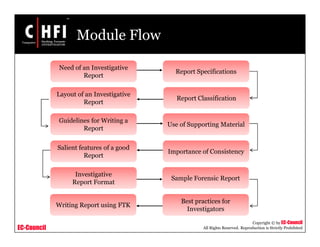
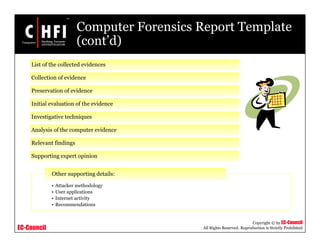
This document discusses best practices for writing investigative reports based on computer forensics investigations. It provides guidelines on the format, structure, and content of reports, including maintaining objectivity, documenting evidence collection methods, and including relevant findings, conclusions, and recommendations. The document also provides a sample report template and discusses using forensic analysis tools like FTK to help generate reports.