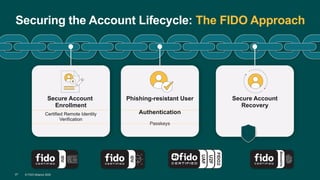
The FIDO Alliance aims to reduce reliance on passwords through secure, interoperable authentication standards while addressing growing online fraud, which exceeded $1 trillion in 2023. Their focus is on promoting phishing-resistant authentication methods, such as passkeys, which have shown significant adoption and effectiveness in improving login speed and reducing security incidents. The alliance also emphasizes the importance of user education and adoption in the transitioning to these new authentication solutions.