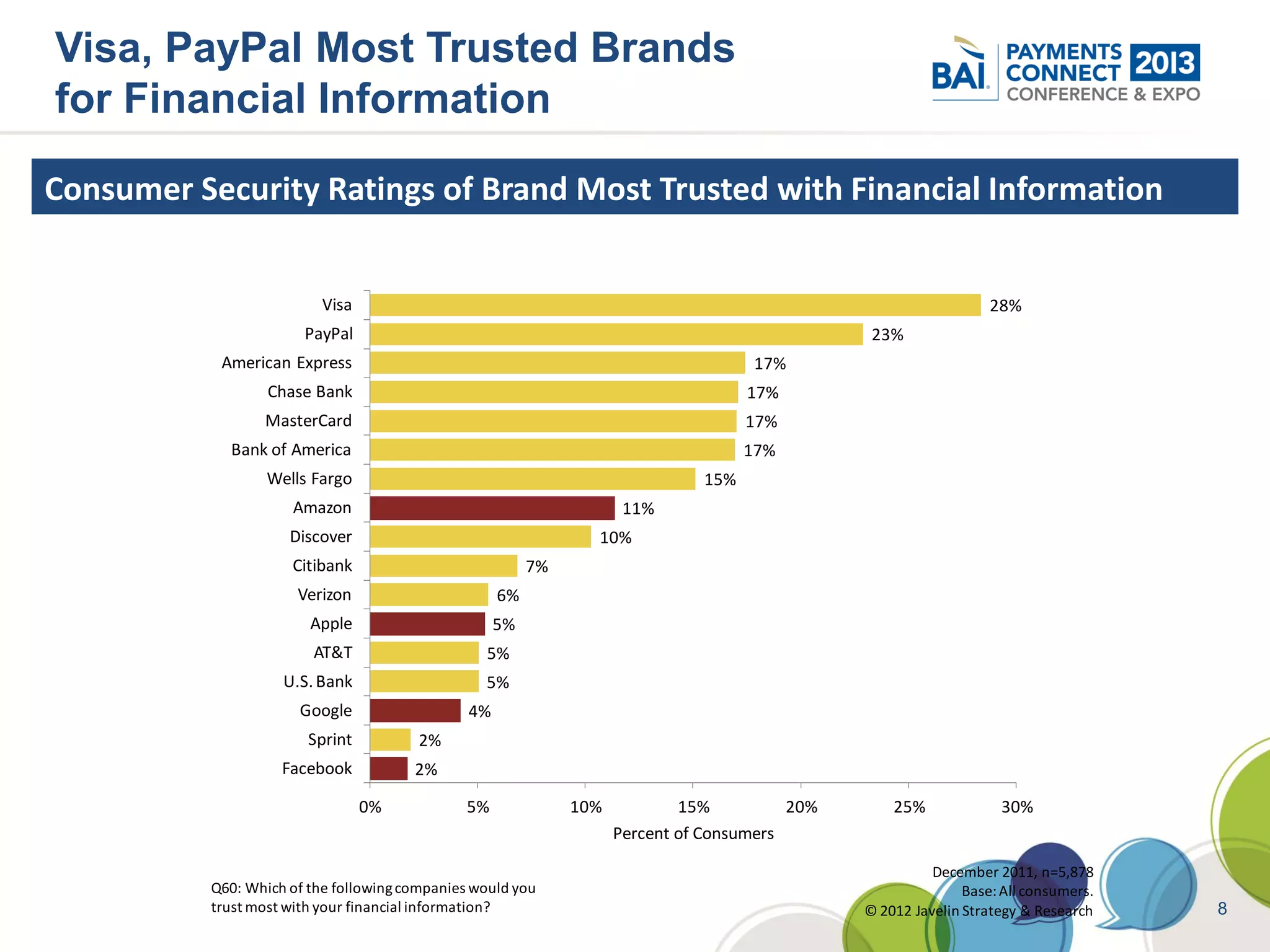
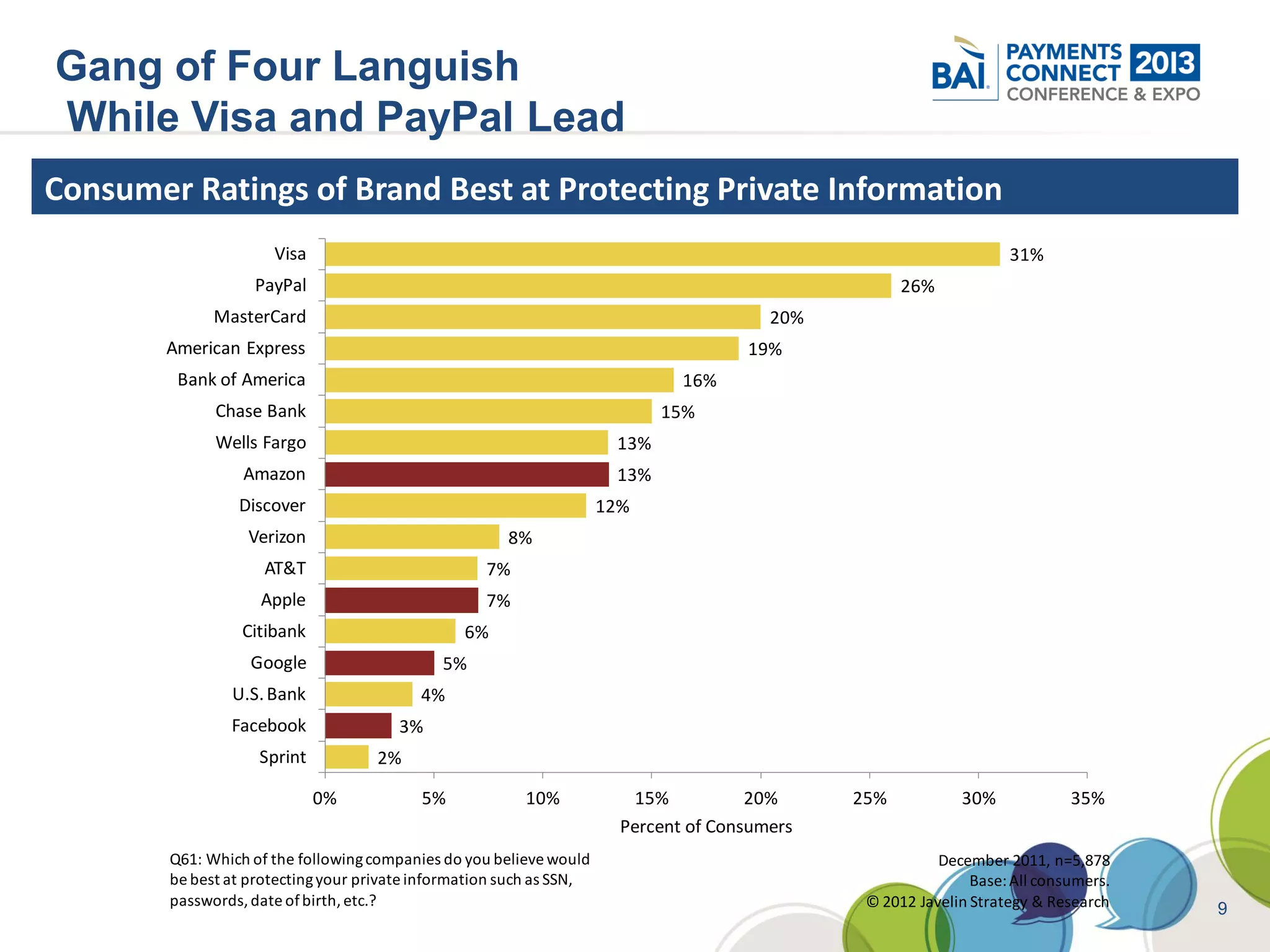
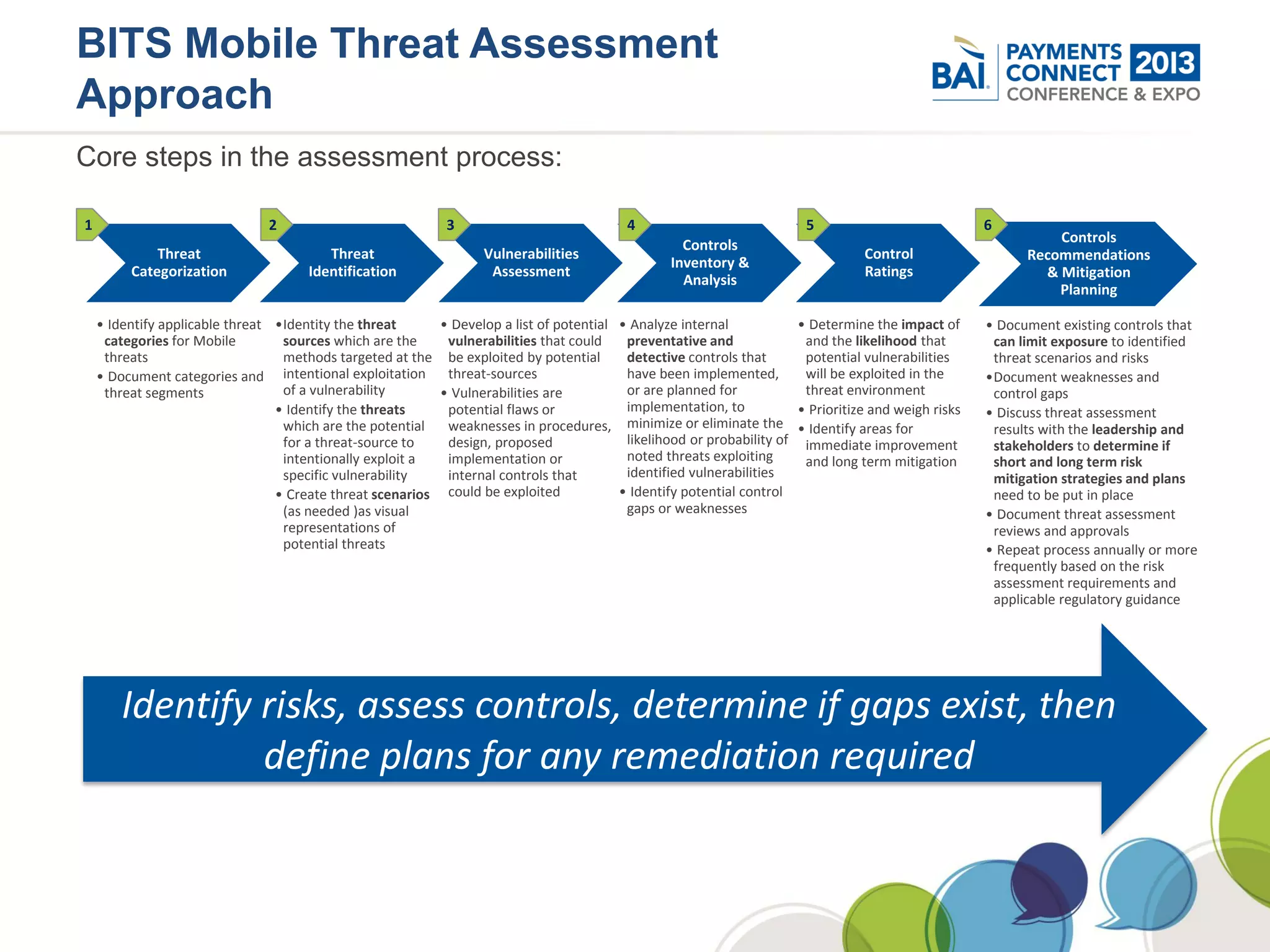
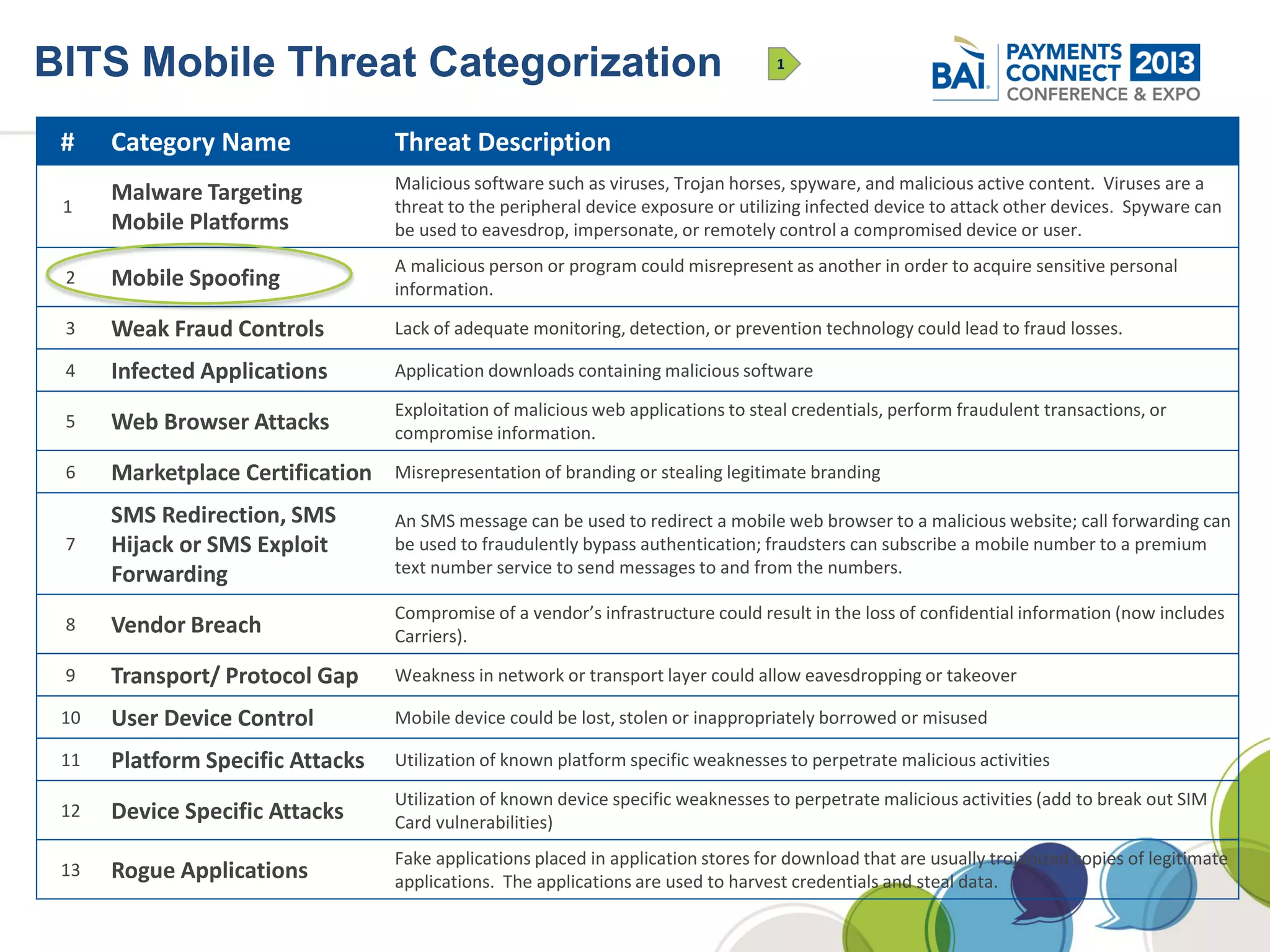
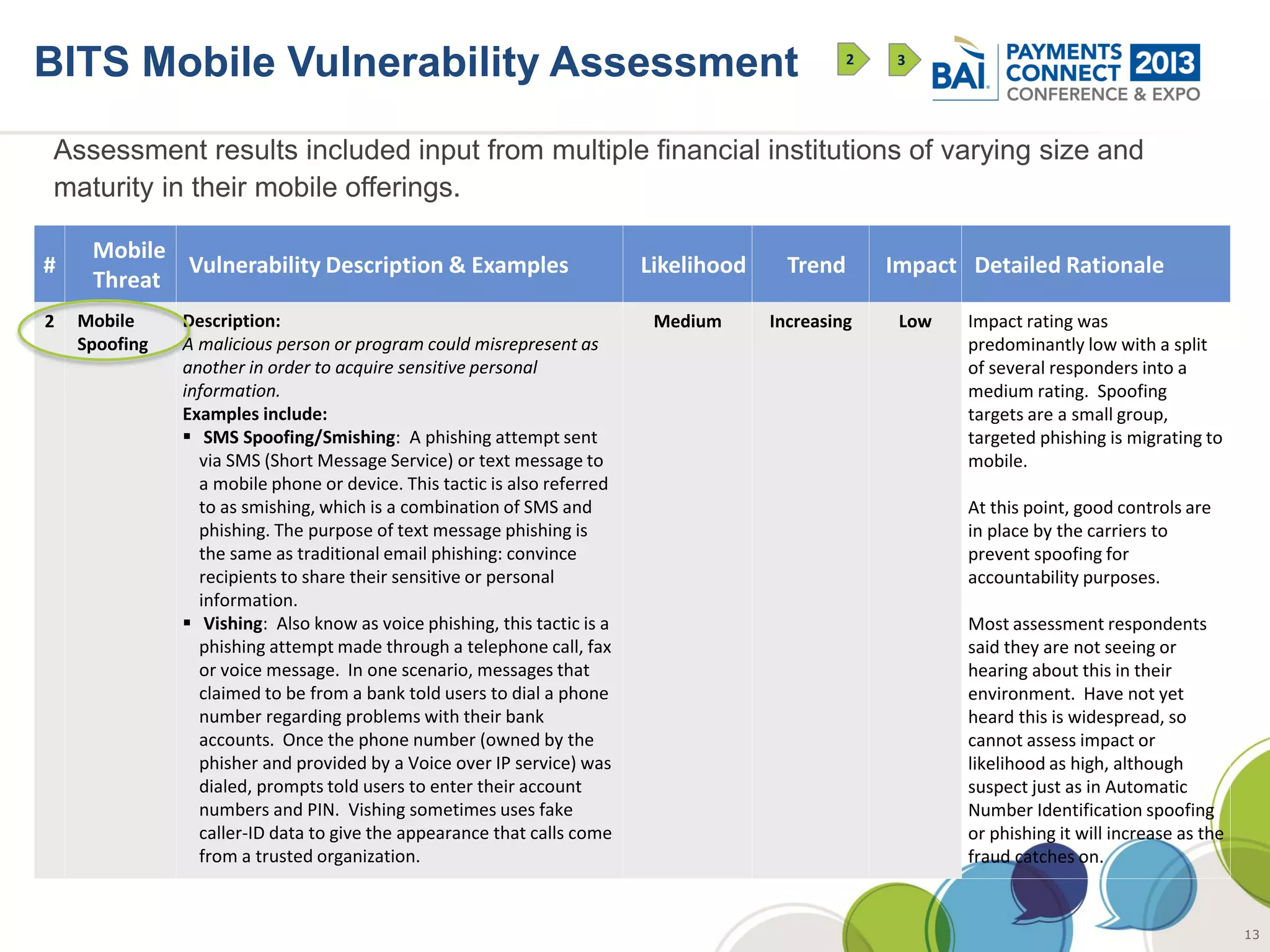
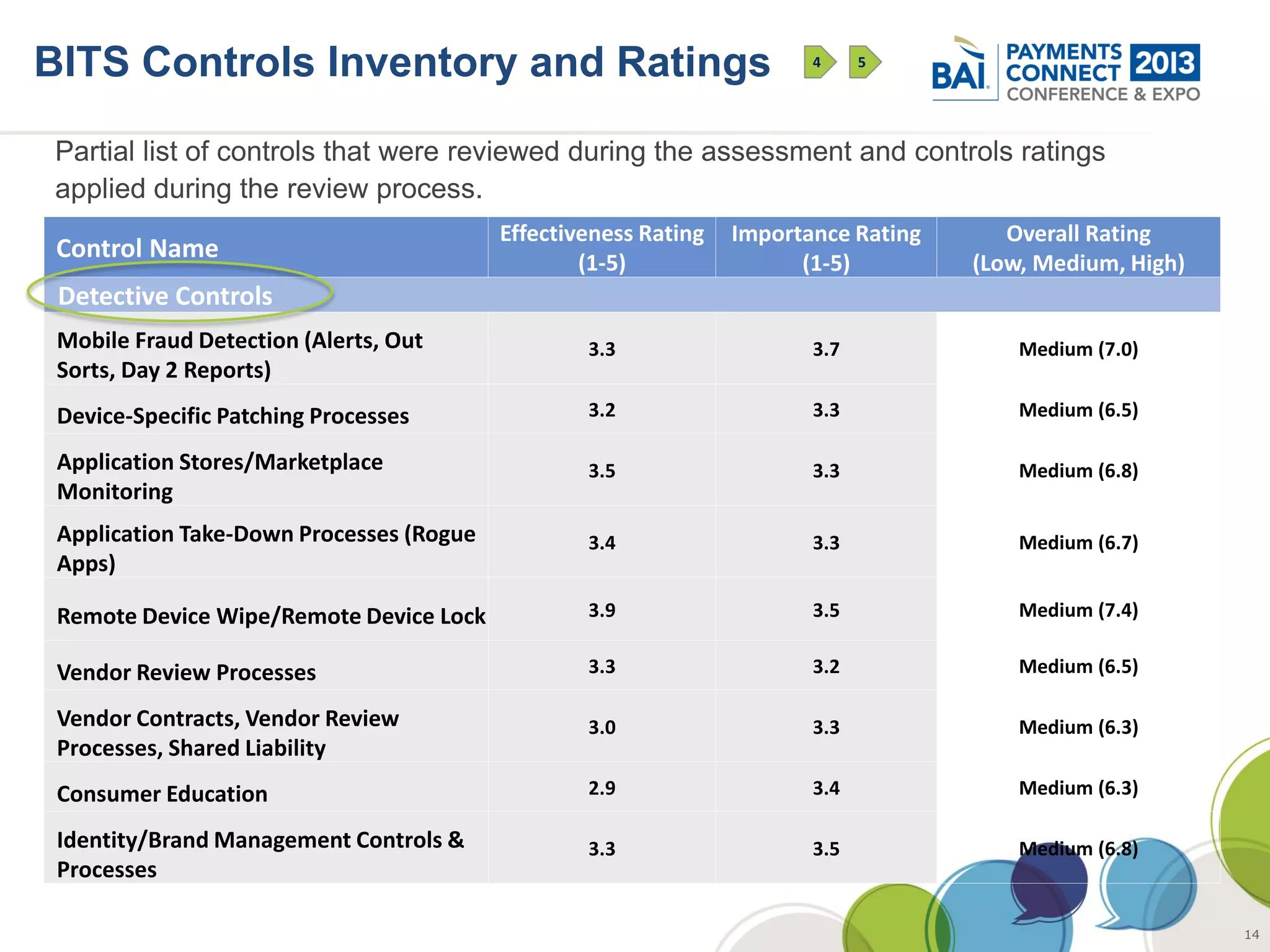
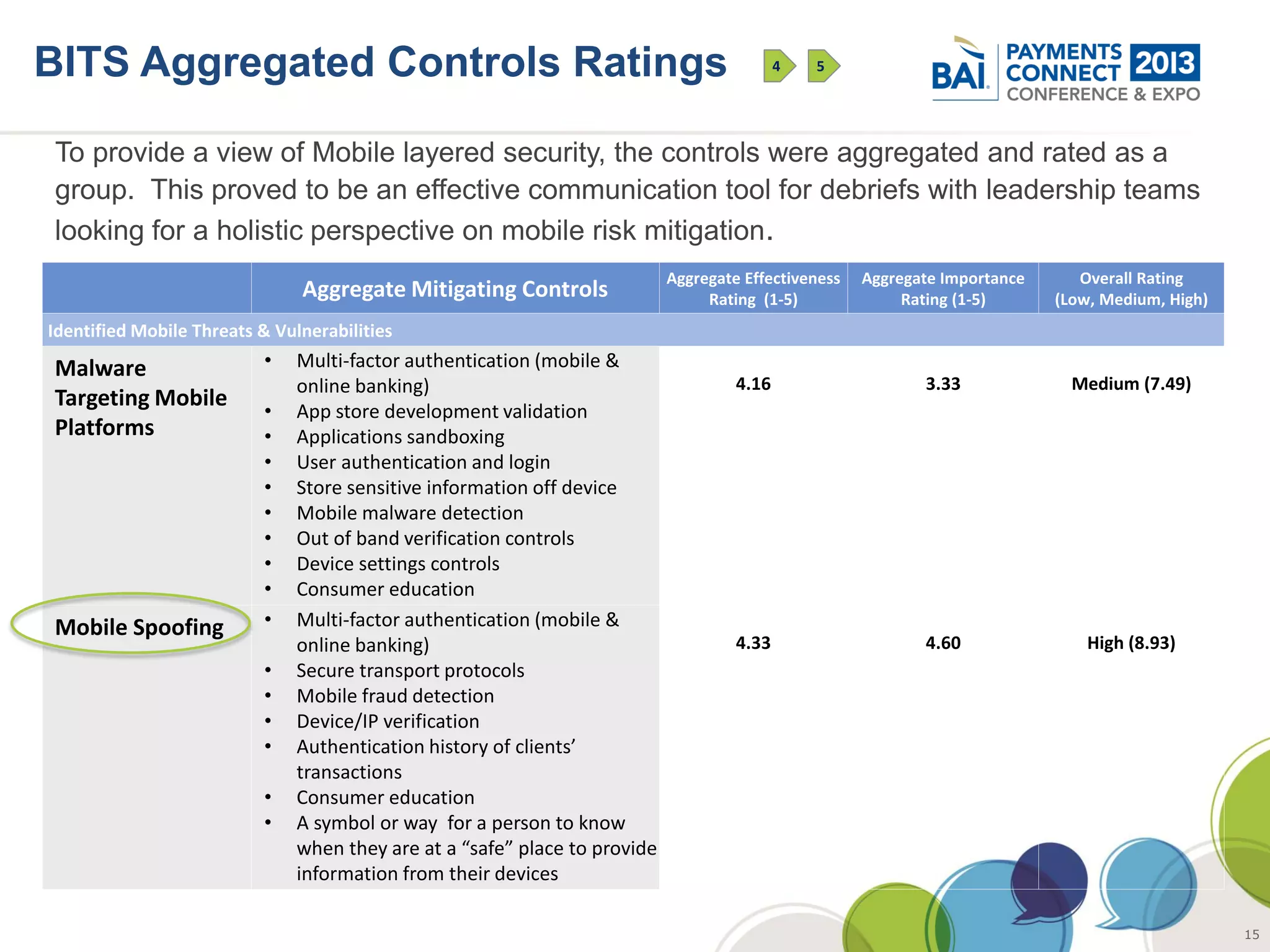
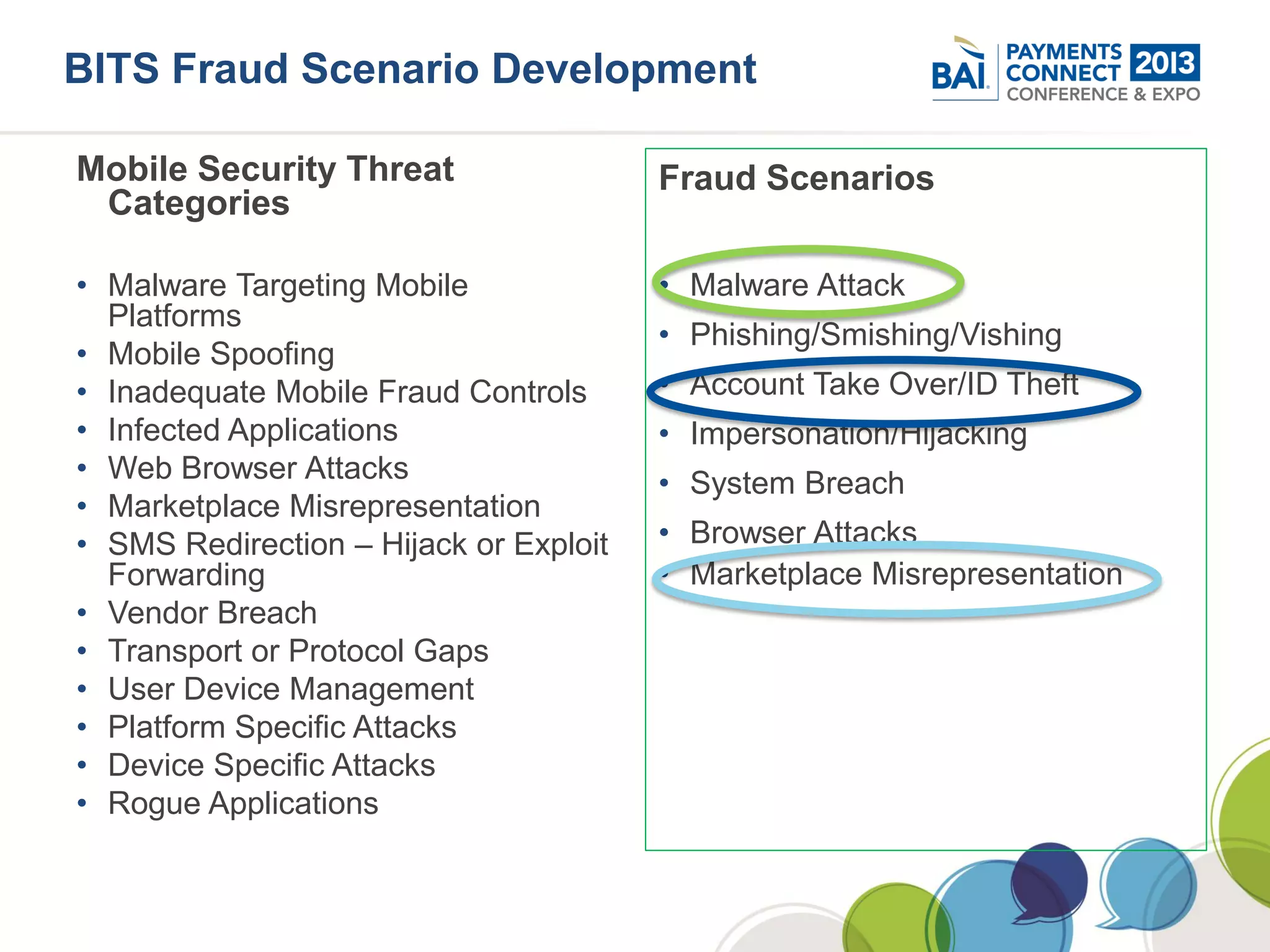
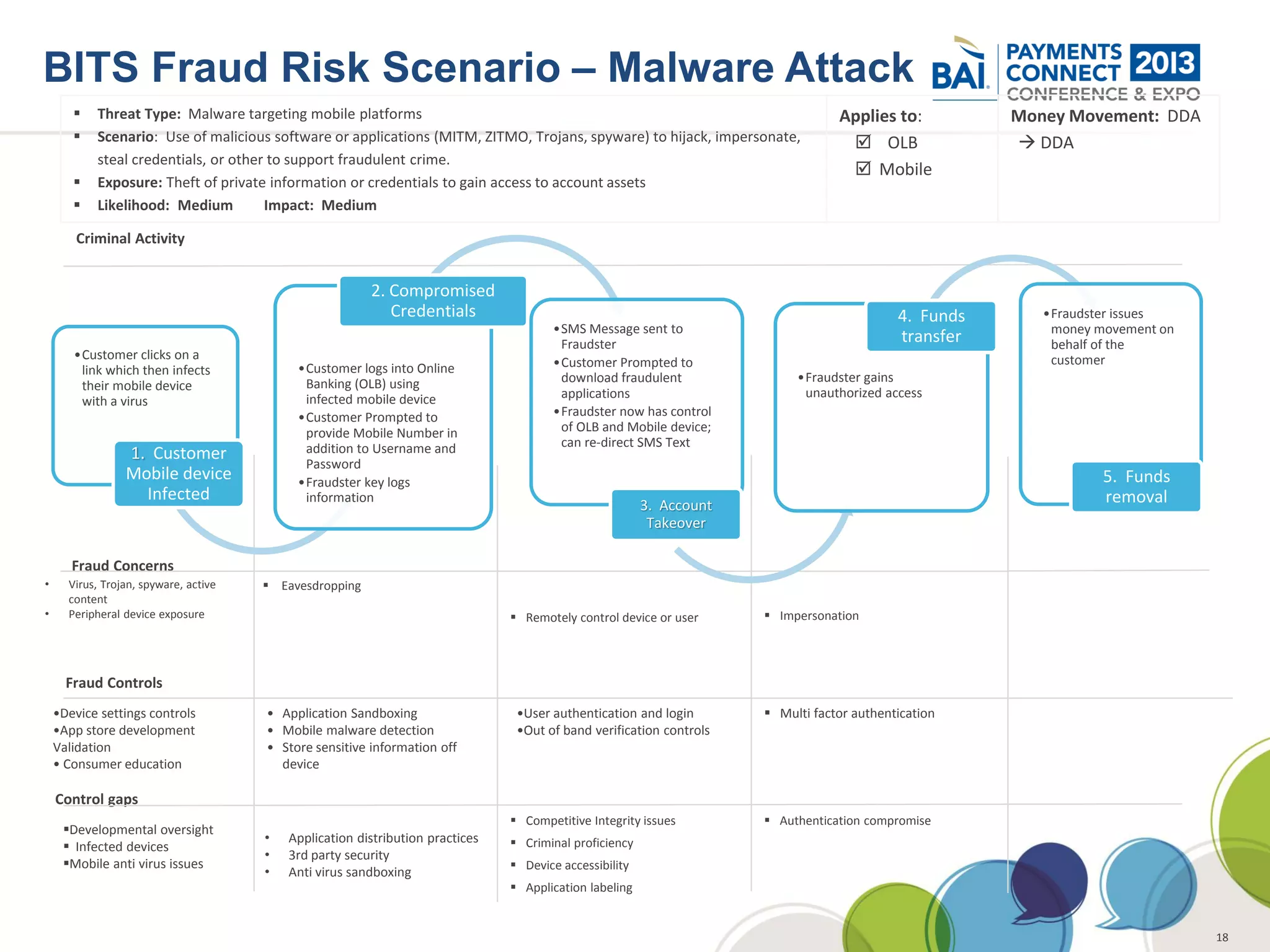
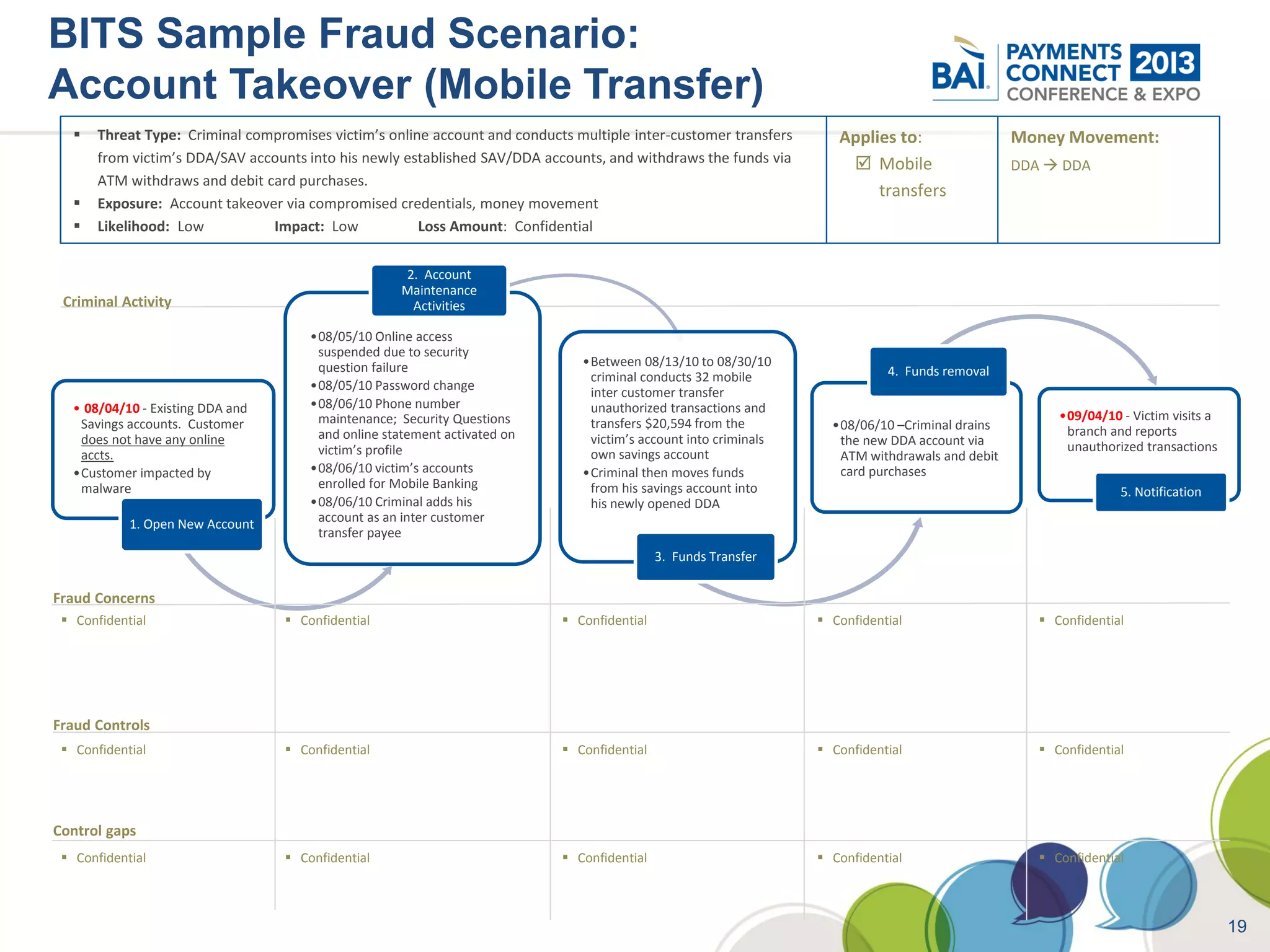
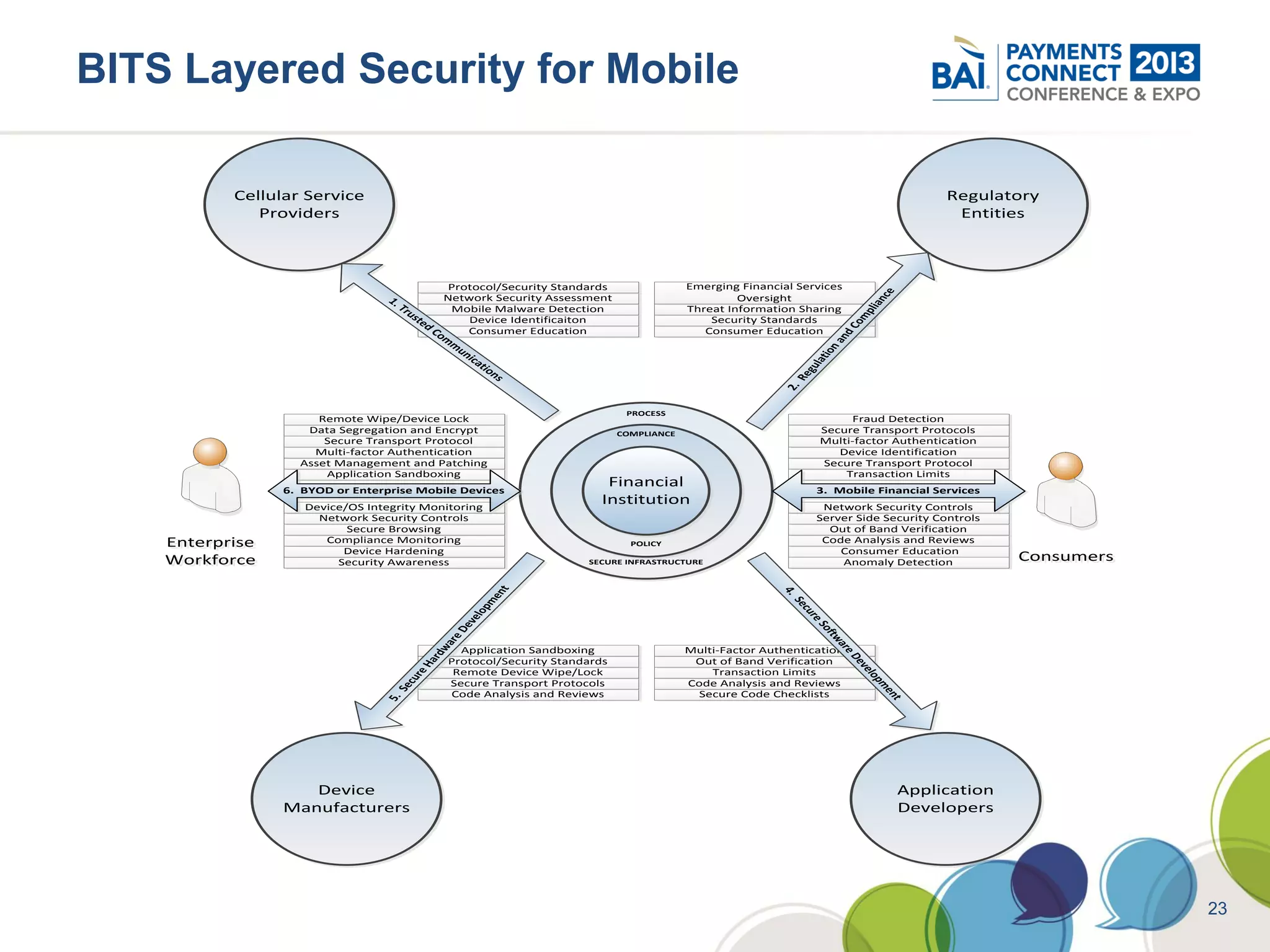
The document discusses mobile payments fraud and security issues. It provides an overview of mobile payments and analyzes threats and vulnerabilities. It then discusses fraud risk and mitigation strategies, and the regulatory outlook for mobile banking and payments. Key points include that mobile payments already represent over 6% of online retail purchases, and smartphone owners are willing to use security services like antivirus and data encryption. Major brands like Visa and PayPal are most trusted with financial information. The document uses a methodology based on NIST guidelines to assess threats and vulnerabilities, rate controls, and make recommendations to address control gaps and long-term risks.