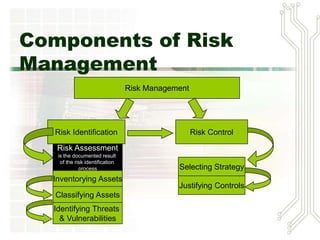
This document discusses risk management for information security. It defines risk management as identifying and controlling risks to an organization. The key components of risk management are risk identification, risk assessment, and risk control. Risk identification involves inventorying assets, identifying threats and vulnerabilities. Risk assessment evaluates the likelihood and impact of risks. Risk control strategies include avoidance, transference, mitigation and acceptance of risks. The goal is to reduce residual risks to a level acceptable for the organization.