1. The document introduces the topic of ethical hacking by defining hacking and explaining its origins in computer culture at MIT in the 1960s, where hackers were students who pursued recreational activities rather than studying.
2. It describes the three main types of hackers: white hat hackers who find security vulnerabilities ethically, black hat hackers who do so illegally and destructively, and grey hat hackers who exhibit traits of both.
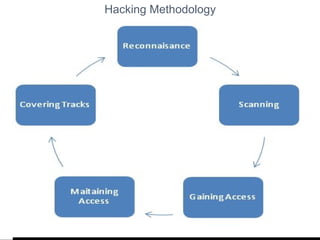
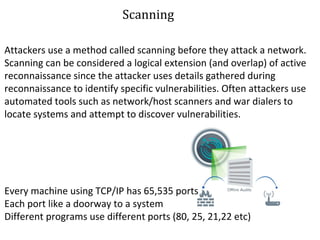
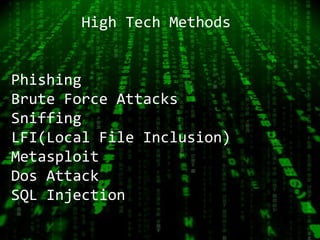
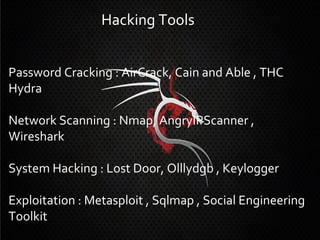
3. The document outlines the typical hacking methodology of reconnaissance, scanning, gaining access, maintaining access, and covering tracks, and provides examples of common low-tech and high-tech hacking techniques.