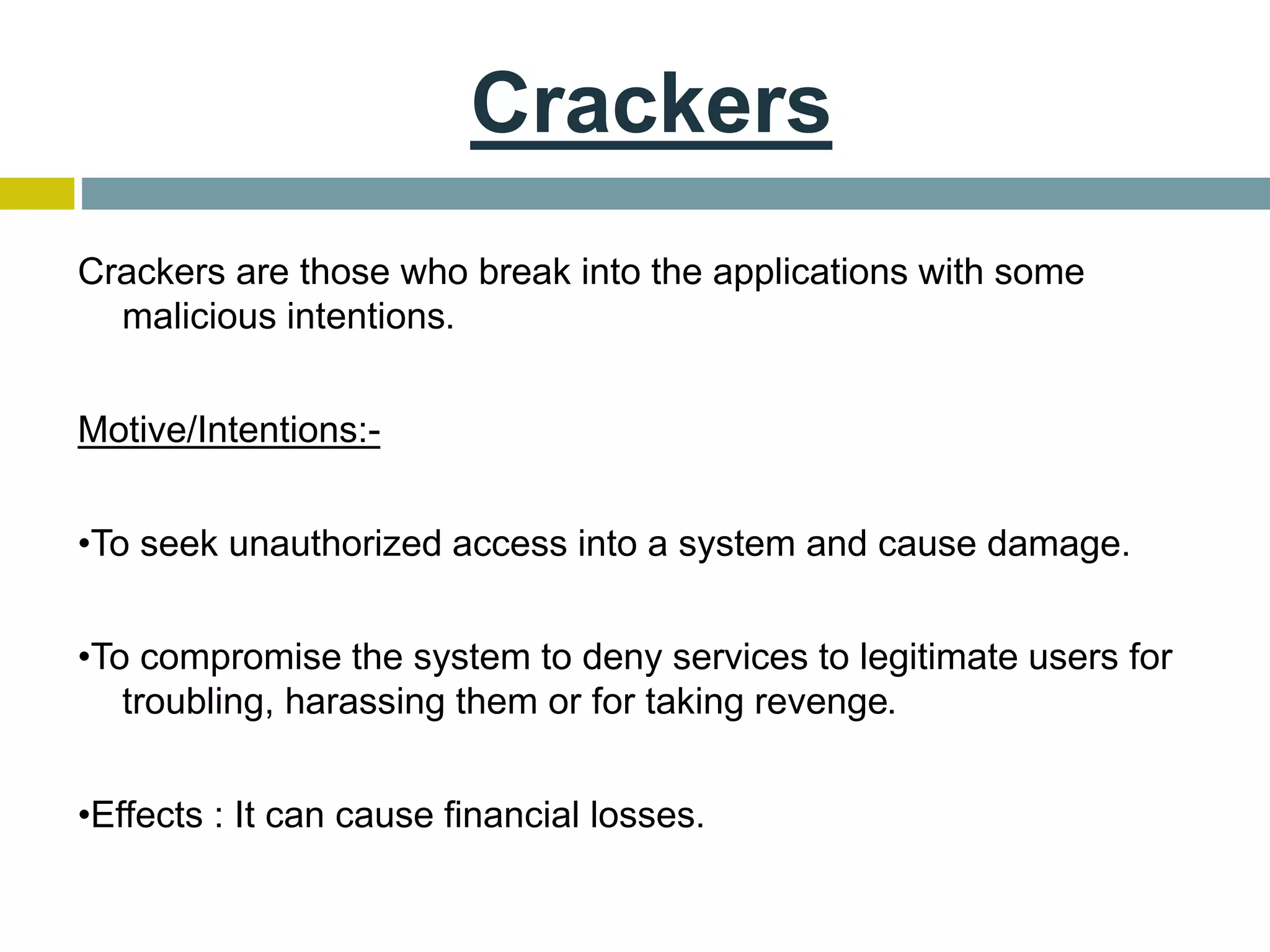
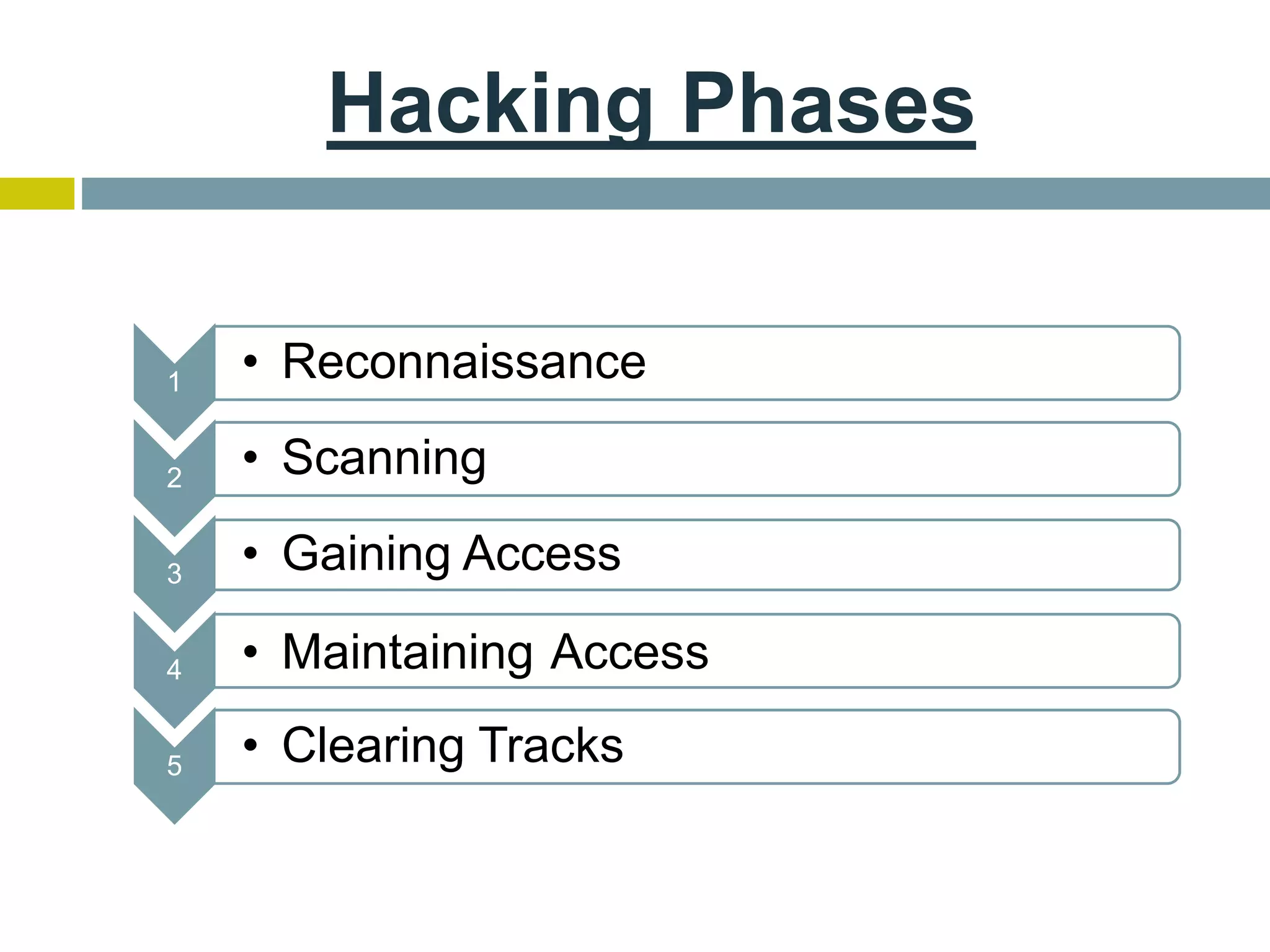
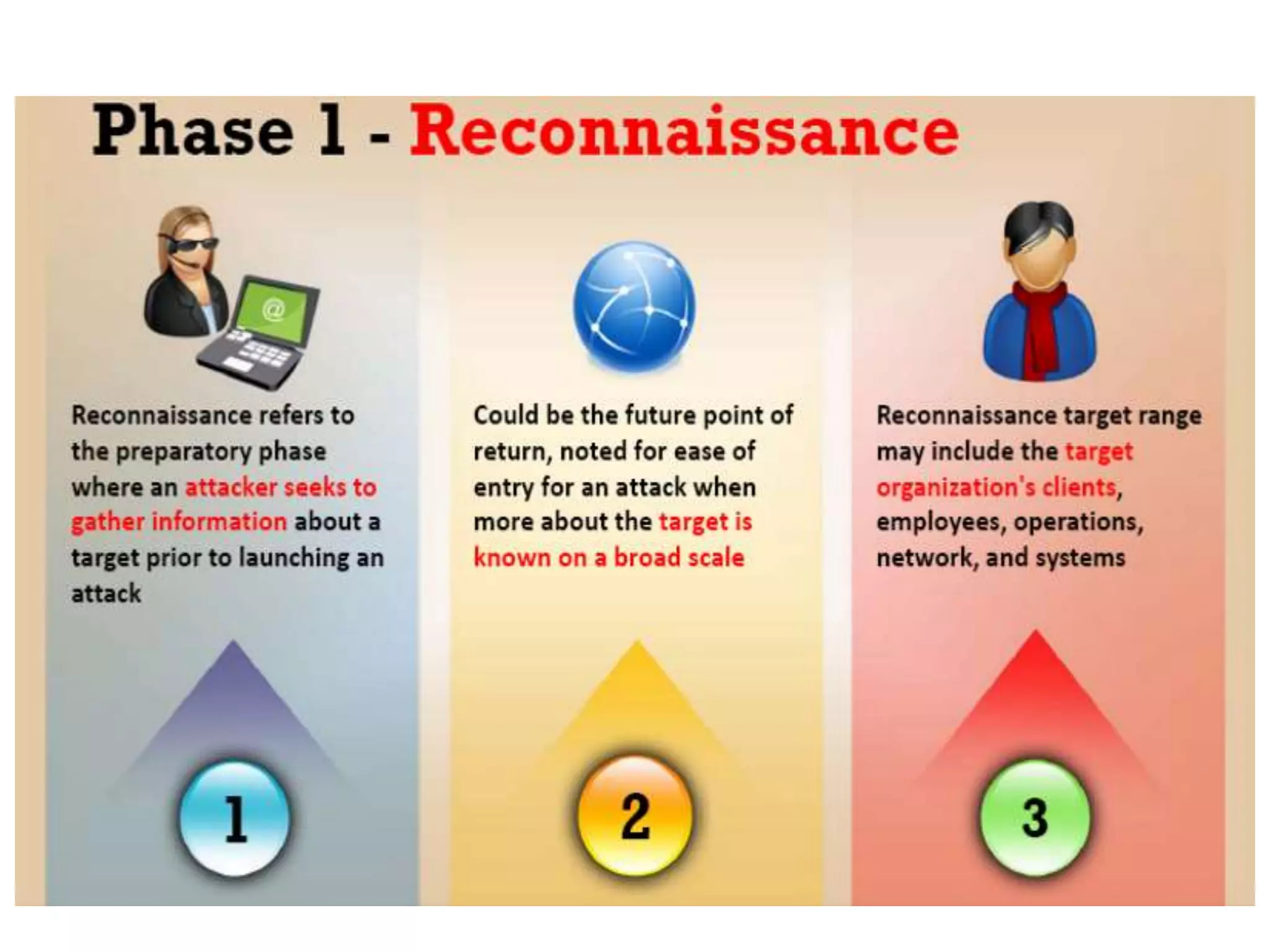
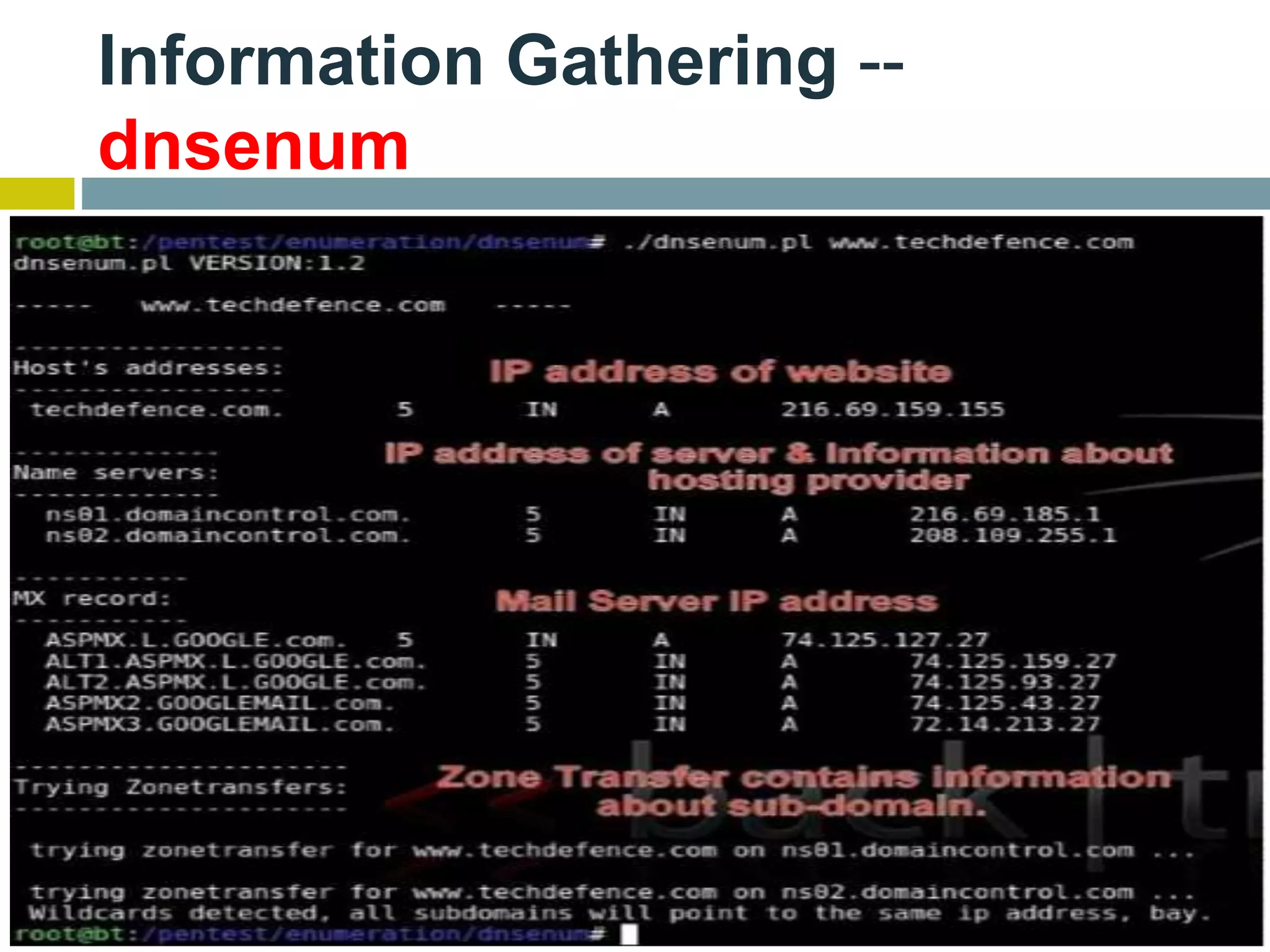
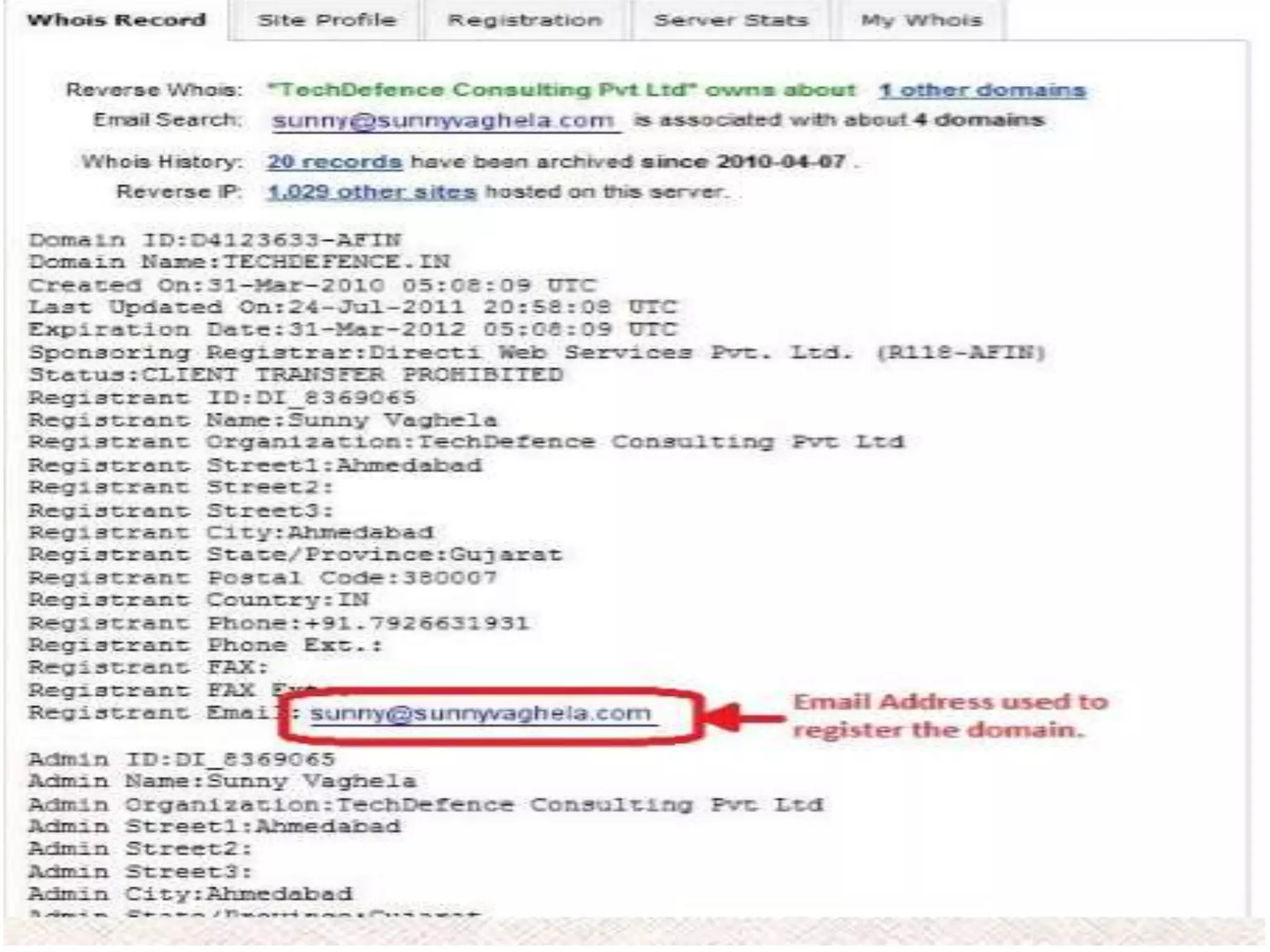
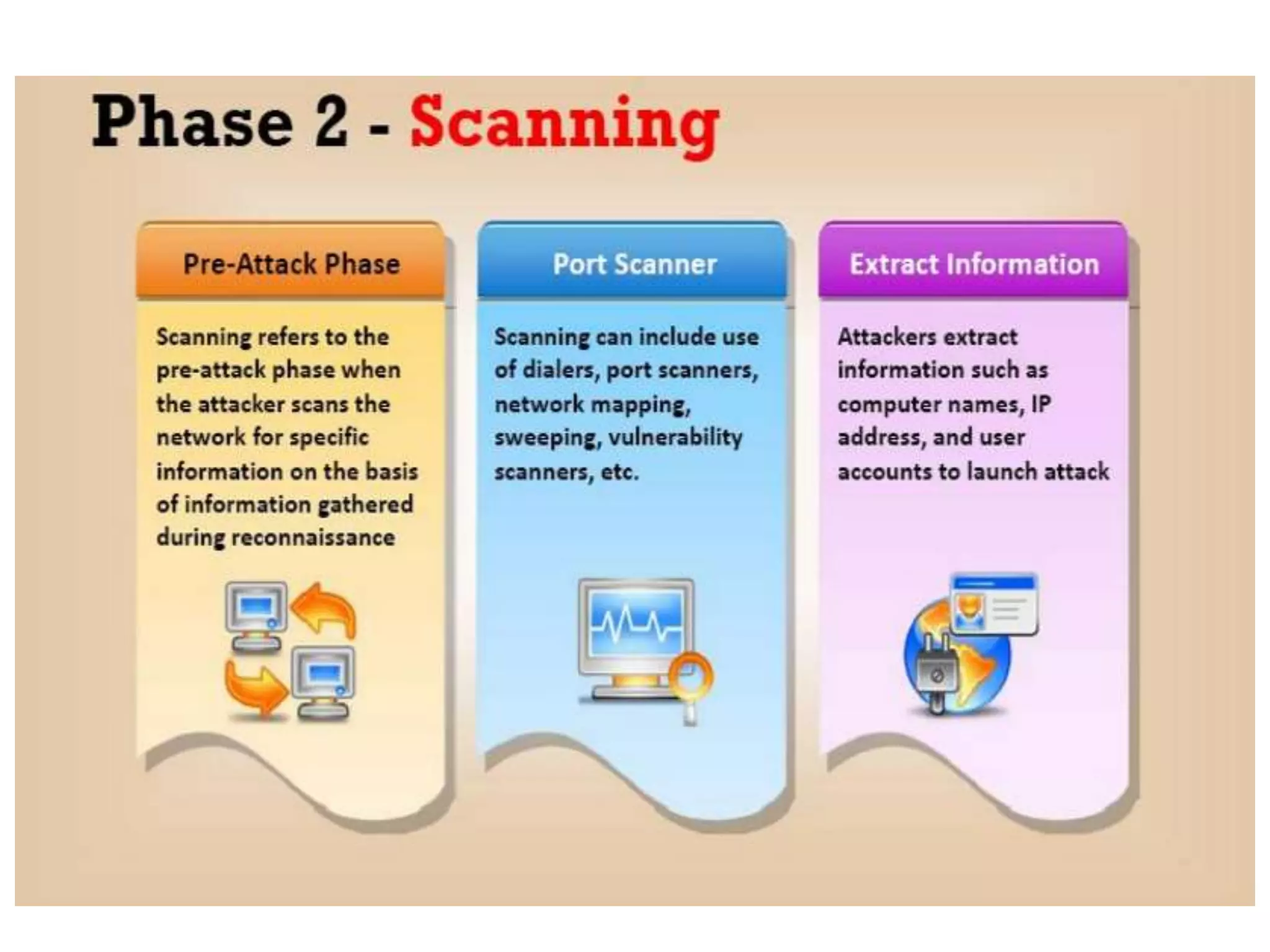
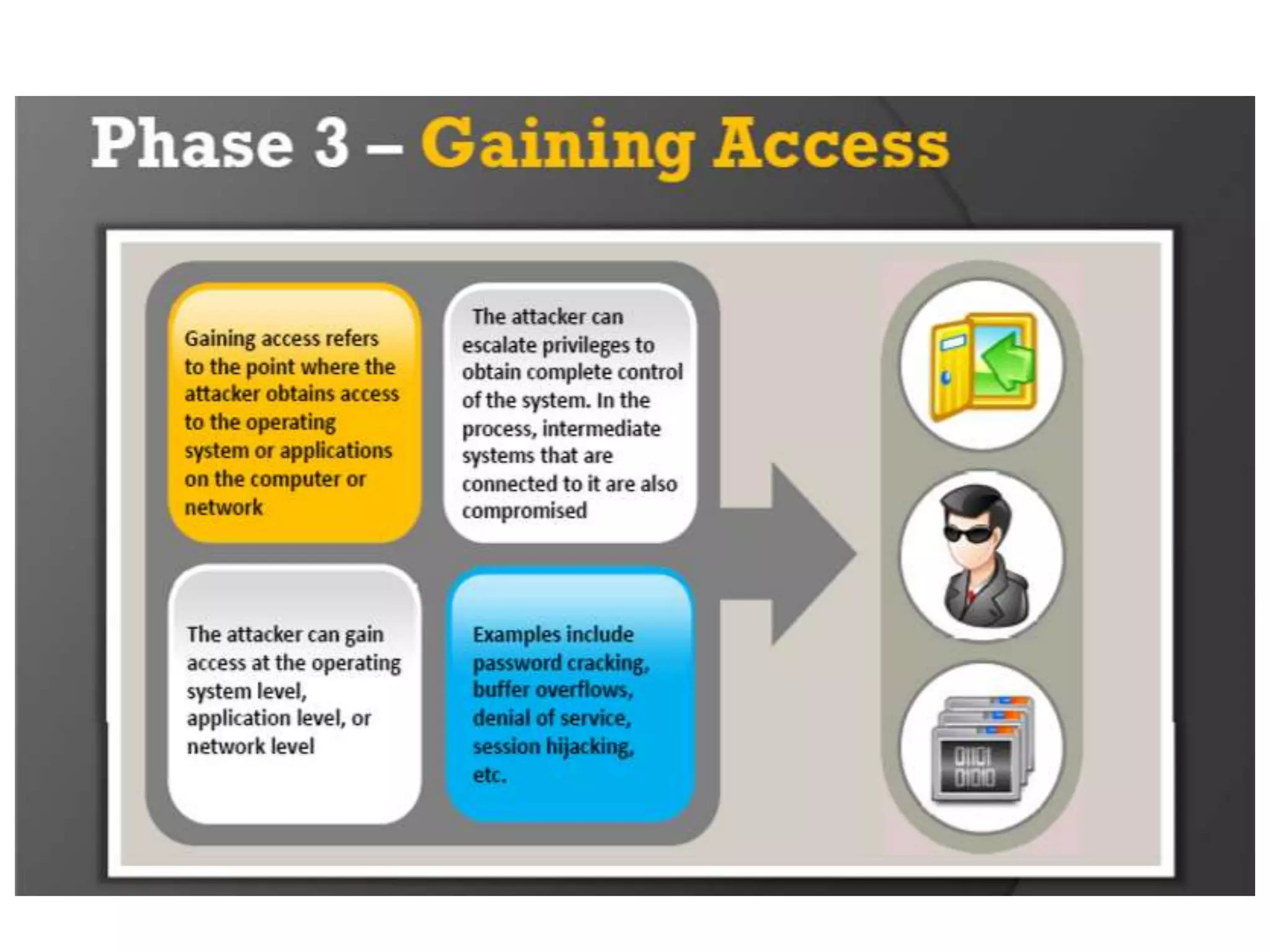
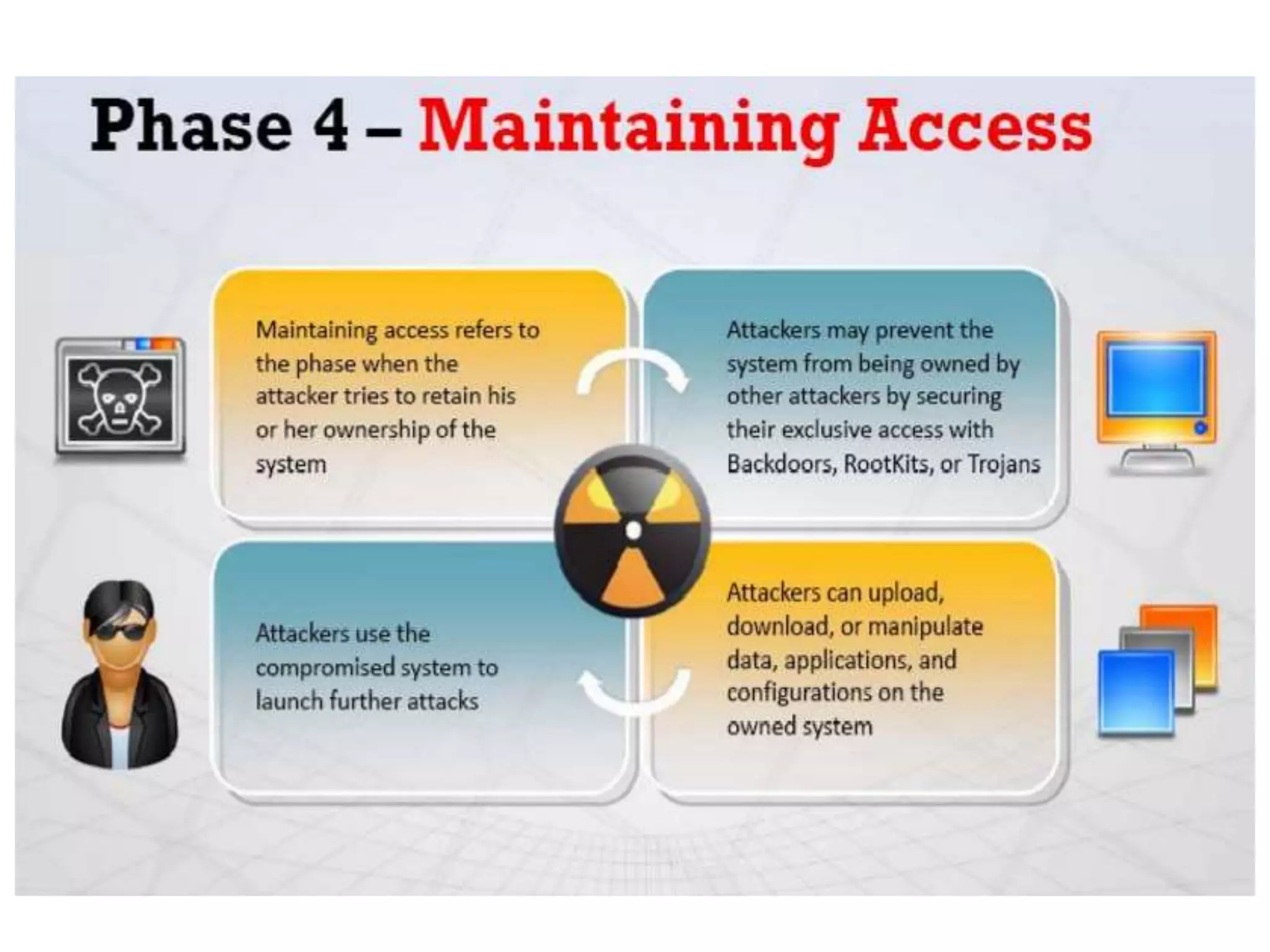
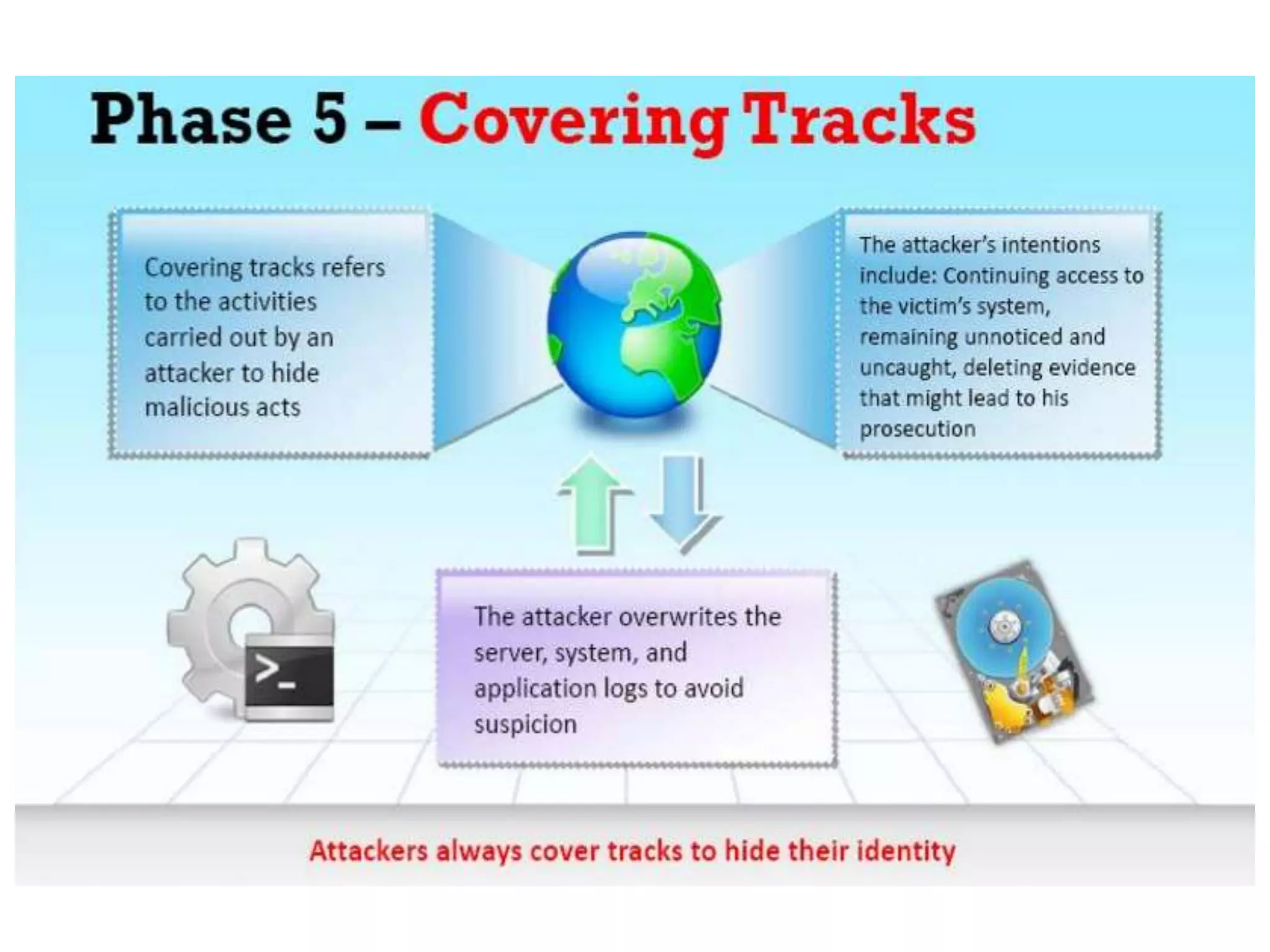
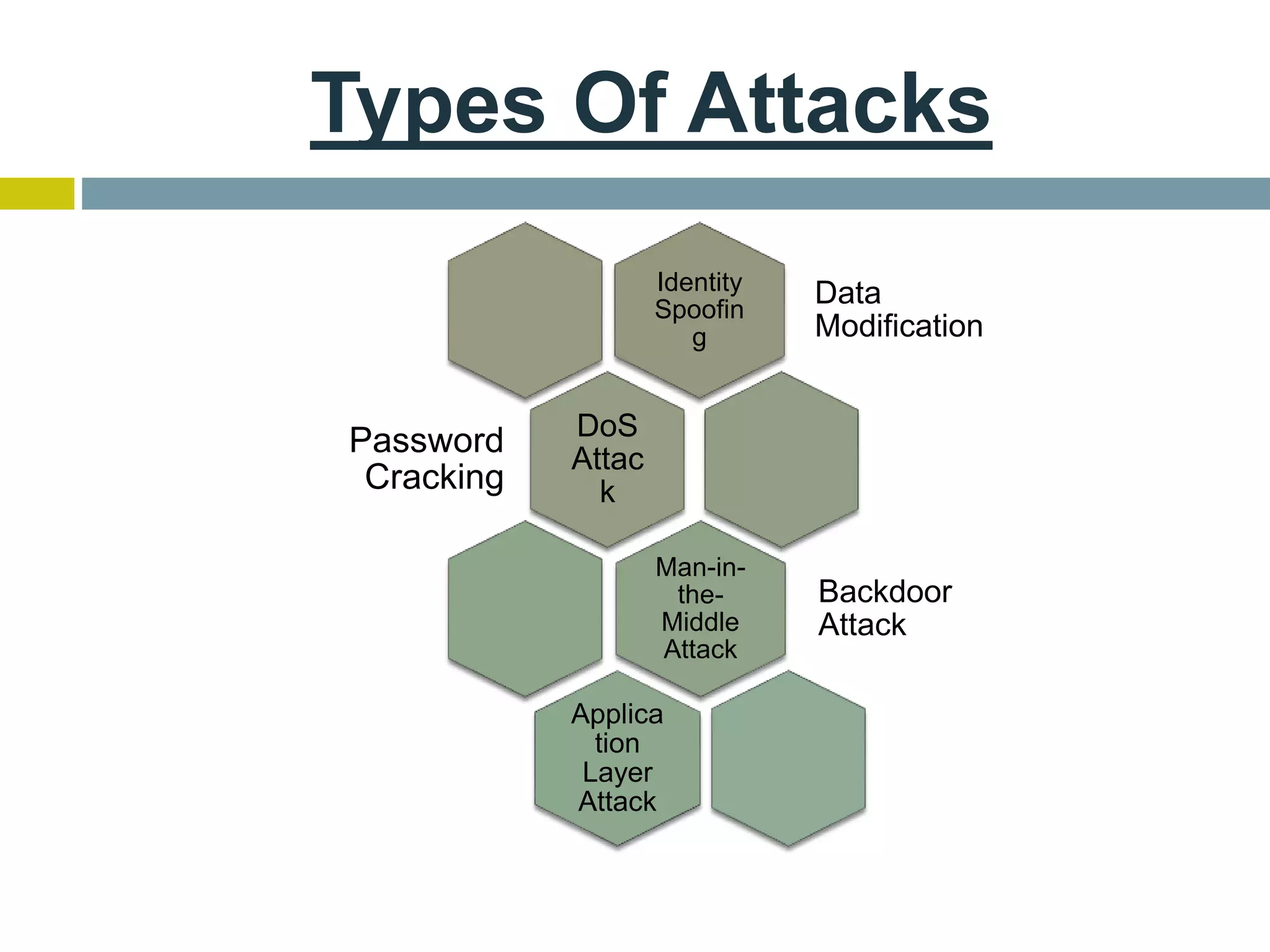
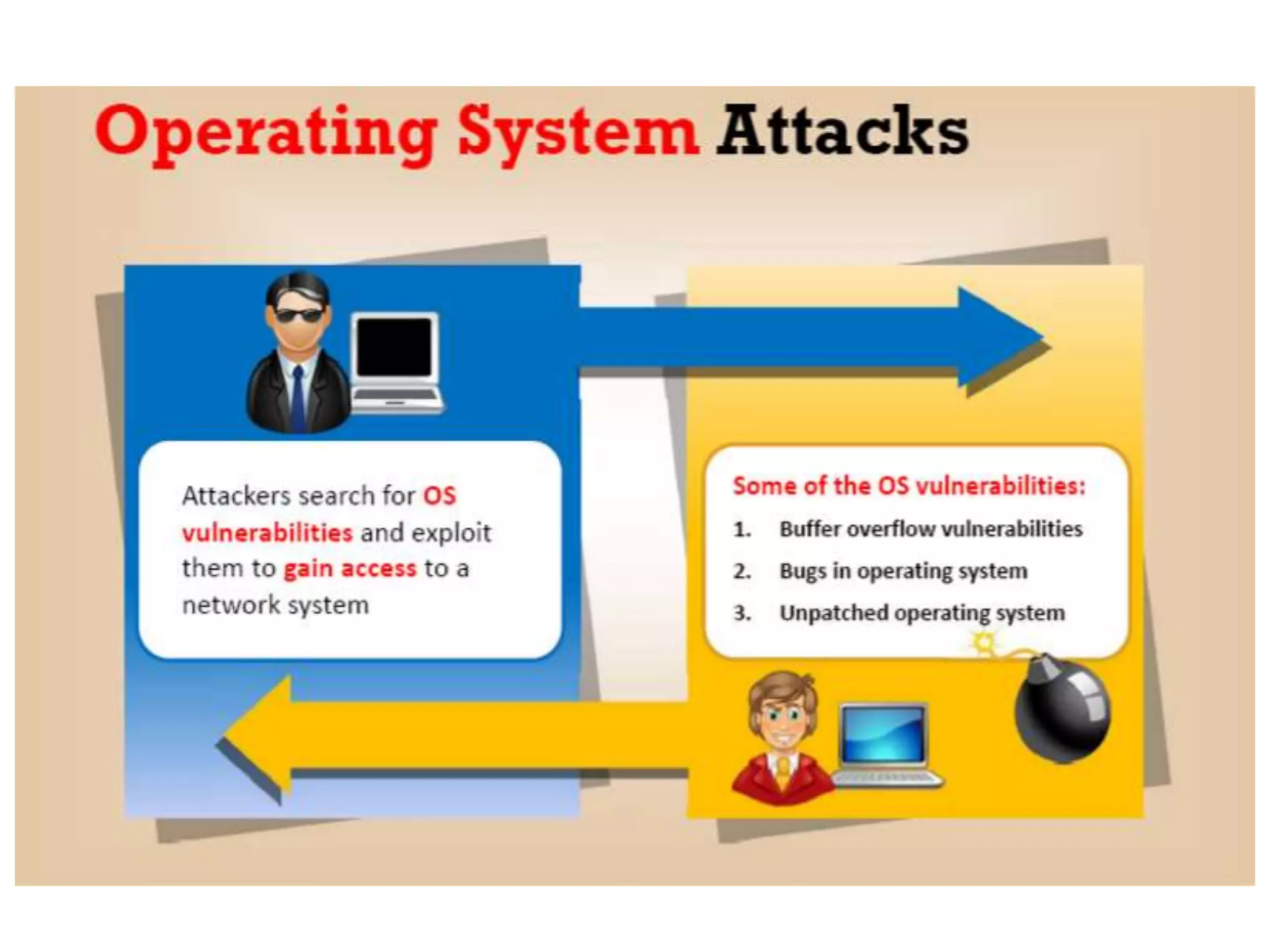
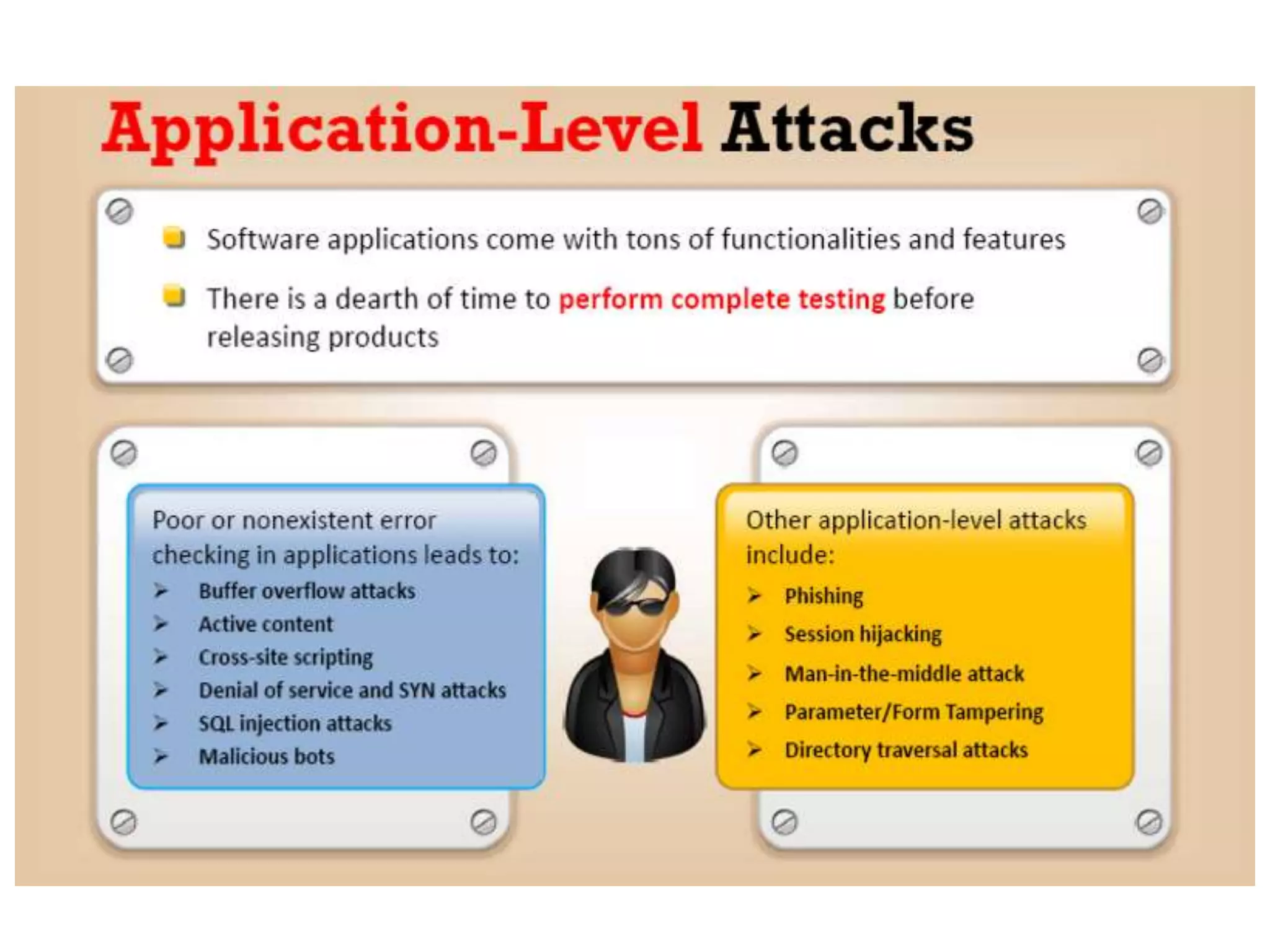
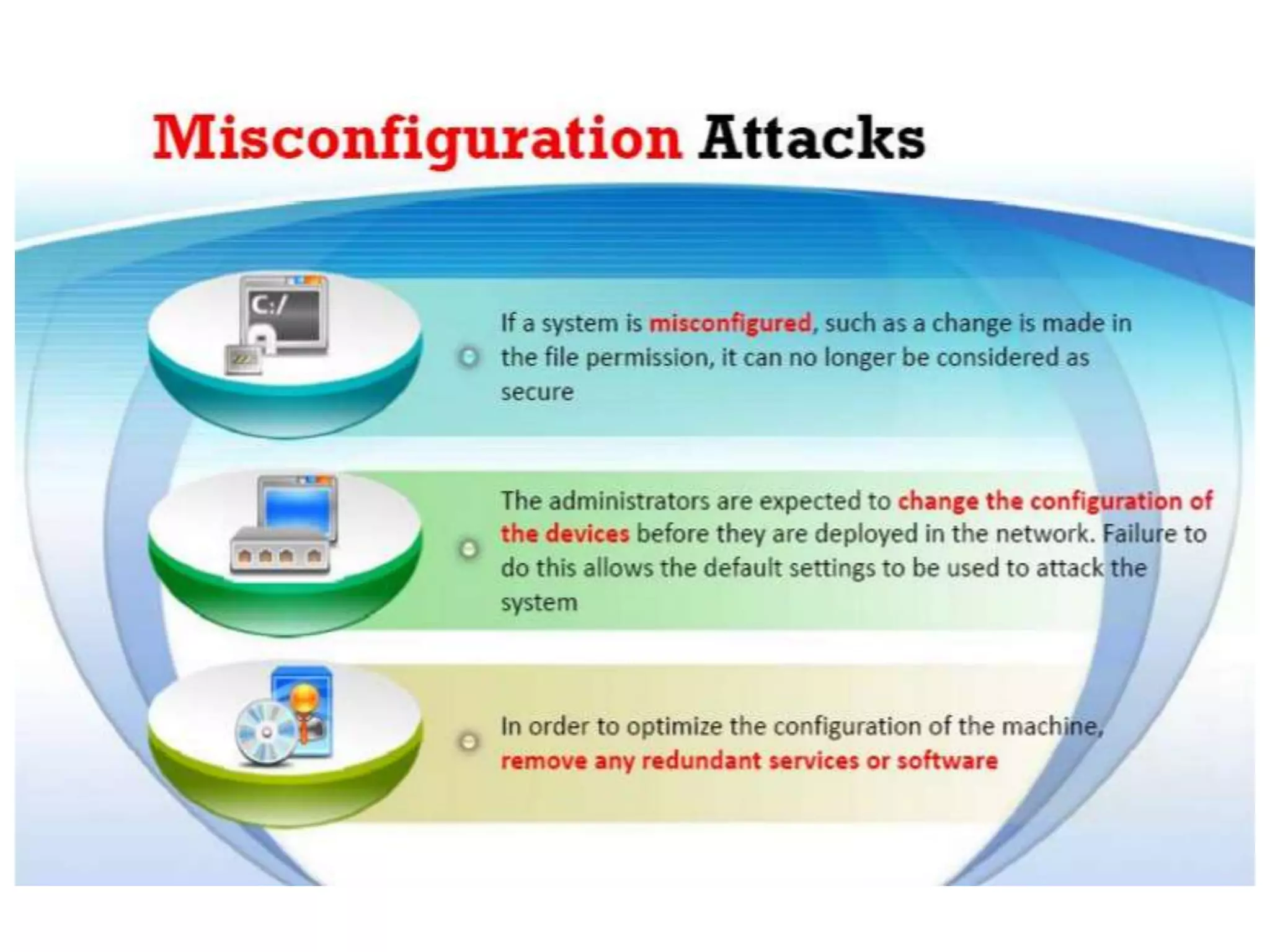
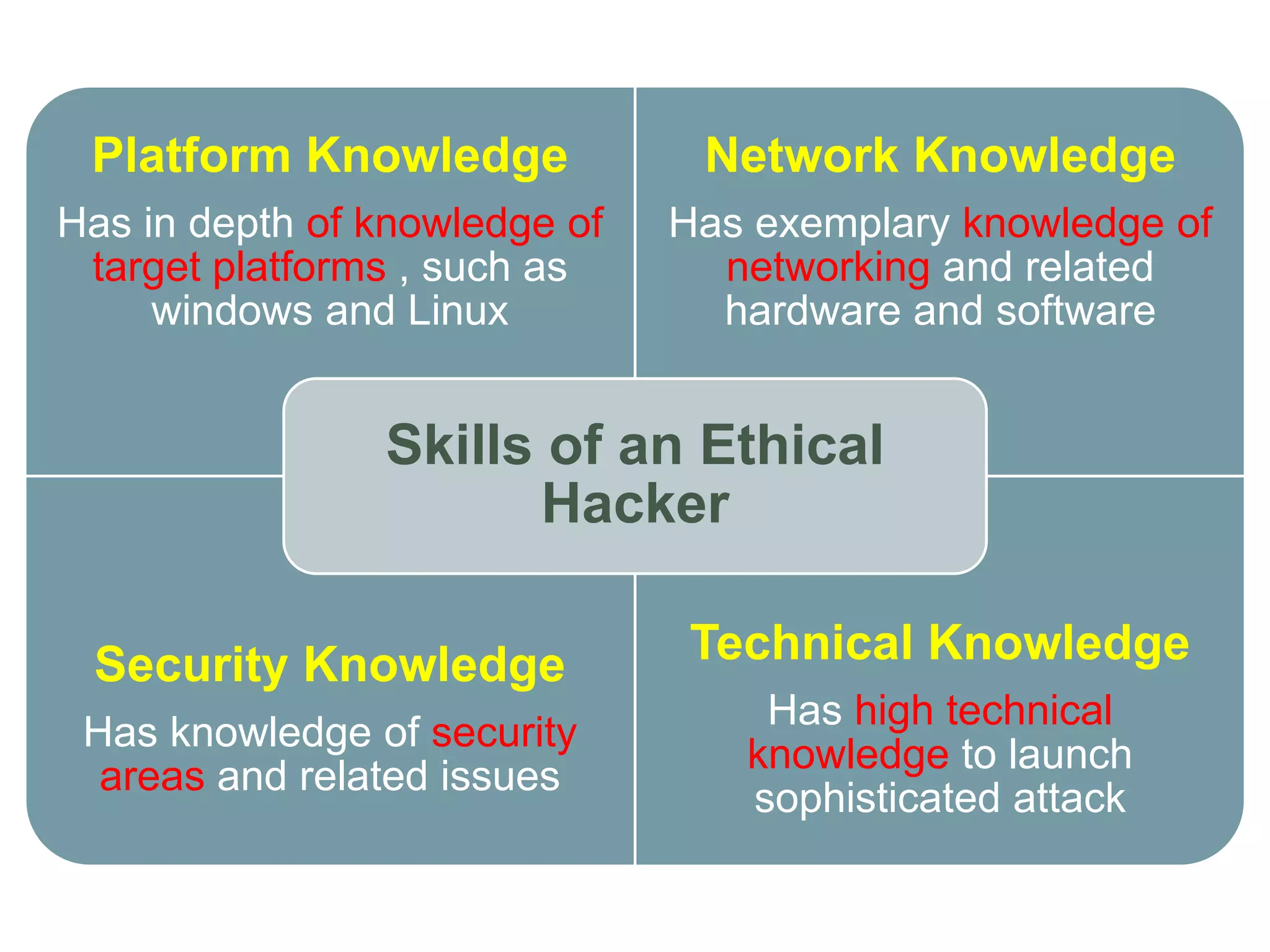
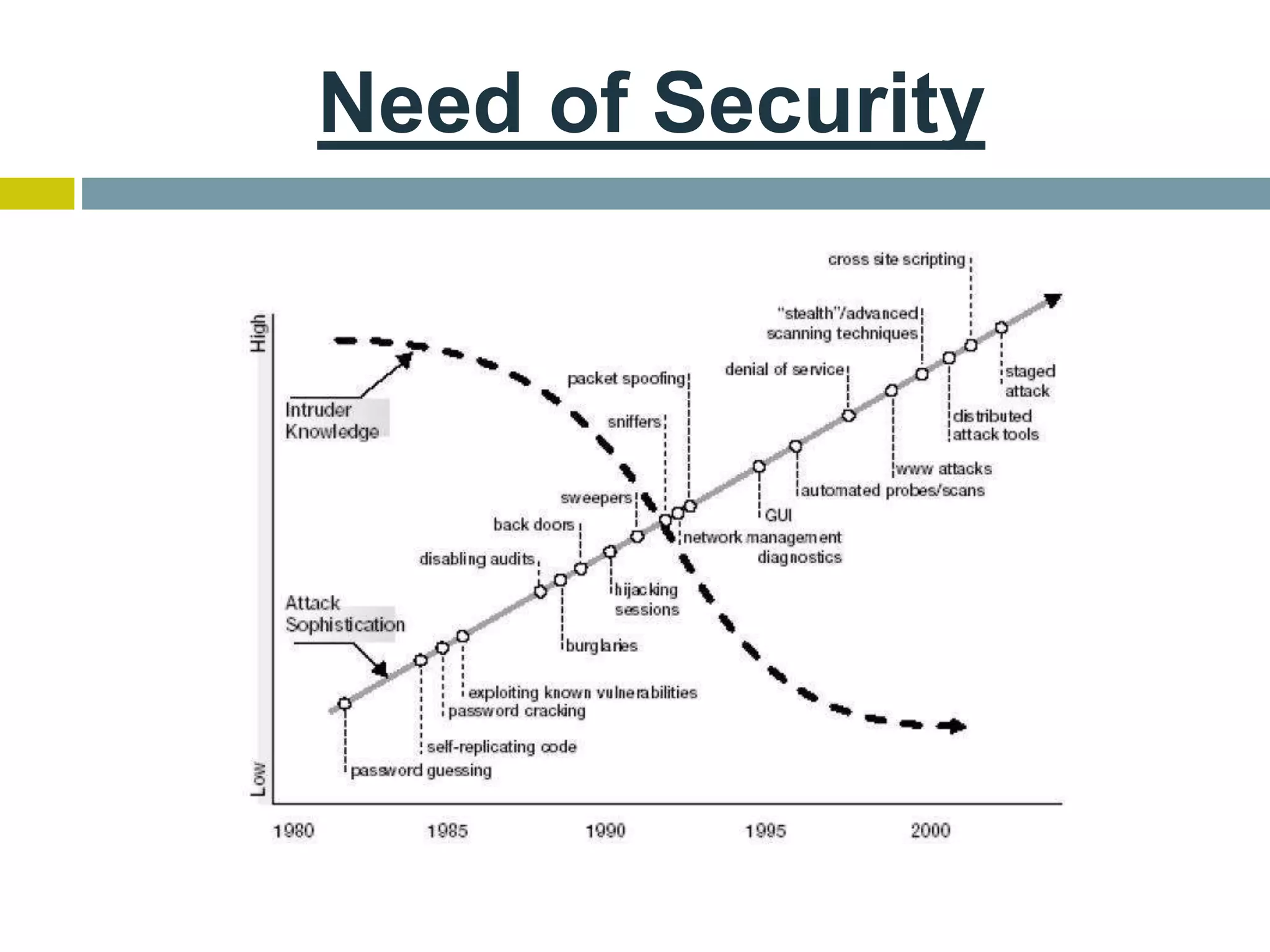
This document provides an overview of ethical hacking. It defines hacking and different types of hackers such as white hat, black hat, and grey hat hackers. It also discusses the phases of hacking attacks and types of attacks like DoS attacks, password cracking, and man-in-the-middle attacks. Ethical hackers are hired by organizations to test their security systems and find vulnerabilities. They need to have in-depth knowledge of platforms, networking, security issues, and technical skills to perform sophisticated attacks. With increasing technology use, there is a greater need for security to protect companies, governments, and individuals from security breaches.