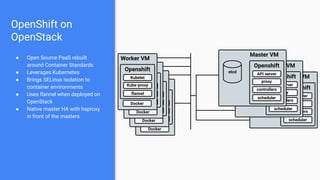
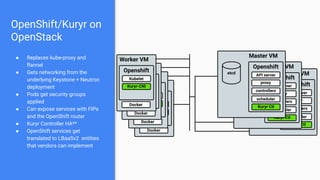
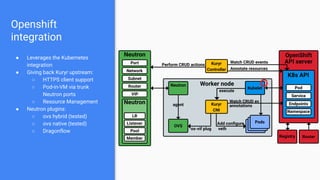
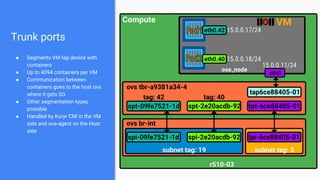
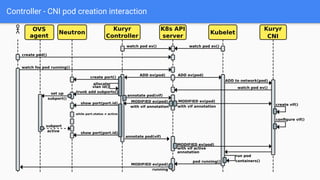
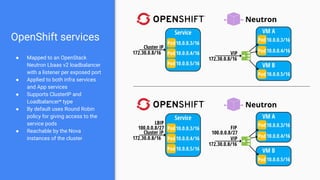
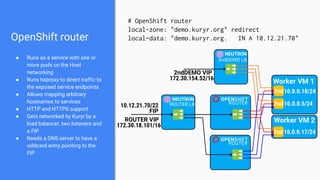
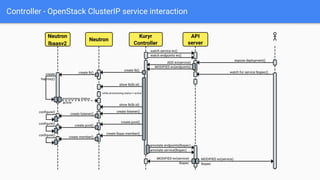
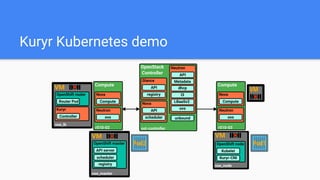
The document outlines the integration of OpenShift with Kuryr to manage hybrid workloads on OpenStack, emphasizing connectivity between pods and virtual machines through various networking configurations. It details the Kuryr controller's high availability, load balancing features, and service interaction including ClusterIP and load balancer types. Additionally, it highlights future enhancements, including resource management and support for multi-homed pod networks.