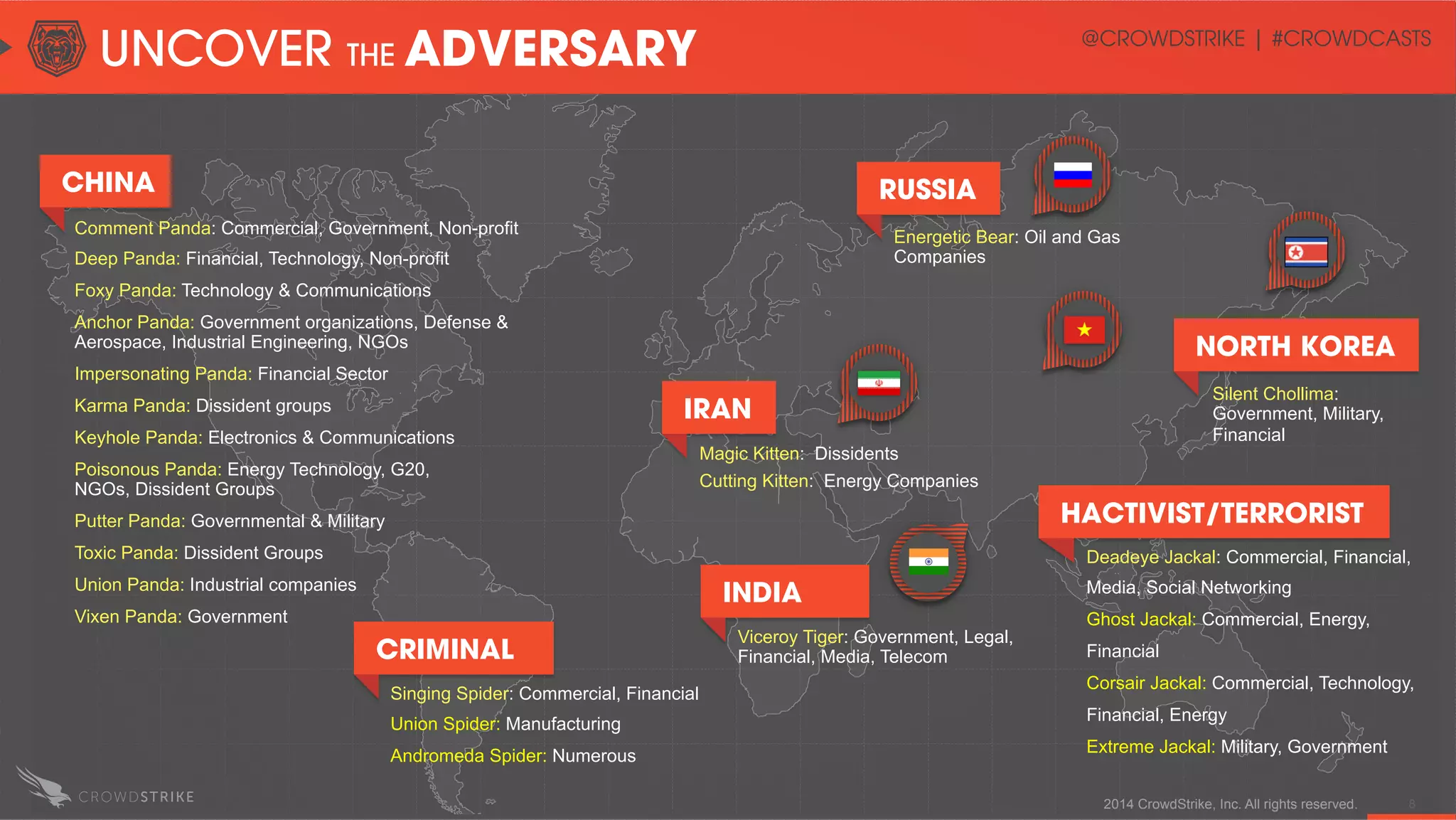
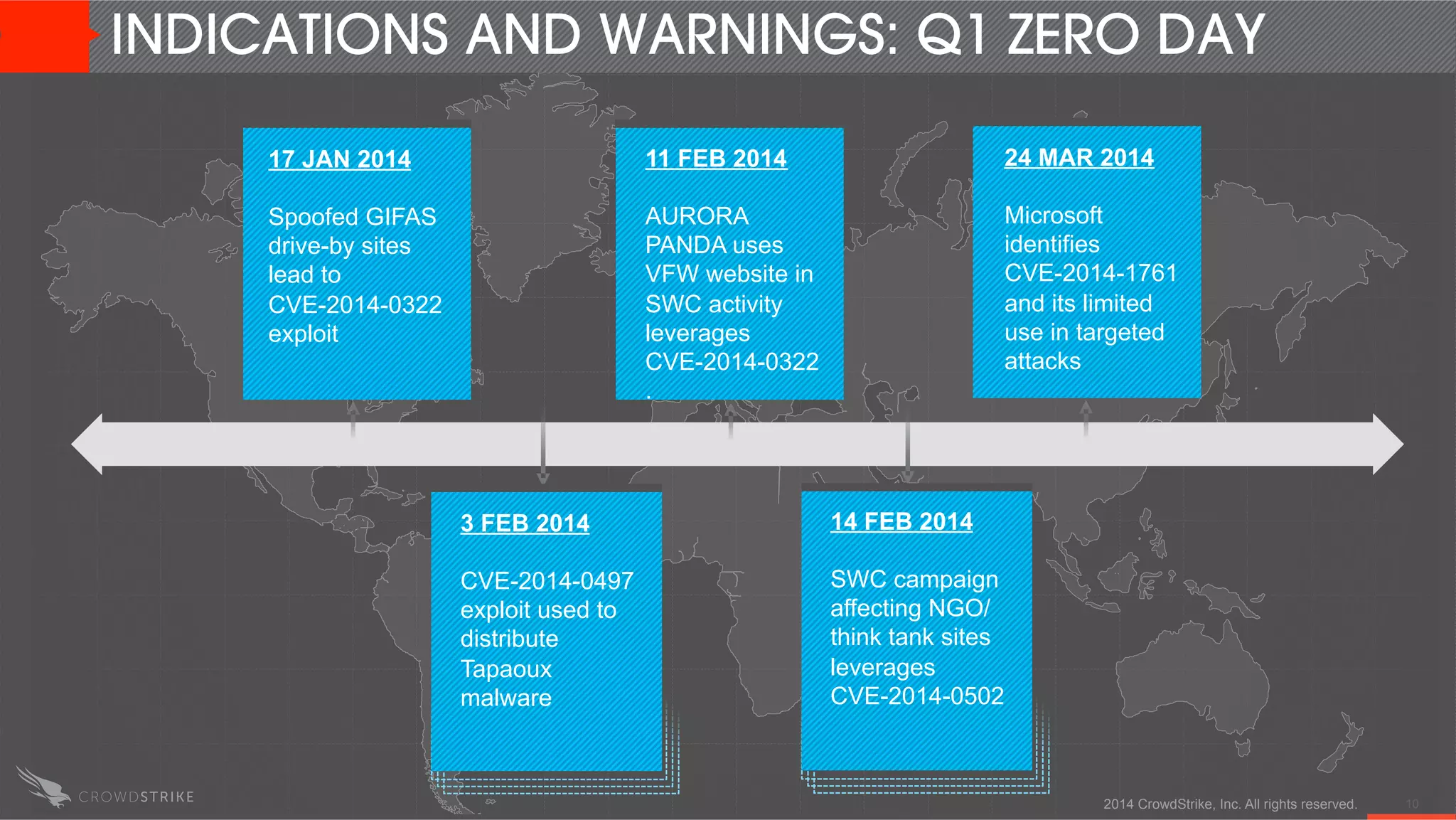
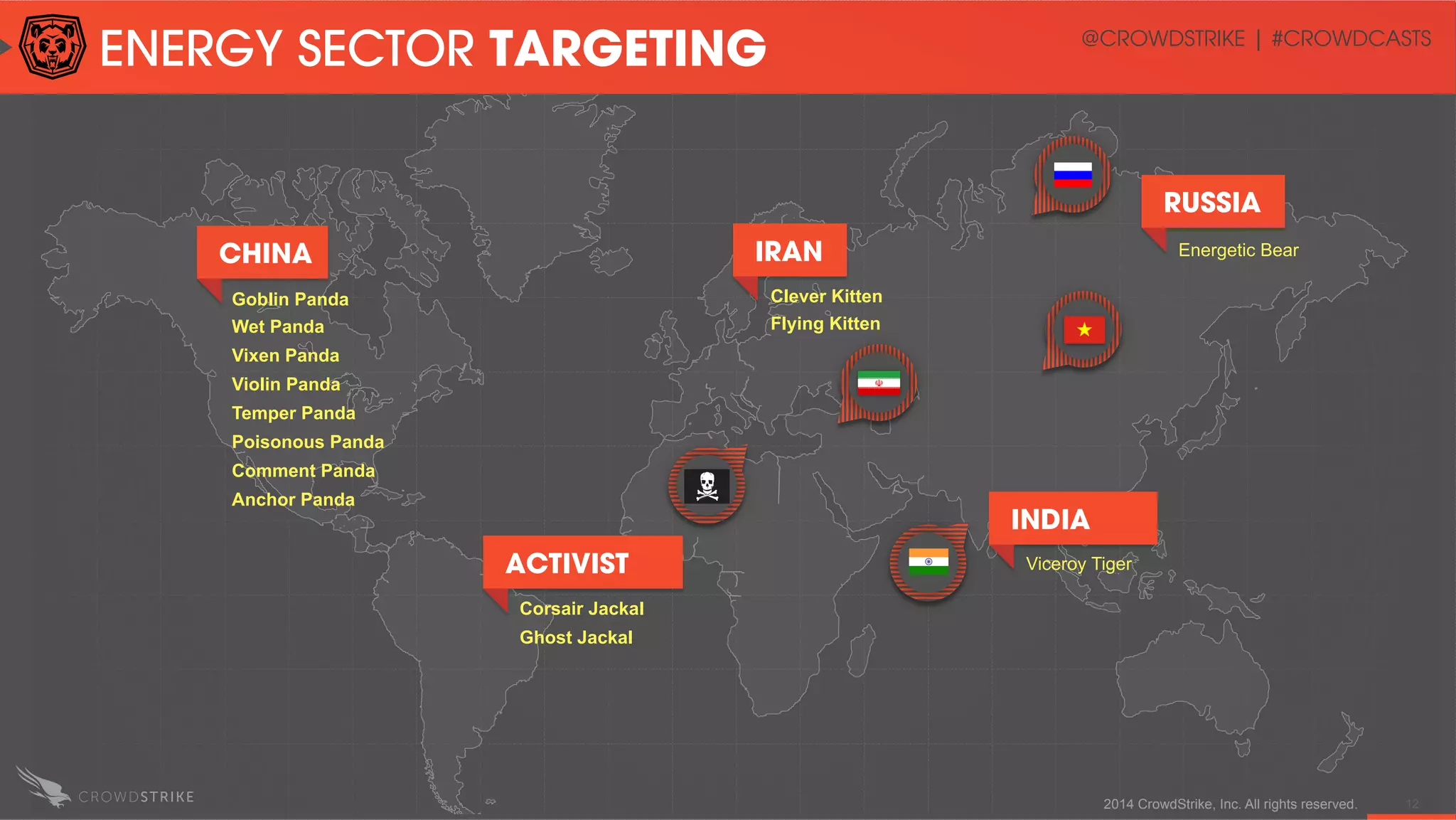
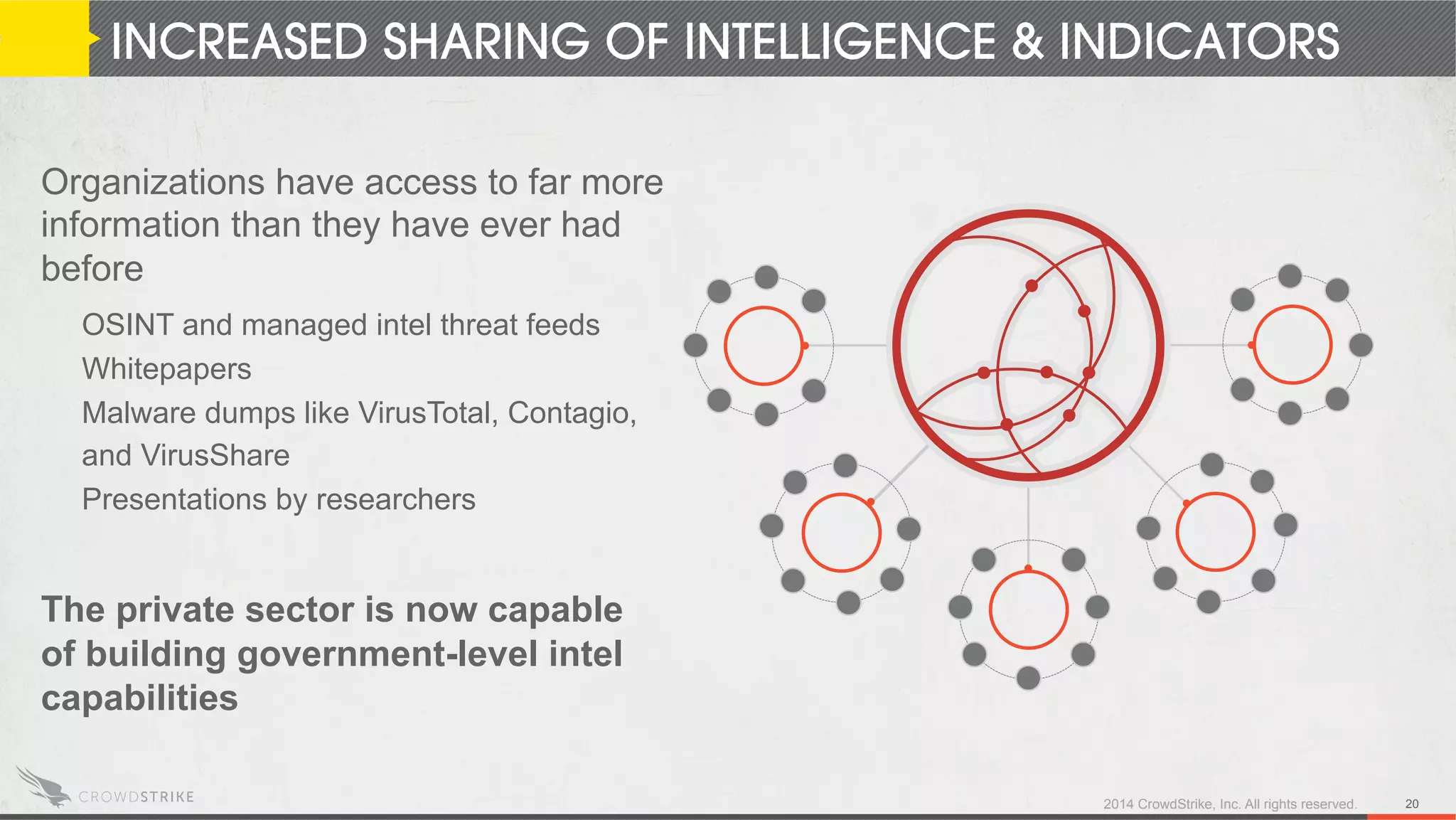
The document discusses the operationalization of threat intelligence in security operations, highlighting the experience of speakers Adam Meyers and Elia Zaitsev from CrowdStrike. It covers various strategies for utilizing actionable intelligence against potential cyber threats, particularly within the context of China's targeting of the oil sector. The text emphasizes the importance of timely and effective threat intelligence to prevent cyber incidents and mitigate the risks associated with emerging patterns of attacks.








![2014 CrowdStrike, Inc. All rights reserved. 22
@CROWDSTRIKE | #CROWDCASTS
DEMOS [ ]DATA VISUALIZATION
PACKET CAPTURE
LOG AGGREGRATION / SIEM
THREAT INTELLIGENCE](https://image.slidesharecdn.com/crowdcastmonthlyoperationalizingintelligence-140430143751-phpapp02/75/CrowdCast-Monthly-Operationalizing-Intelligence-22-2048.jpg)