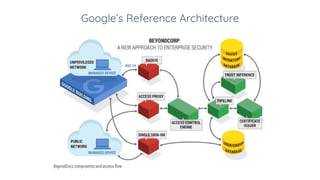
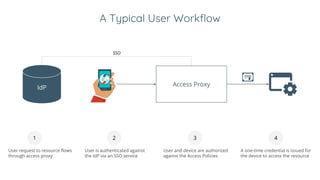
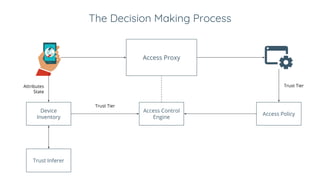
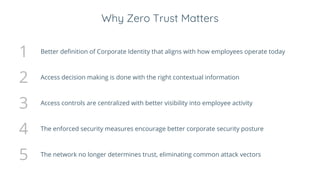
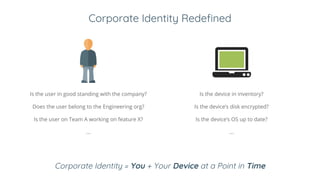
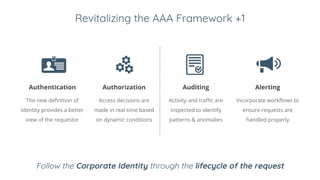
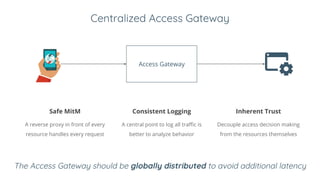
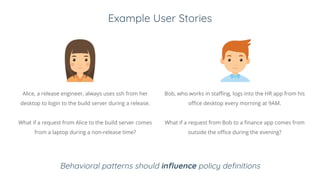
BeyondCorp is Google's security initiative developed in response to the 2009 Operation Aurora cyberattack, which recognized traditional perimeter security methods like VPNs were insufficient. The initiative promotes a zero trust architecture that allows employees to access company resources from untrusted networks while continuously validating their identity and device security. By eliminating reliance on network segmentation, BeyondCorp enhances visibility into employee activity and improves overall corporate security posture.