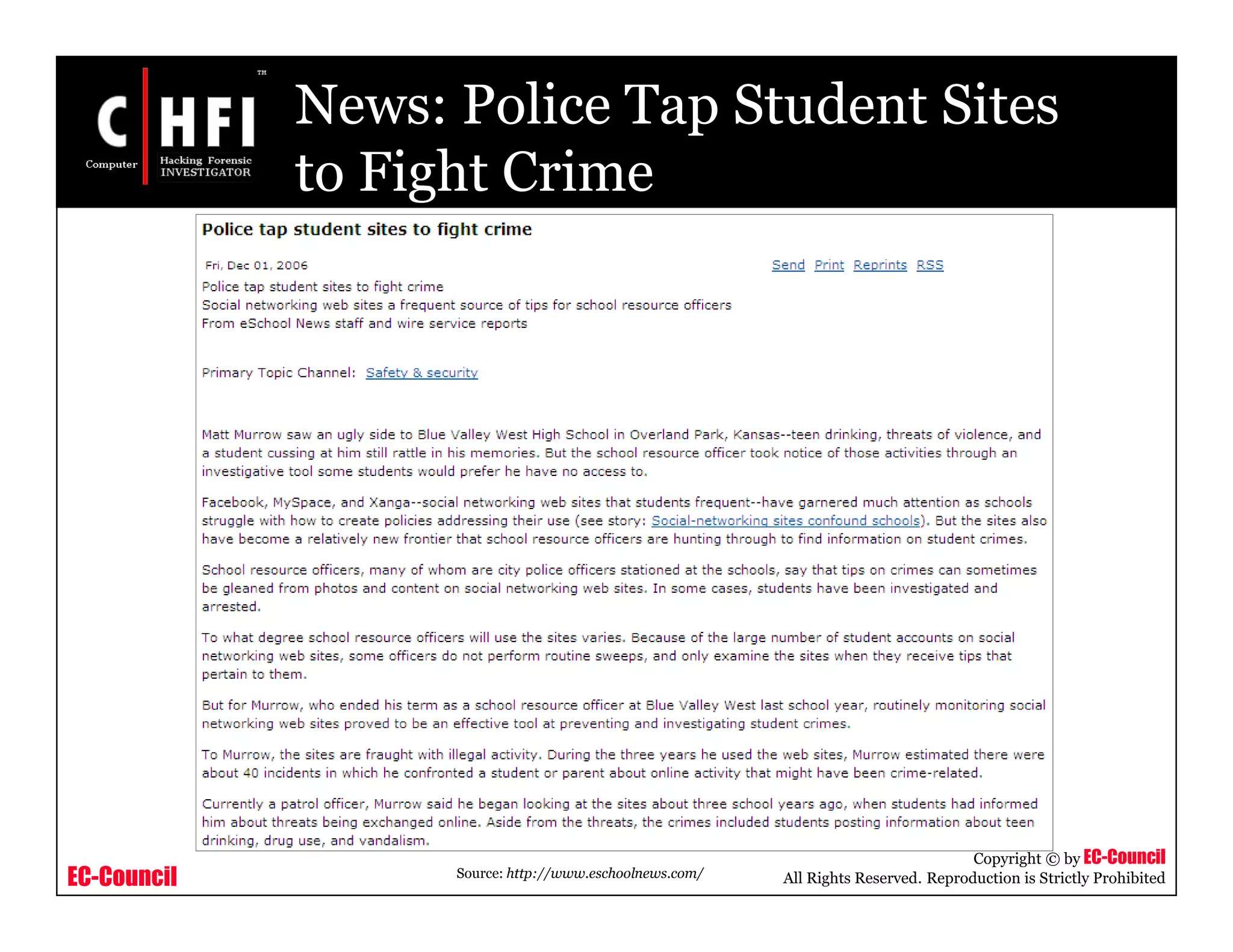
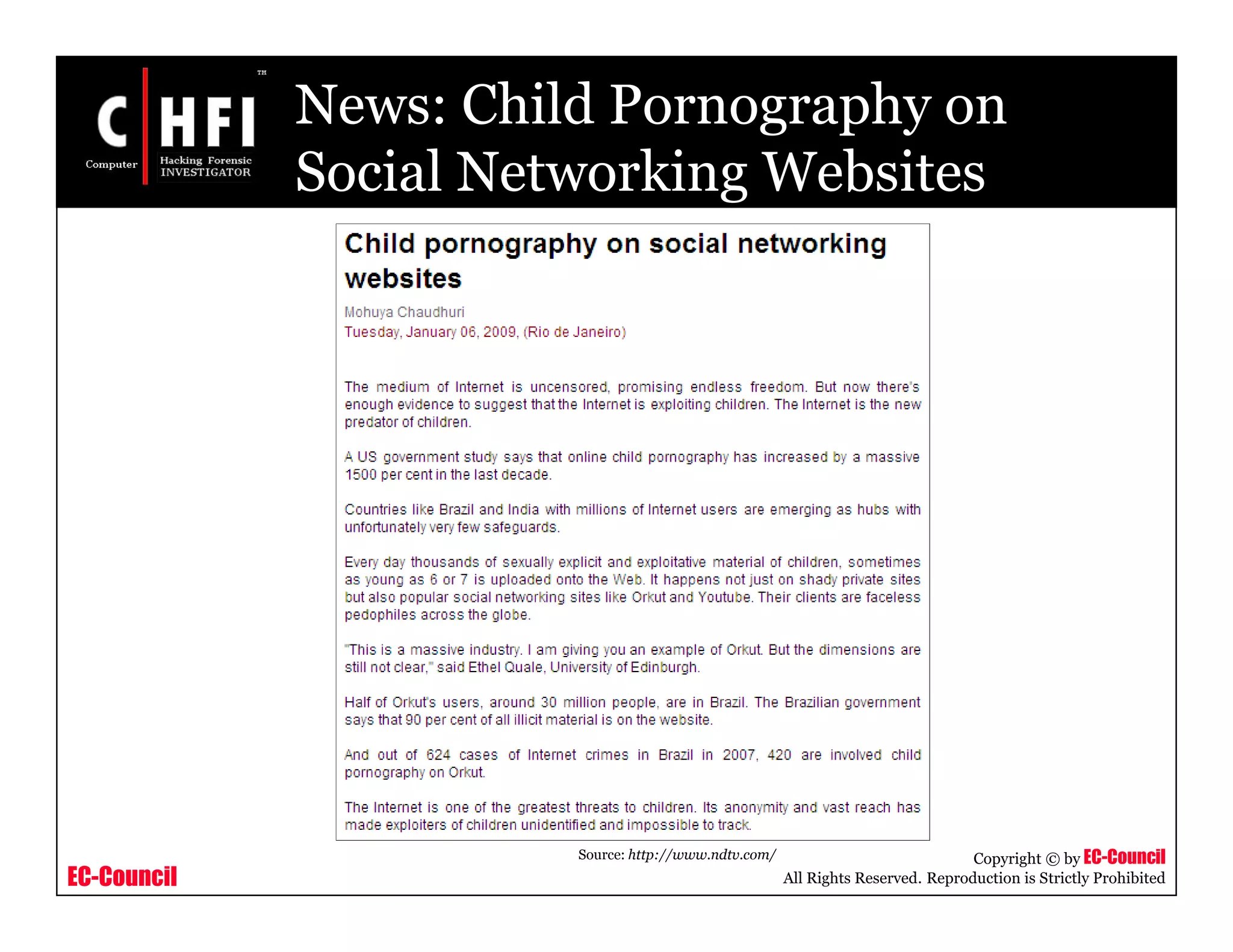
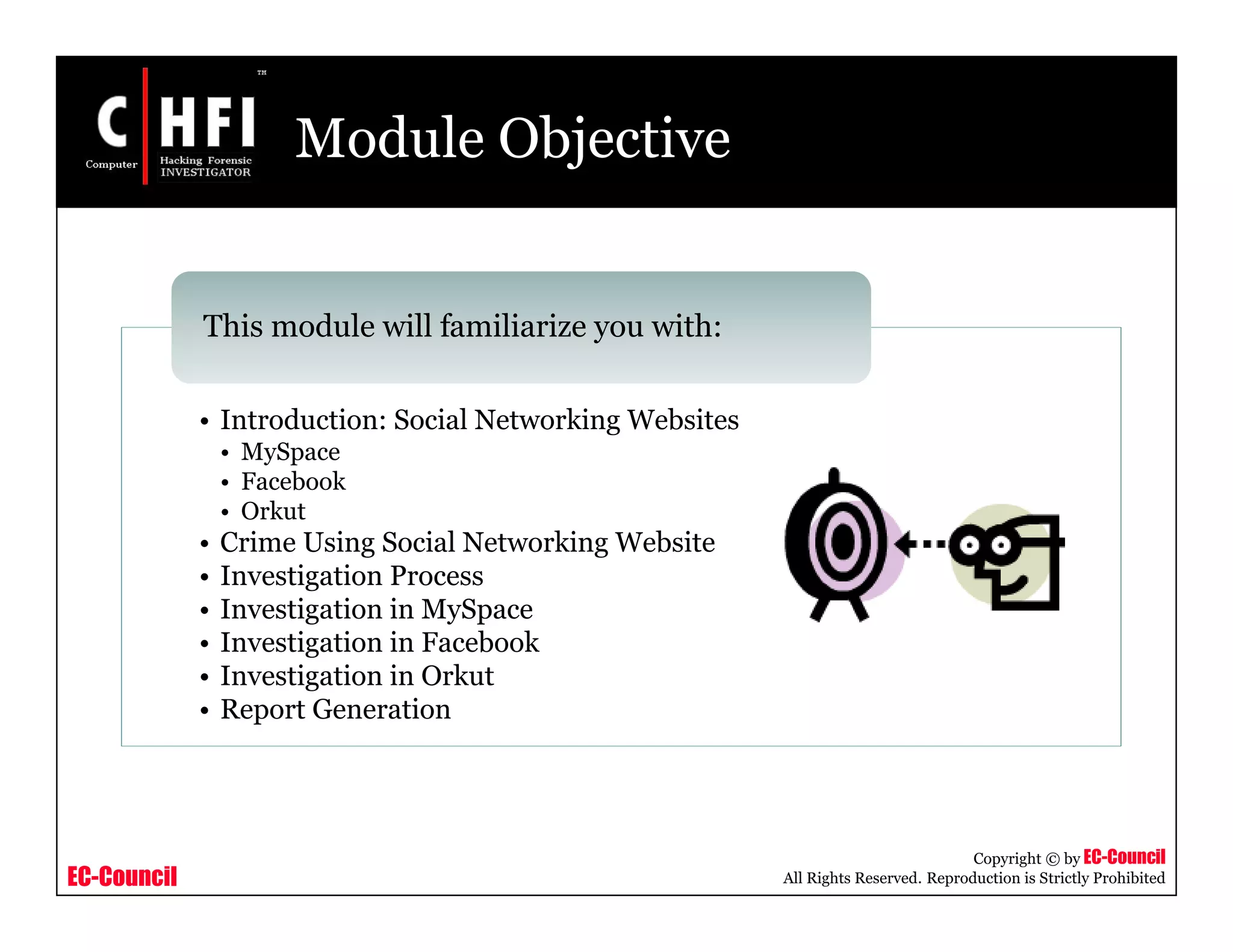
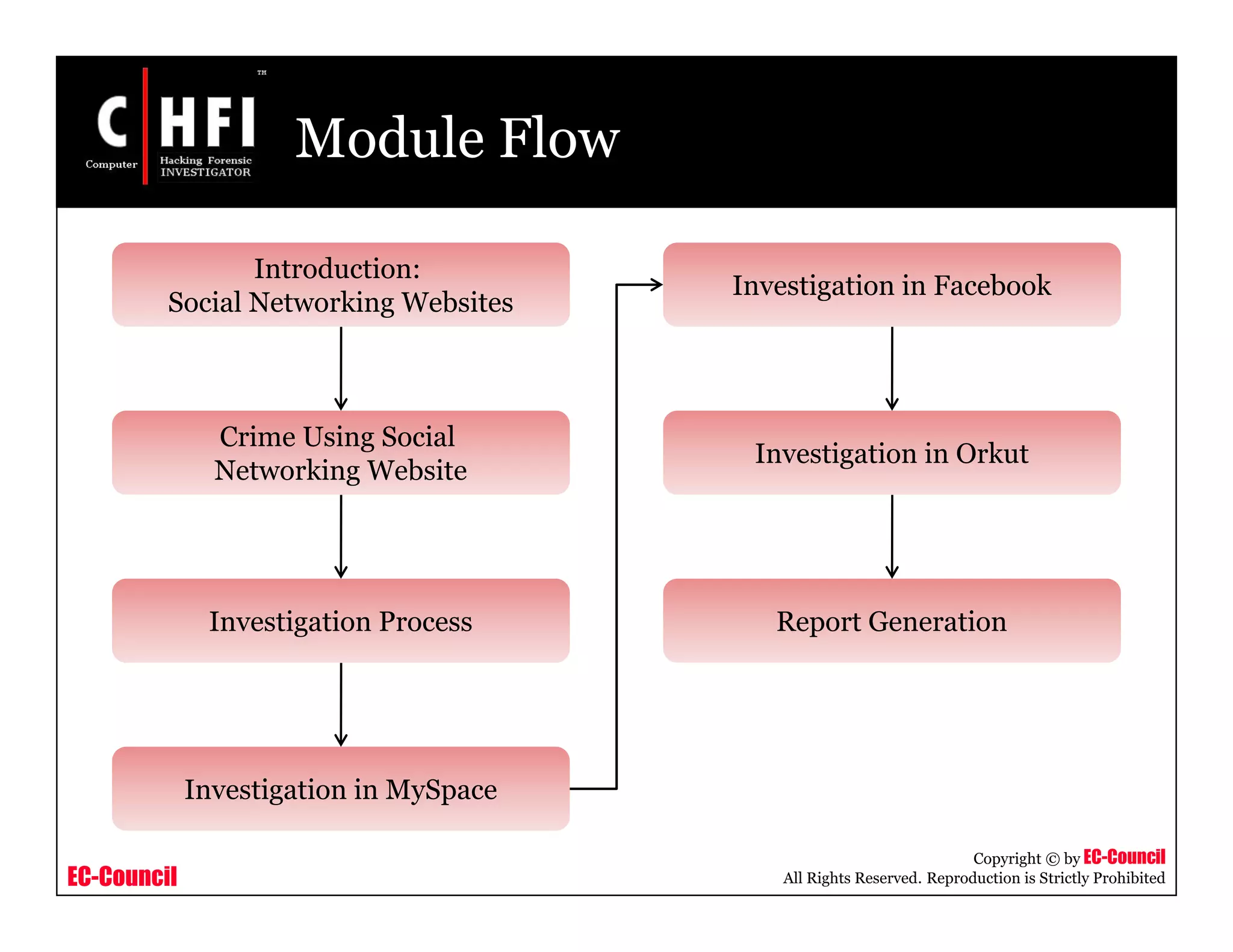
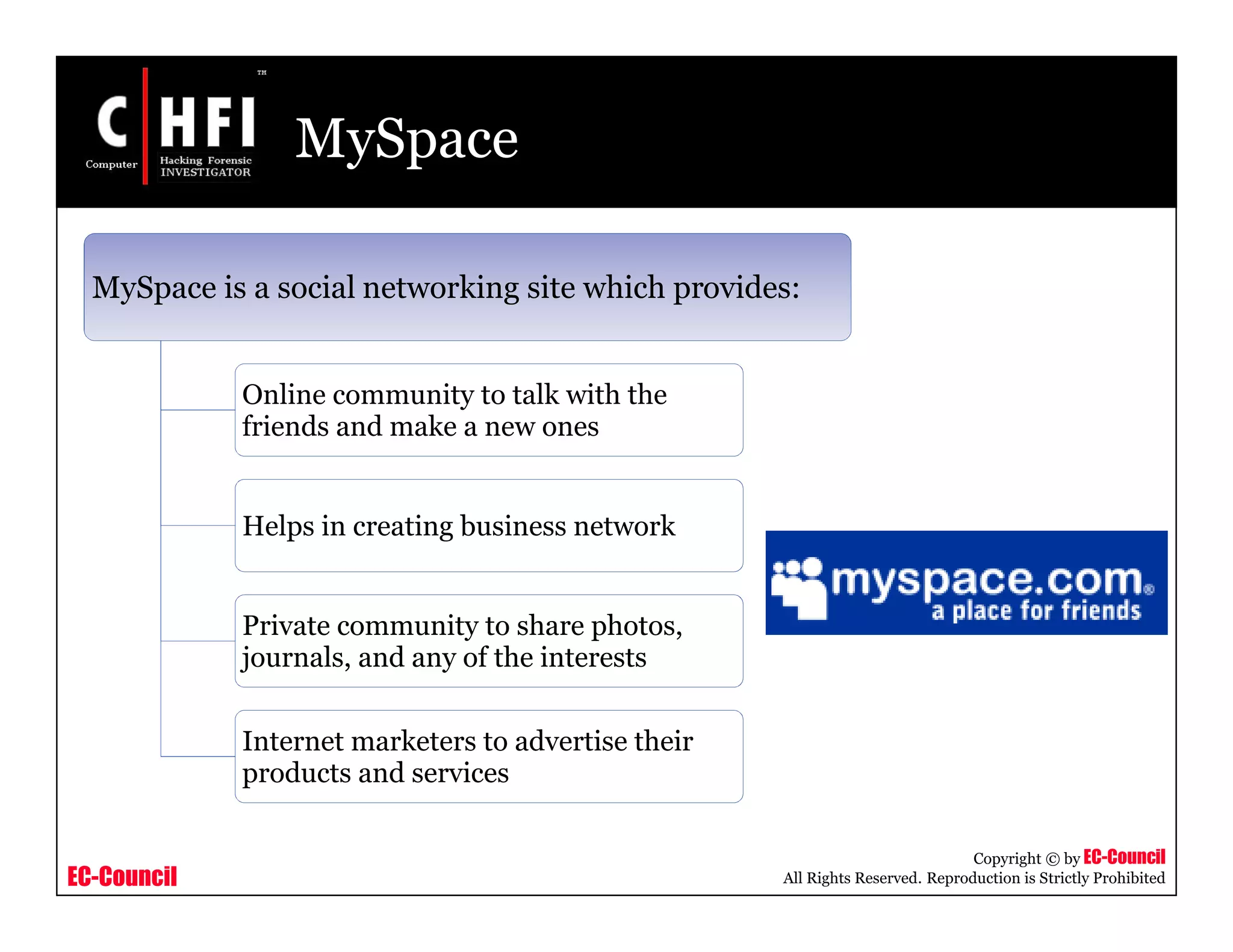
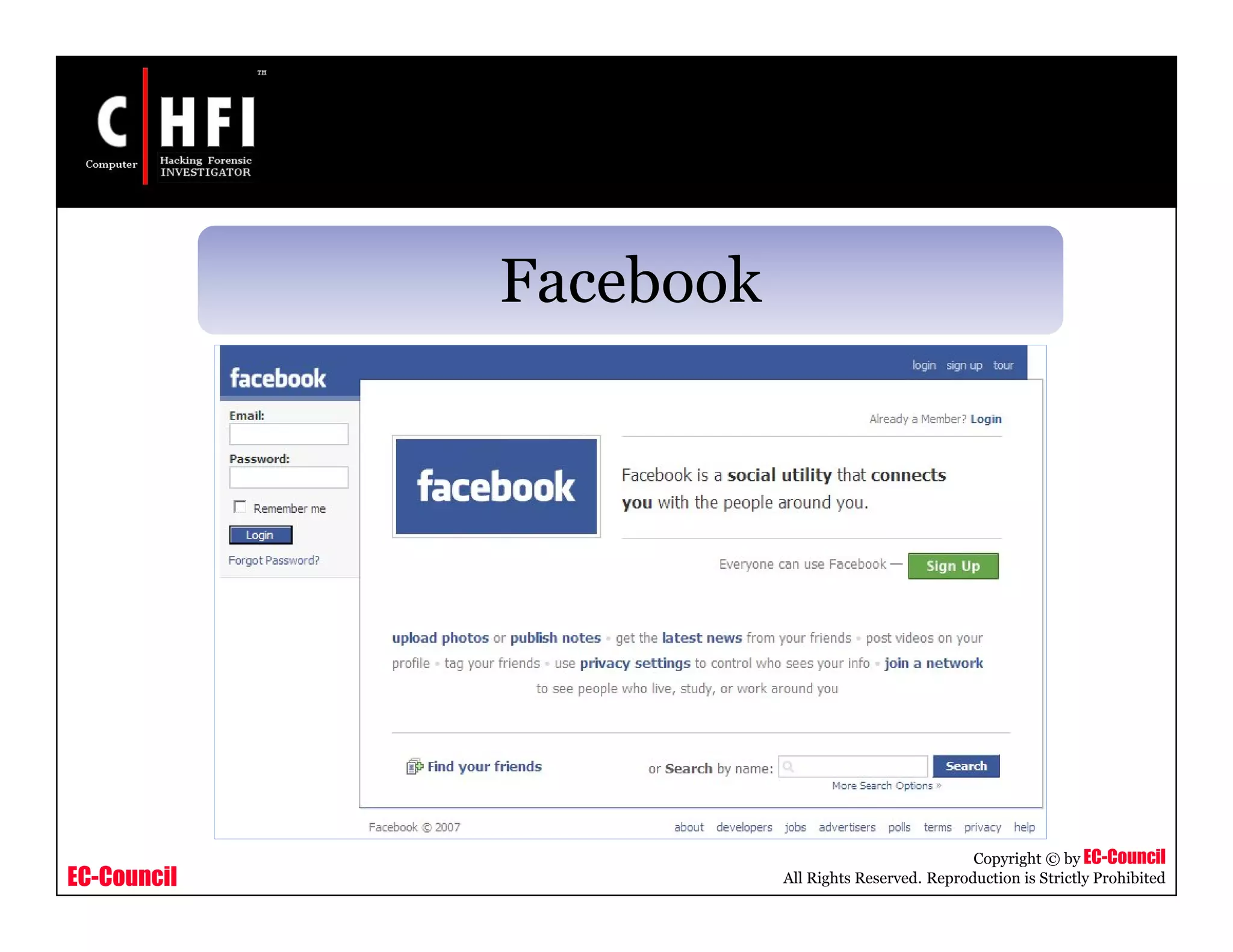
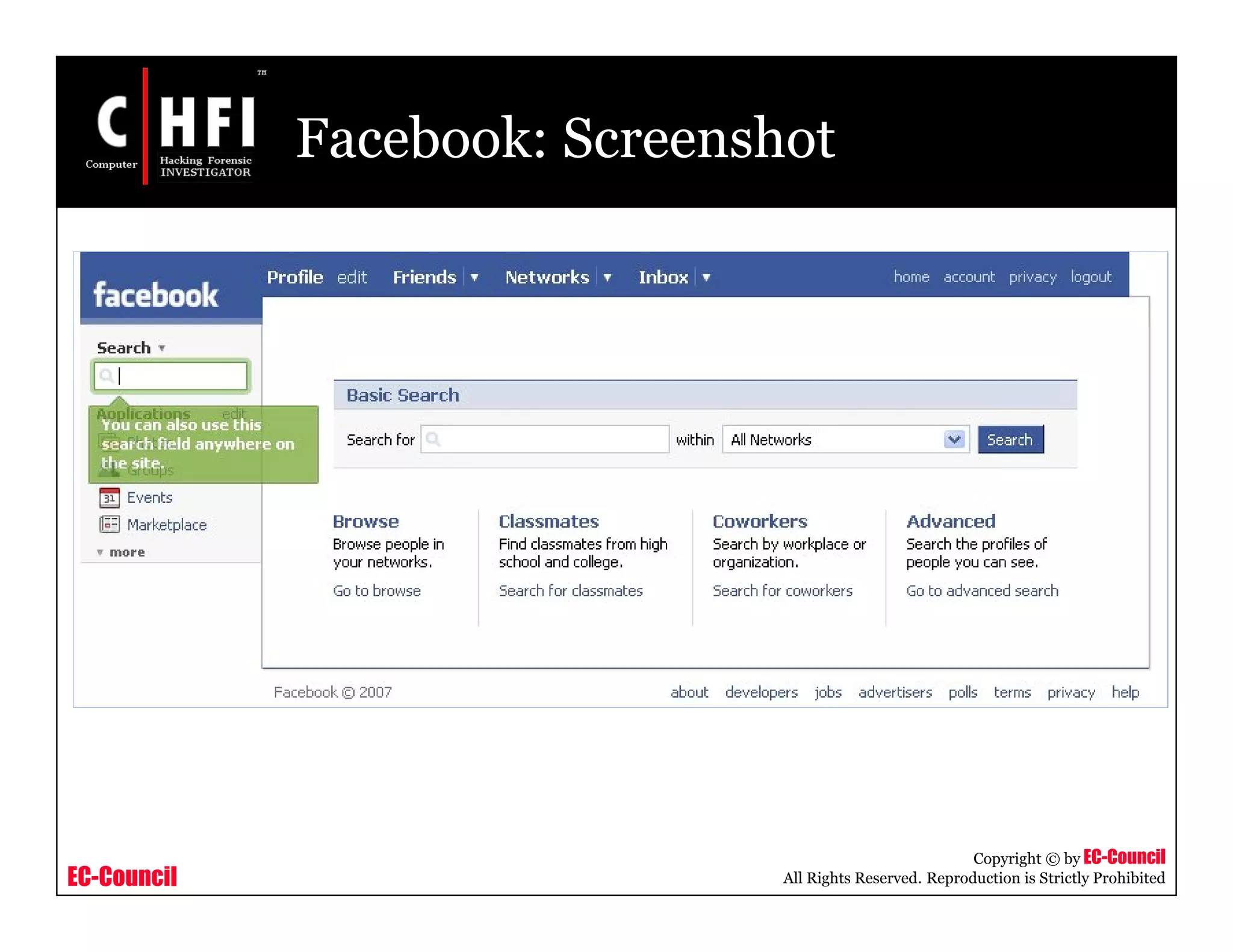
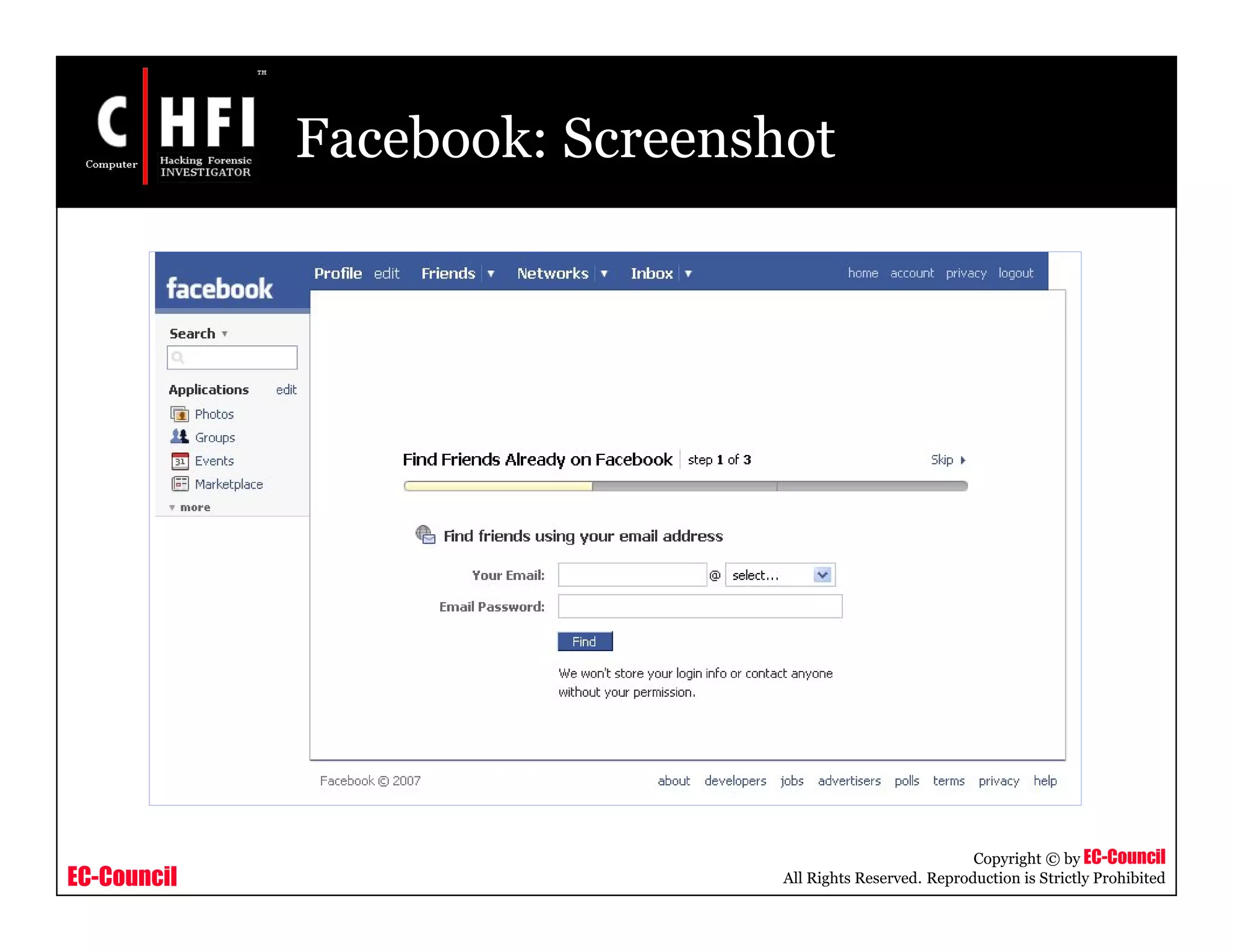
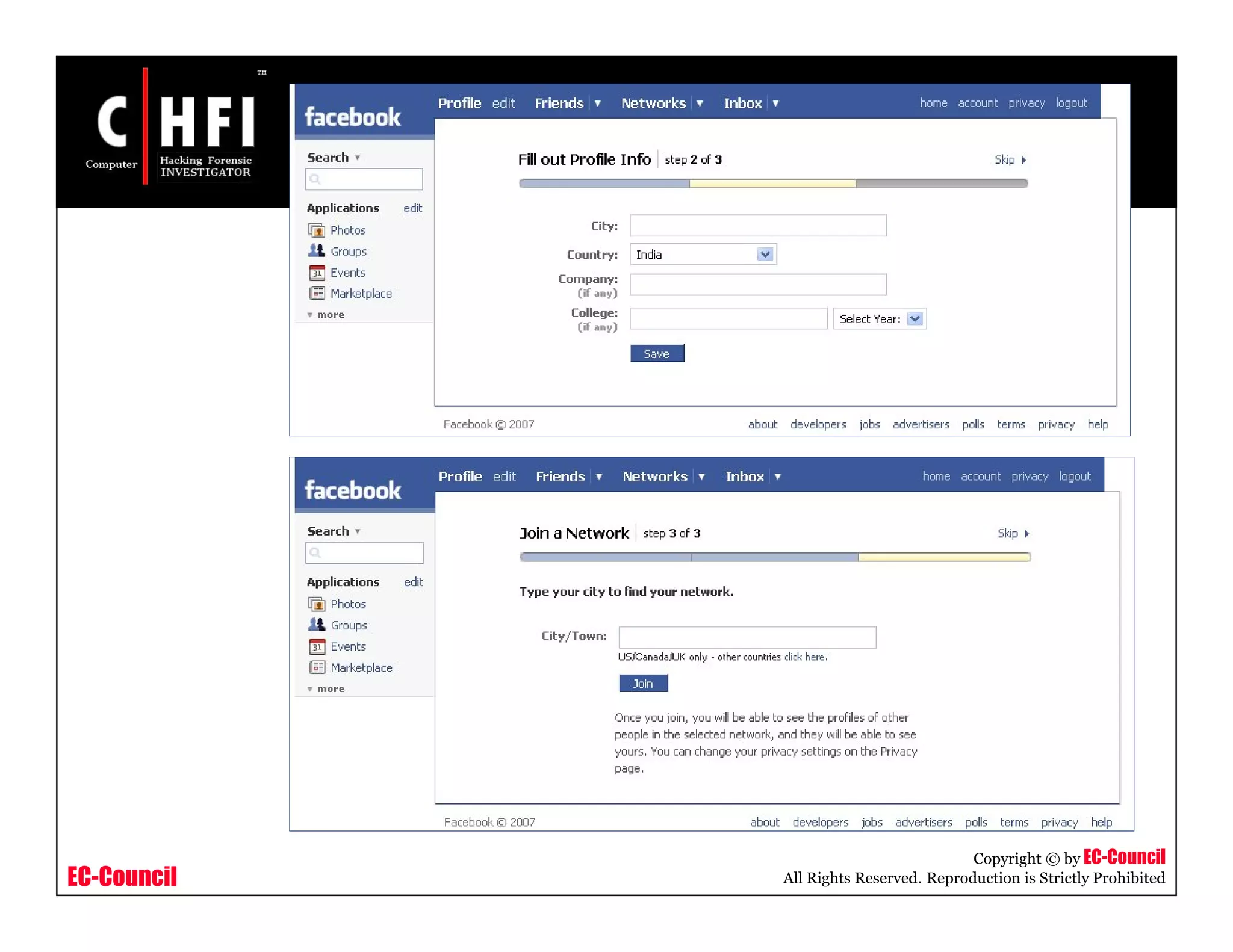
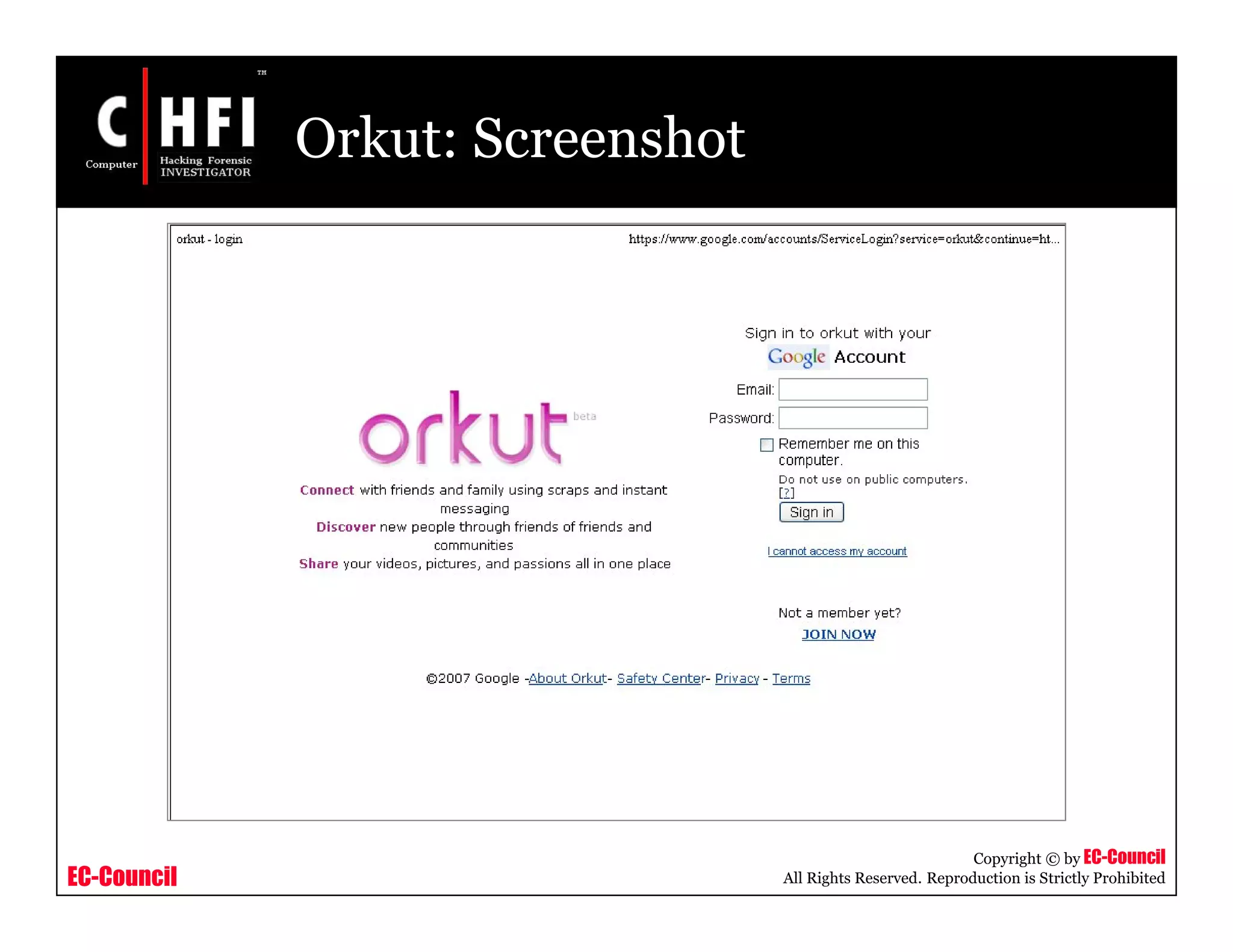
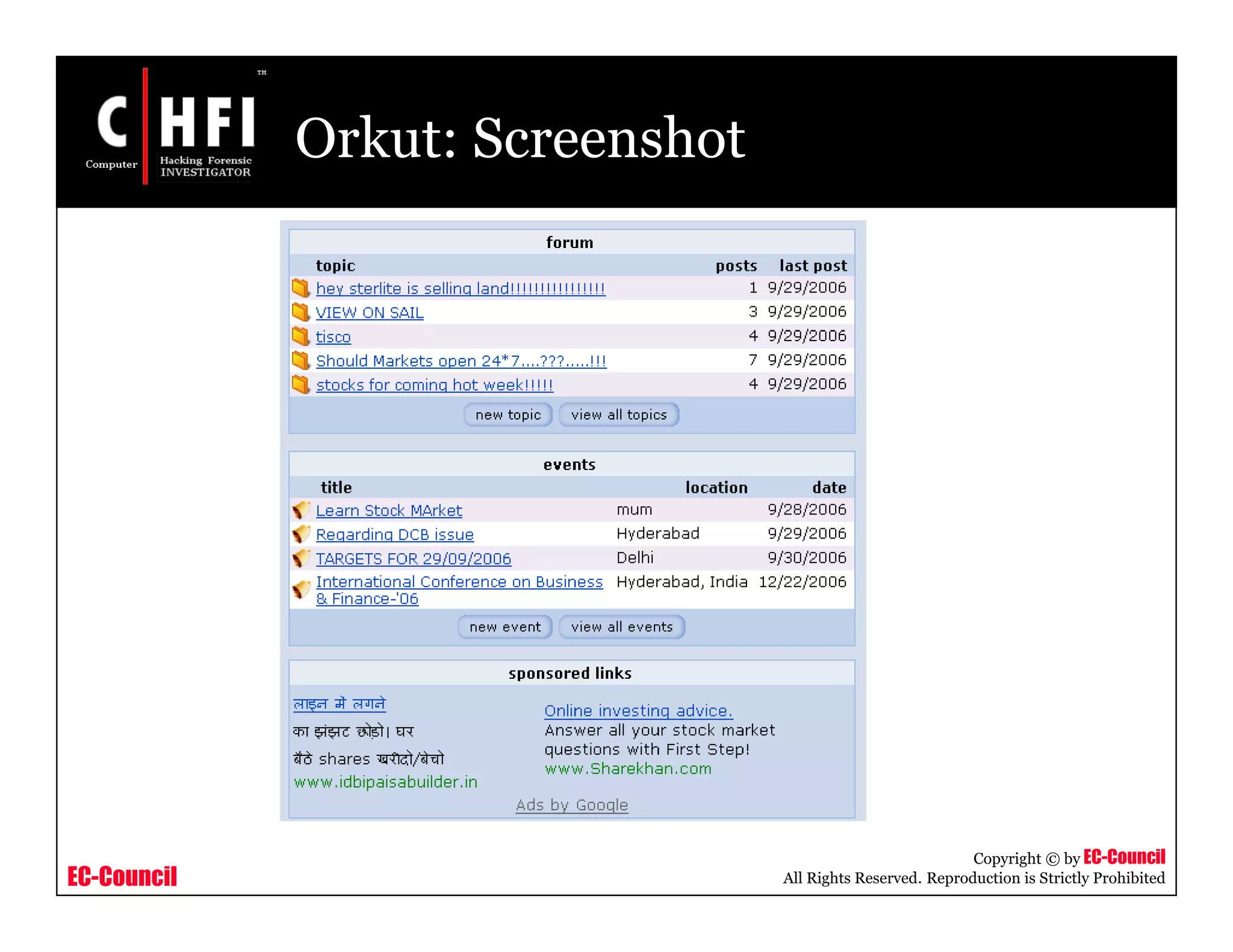
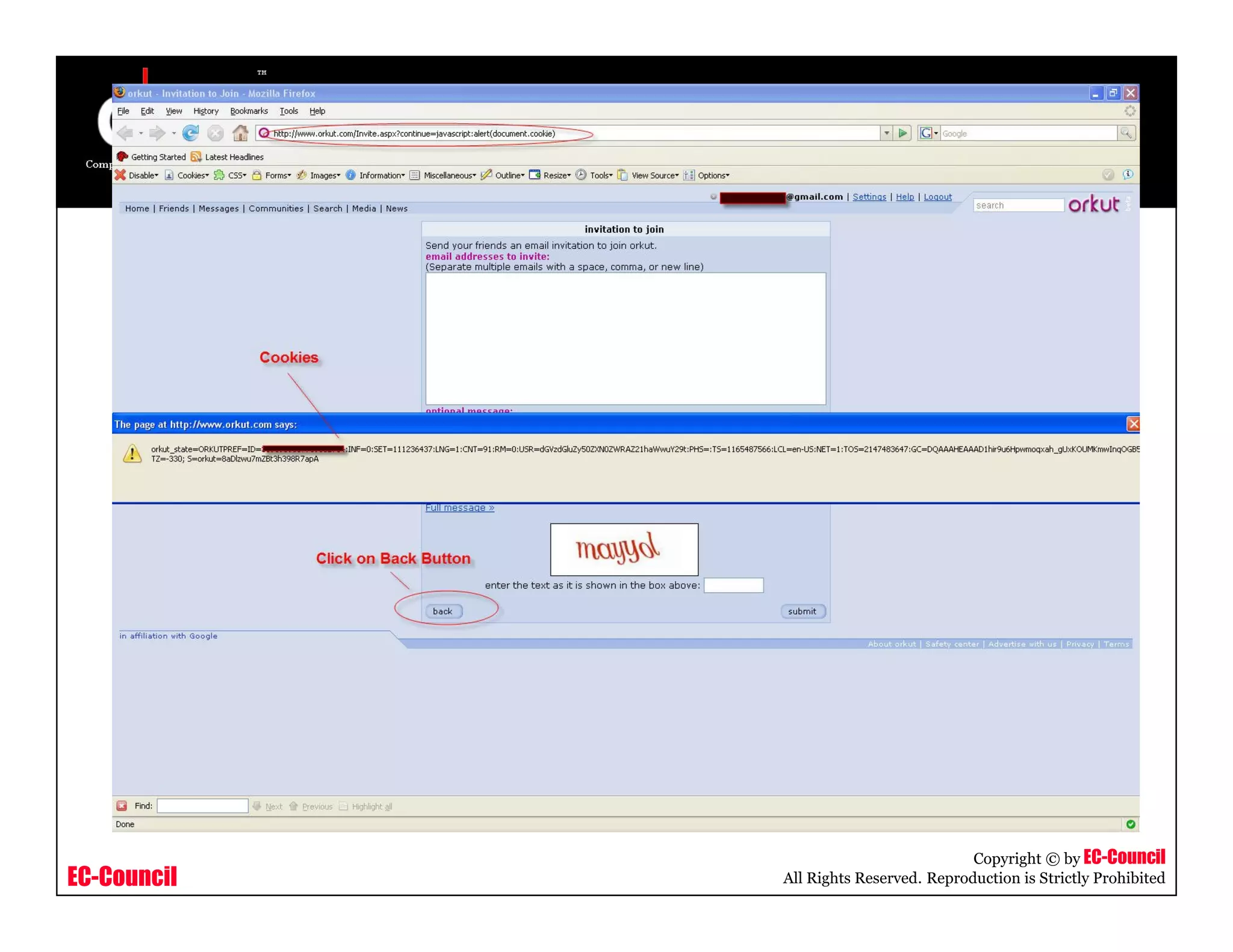
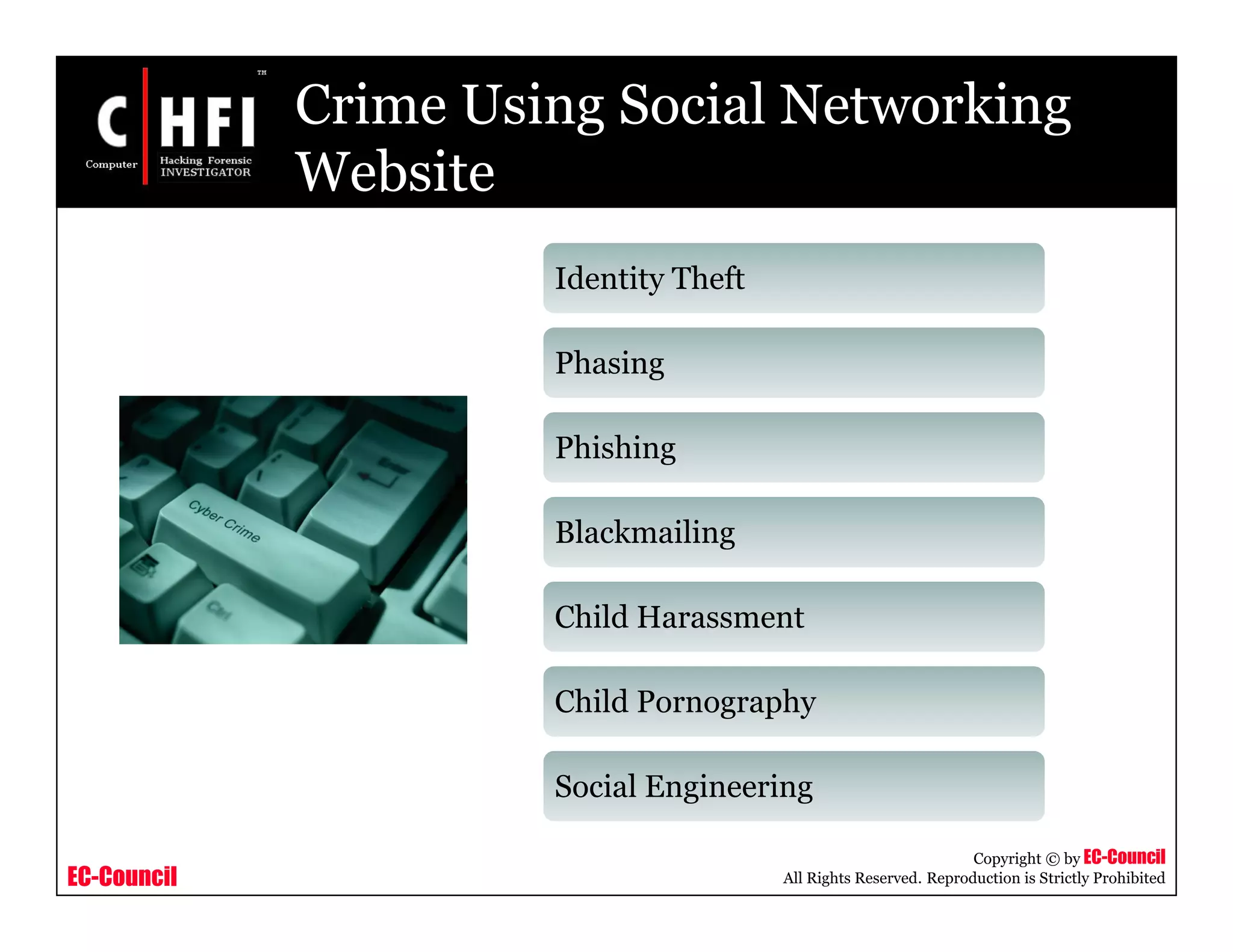
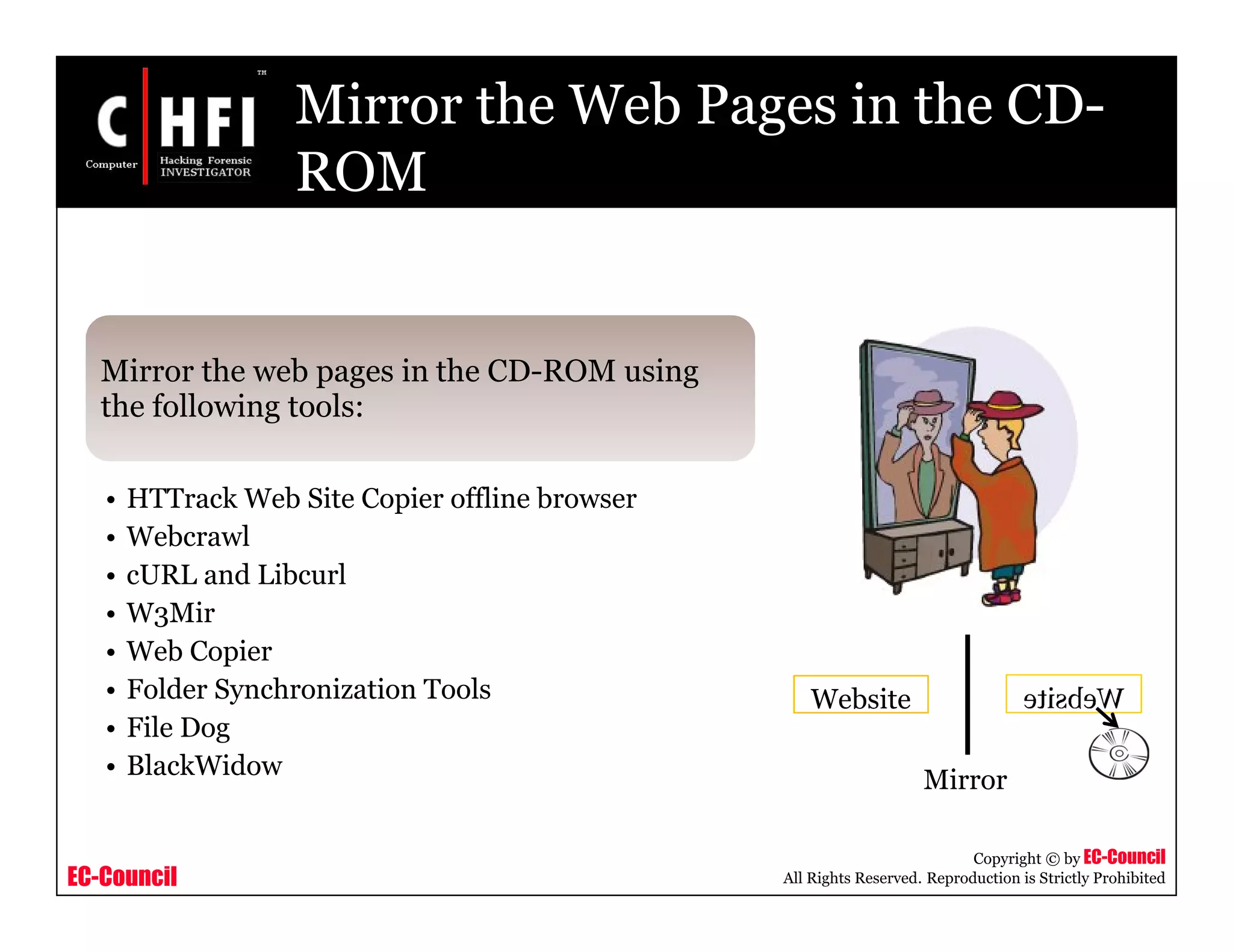
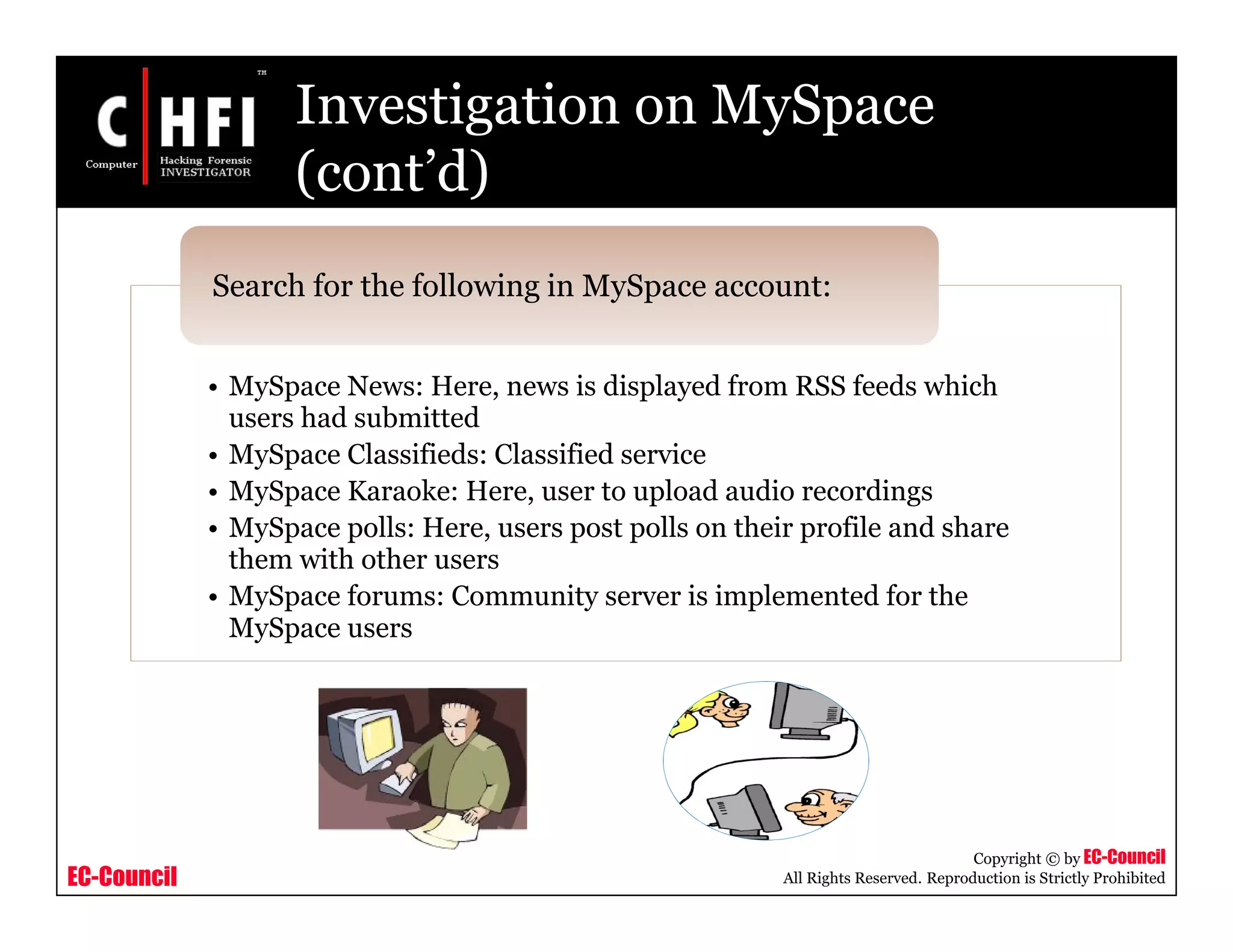
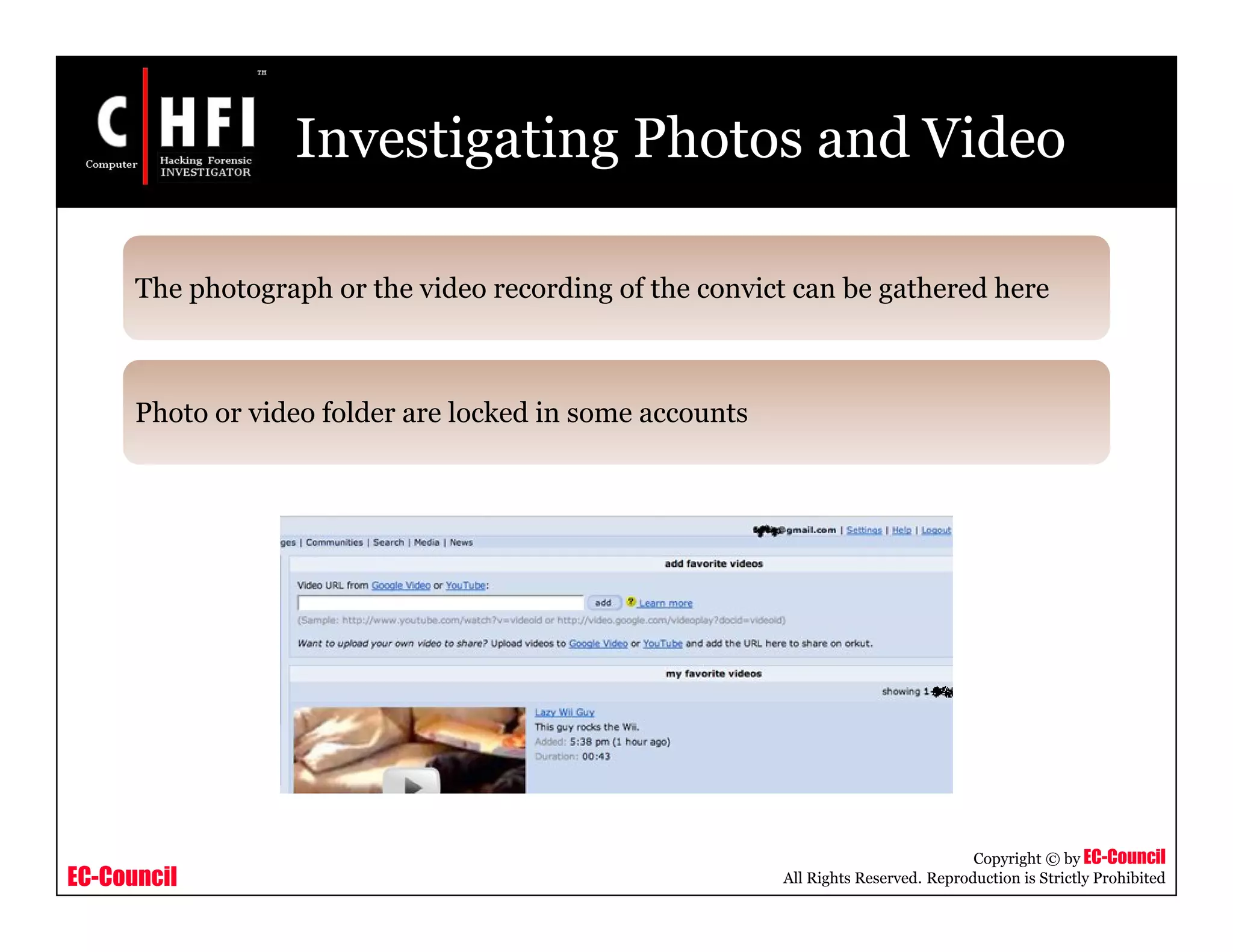
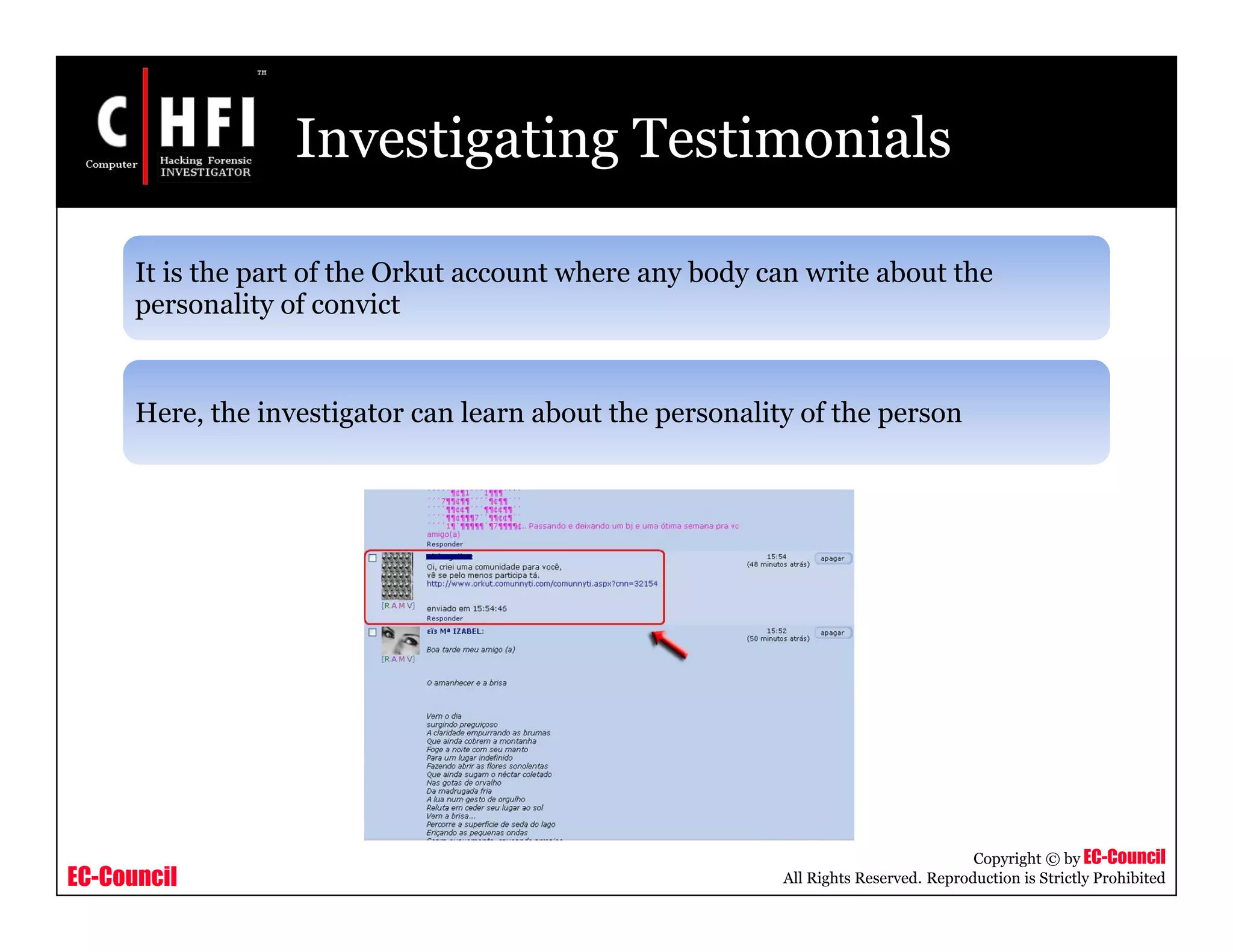
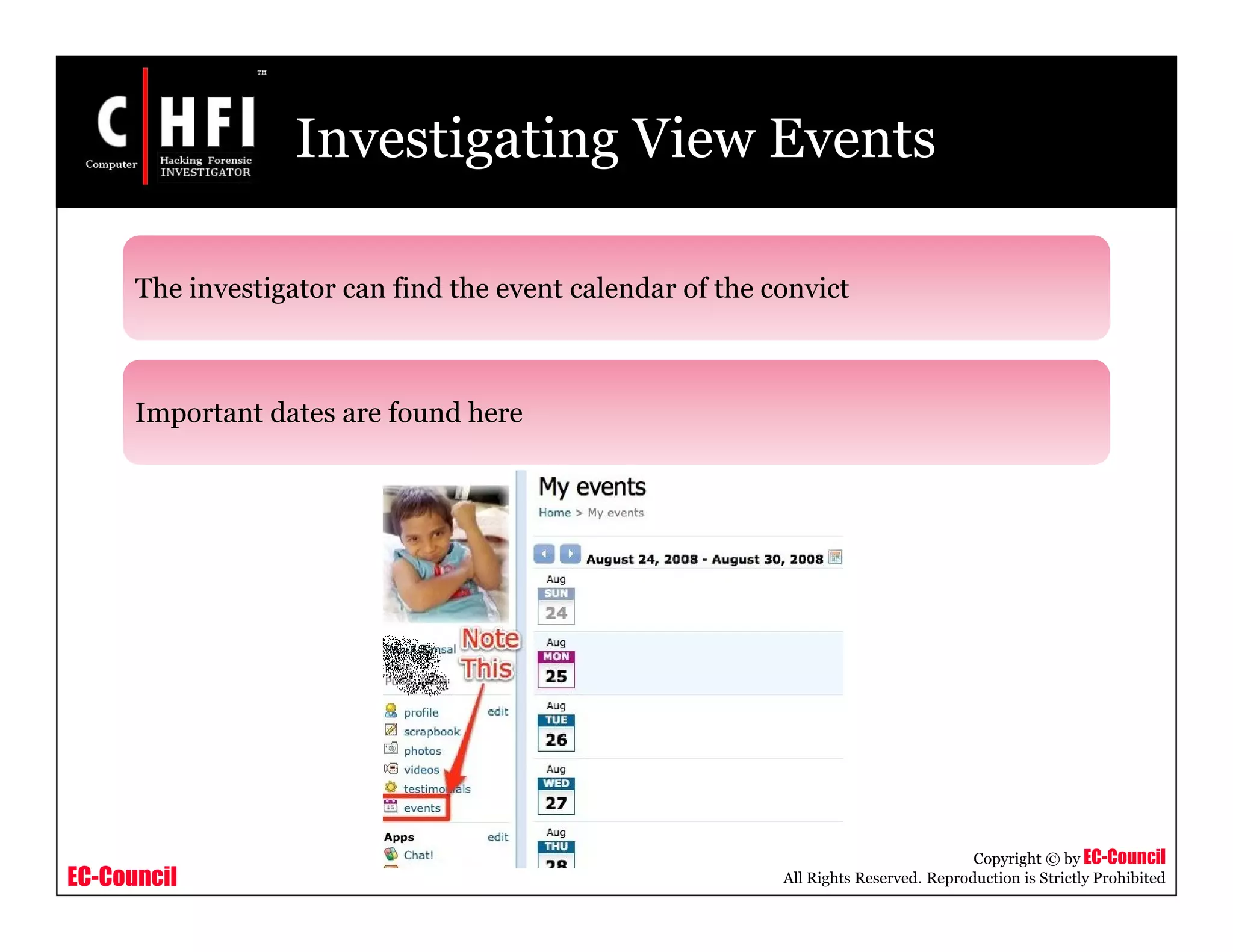
The document discusses investigating social networking websites for evidence. It provides an overview of social networking sites like MySpace, Facebook, and Orkut and how they are used. It outlines the investigation process, including searching for accounts, mirroring web pages, and documenting evidence. Specific areas of investigation on each site are examined, such as friend lists, photos, and comments. The summary report generation is also reviewed.