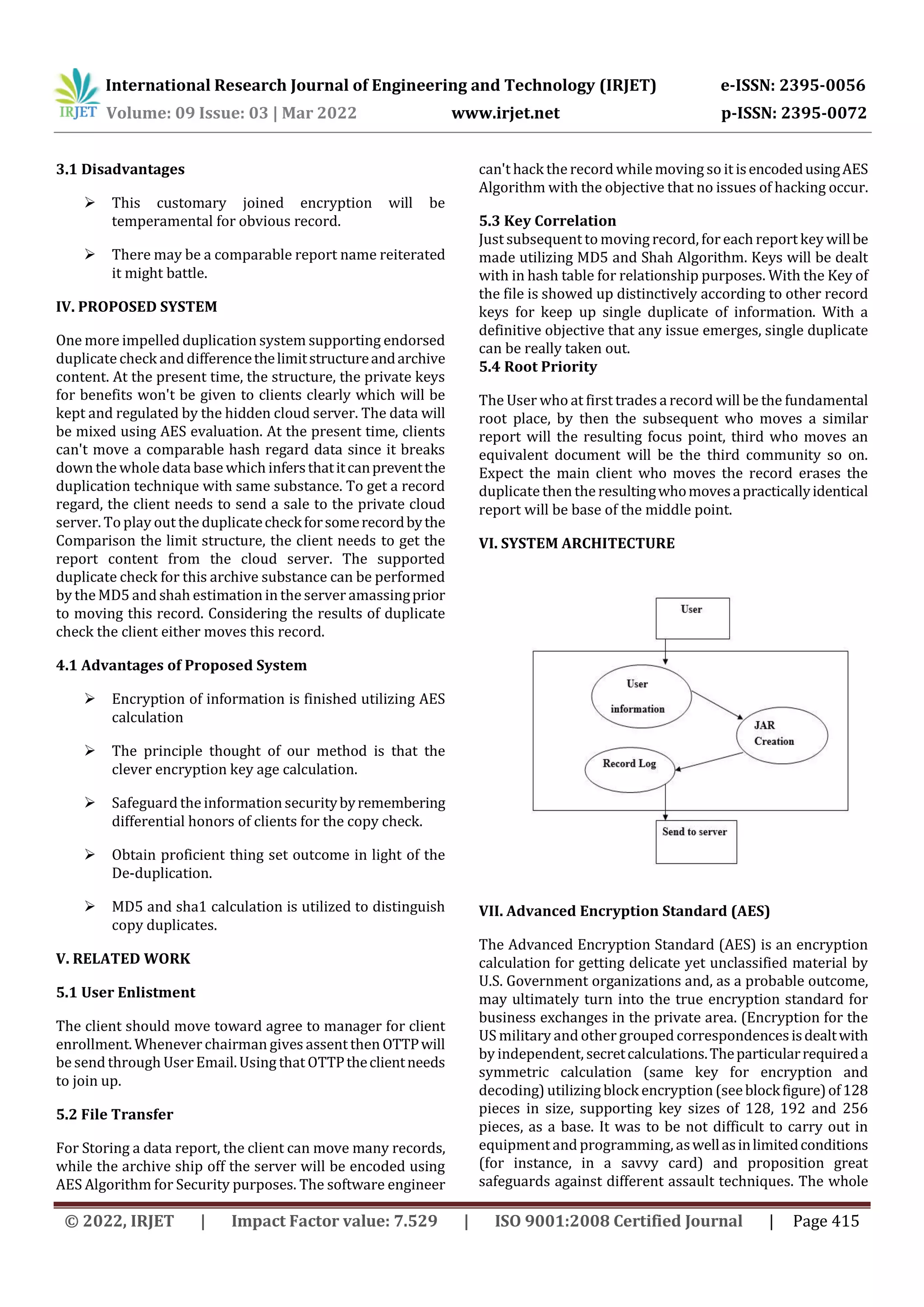
The document proposes a new deduplication system that supports endorsed duplicate check and separates the record structure and substance. It utilizes AES calculation to encrypt information for security. MD5 and sha1 calculations are utilized to recognize duplicate records. The private cloud is outfitted with mystery validation to give more prominent security. The proposed framework separates record structure and substance and underpins endorsed duplicate check to give proficient deduplication while ensuring information security in the cloud.
![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 03 | Mar 2022 www.irjet.net p-ISSN: 2395-0072
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 414
EXPLORING WOMEN SECURITY BY DEDUPLICATION OF DATA
Priyadharsini R[1], Mrs C. Soundarya M.E.[2]
[1]Student, Dept. of Computer Science Engineering , Jayalakshmi Institute of Technology, Dharmapuri, Tamil Nadu,
India.
[2]Professor, Dept. of Computer Science Engineering, Jayalakshmi Institute of Technology, , Dharmapuri, Tamil
Nadu, India.
-------------------------------------------------------------------------***------------------------------------------------------------------------
Abstract - To reduce the enrolling time and reaction time
between Token deals and reaction, File move or download
deals and results. It reduces the extent of extra room in
scattered limit. To get the assurance of information
differential upheld copy check is utilized. It presents this
embraced copy check in cream cloud plan. The mutt cloud
setup proposes in regards to both the open cloud and the
private cloud. To give more imperative security, the private
cloud is equipped with dazed affirmation. Levelsofprogressin
scattered enlisting are inciting a promising future for
Collaborative Cloud Computing (CCC). Todiminishthedealing
with time and reaction time between Token mentioning and
reaction, File move or download deals and results. Where
generally spread dissipated cloud assets having a spot with
various affiliations or people (i.e., parts) are aggregately
utilized in a strong way to give organizations. The records are
managed in the cloud. That is each client enlists an
information key to encode the information that he means to
store in the cloud. It depicts a computationally modest
procedure for making all log regions made. Going before the
logging machine's trade off tremendous for the assailant to
analyze furthermore hard to indistinguishably change or
pulverize. That is each client works out an information key to
encode the information that he desires to store in the cloud.
Key Words: Collaborative Cloud Computing (CCC), cloud.
I.INTRODUCTION
To decrease the figuring time and response time between
Token referencing and response, File move or download
arrangements and results.It reducesthedegreeofadditional
room in flowed limit. To get the mystery of data differential
upheld duplicate check is used. It presents this embraced
duplicate check in cross arrangement cloud arranging. The
mutt cloud arranging proposes as for both the open cloud
and the private cloud. To give more obvious security, the
private cloud is outfitted with stunned check. Levels of
progress in streamed enrolling are actuating a promising
future for Collaborative CloudComputing(CCC).Todiminish
the enlisting time and response time between Token
arrangements and response, File move or download
arrangements and results. Where completely scattered
conveyed cloud resources having a spot with different
affiliations or individuals (i.e., parts) are everything viewed
as used in a delightful manner to offer sorts of help. The
archives are managed in the cloud. That is every client
figures a data key to encode the data that he hopes to store
in the cloud. It portrays a computationally simple strategy
for making all log regions made. Before the logging
machine's compromise astounding for the aggressor to take
a gander at what's more challenging to disastrously change
or pound. That is every client chooses a data key toscramble
the data that he wants to store in the cloud.
Data De-duplication with centre point is one of fundamental
data uncovering structures for taking duplicate copies of
reiterating data. It took a gander at the degree of additional
room and extra exchange speed.Toguaranteethemystery of
delicate data while supporting De-duplication with centre
point, the simultaneous encryption structure has been
proposed to scramble the data going before overhauling.We
propose one more moved duplication system supporting
embraced duplicate check andpartitiontheremoveplanand
record substance. The cross-breed cloud arrangement
proposes in regards to both the open cloud and the private
cloud. Appropriately, equivocal data copies of different
clients will incite gathered figure works, making De-
duplication with centre point unimaginable. To give more
basic security, the private cloud is outfitted with stunned
assertion.
II. PROBLEM STATEMENT
The Main point of deduplication to give security on friendly
sites keeping away from numerous duplicates of same
information so that any issues emerge the duplicate of the
information can be taken out.
III. EXISTING SYSTEM
The combined encryption methodology has been proposed
to scramble the data before re-appropriating. To all the
almost certain guarantee data security, this system makes
the chief undertaking formally address the issue of
supported data De-duplication.Particularfilenameinviewof
the differential advantages of clientsarealsothoughtto bein
duplicate check archive name trademark the actual data. It
moreover shows a couple of new De-duplication
improvements supporting endorsed duplicate. Data dealing
with in the cloud encounters a capricious and dynamic
different evened out to organization chain. Thereisnomuch
thing as this in standard circumstances. Standard web
structure Uses web organizations for sales and responses.](https://image.slidesharecdn.com/irjet-v9i376-220915121430-53cb5d24/75/EXPLORING-WOMEN-SECURITY-BY-DEDUPLICATION-OF-DATA-1-2048.jpg)
![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 09 Issue: 03 | Mar 2022 www.irjet.net p-ISSN: 2395-0072
© 2022, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 416
choice interaction was completely open to public
investigation and remark, it being concluded that full
perceivability would guaranteethemostidealexaminationof
the plans. Based on this, in August 1999, NIST chose five
calculations for more broad investigation. These were:
• MARS, presented by a huge group from IBM
Research
• RC6, put together by RSA Security
• Rijndael, put together by two Belgian
cryptographers, Joan Daemen and Vincent Rijmen
• Snake, put togetherbyRossAndersen,EliBihamand
Lars Knudsen
Two fish, put together by an enormous group of specialists
including Counterpane's regarded cryptographer.
VIII. CONCLUSION
The recently proposed framework is finished framework to
safely reevaluatelog recordsto a cloudsupplier.Inthiswork,
discover the difficulties for a solid cloud-based log the
executives administration. The aggressors use under three
stages to hack. To begin with, the assailant can catch any
message sent over the Internet. Second, the assailant can
integrate, imitate, and replay messages in his ownership and
the aggressor can be an authentic member of the
organization or can attempttomimicgenuinehosts.Itcarries
out how to store secure log document in cloud and that
record we can change read, compose, erase, transfer and
download. It can carry out AES calculation that utilizations
for log screen and log generator. One of the novel difficulties
is the issue of log security that emerges when we re-
appropriatedlog the executives to the cloud.Logdataforthis
situation ought not be nonchalantly linkable or recognizable
to their sources duringcapacity,recoveryanderasure.Itgave
mysterious transfer, recover and erase conventions on log
records in the cloud utilizing the Tor organization. The
conventions that it produced for this reason have potential
for use in various regions including unknown distribute buy
in.
IX. FUTURE WORK
The fundamental thought of secure De-duplication
administrations can be executed given extra security
highlights insider assailant on De-duplication and pariah
aggressor byutilizingtherecognitionofdisguiseactionwhich
implies obscure individual taken and harm the information.
Thus, we disarray of the aggressor and the extra expenses
caused to recognizegenuinefromcounterfeitdataadded,and
the discouragement impactwhich, albeit difficulttoquantify,
assumes a critical part in keeping from the assailants, that
will hurtful for our information.
REFERENCES
[1] M. Abadi et al. Tensor flow: A system for large-scale
machine learning. In USENIX OSDI, pages 265–283, 2016.
[2] M. Abdalla and D. Pointcheval. Simple password-based
encrypted key exchange protocols. In CT-RSA, pages 191–
208. Springer, 2005.
[3] G. Bradski. The OpenCV Library. Dr. Dobb’s Journal of
Software Tools, 2000.
[4] M. Chen, S. Wang, and L. Tian. A high-precision duplicate
image deduplication approach. JCP, 8:2768–2775, 2013.
[5] F. Chollet et al. Keras. https://keras.io, 2015.
[6] P. K. Dhillon and S. Kalra. A lightweight biometrics based
remote user authentication scheme for iot services. Journal
of Information Security and Applications,34:255–270,2017.
[7] L. et al. A secure cloud storage system supporting privacy
preserving fuzzy deduplication.SoftComputing,20,012015.
[8] R. et al. Learning multiple visual domains with residual
adapters. In NIPS, pages 506–516, 2017.
[9] T. Granlund and the GMP development team. GNU GMP
The GNU Multiple PrecisionArithmeticLibrary,5.0.5 edition,
2012.
[10] K. Grauman and T. Darrell. Pyramid match hashing:
Sublinear time indexing over partial correspondences. In
IEEE CVPR 2007, pages 1–8. IEEE, 2007.](https://image.slidesharecdn.com/irjet-v9i376-220915121430-53cb5d24/75/EXPLORING-WOMEN-SECURITY-BY-DEDUPLICATION-OF-DATA-3-2048.jpg)