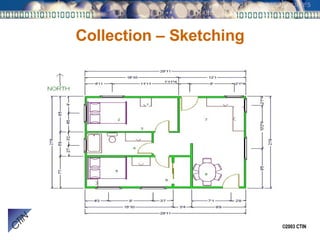
This document provides guidance on collecting and preserving high-tech evidence in criminal cases. It discusses identifying different types of computer-related evidence, such as hard drives, disks, and memory cards. Guidelines are given for photographing the evidence, sketching the layout, disconnecting computers safely, and transporting items securely. Maintaining a clear chain of custody for all evidence is emphasized, from seizure through presentation in court. The document also outlines proper storage conditions to prevent evidence degradation.








![Identification – General Concepts All computing evidence is considered physical evidence. [1] Information listed here are excerpts from the book “Digital Evidence and Computer Crime” by Eoghan Casey, Academic Press.](https://image.slidesharecdn.com/evidence-seizure-level-one-1205345340216912-2/85/Evidence-Seizure-Level-One-9-320.jpg)