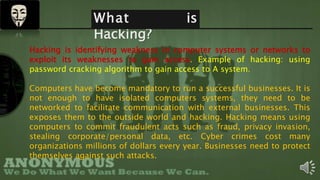
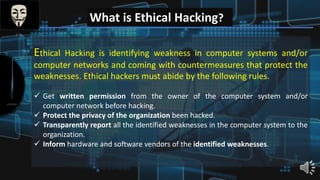
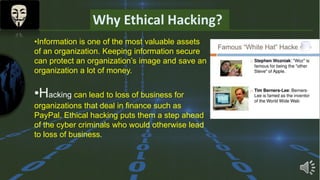
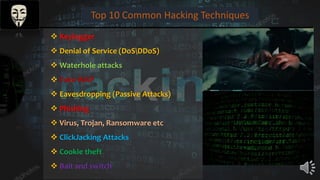
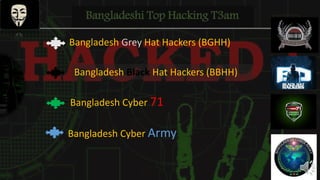
Shawon Raffi is presenting on the topic of hacking. He explains that hacking has negative connotations but can actually be used for positive purposes like security testing and finding vulnerabilities. There are different types of hackers, including black hat hackers who perform criminal acts and white hat hackers who work in cybersecurity. The presentation then covers the history of hacking, definitions, famous hackers, countries with many hackers, and tips for protecting against hackers. It aims to provide an overview of hacking and clear up misconceptions, while emphasizing the importance of ethical hacking for security.