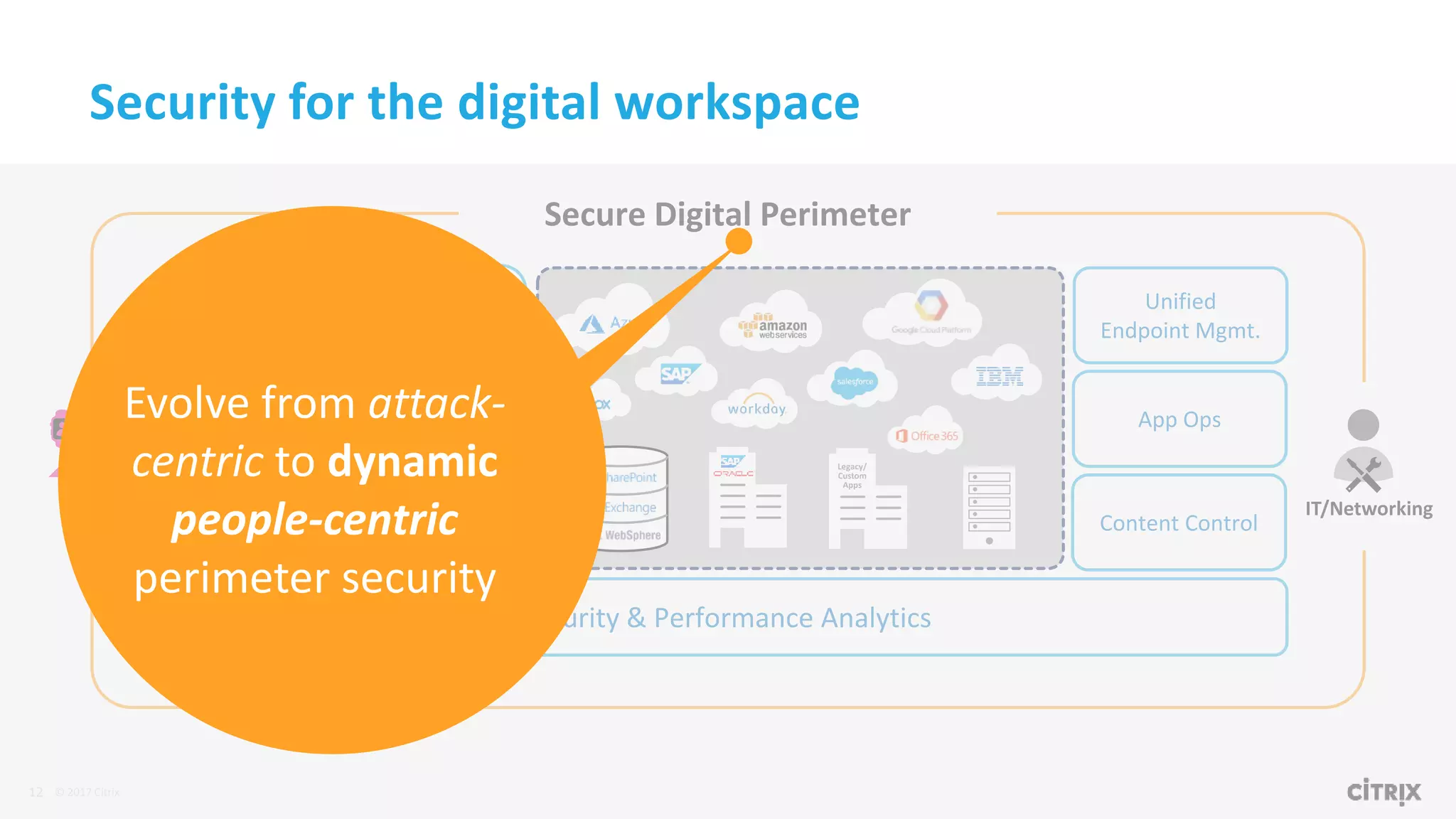
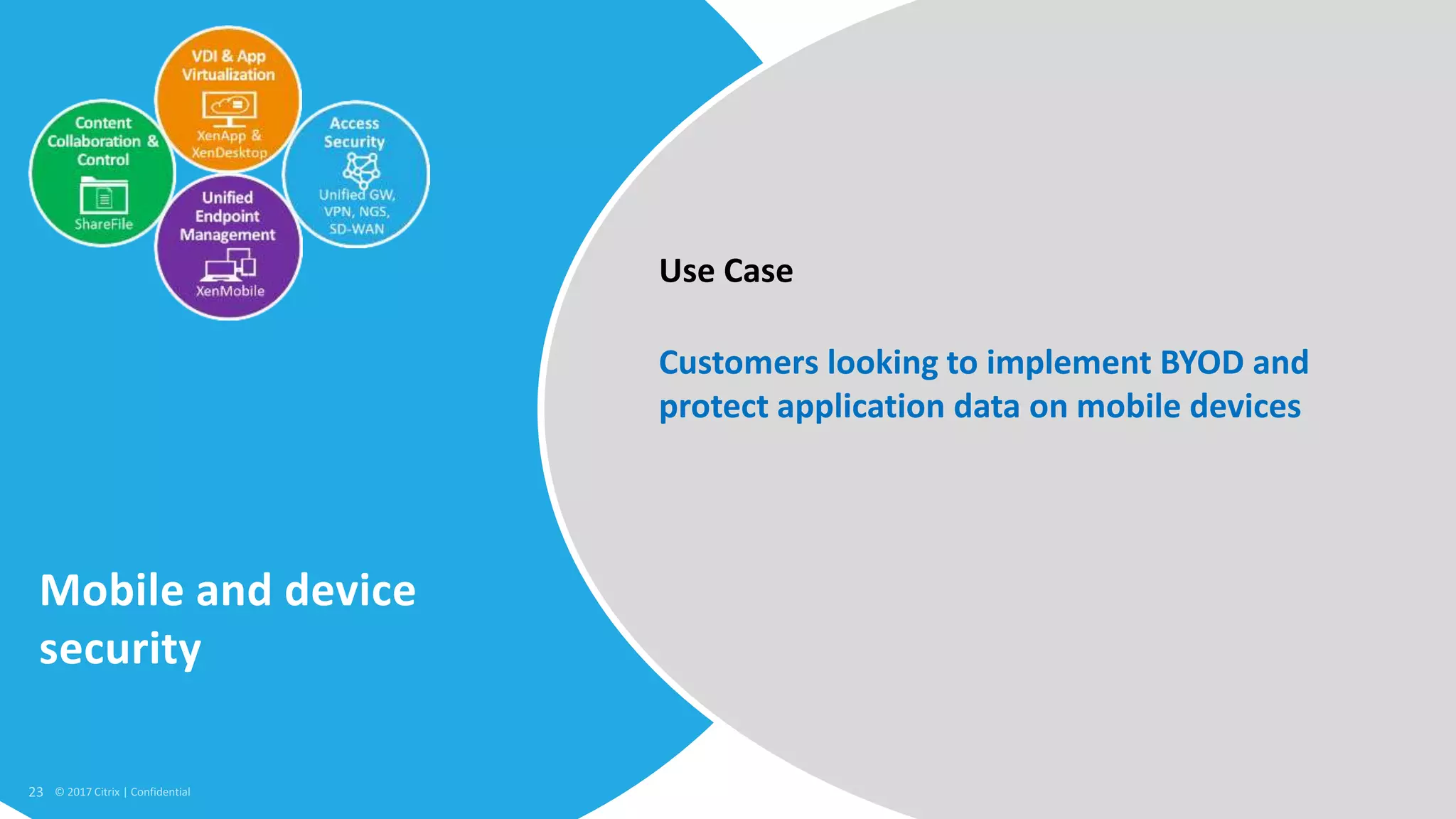
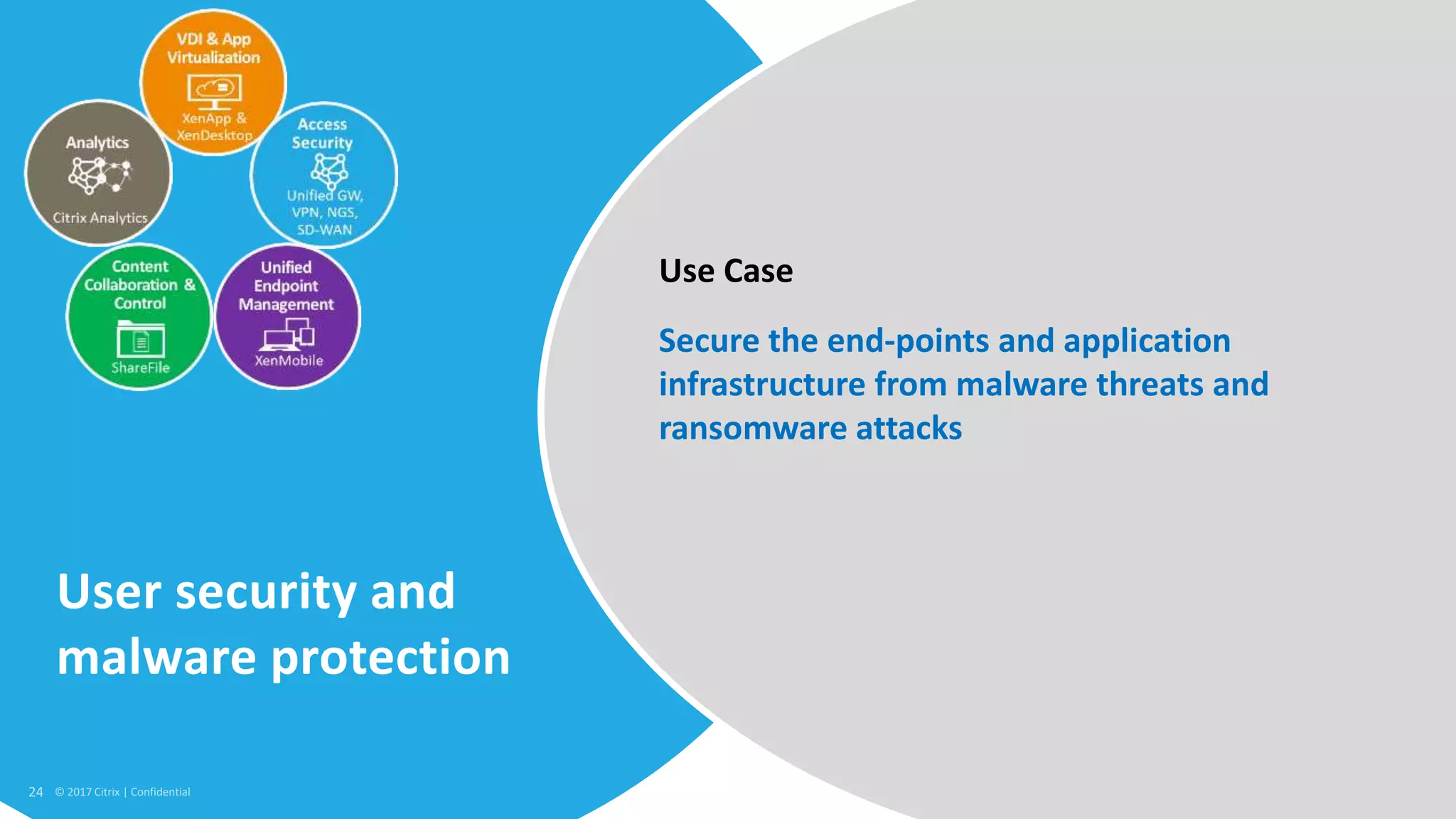
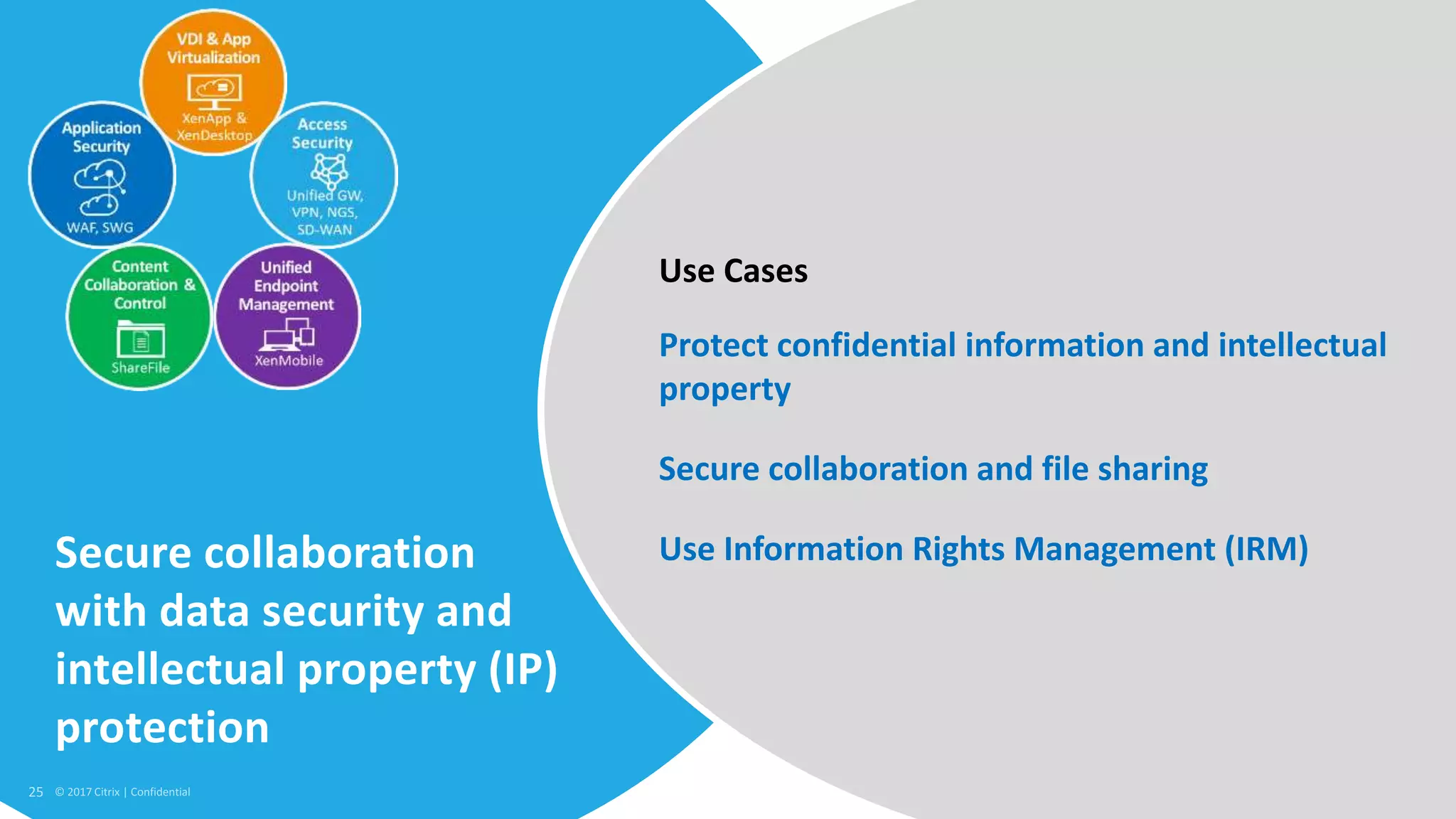
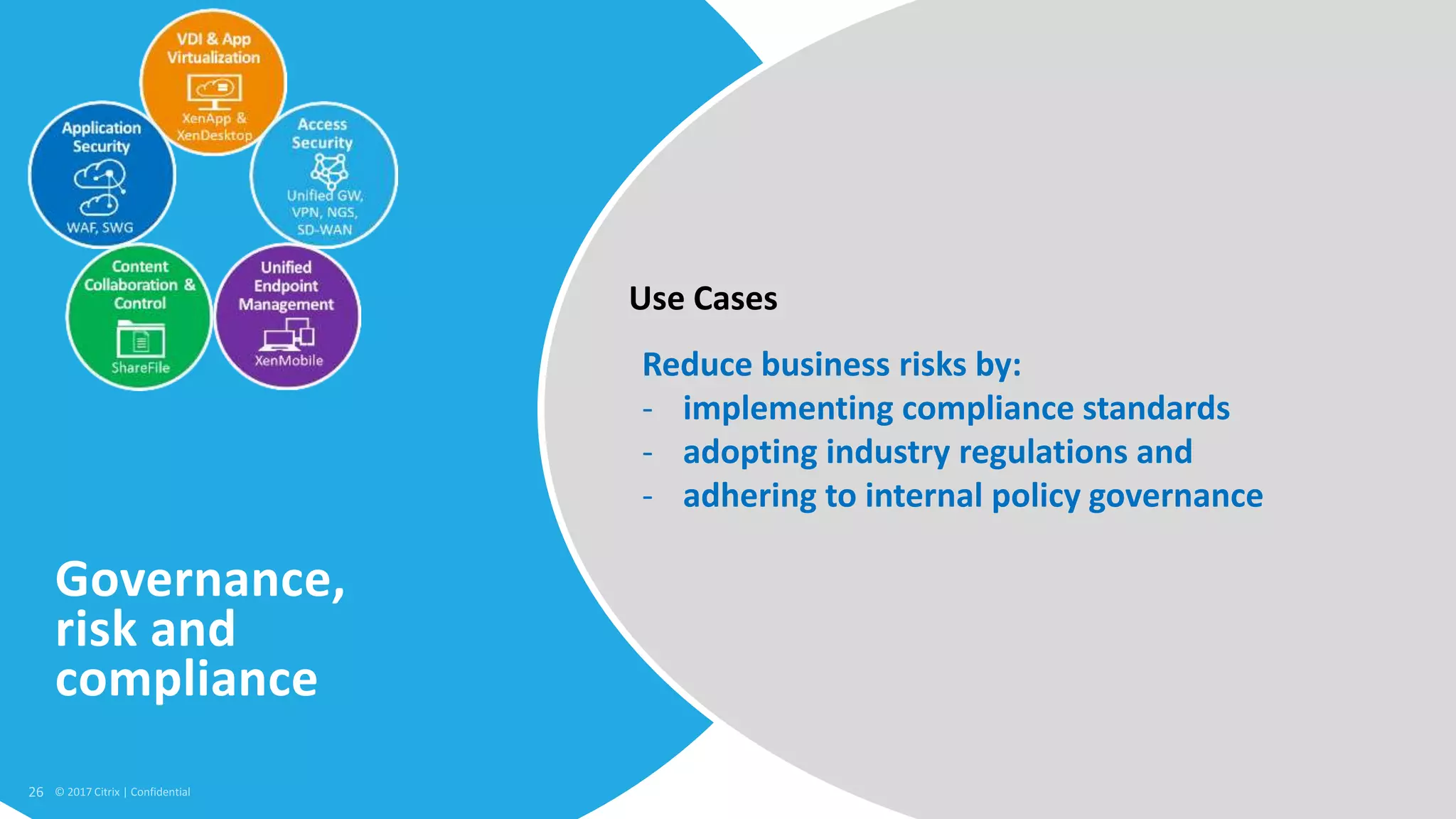
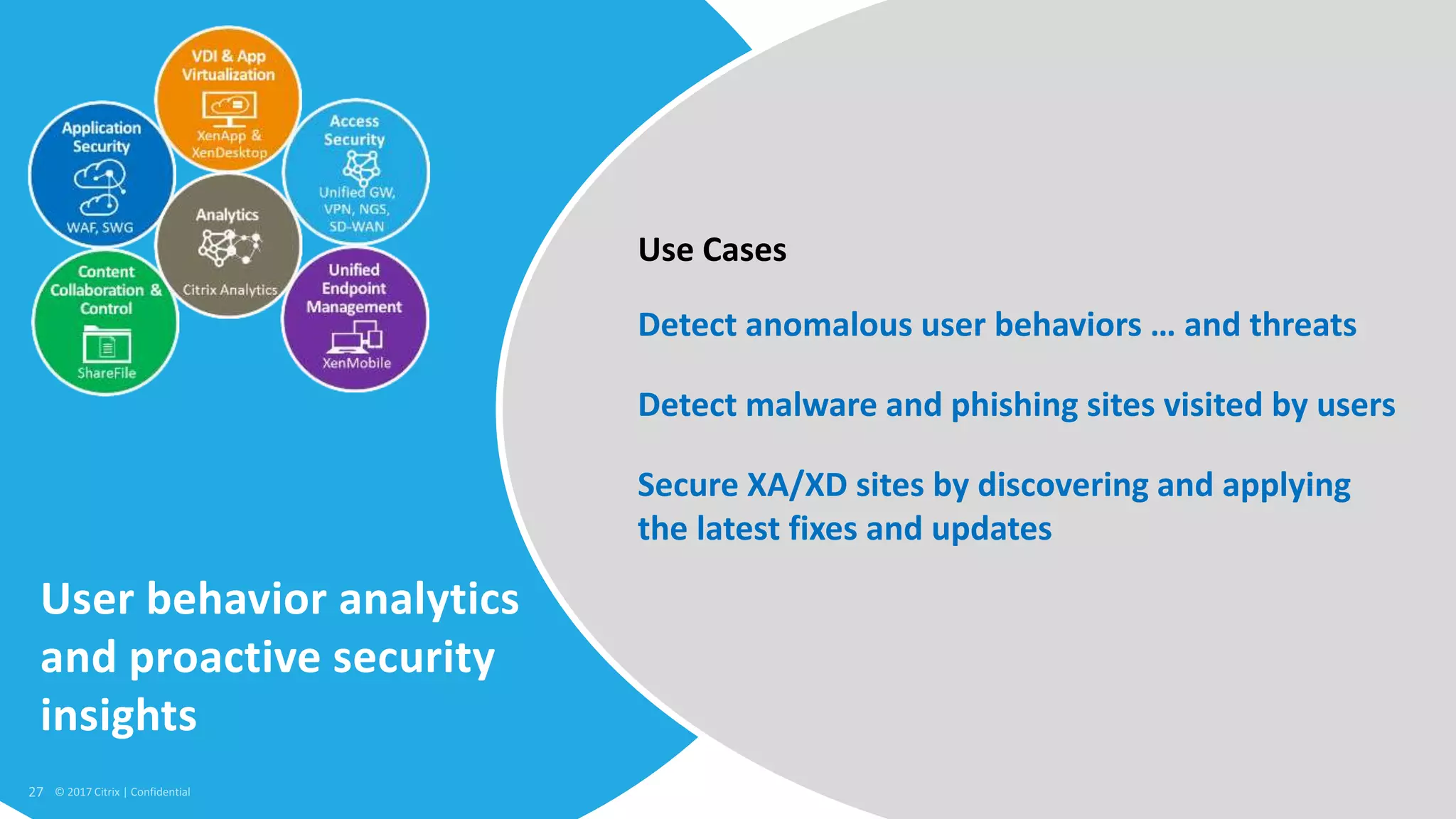
1. Citrix is proposing a new approach called the Secure Digital Perimeter (SDP) to address security challenges in a world where work is distributed across SaaS apps, cloud services, and remote users.
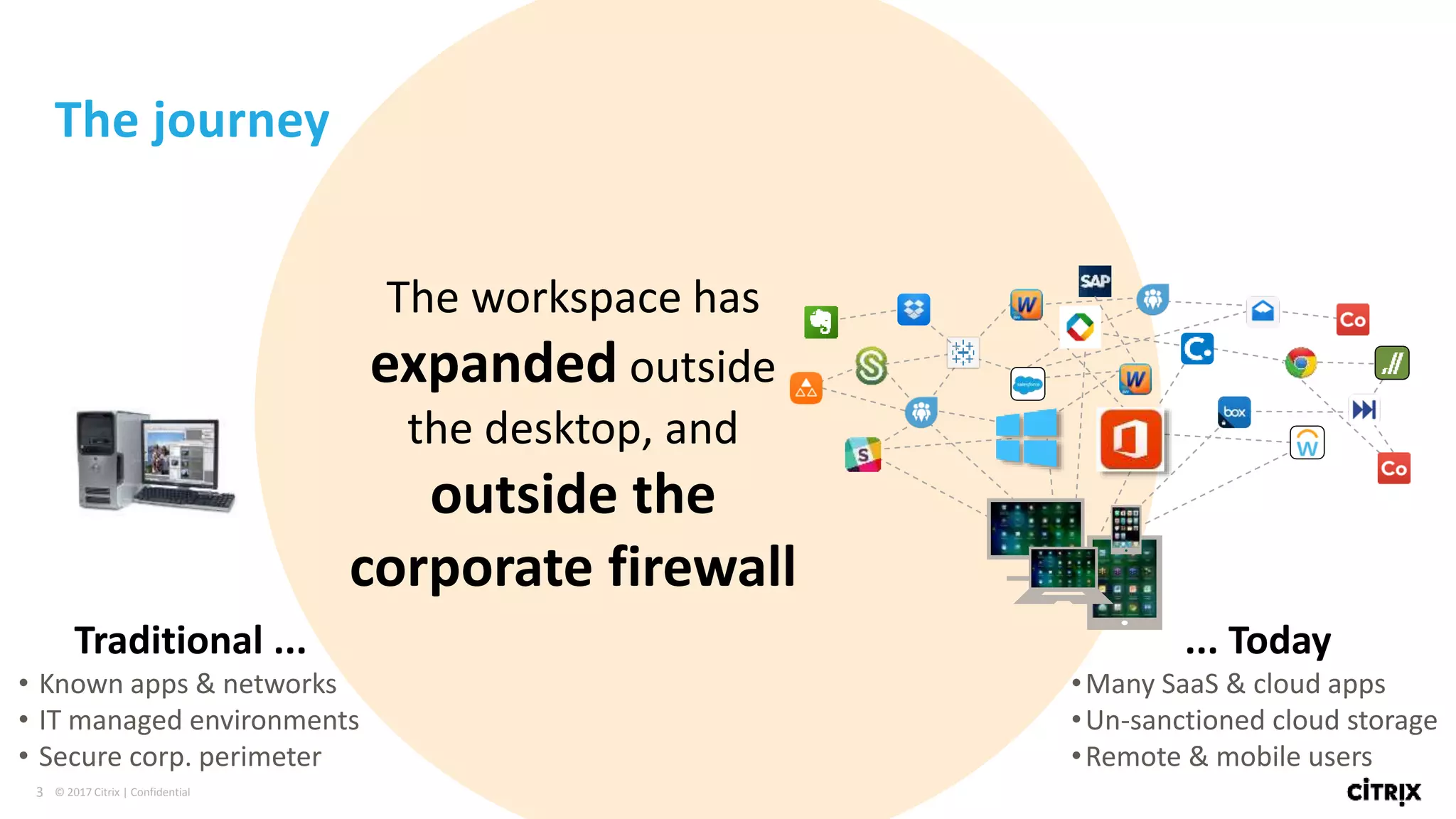
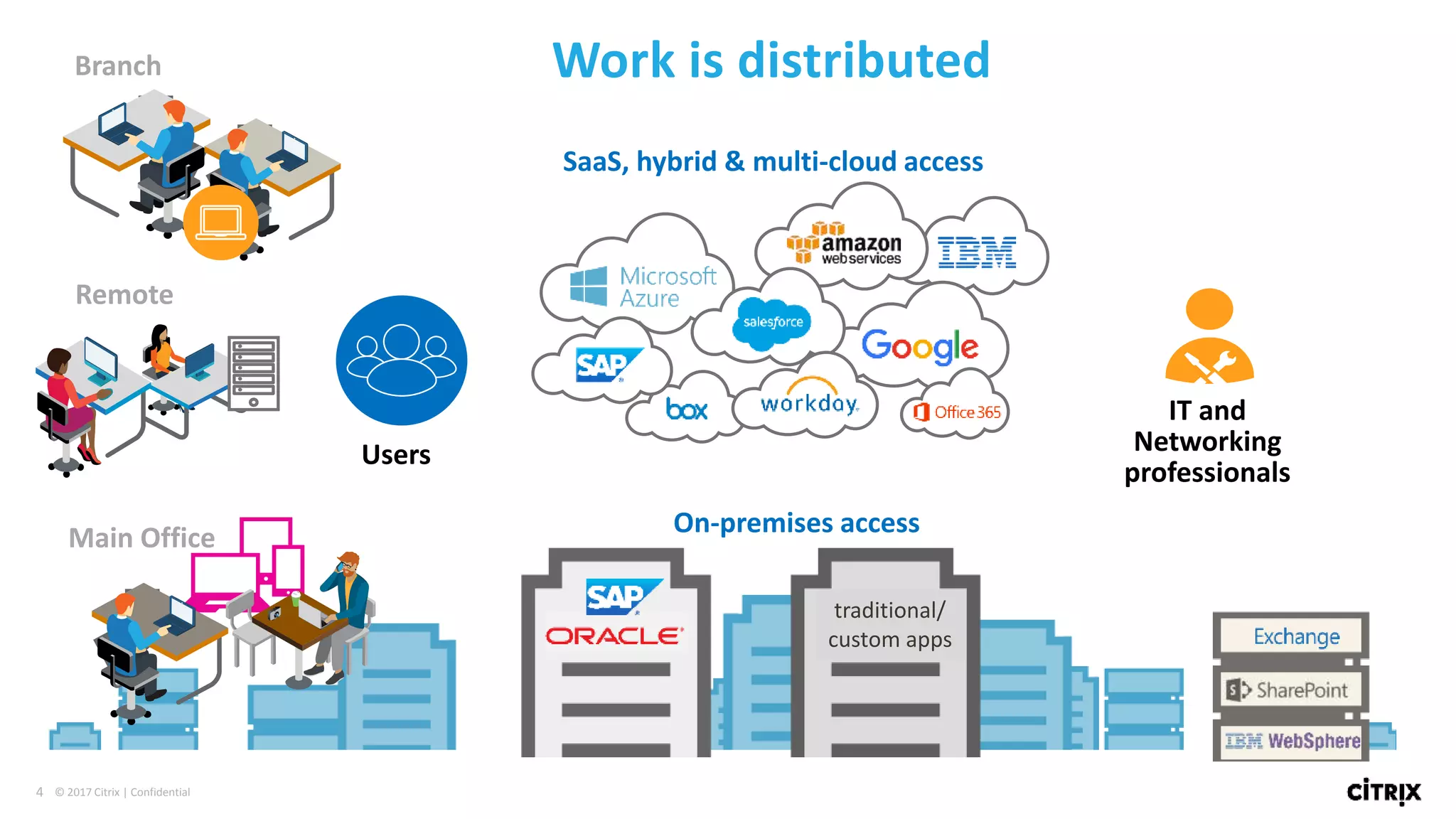
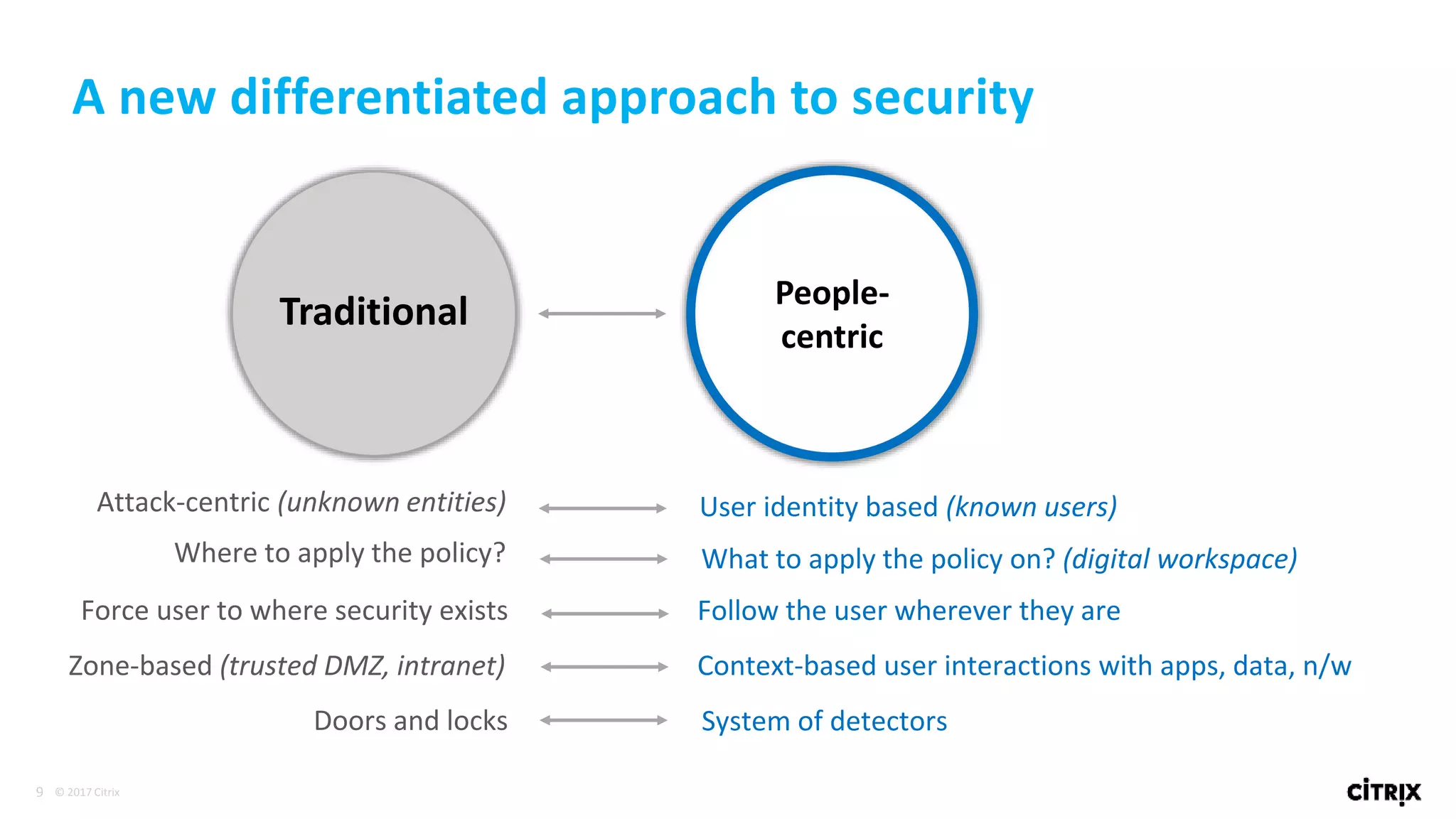
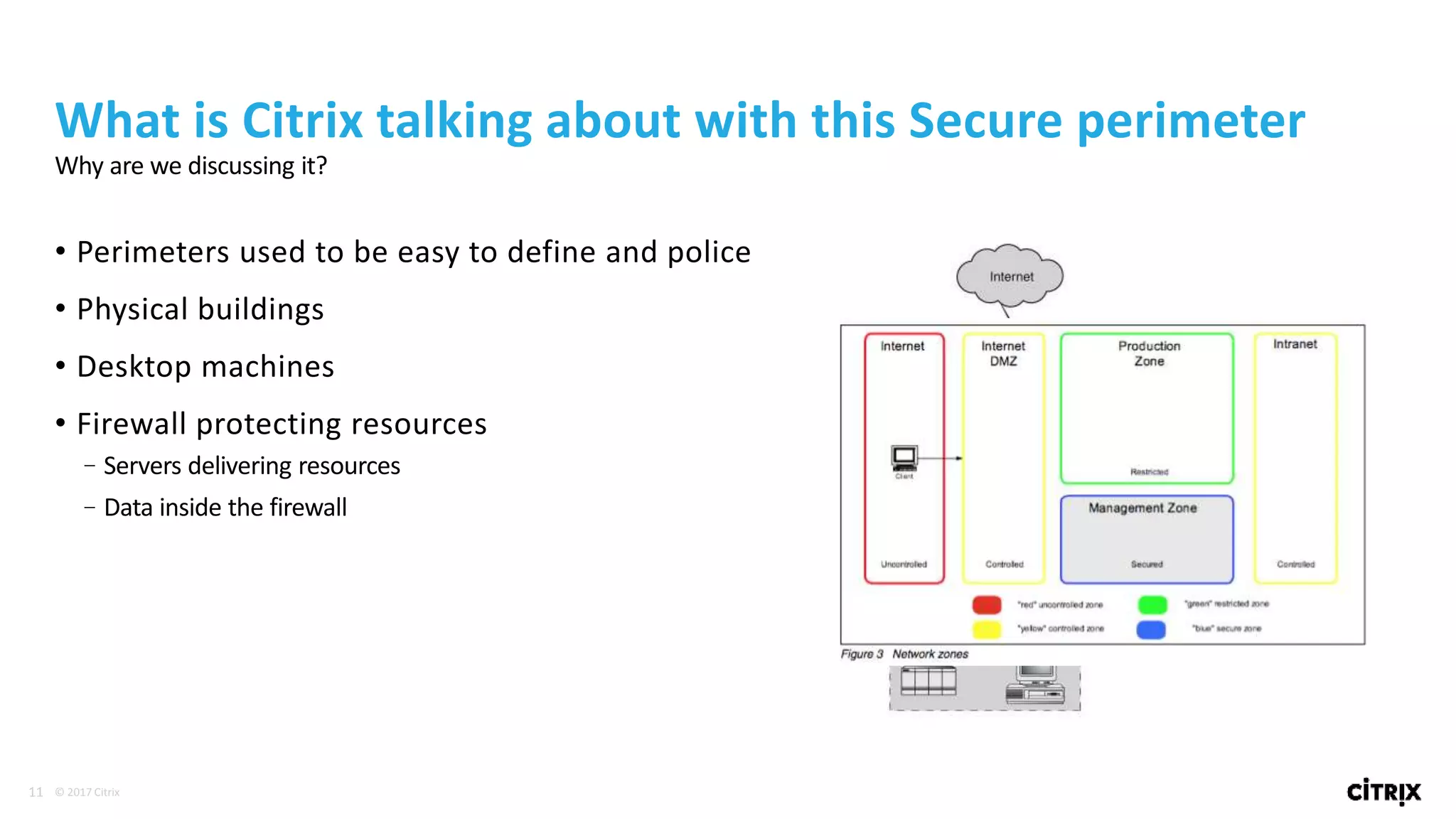
2. Traditional security approaches focused on protecting networks and resources within organizational perimeters but SDP takes a people-centric approach that follows users across devices and locations.
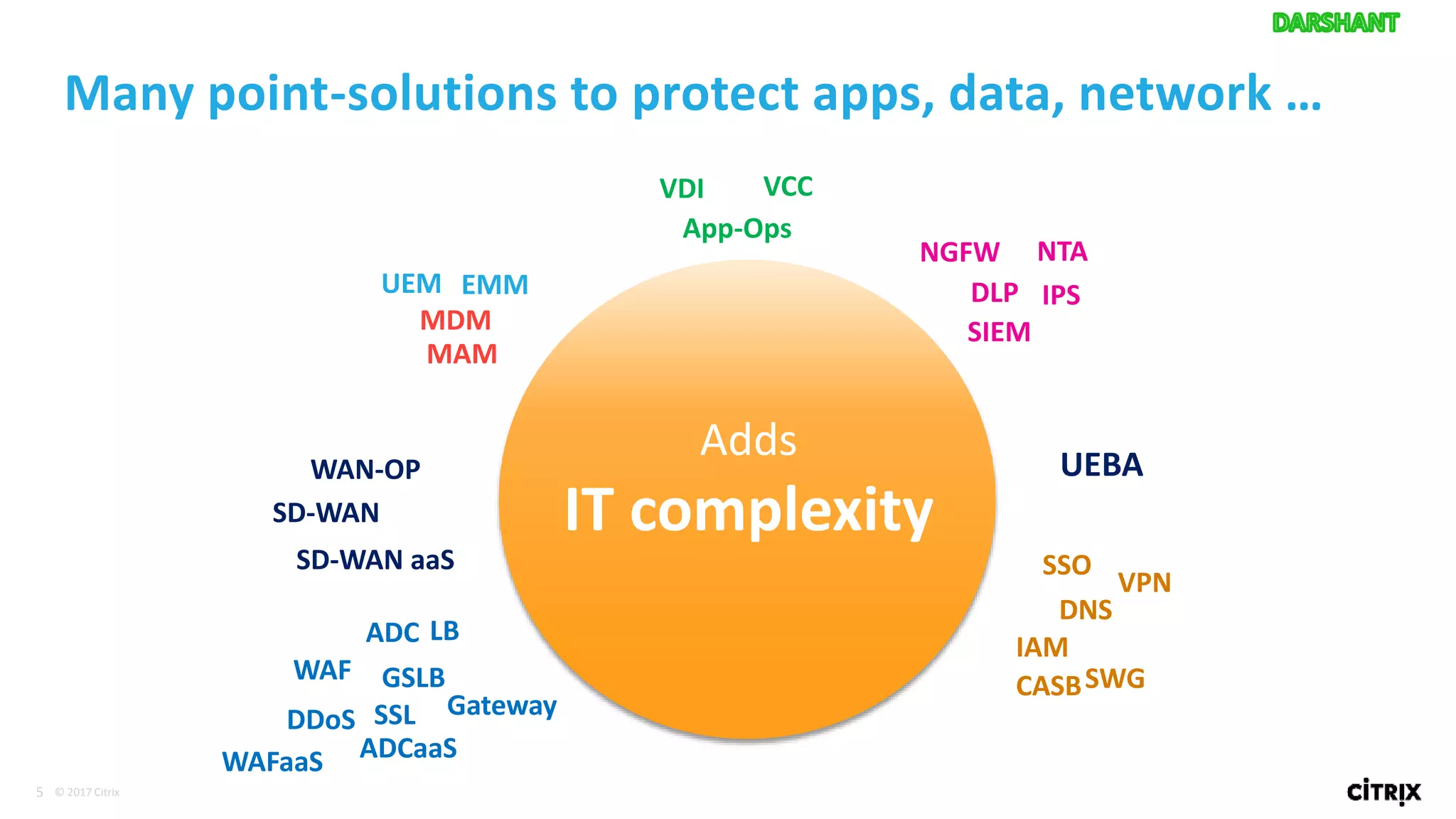
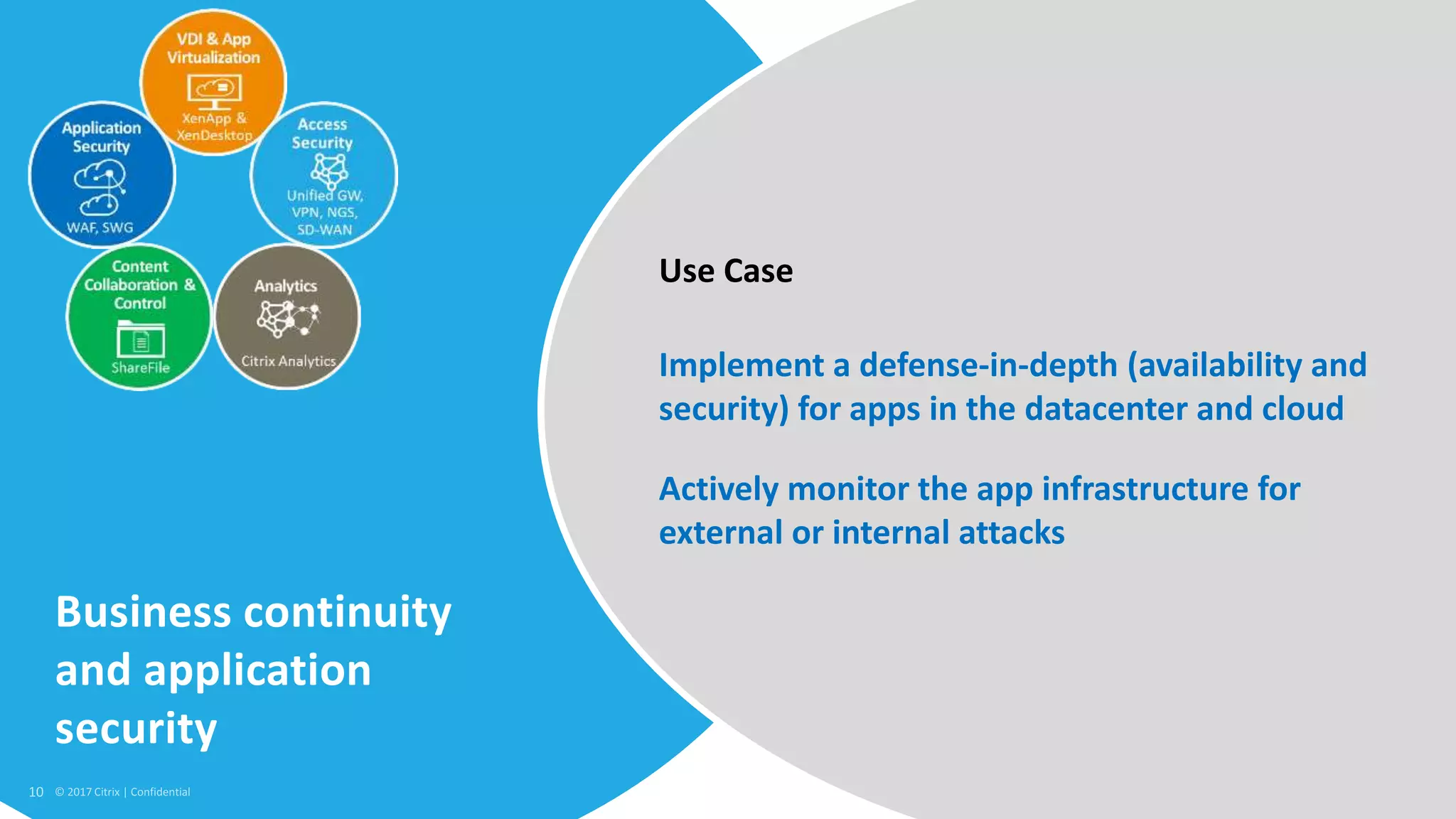
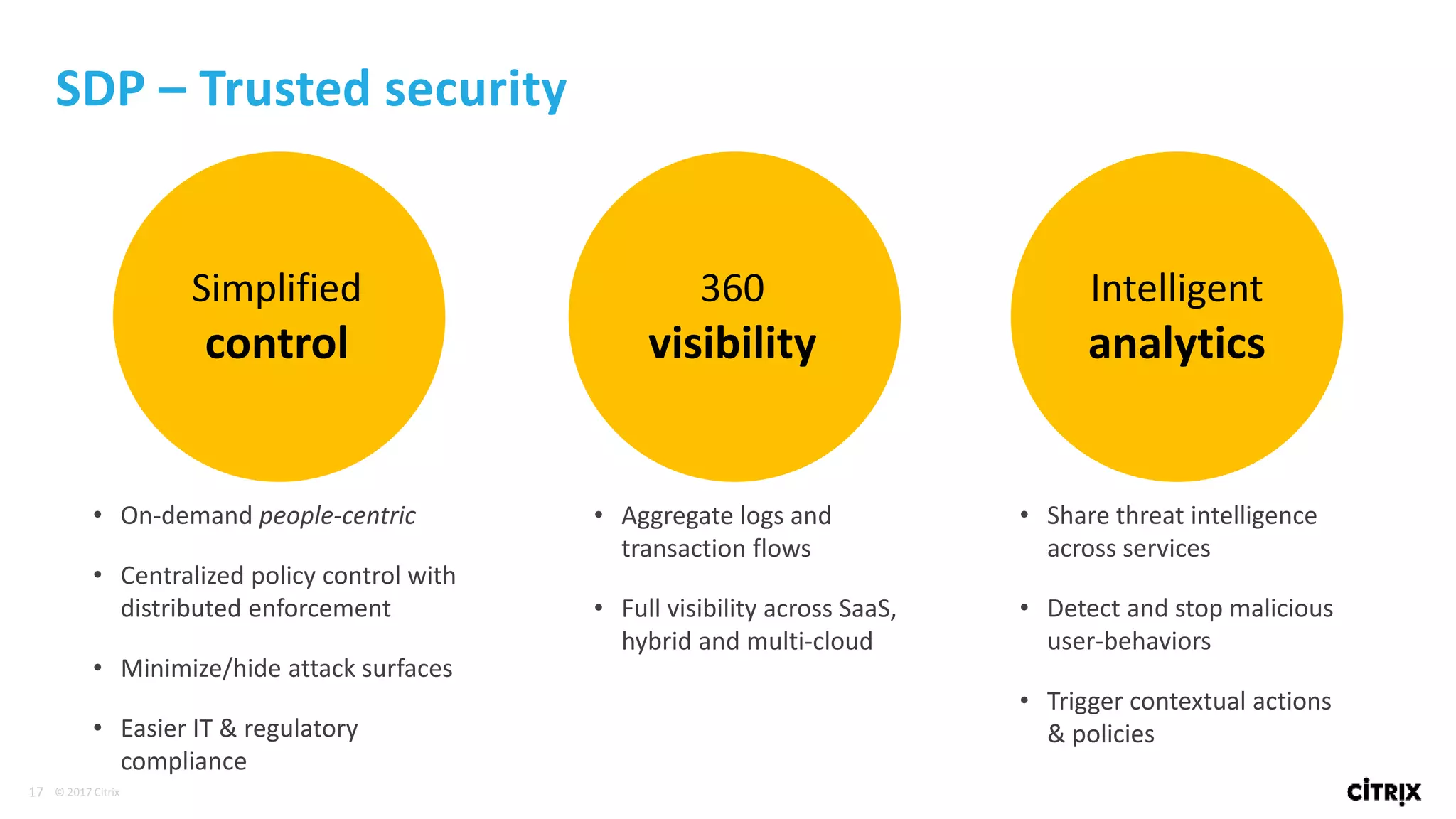
3. SDP provides simplified control, 360-degree visibility, and intelligent analytics across networking and security services to minimize attack surfaces and gain compliance while allowing access from any device.