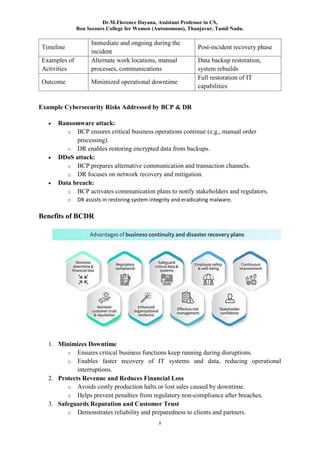
Fundamentals of Risk Management, Risk Management Life cycle,Identify the Risk, Assess the Risk, Treat the Risk, Monitor the Risk, Risk Assessment Frameworks, Risk Mitigation, Risk Mitigation Strategies, Risk Avoidance, Risk Reduction, Risk Transfer, Risk Acceptance, Business Continuity Planning, Key Components of BCP, Disaster Recovery (DR), Key Components of DR, How BCP and DR Work Together in Cybersecurity, Benefits of BCDR