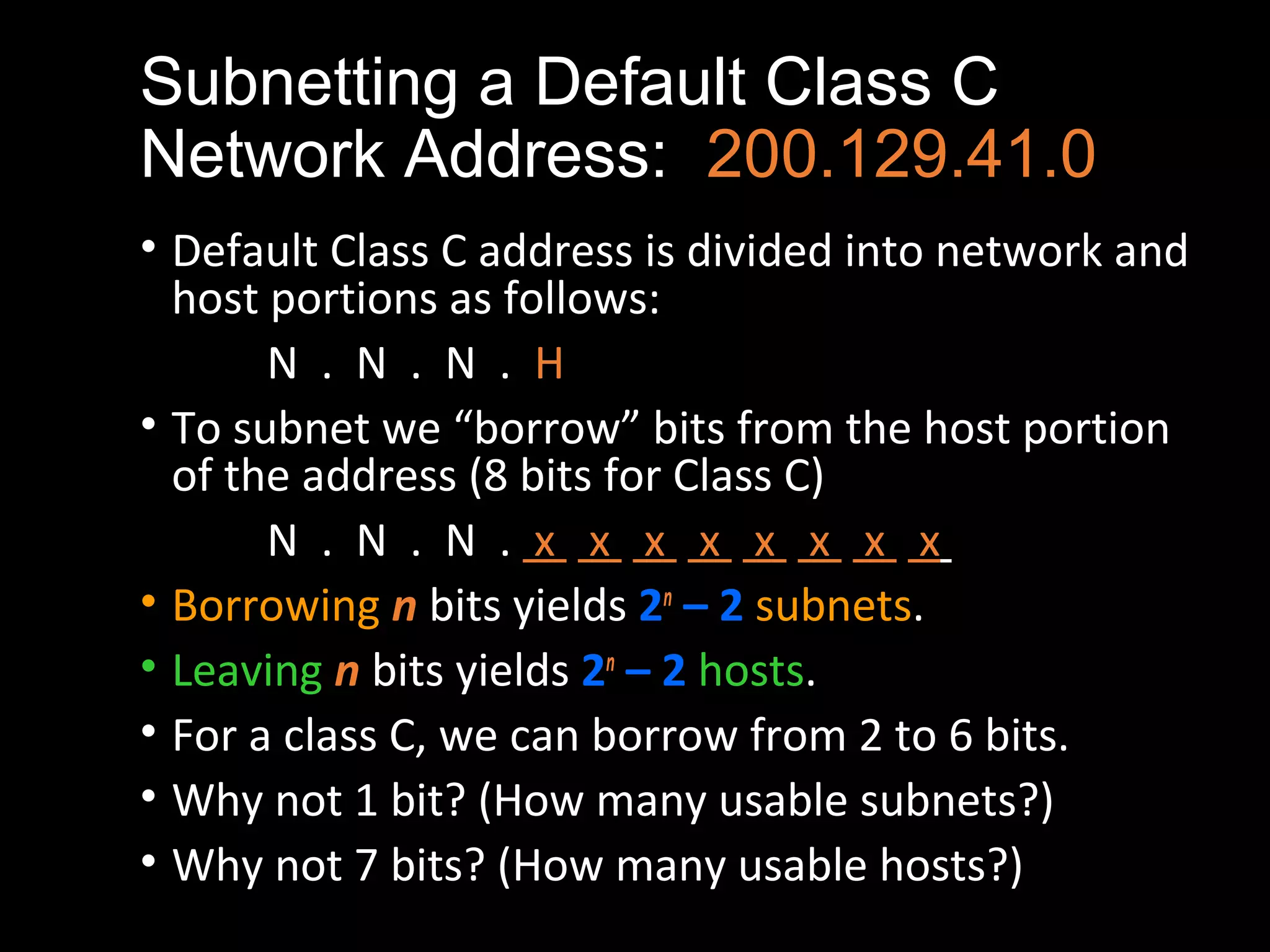
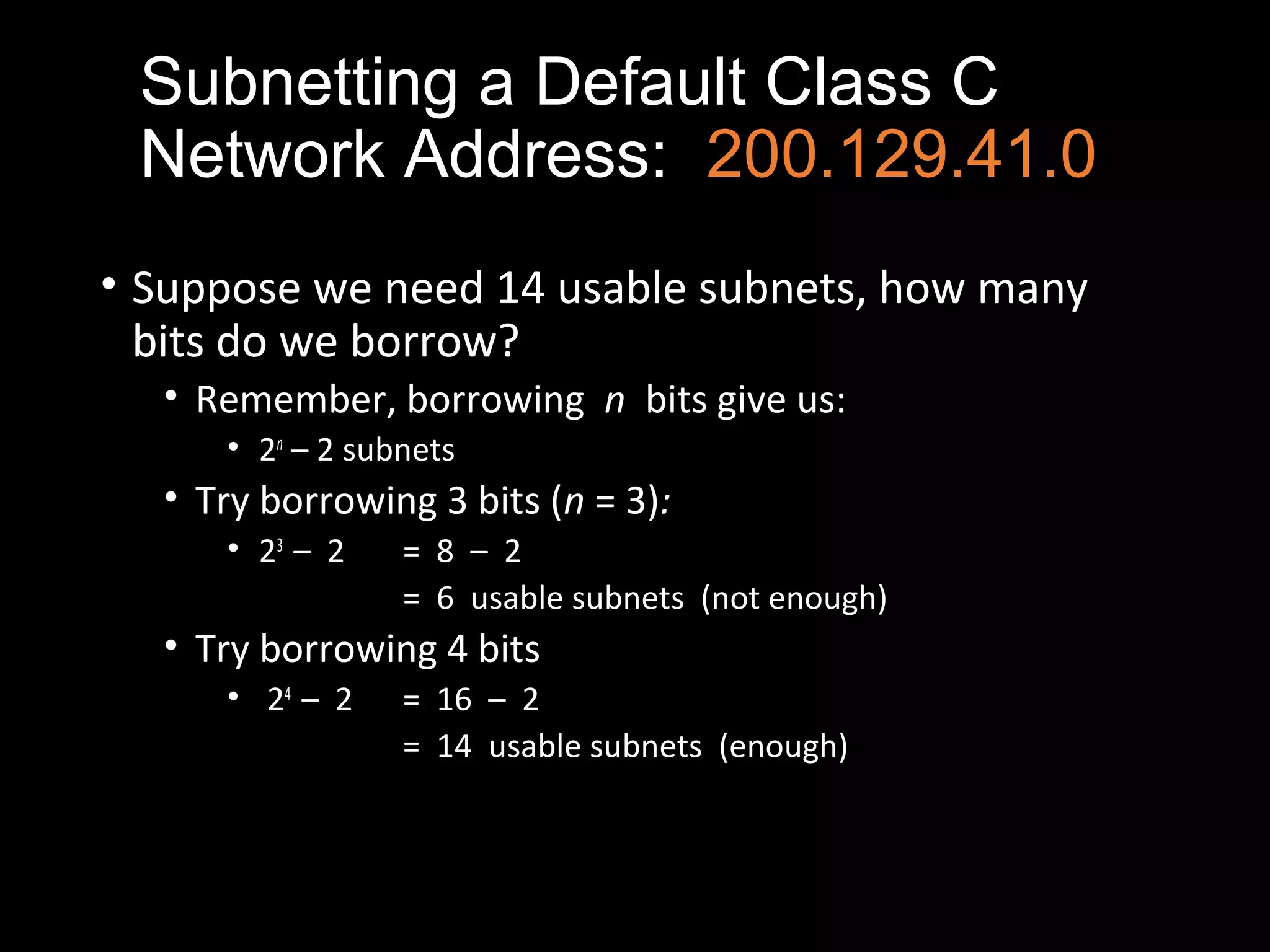
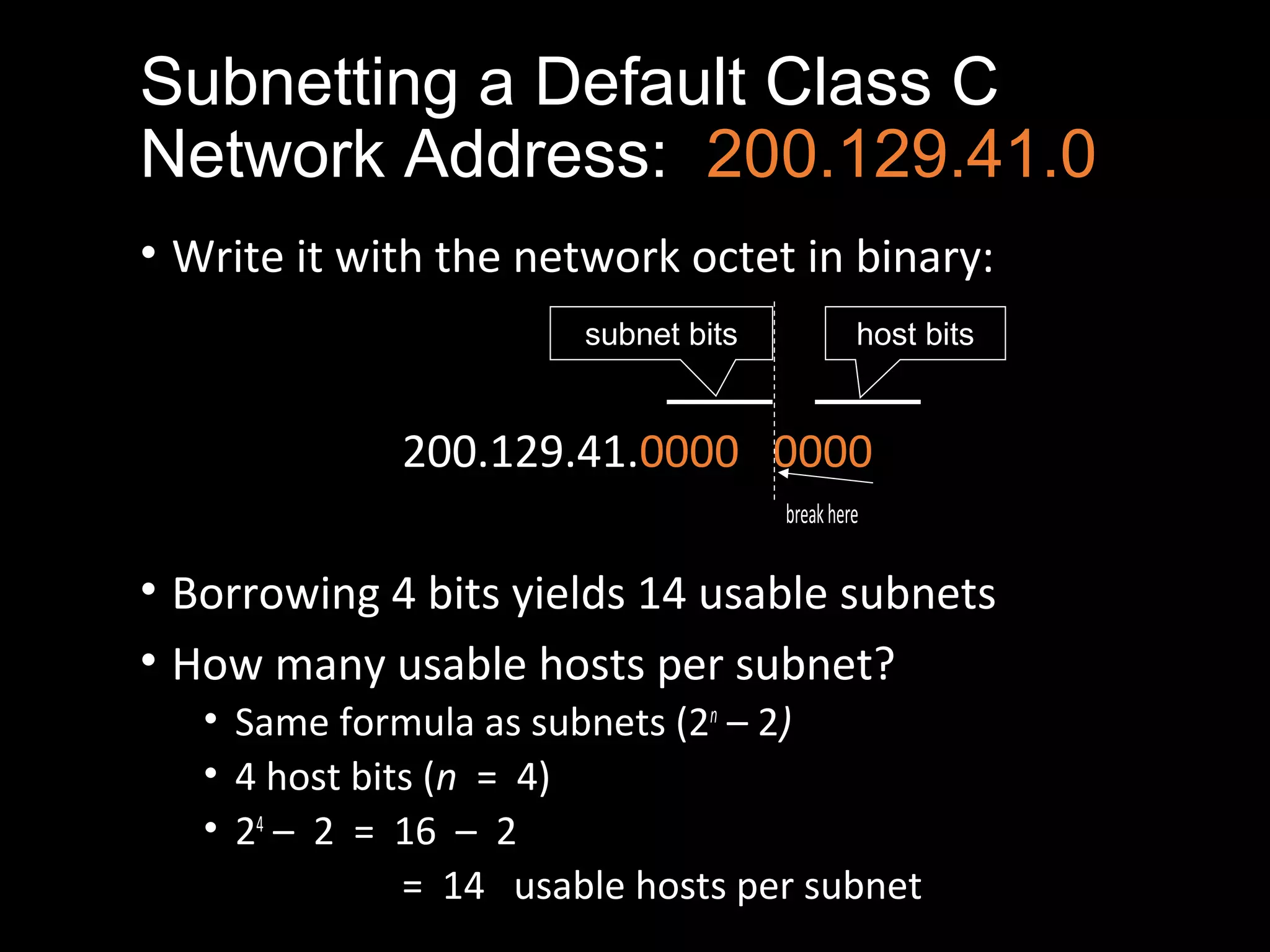
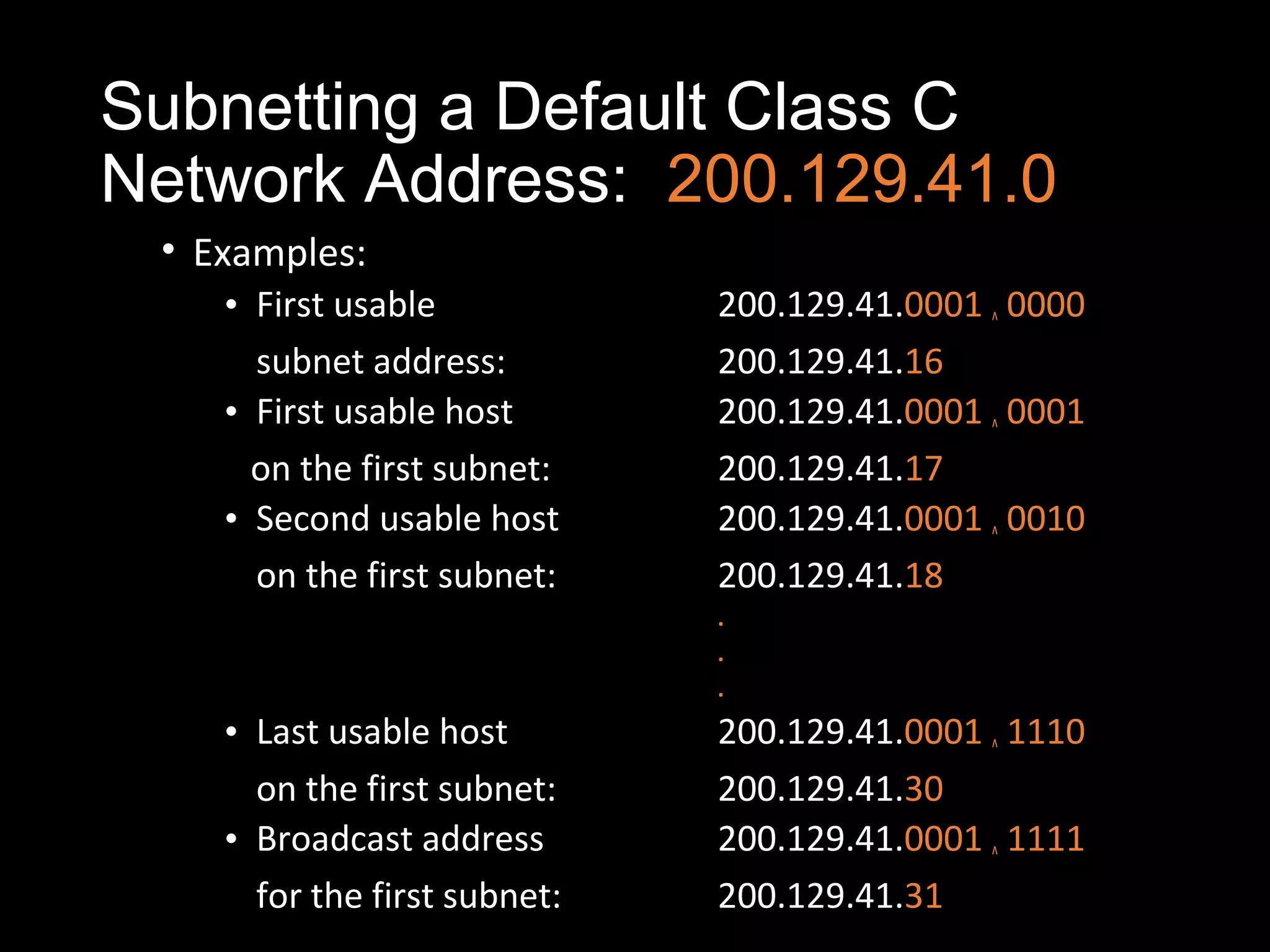
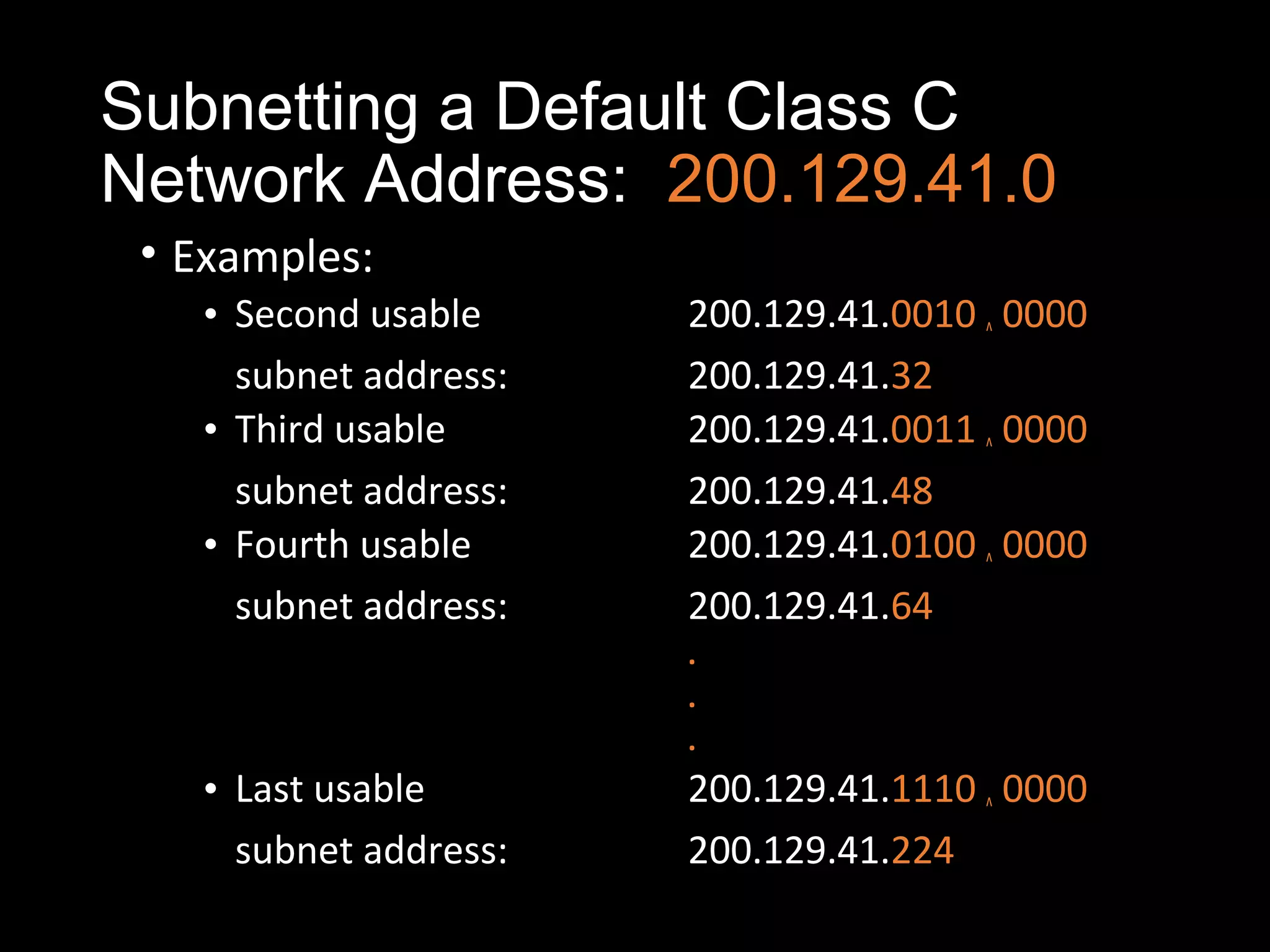
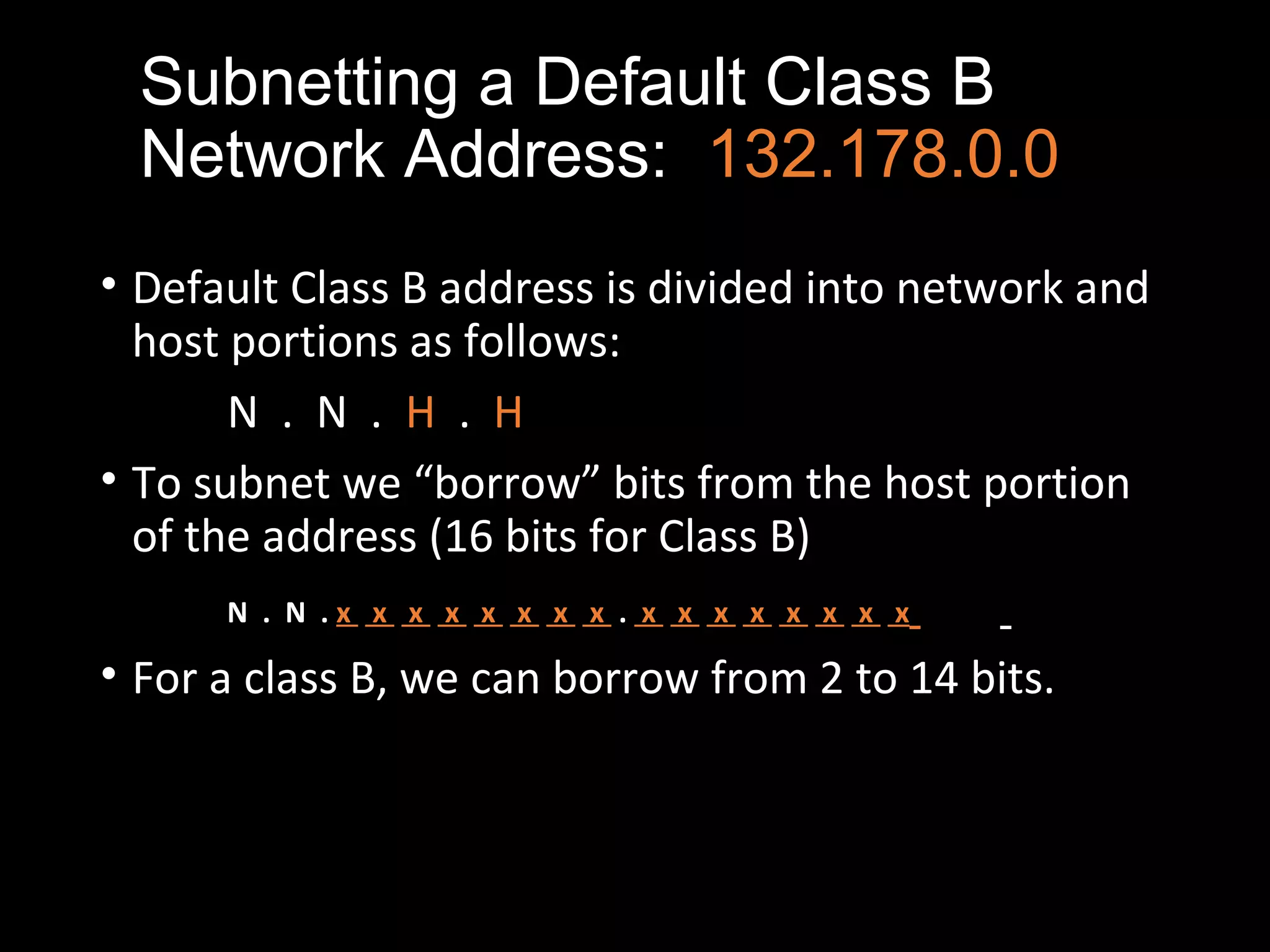
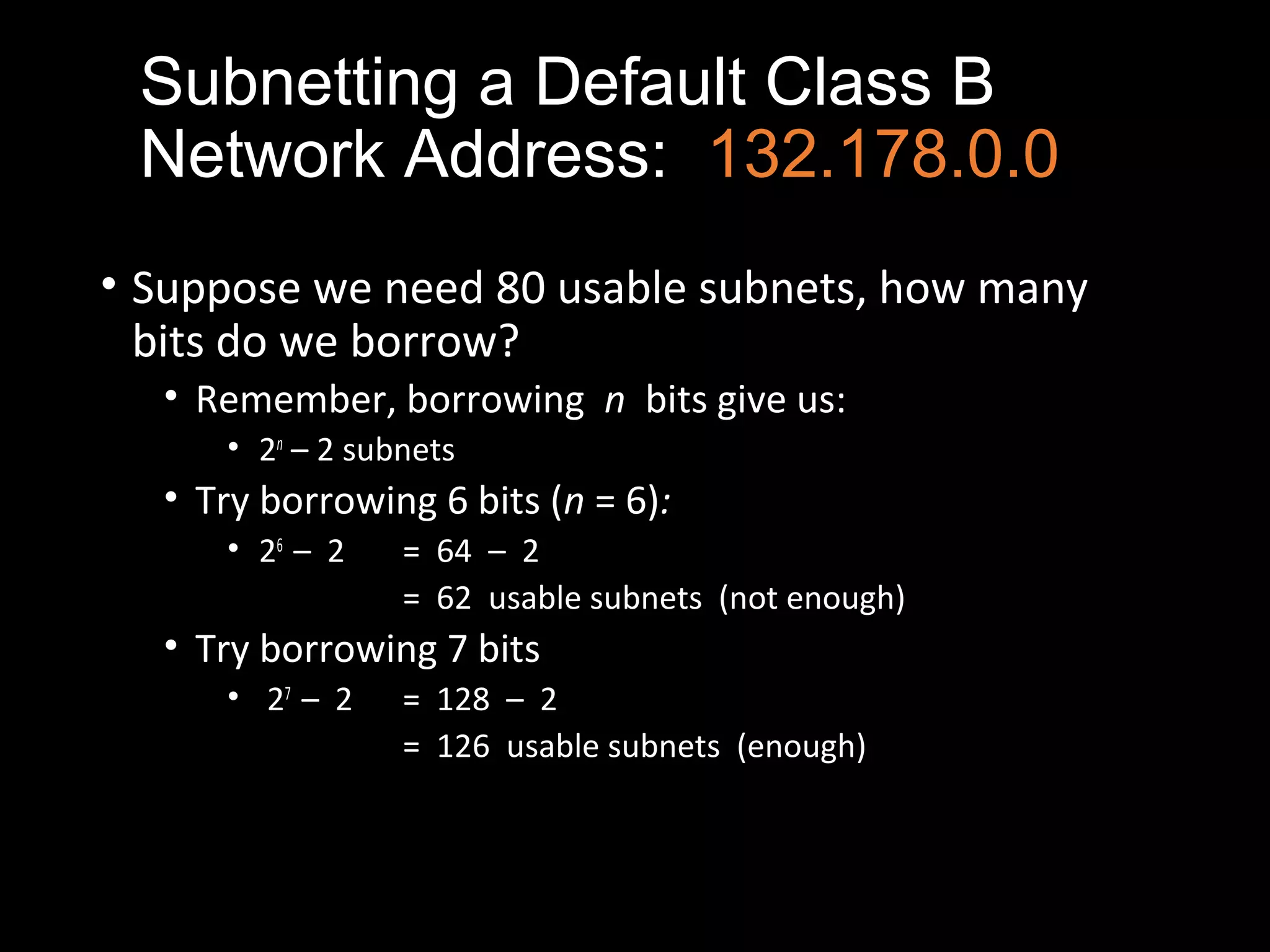
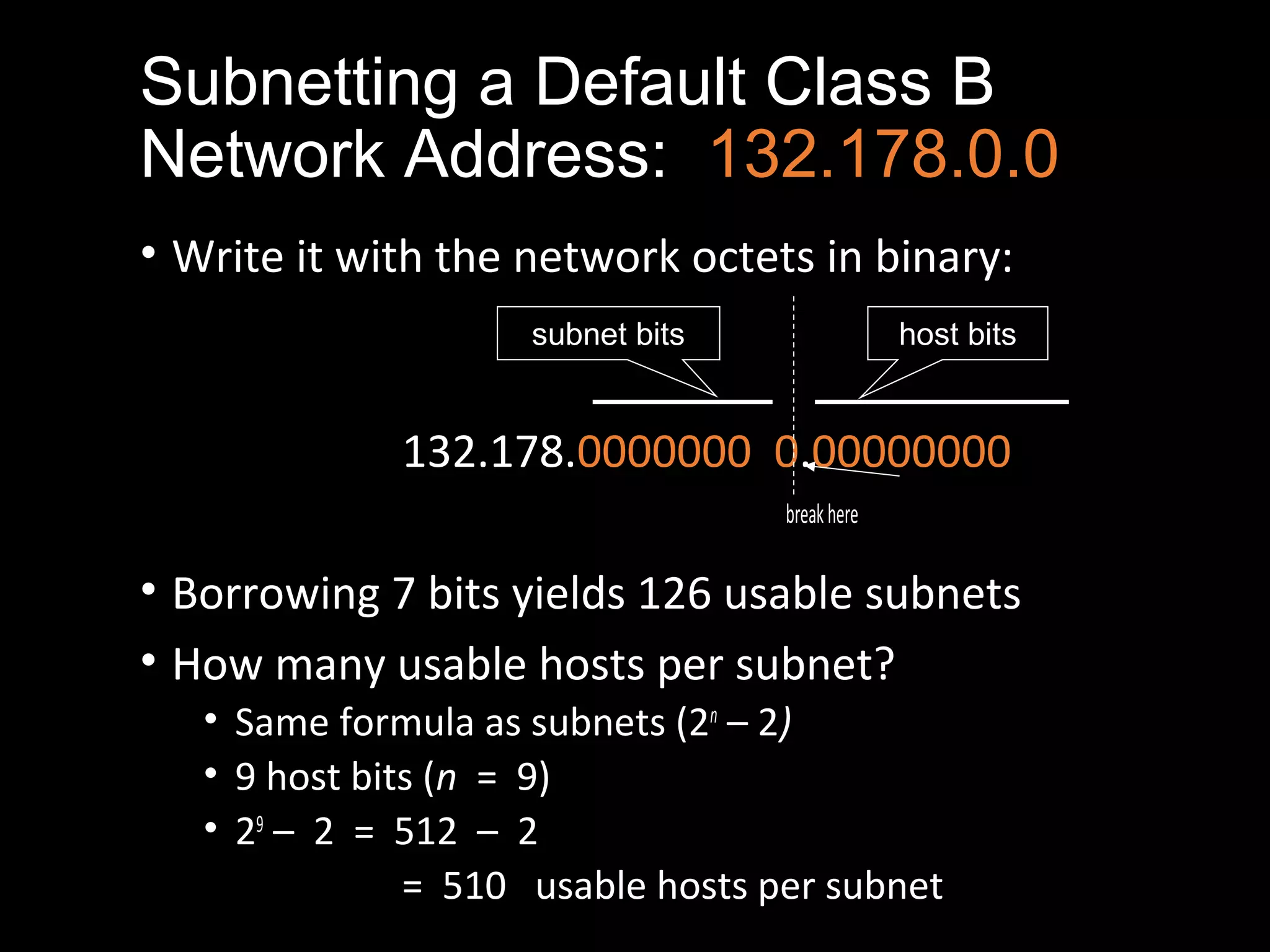
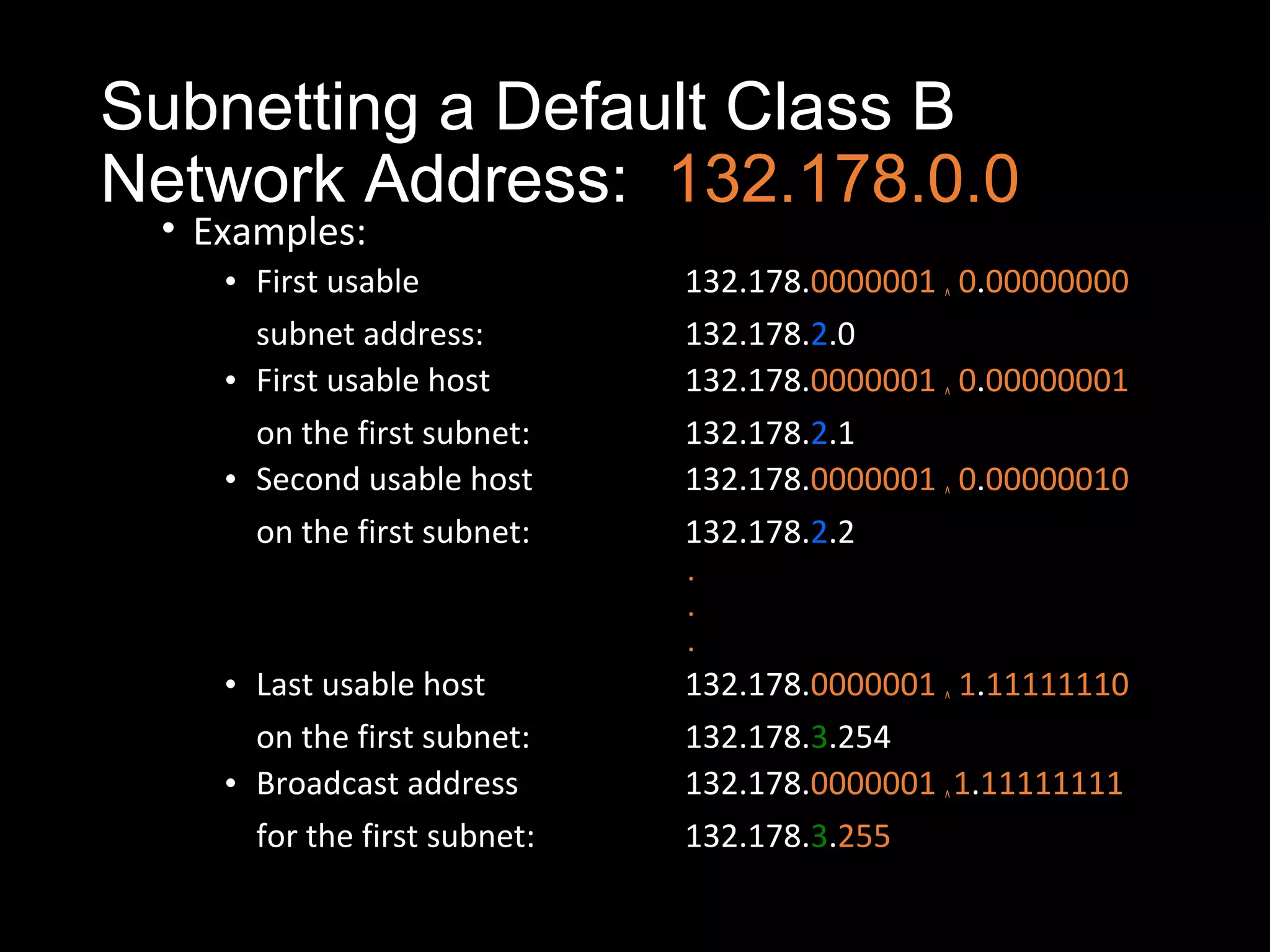
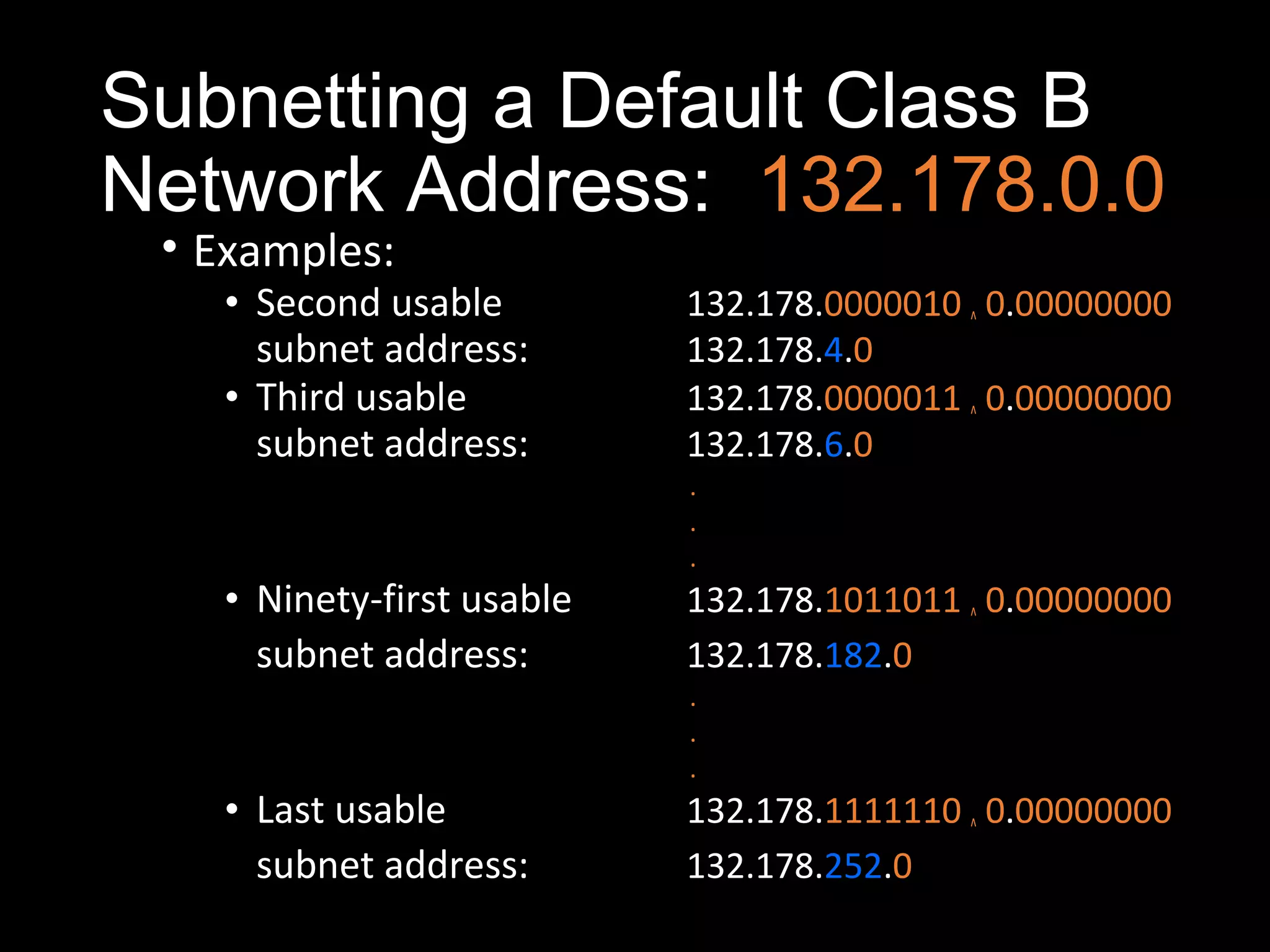
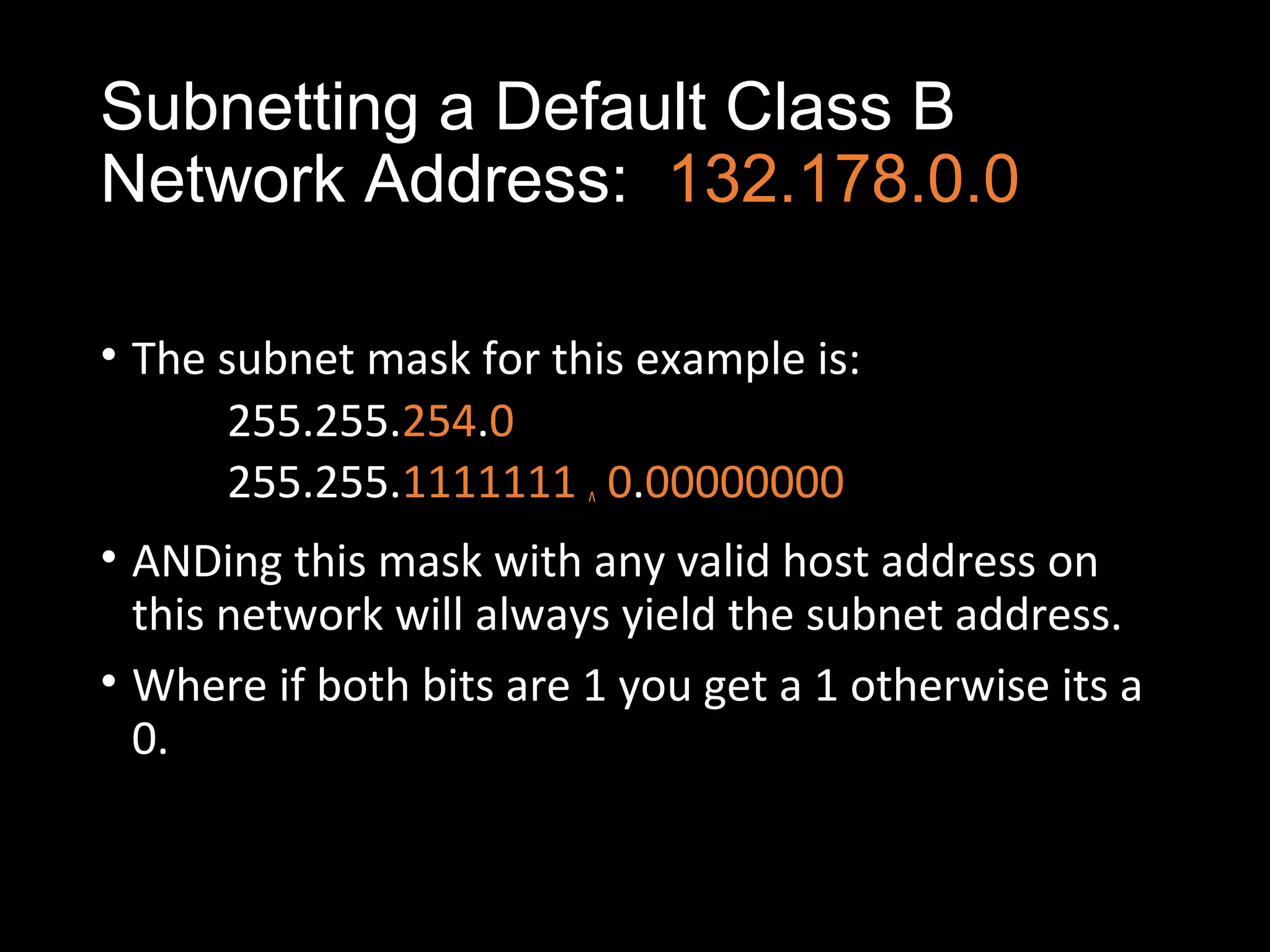
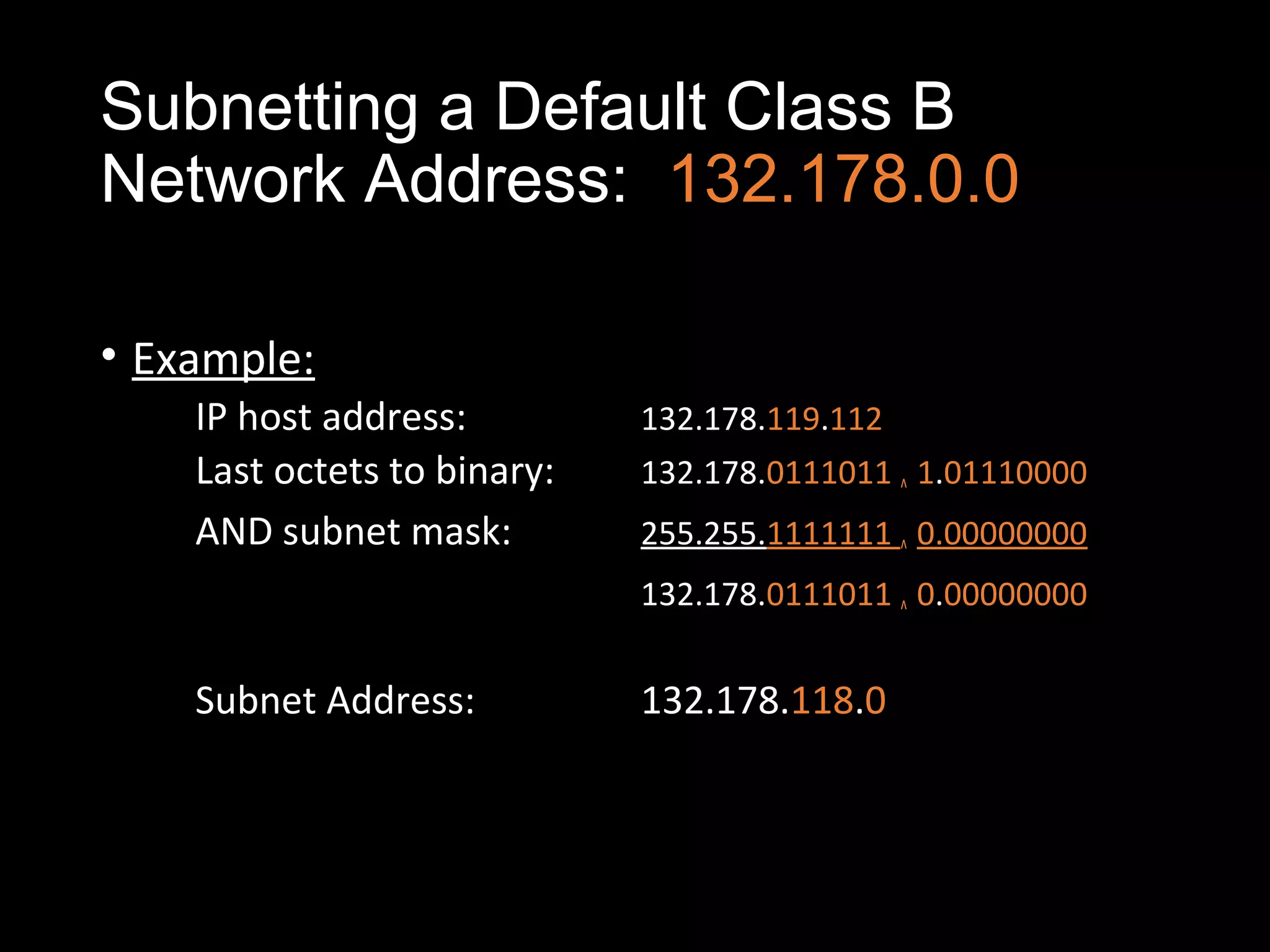
Subnetting allows a network administrator to break a single network into multiple subnets. It is done by borrowing bits from the host portion of the IP address to create a subnet portion. This increases the number of available subnets while reducing the number of available hosts per subnet. The document provides examples of subnetting default class C and class B network addresses, showing how to determine the number of bits to borrow to meet subnet and host requirements, and how subnet masks are used to identify the subnet of a given host IP address.