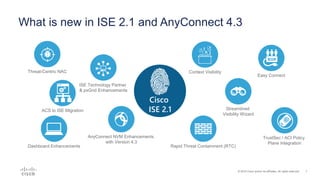
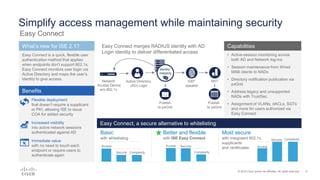
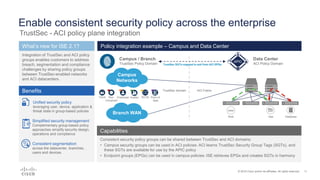
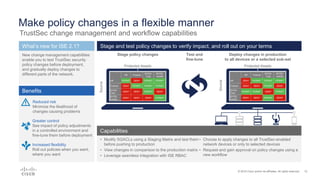
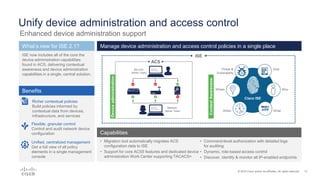
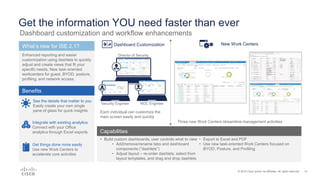
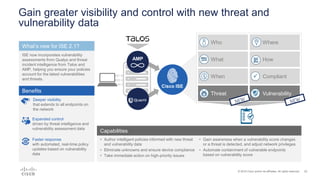
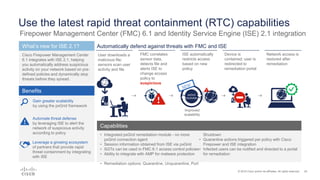
Cisco ISE 2.1 enhances network visibility and security management by integrating new features such as easy connect for user authentication, improved threat-centric NAC, and unified security policies through TrustSec and ACI integration. The update also includes capabilities for flexible policy management, device administration unification, and enhanced reporting through customizable dashboards, enabling organizations to better respond to threats and maintain compliance. Overall, ISE 2.1 supports greater control over network access and improved analytics for threat detection and vulnerability management.