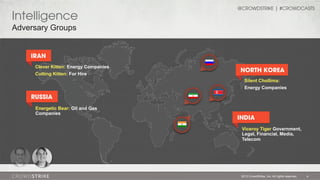
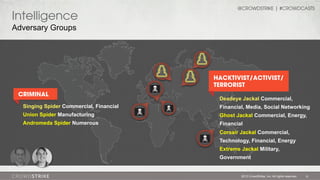
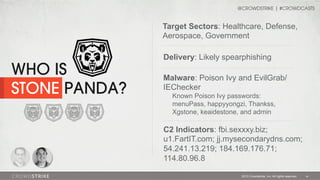
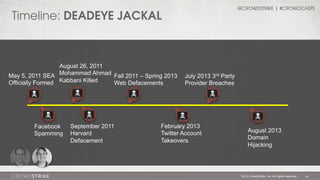
The document discusses adversary problems in cybersecurity, focusing on the identification and categorization of various adversary groups and their activities. It highlights notable adversaries, their motivations, and the tactics they utilize, such as spearphishing and lateral movement, while emphasizing the need for intelligence-driven security. The presentation also includes insights from CrowdStrike experts and encourages organizations to implement adversary-focused security practices.