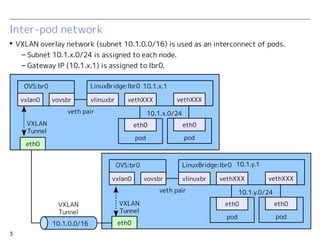
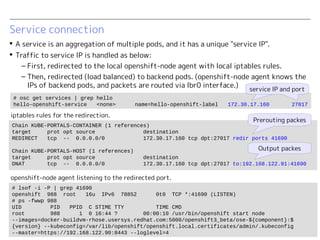
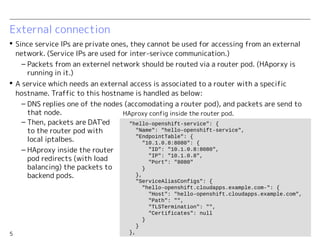
OpenShift v3 uses an overlay VXLAN network to connect pods within a project. Traffic between pods on a node uses Linux bridges, while inter-node communication uses the VXLAN overlay network. Services are exposed using a service IP and iptables rules to redirect traffic to backend pods. For external access, services are associated with router pods using a DNS name, and traffic is load balanced to backend pods by HAProxy in the router pod.