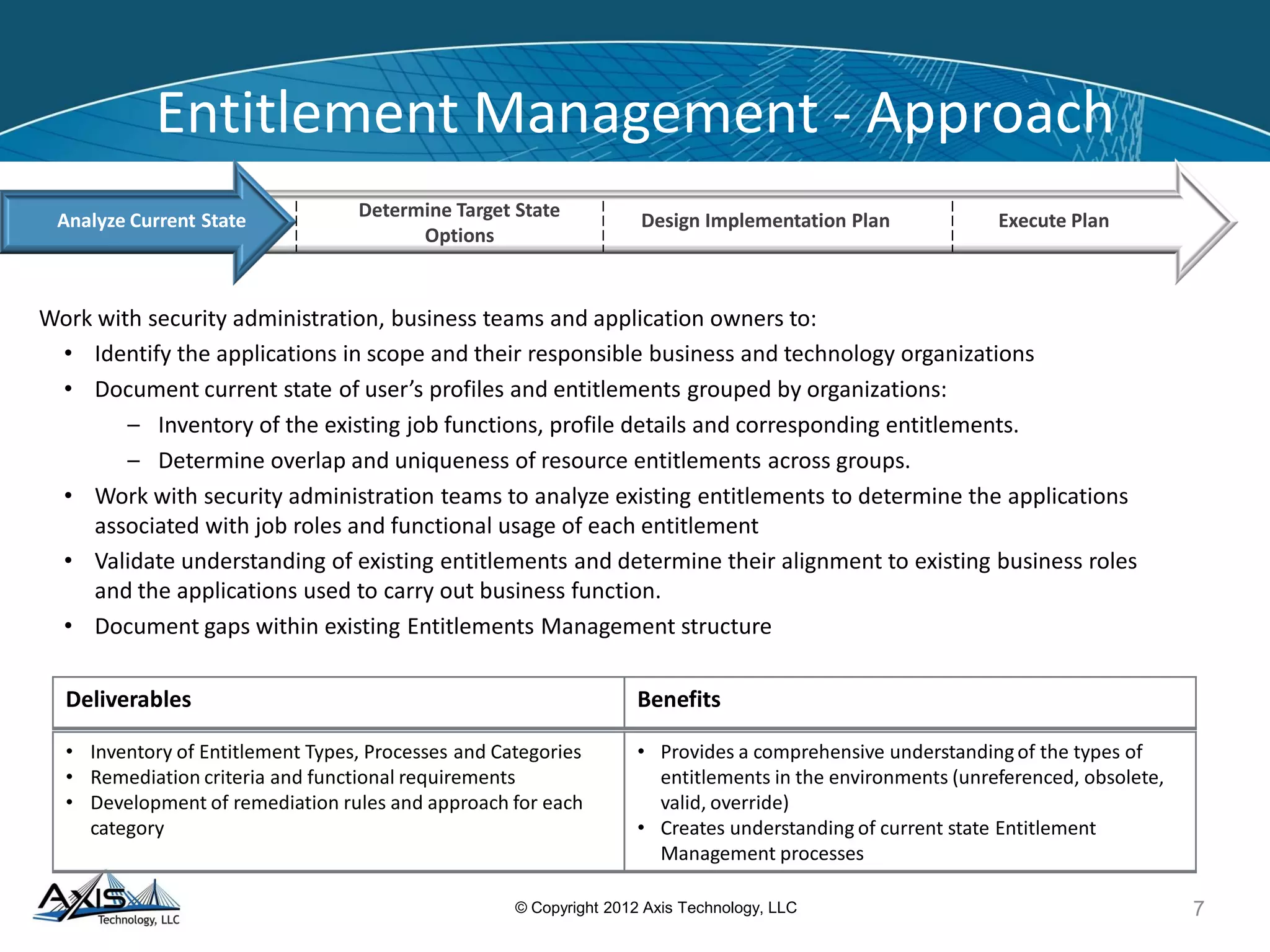
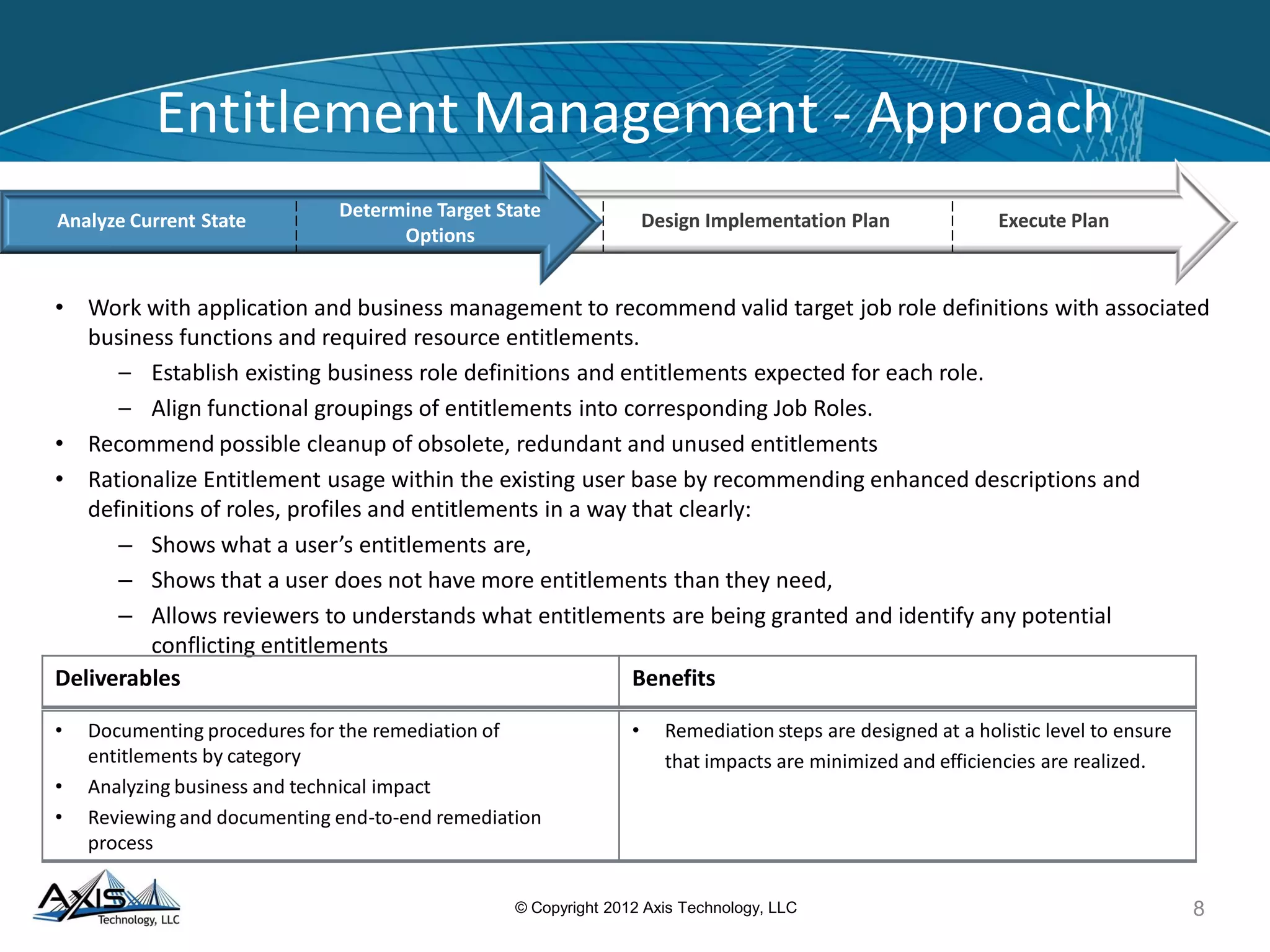
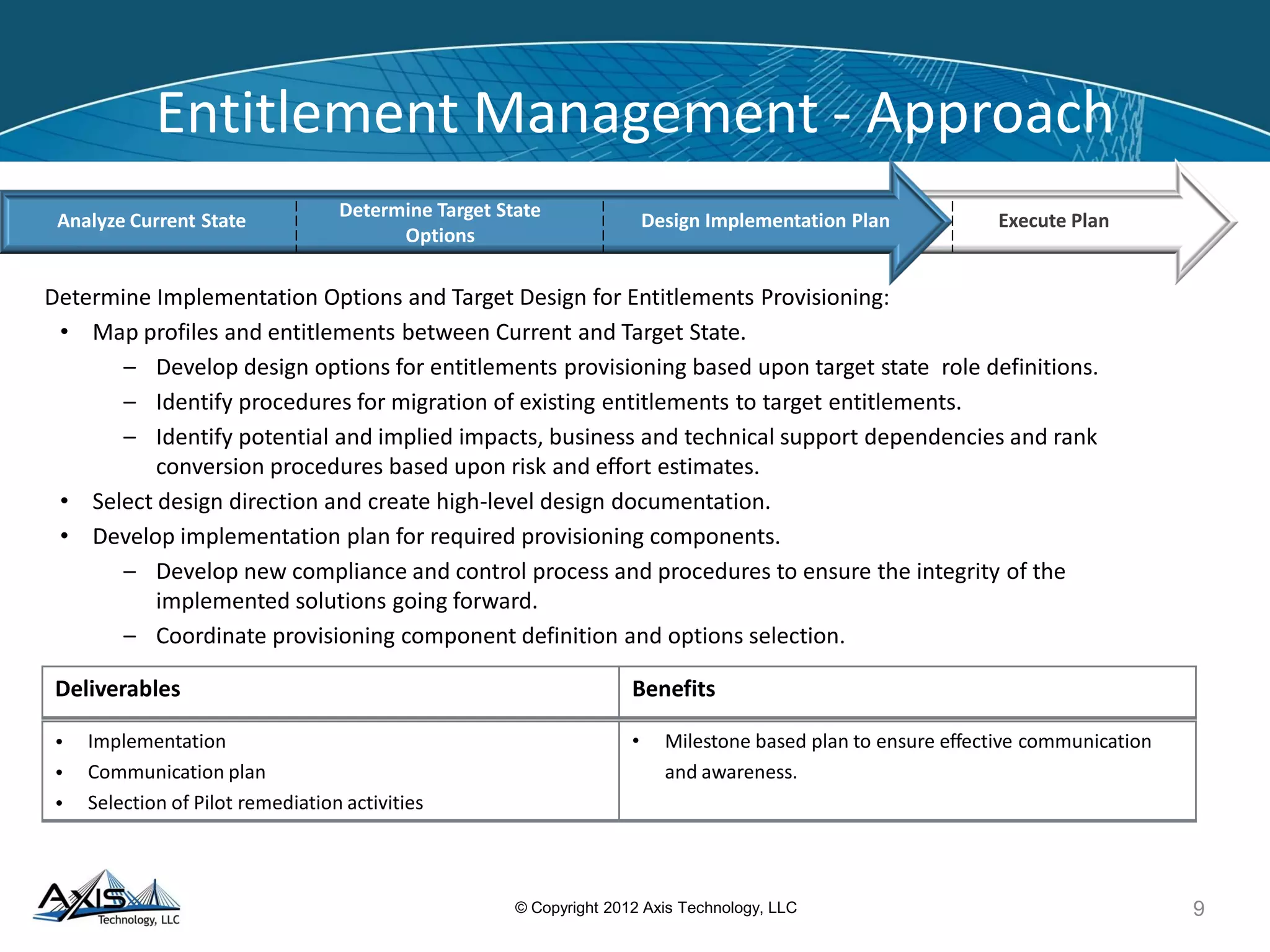
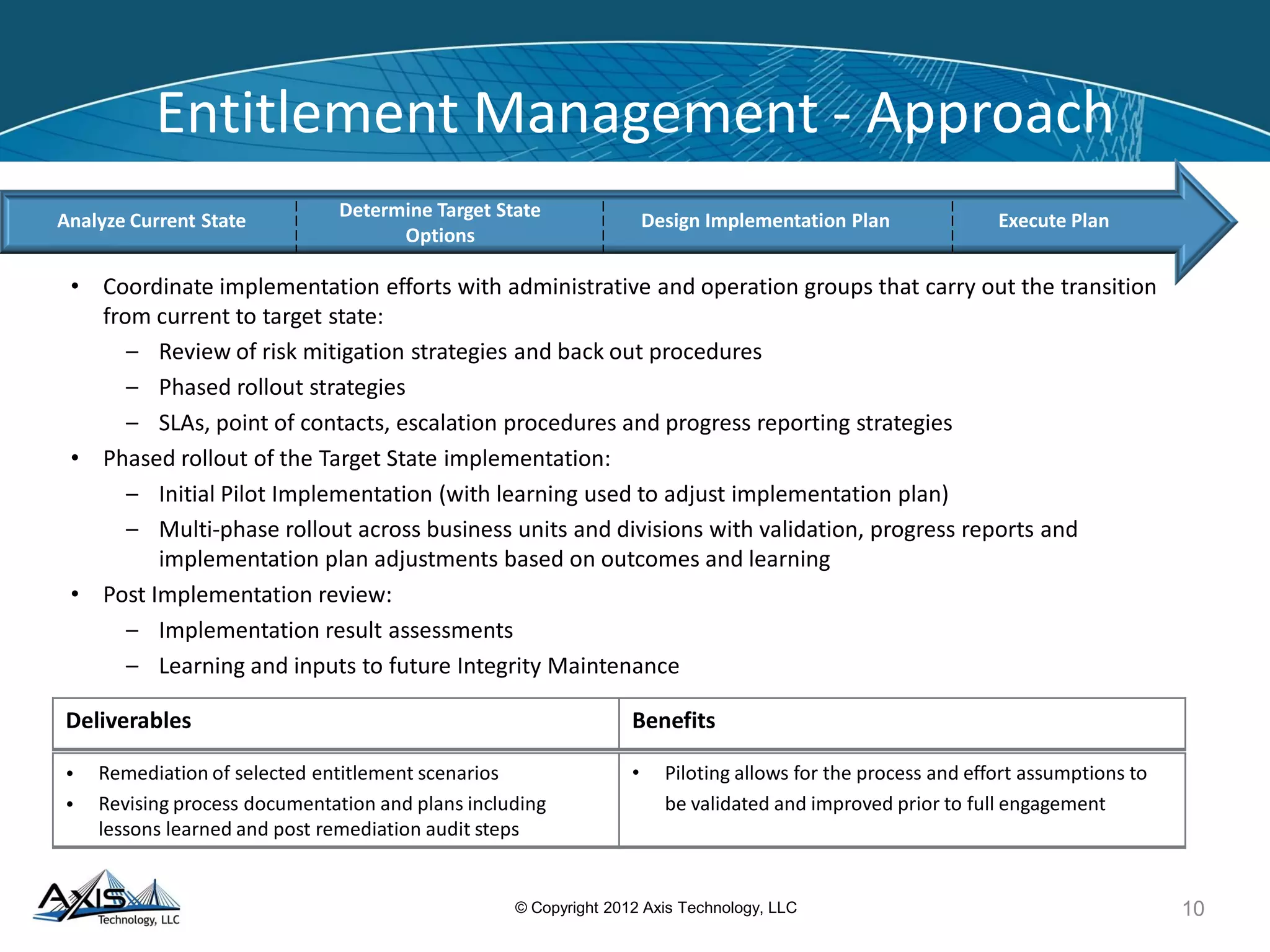
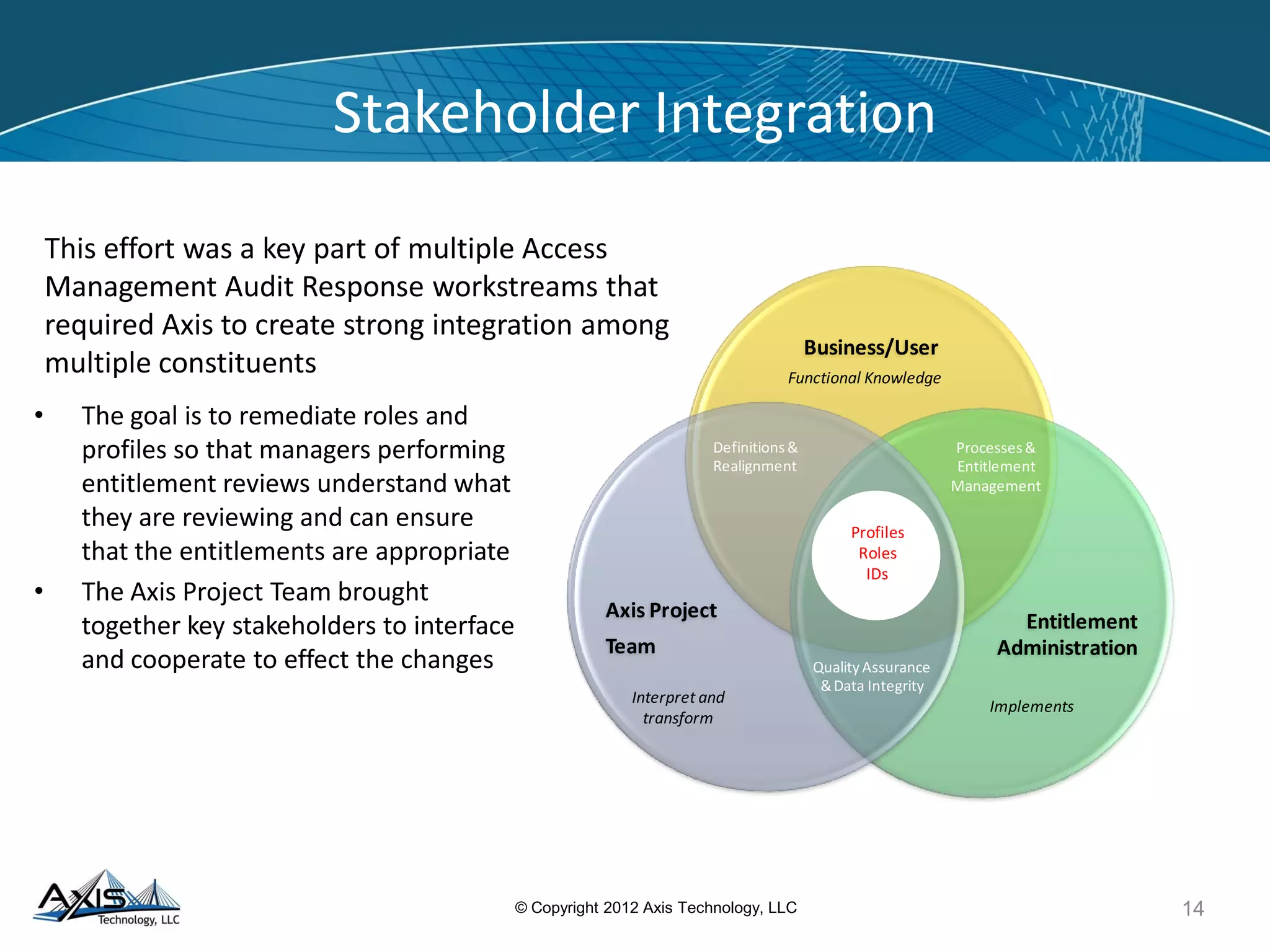
The document discusses entitlement and access management, emphasizing the importance of regulatory compliance and the risks associated with ineffective entitlements in application environments. It outlines an approach for analyzing, designing, and implementing entitlement management systems to ensure that user access aligns with organizational policies and requirements. Key deliverables include inventorying entitlement types, documenting procedures, and remediating obsolete access controls to enhance security and compliance.