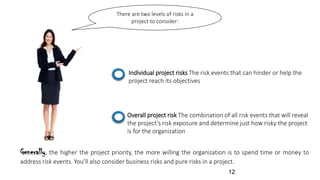
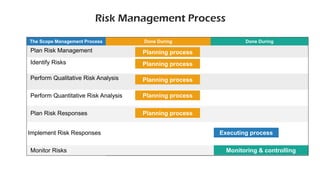
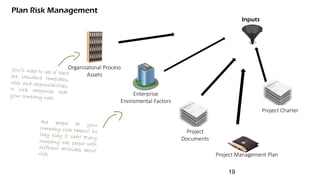
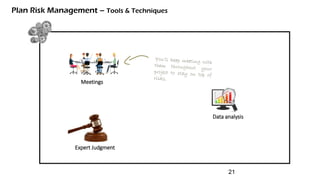
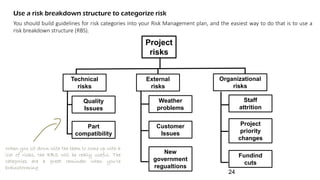
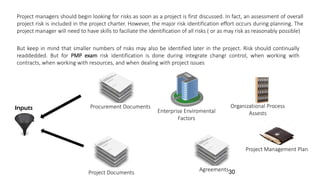
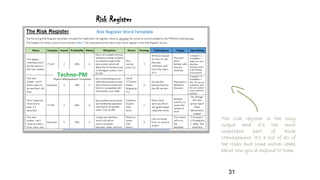
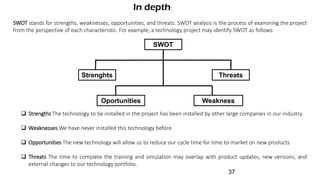
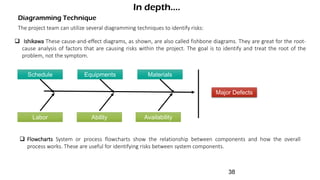
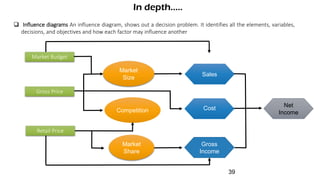
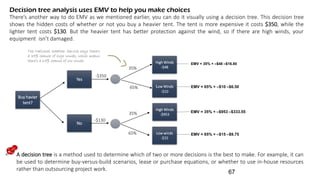
The document discusses risk management for projects. It defines risk as any uncertain event or condition that could positively or negatively impact a project's objectives. It notes that through risk management, a project manager can identify potential problems, take actions to prevent or minimize risks, and stay in control of the project. The document outlines the key steps in risk management as identifying risks, analyzing them, planning responses, implementing responses, and monitoring risks. It also discusses different ways to handle risks, such as avoiding, mitigating, transferring, accepting, or escalating risks.