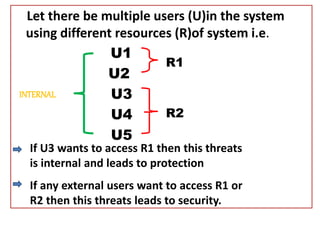
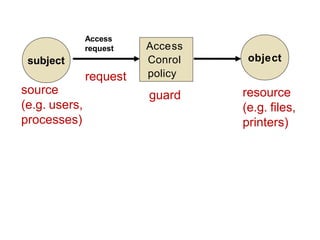
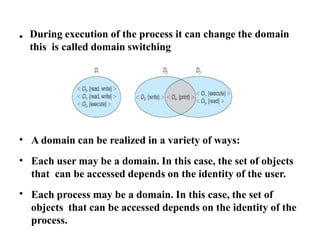
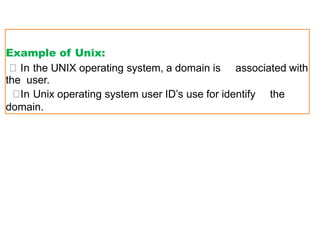
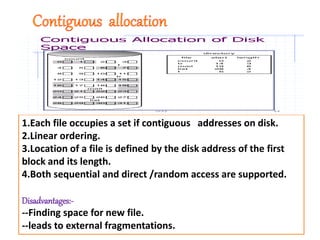
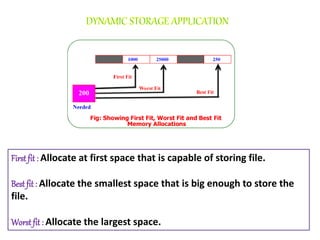
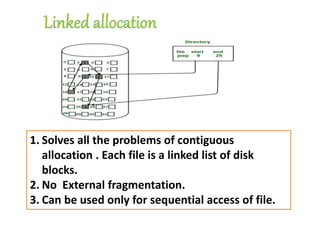
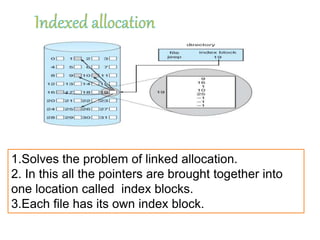
The document discusses file protection mechanisms to prevent unauthorized access in computer systems, highlighting internal and external threats. It covers concepts like access control, protection domains, and file allocation strategies, stressing the importance of efficient disk space utilization. The text also addresses challenges faced by OS designers in creating robust protection schemes.