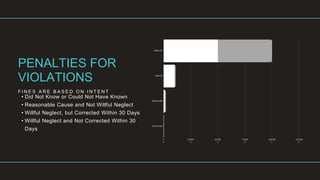
The document serves as a beginner's guide to HIPAA compliance, covering its history, intent, and key provisions concerning the privacy, security, and breach notification rules of health information. It explains who must comply with HIPAA, defines critical terms, and details the roles of covered entities and business associates. Additionally, it outlines the enforcement mechanisms and penalties for violations while highlighting the importance of patient privacy and security in health care.