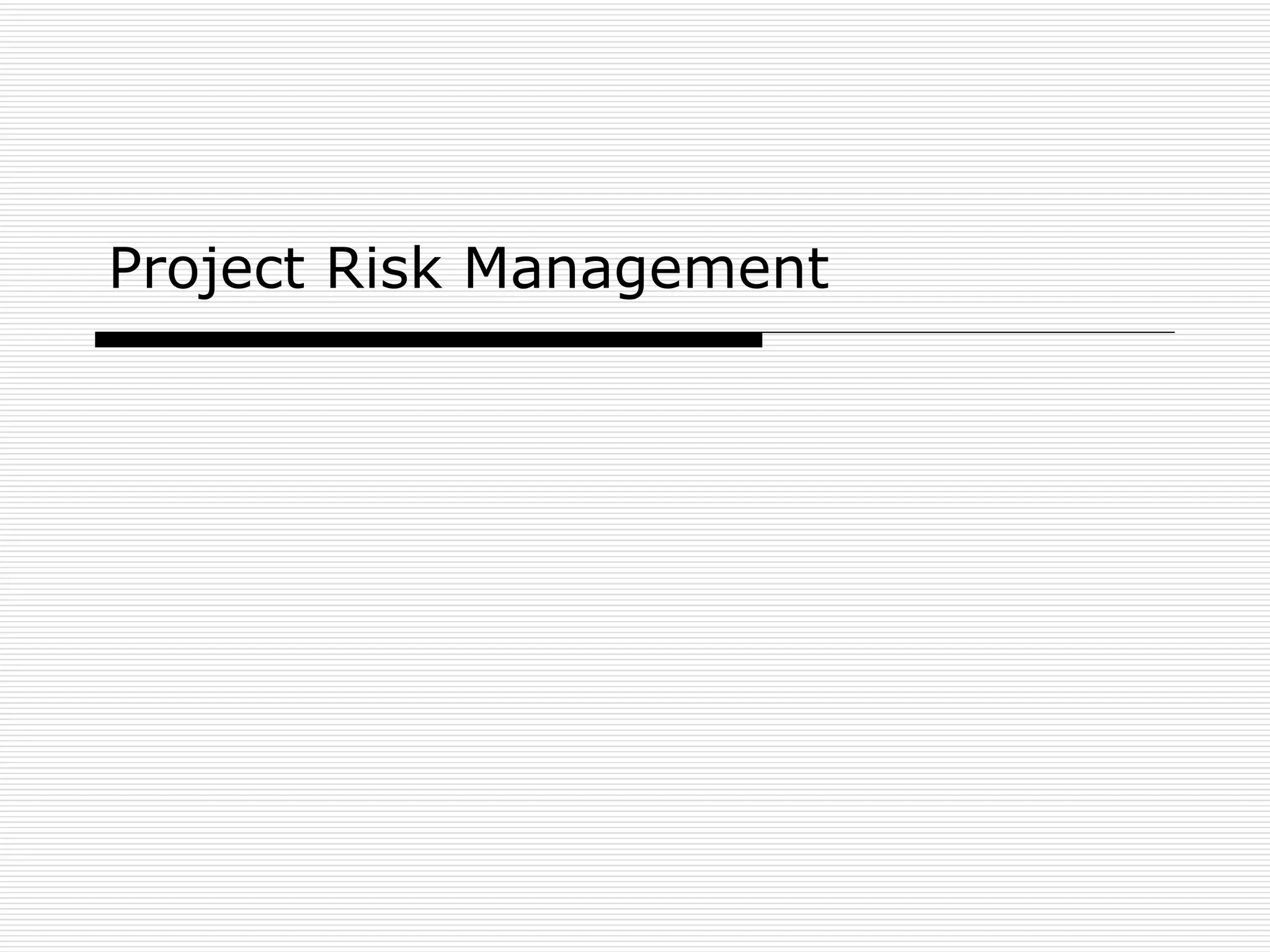
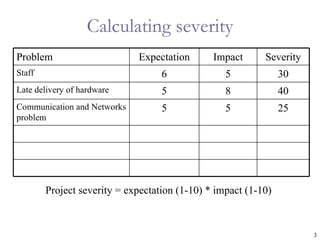
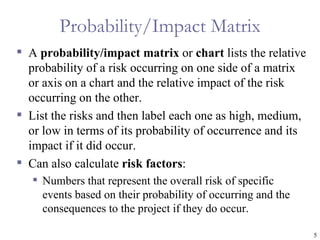
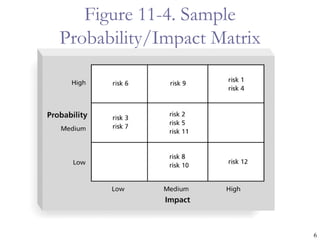
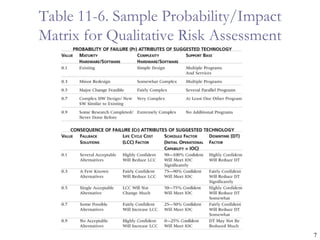
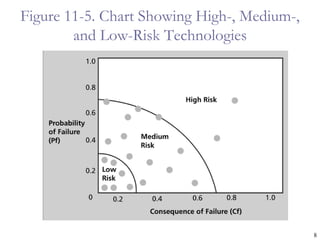
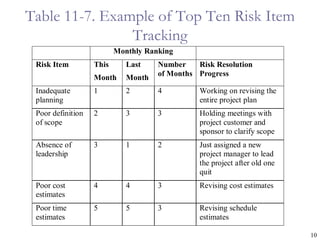
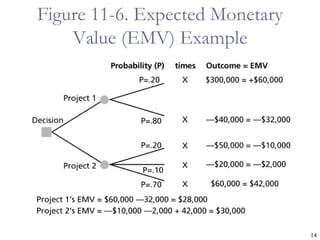
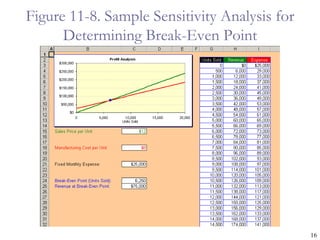
The document provides an overview of project risk management processes and techniques. It discusses qualitative and quantitative risk analysis methods, such as probability/impact matrices and decision trees. Response strategies like risk avoidance, mitigation, and acceptance are also covered. The document aims to equip project managers with tools and best practices for identifying, assessing, and responding to risks throughout the project life cycle.