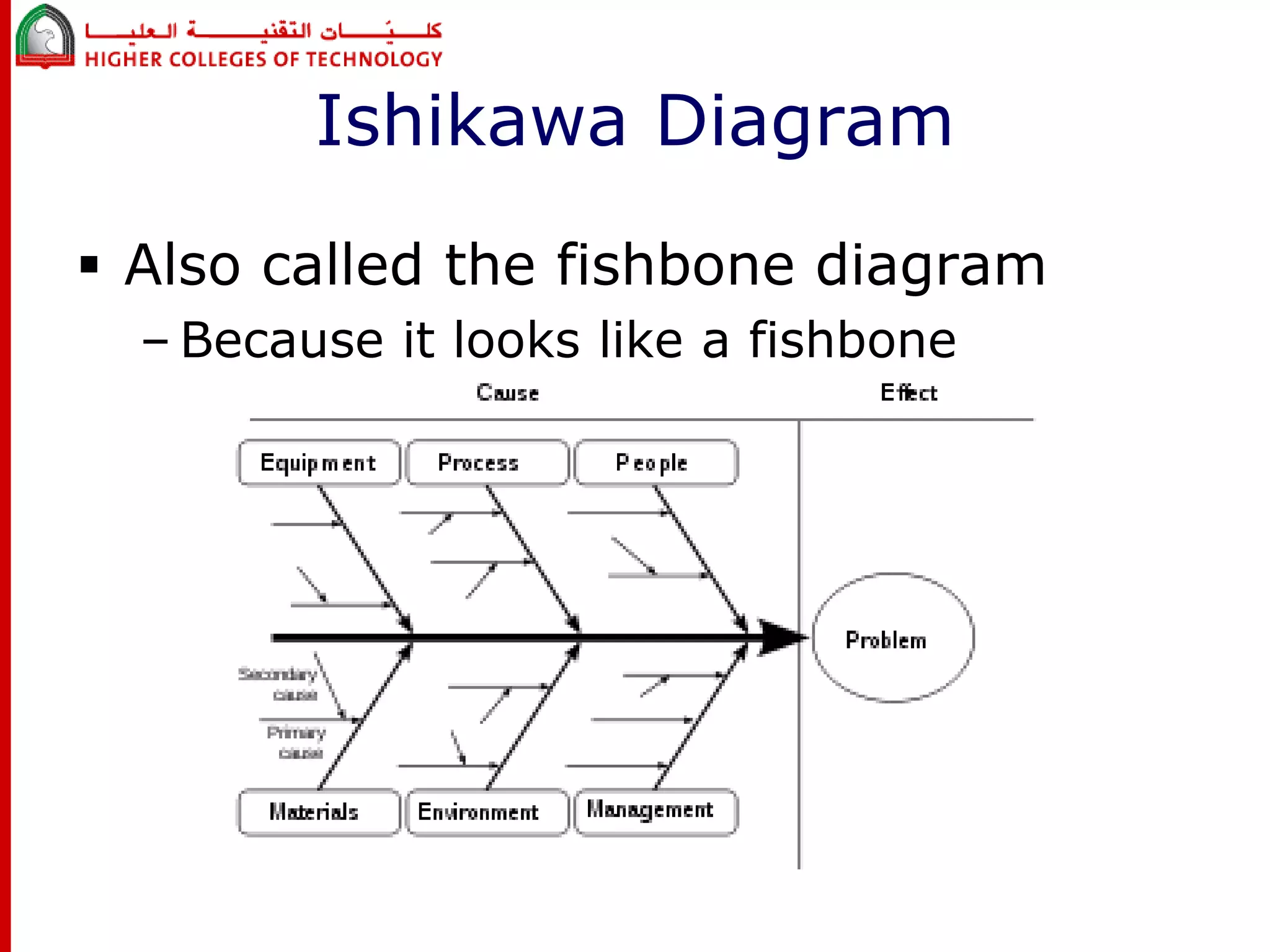
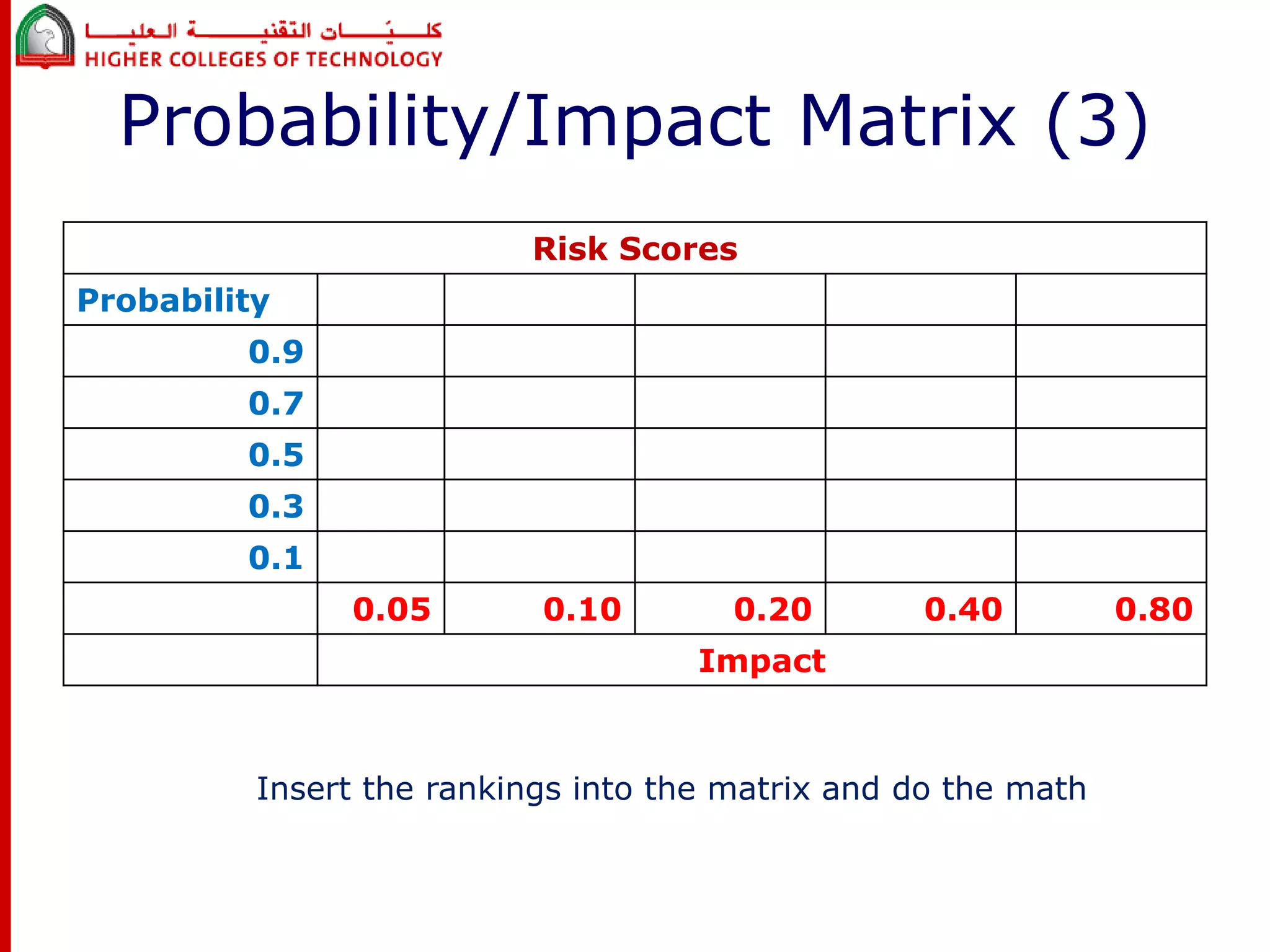
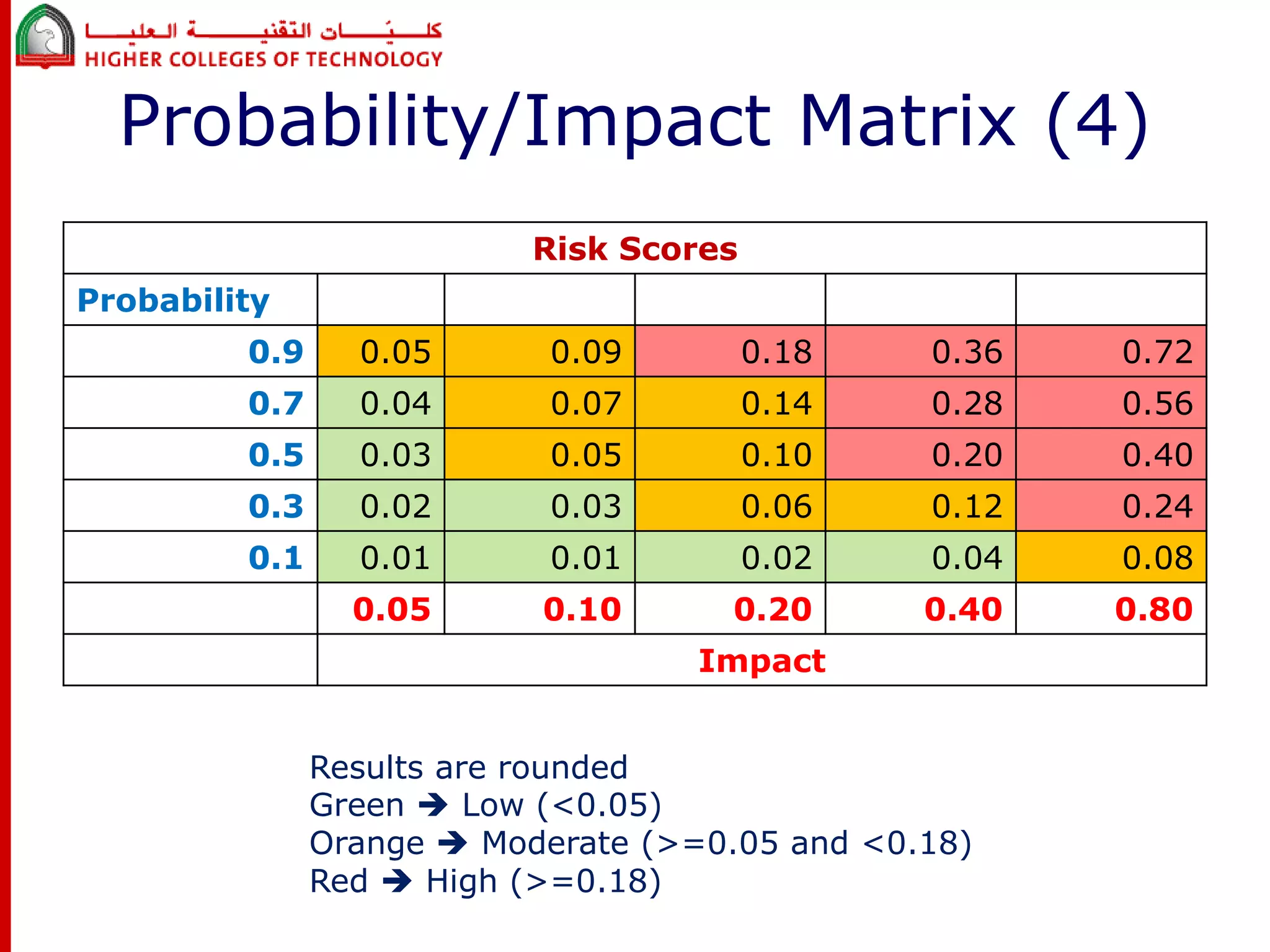
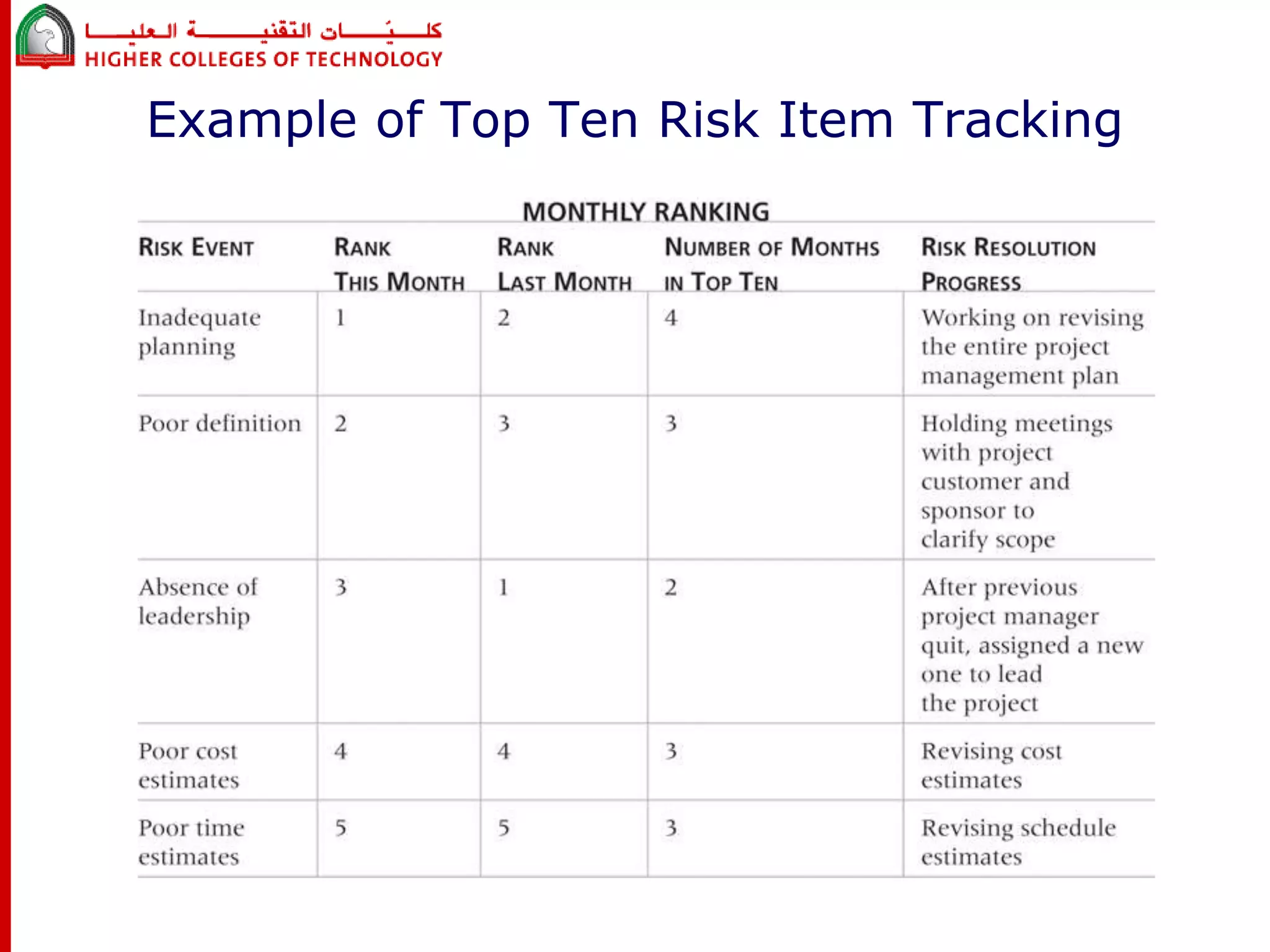
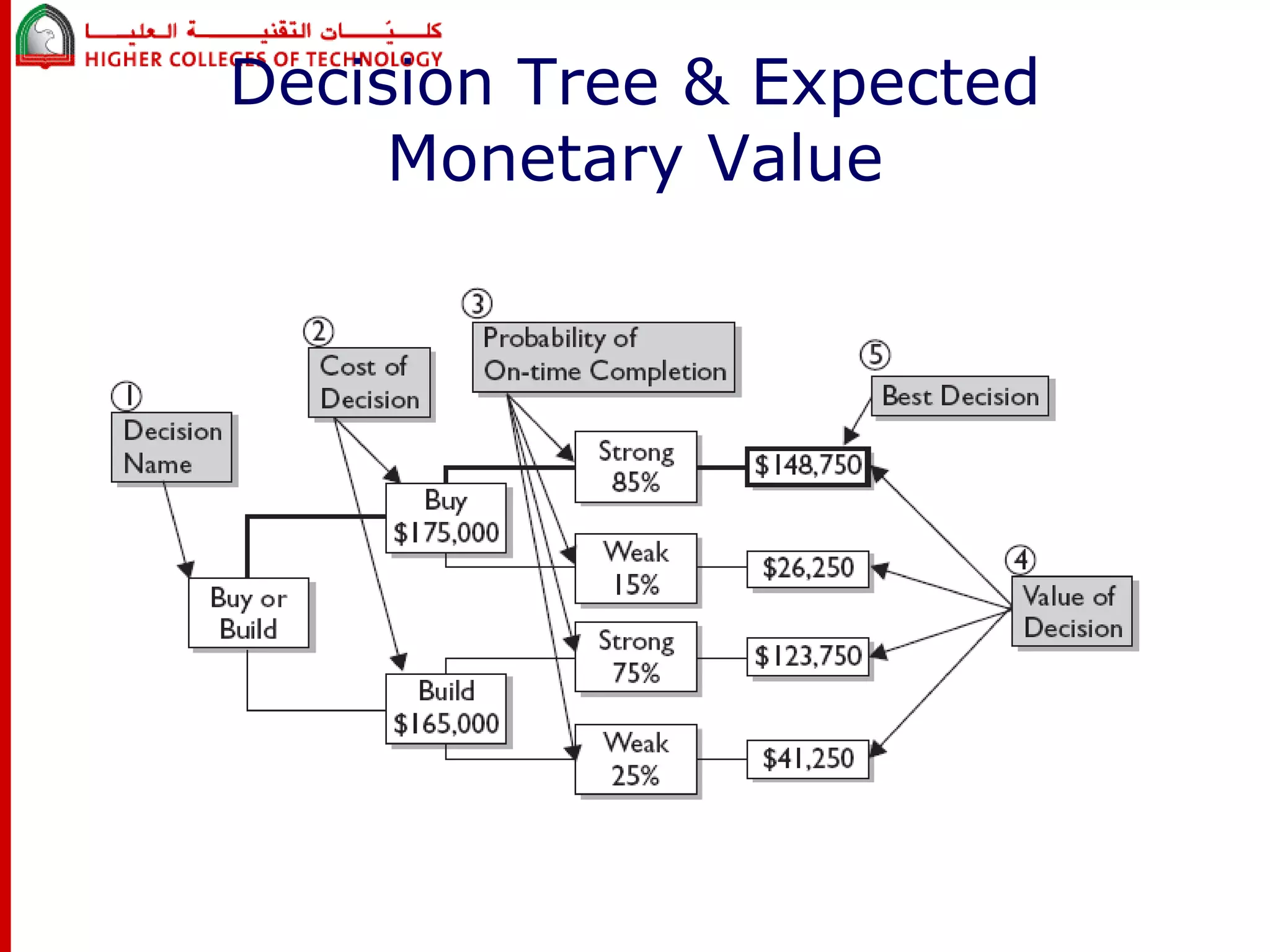
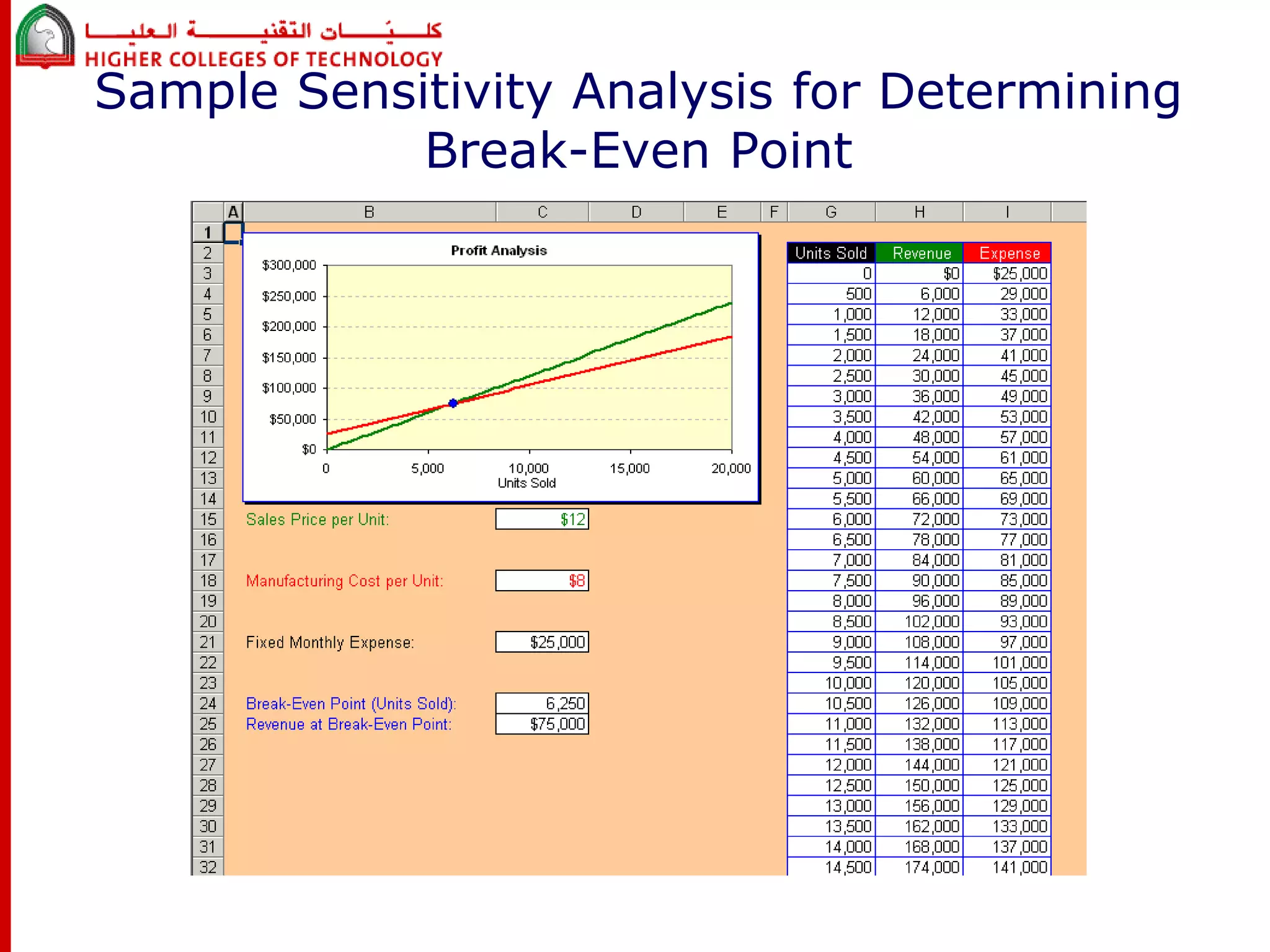
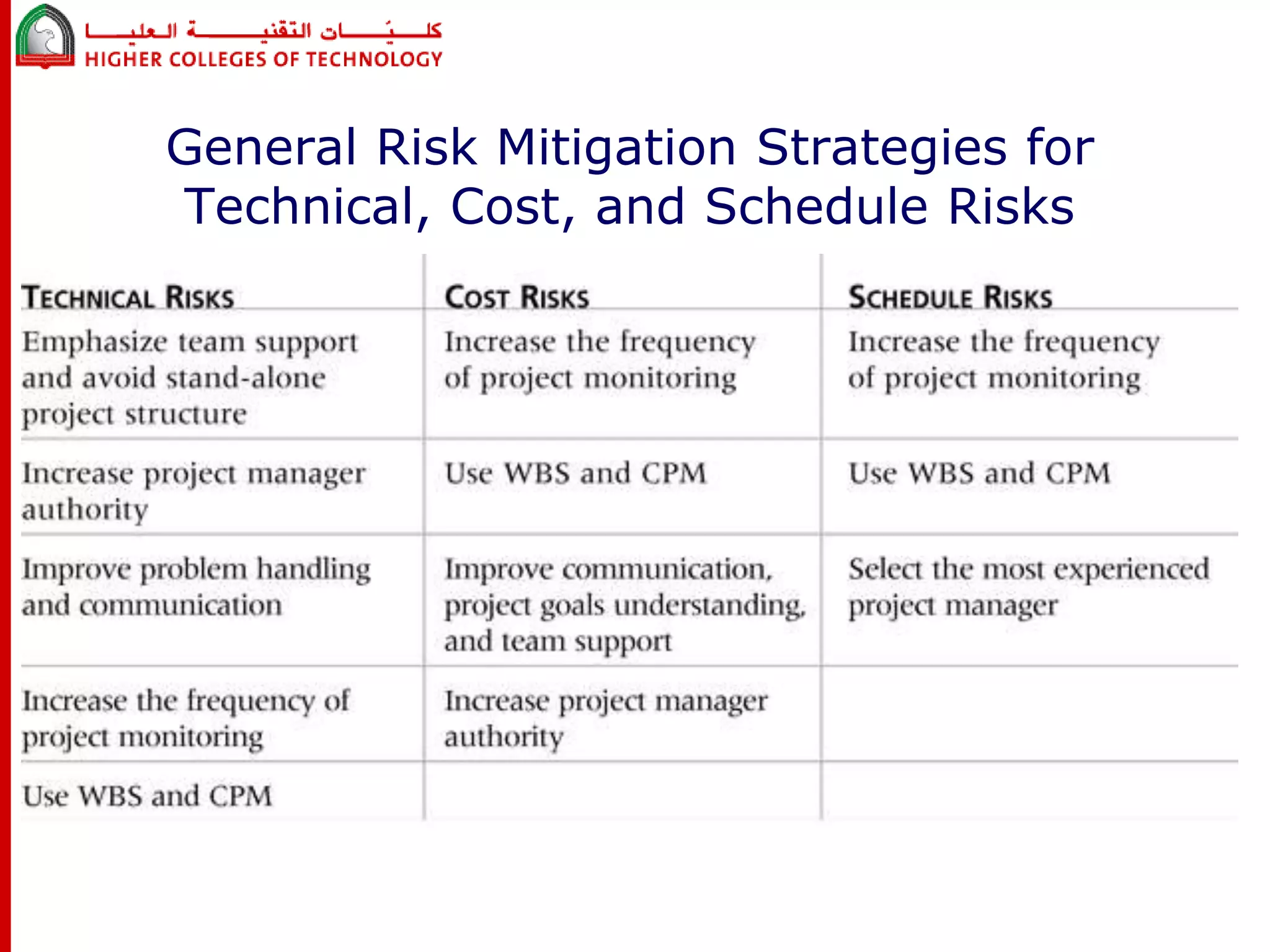
This document discusses project risk management for an IT project management course. It defines risk management and identifies key risk management processes: planning, identification, analysis, response planning, and monitoring/control. Various risk analysis techniques are described like probability/impact matrices and decision trees. The goal of risk management is to minimize negative risks while maximizing positive opportunities through risk avoidance, acceptance, transference, or mitigation strategies.