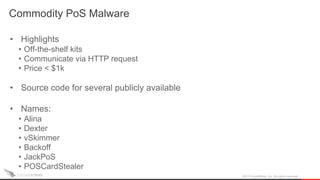
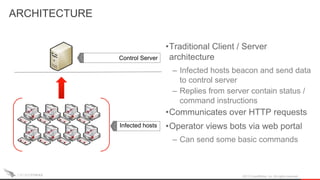
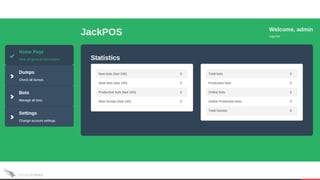
The document discusses the shifting landscape of point-of-sale (POS) malware. It covers the rise of commodity POS malware kits that are cheap and available online. It also discusses targeted breaches like the one against Target in 2013 where tailored malware was used to steal payment card data from their POS systems. Looking forward, the document discusses how the liability shift for EMV compliance in October 2015 and migration to tokenization systems may help address POS payment card theft going forward.









![What makes it targeted
2015 CrowdStrike, Inc. All rights reserved.
• [ Quality of Malware ] != Targeted
• Tailored options
( Implants designed to work in one infrastructure)
• Only targets specific PoS terminal types
• Logs to Internal IP addresses
• Forensic countermeasures
• Limited client-side controls*](https://image.slidesharecdn.com/output-150322194042-conversion-gate01/85/The-Shifting-Landscape-of-PoS-MalwareOutput-19-320.jpg)





![Looking Forward
2015 CrowdStrike, Inc. All rights reserved.
• October 2015 Liability Shift
• “ The party that has made investment in EMV deployment is protected from
financial liability for card-present counterfeit fraud losses on this date. If neither
or both parties are EMV compliant, the fraud liability remains the same as it is
today.” [1]
• Tokenization of Payment Methods
• iPay
• Google Wallet
[1]http://www.emv-connection.com/emv-migration-driven-by-payment-brand-milestones/](https://image.slidesharecdn.com/output-150322194042-conversion-gate01/85/The-Shifting-Landscape-of-PoS-MalwareOutput-25-320.jpg)

