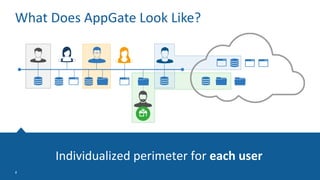
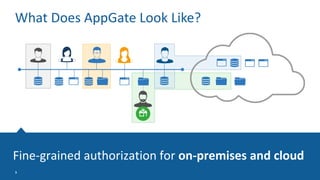
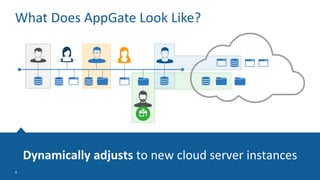
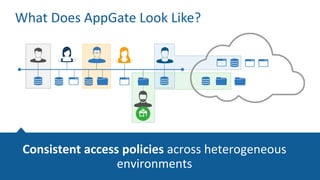
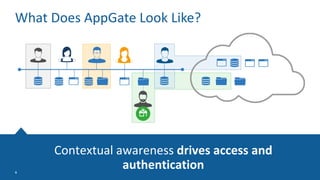
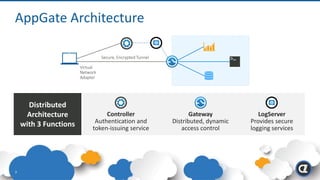
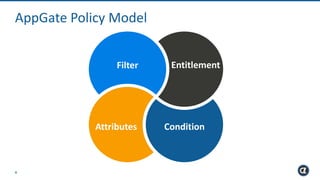
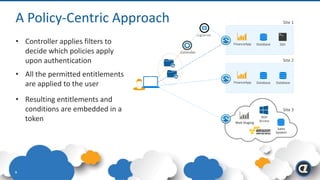
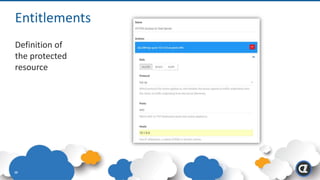
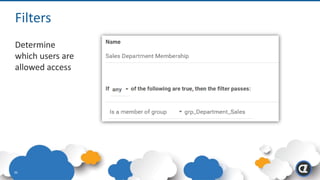
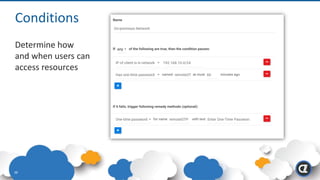
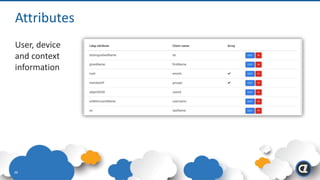
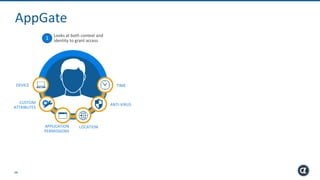
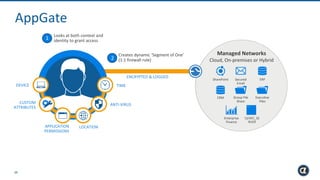
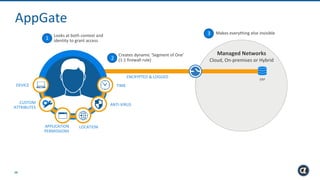
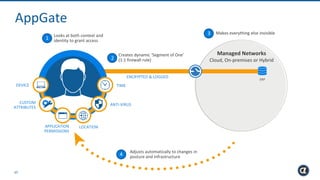
The Appgate technical architecture provides individualized perimeter security for users with fine-grained authorization for both on-premises and cloud resources. It employs a dynamic access control model that adjusts based on user context and identity, creating a secure and encrypted environment while eliminating traditional network defenses. The architecture supports secure logging, customizable access policies, and integrates legacy applications into its security framework.