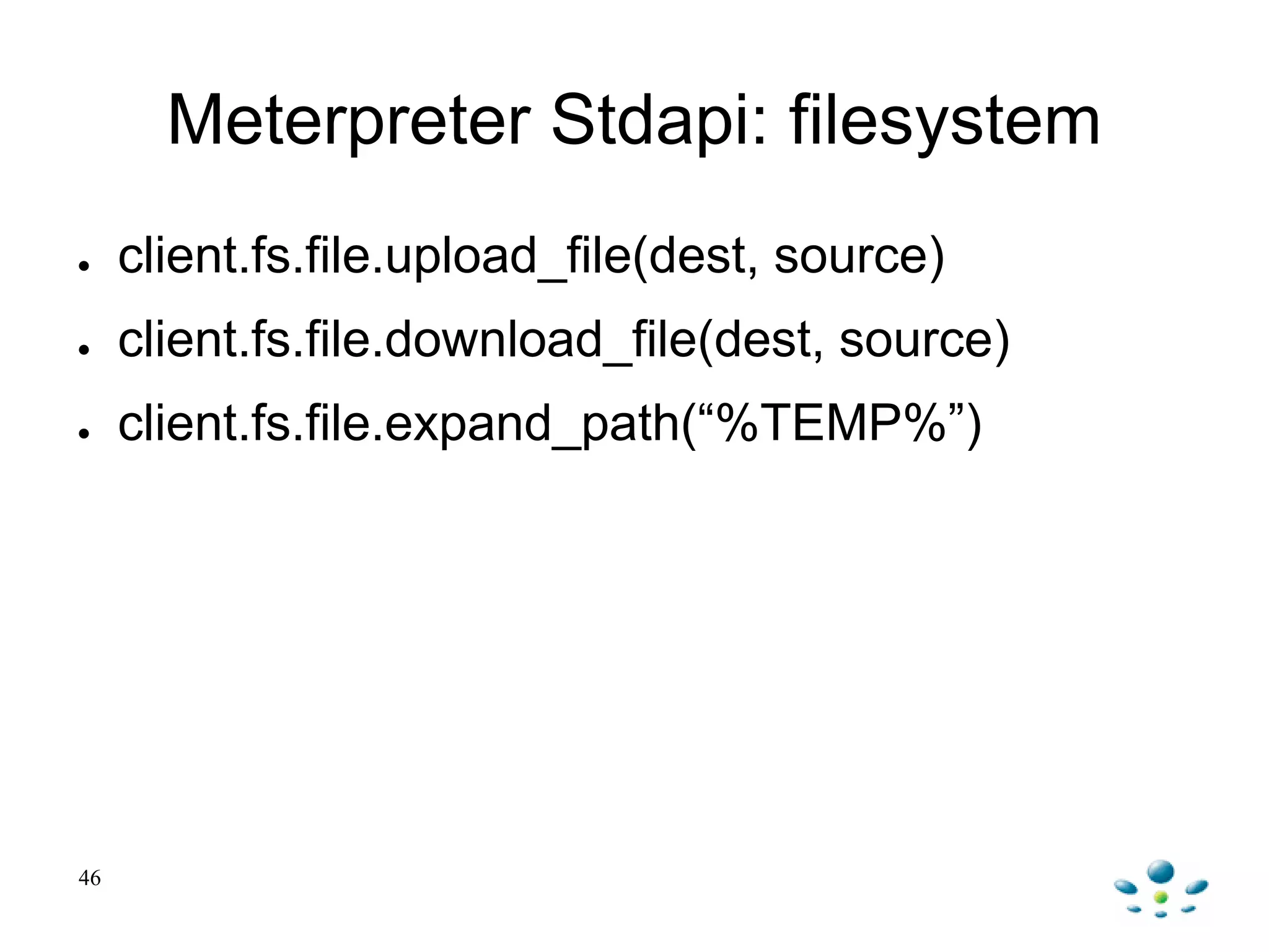
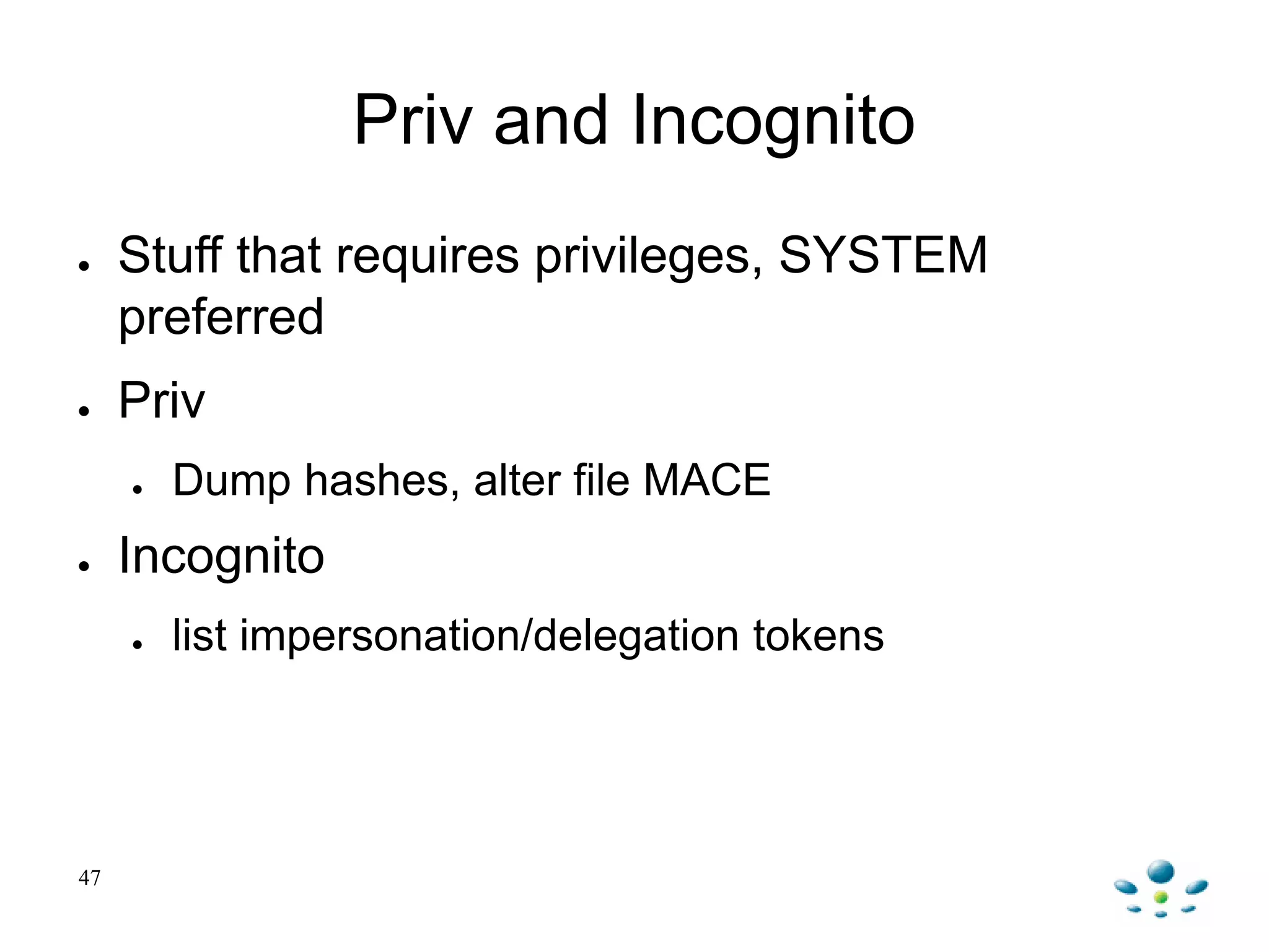
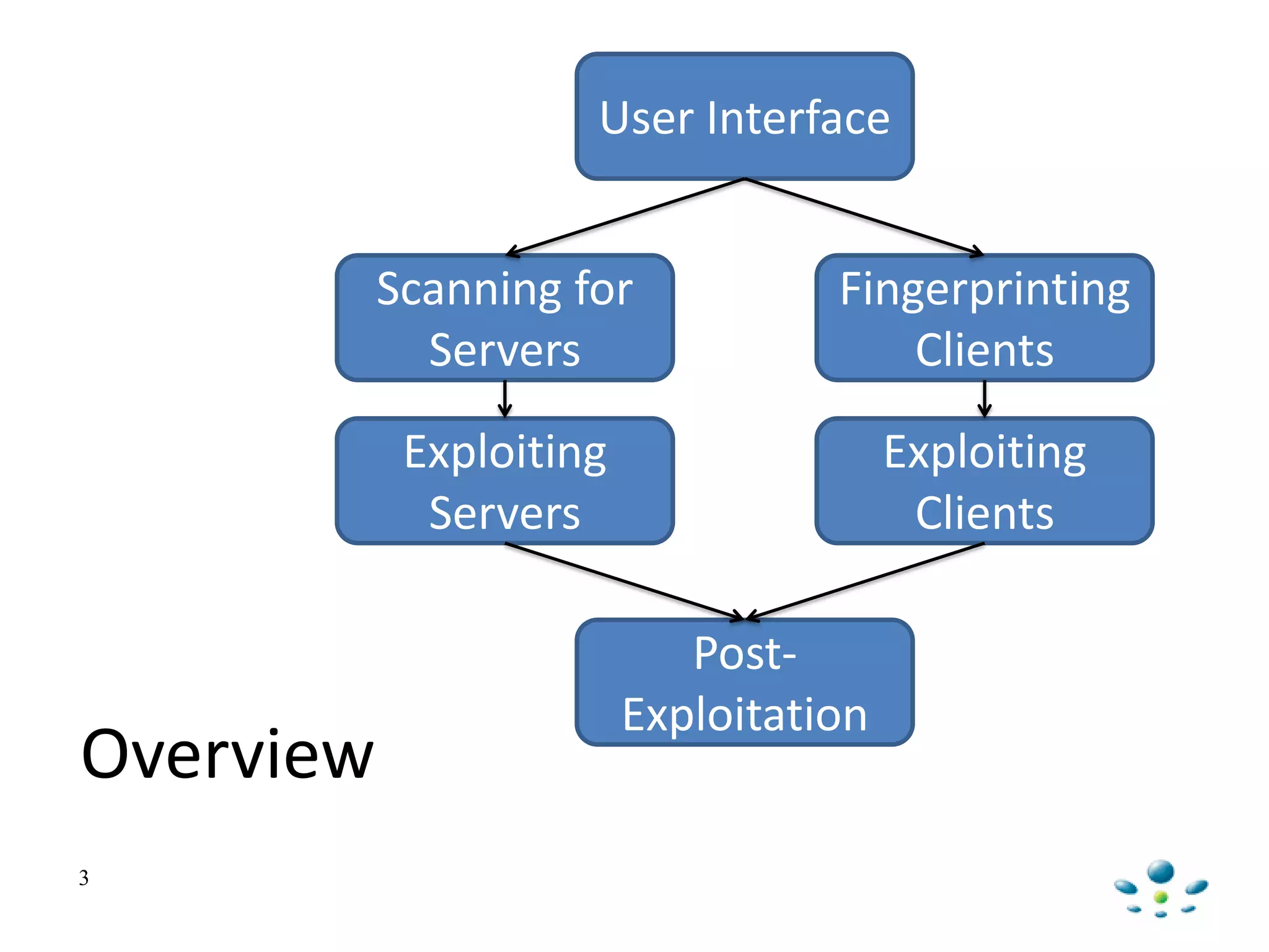
Unmanned Aerial Vehicles can be automated using Metasploit to fingerprint clients, scan for servers, and exploit vulnerabilities. Metasploit provides built-in modules to automate scanning networks using tools like Nmap and Nexpose. Exploits and payloads can then be automatically run on vulnerable servers and clients. Post-exploitation activities can also be automated using Meterpreter scripts and plugins to perform tasks like privilege escalation, packet capture, and maintaining persistence.
























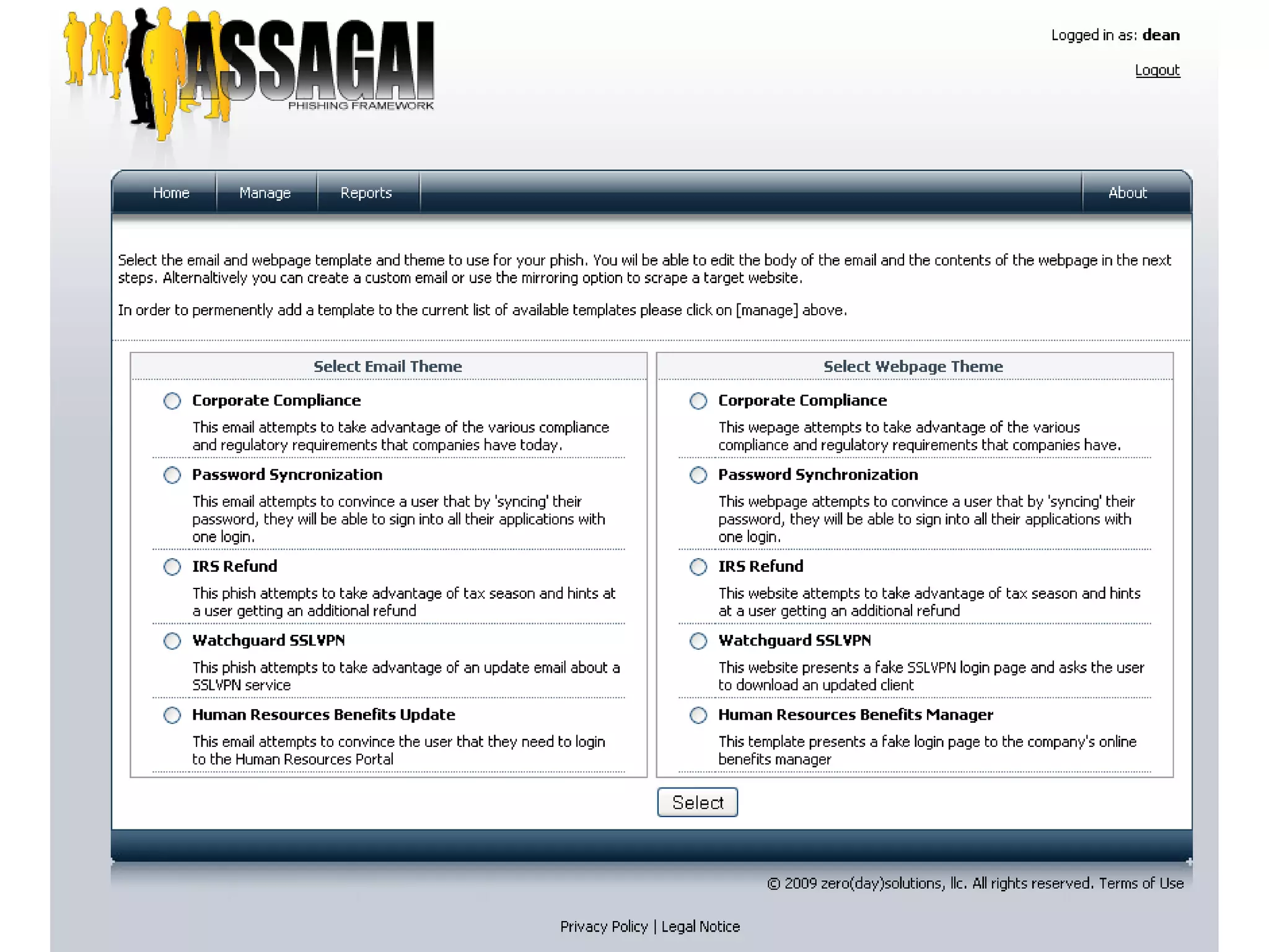
![Browser Autopwn Usage
msf> use auxiliary/server/browser_autopwn
msf (browser_autopwn)> set URIPATH /
msf (browser_autopwn)> set EXCLUDE opera
msf (browser_autopwn)> set MATCH .*
msf (browser_autopwn)> run
[*] Starting exploit modules on host 10.1.1.1...
[*] ---
32](https://image.slidesharecdn.com/blackhat-dc-2010-egypt-uav-slides-130805090449-phpapp02/75/Black-hat-dc-2010-egypt-uav-slides-32-2048.jpg)








![Meterpreter Stdapi: process
● client.sys.process
● Acts like a Hash, where keys are image names and
values are process IDs
● client.sys.process[„explorer.exe‟]
● => 1408
44](https://image.slidesharecdn.com/blackhat-dc-2010-egypt-uav-slides-130805090449-phpapp02/75/Black-hat-dc-2010-egypt-uav-slides-44-2048.jpg)