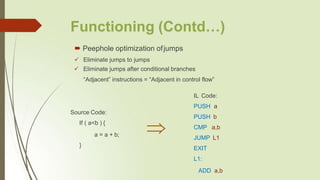
The document discusses peephole optimization, a technique that enhances the efficiency of small segments of code without altering their output. It outlines the goals of peephole optimization, such as improving performance and reducing code size, by using various strategies like constant folding and strength reduction. The conclusion emphasizes the continued relevance of peephole optimization for post-allocation improvements and its application in binary translation.









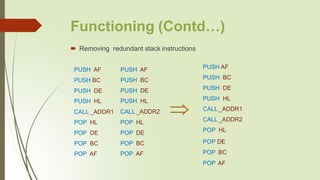
![Functioning (Contd…)
Removing redundant code
Another example is to eliminate redundant load stores.
a = b + c;
d = a + e;
is straightforwardly implemented as
MOV b,
ADD c,
MOV R0, a
MOV a,
ADD e,
MOV R0, d
R0 # Copy b to the register
R0 # Add c to the register, the register is now b+c
# Copy the register to a
R0 # Copy a to the register
R0 # Add e to the register, the register is now a+e [(b+c)+e]
# Copy the register to d](https://image.slidesharecdn.com/cd25017-meghaj-201020151739/85/Peephole-Optimization-10-320.jpg)
![Functioning (Contd…)
Removing redundant code
but can be optimized to
MOV b,
ADD c,
MOV R0, a
ADD e, R0
MOV R0, d
R0 # Copy b to the register
R0 # Add c to the register, which is now b+c (a)
# Copy the register to a
# Add e to the register, which is now b+c+e [(a)+e]
# Copy the register to d](https://image.slidesharecdn.com/cd25017-meghaj-201020151739/85/Peephole-Optimization-11-320.jpg)