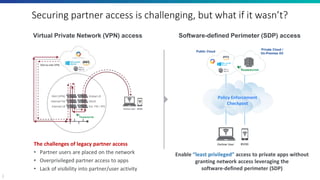
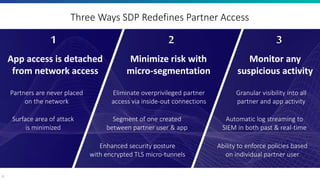
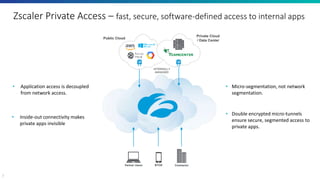
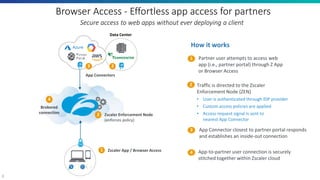
The document discusses the challenges of traditional partner access through VPNs and presents the Software-Defined Perimeter (SDP) as a more secure alternative. SDP enables least privileged access to private applications without granting network access, enhancing security by employing micro-segmentation and advanced visibility. Zscaler Private Access (ZPA) is highlighted as a solution for achieving secure, effortless, and managed access to internal applications for partner users.