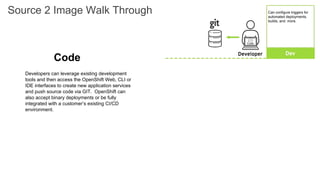
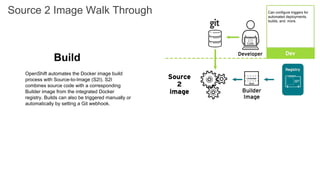
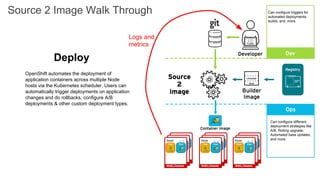
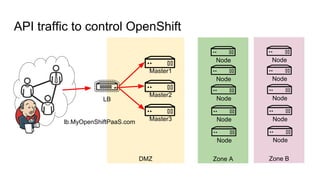
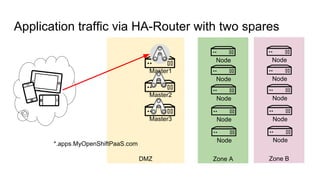
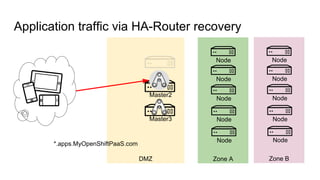
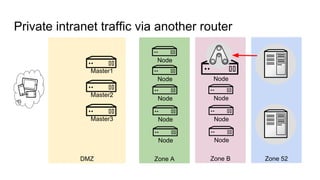
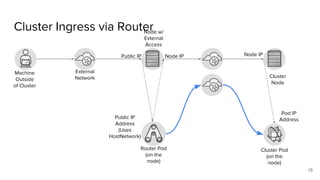
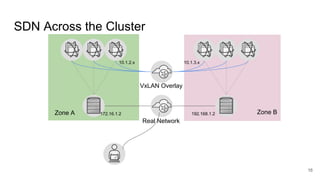
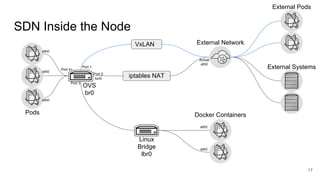
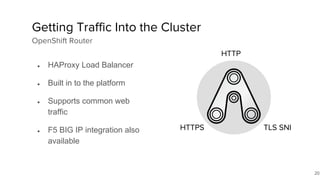
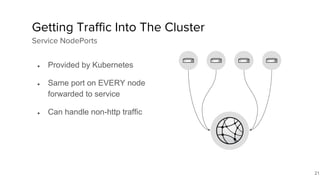
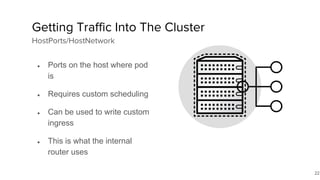
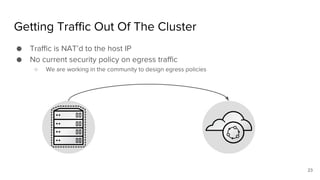
The document discusses the benefits and automation capabilities of OpenShift's networking through software-defined networking (SDN). It highlights OpenShift's ability to automate deployment processes, manage container networking, and integrate with CI/CD environments, while also providing strategies for scaling and service discoverability. Future directions include the adoption of the Container Network Interface (CNI) for plugins and potential integrations with OpenStack for enhanced functionalities.