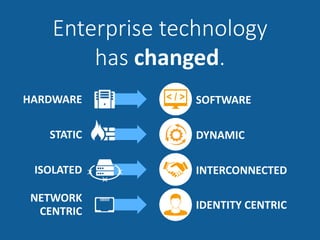
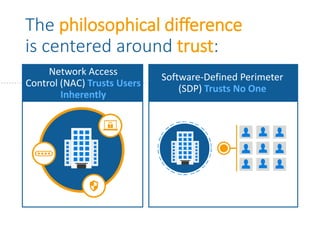
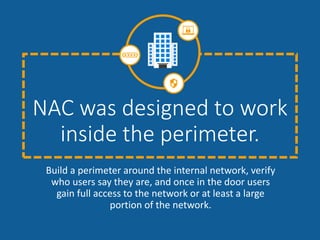
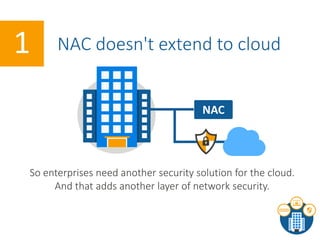
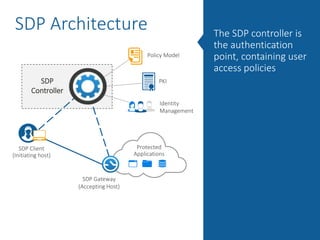
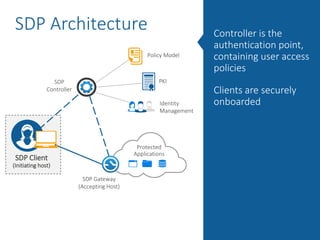
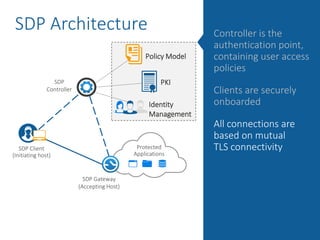
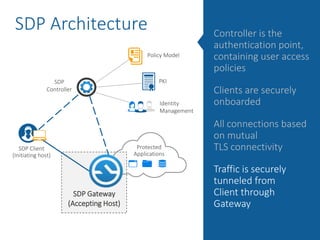
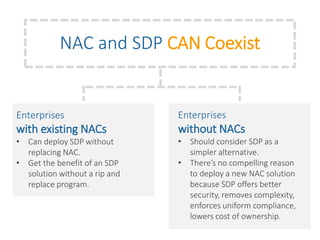
The document summarizes the limitations of Network Access Control (NAC) solutions for securing networks and controlling access in modern IT environments where resources are distributed. It argues that a Software-Defined Perimeter (SDP) model provides better security by establishing encrypted, individual connections between each user and only the specific applications and resources they are authorized to access, rather than relying on trust-based access inside the network perimeter. Key benefits of SDP include zero-trust authentication, dynamic identity-based policies, encryption of all traffic, simplicity, and consistency across cloud and hybrid environments.