Data Management Strategy
•
1 like•321 views
The document summarizes a case study of a Property and Casualty Insurance Carrier that engaged an assessment of its data management practices. The assessment found the current practices to be disjointed due to recent acquisitions. It identified a roadmap of initiatives to mature the data management practice across six pillars including data governance. The solution extended the system development lifecycle to implement controls for data quality, profiling, and metadata capture. It also established operational quality audits and a knowledge transfer plan to communicate changes and monitor ongoing performance.
Report
Share
Report
Share
Recommended
SDM Presentation V1.0

This presentation contains our view on how data can be Strategically managed and stewarded in an organization, and the categories where rules can be applied to facilitate that process.
Is Your Data Ready to Drive Your Company's Future?

Before investing the time and money to implement a reporting and analytics solution to guide you out of the current economic crisis, make sure that your data is prepared to lead the way.
Join Edgewater Technology for a step-by-step approach to readying your data to support enterprise reporting and analytics applications.
Information systems, organizations, management and strategy

The document discusses various topics related to organizations and information systems including:
- Definitions of organizations from technical and behavioral perspectives
- Structural characteristics of organizations like division of labor and standard operating procedures
- Changing roles of information systems in organizations and how they lead to automation and virtual organizations
- Decision making processes at different levels and models like rational, political, and "garbage can"
- Use of information technology for competitive advantage at business, firm, and industry levels through strategies
- Importance of managing strategic transitions when adopting new information systems technologies
Enterprise information flow and data management

The document discusses the importance of aligning master data management, master data governance, and business process management for effective enterprise information management and decision making. It states that bad data costs businesses 10-20% of annual revenue. The document provides a framework for assessing the maturity of these initiatives and advancing them in a synchronized manner from the initial configuration stage through facilitating, delivering, evaluating, and changing stages. It identifies key factors for evaluating solutions for master data management, governance, and business process management.
Data Quality Management: Cleaner Data, Better Reporting

This document discusses Accenture's regulatory reporting framework and offerings around data quality management. It provides an overview of Accenture's high-performance financial reporting framework, which aims to consolidate frameworks, processes, and technology to create efficiencies across reporting functions. It also summarizes Accenture's regulatory reporting offerings, including data quality management, capability design, target operating models, and regulatory reporting vendor implementation support. Finally, it covers key aspects of data quality management, such as issue classification, management processes, governance structures, root cause analysis, and issue prioritization. The goal is to help financial institutions improve data quality, reporting accuracy and efficiency.
Data Governance That Drives the Bottom Line

The financial services sector is investing heavily in data governance solutions to find, understand and trust customer data, while also managing compliance risk around an ever-evolving regulatory landscape more effectively.
But do you still find it difficult to get management support for data governance budgets? Do you have the tools you need to determine the “business cost of data” accurately? Can you show the CFO an ROI projection he can count on? Are you able to answer, “Will I see results on the top line or the bottom line?” Are your business line leaders able to identify areas that are losing money due to data problems?
If you answered no to any of these questions, join Precisely in our upcoming webinar that will focus on how Financial Services companies can monetize the return on investment for data governance and how to relate it to business results that every senior leader understands.
Join this on-demand webinar to learn about:
- How to select data initiatives based on corporate goals and strategy
- How to connect the dots from data challenges (quality, availability, accuracy, currency) to specific business metrics around
- How to quantify the data contribution to improving business performance around
- How to leverage metadata and linage to get a 360-degree understanding of your data
- How to evaluate data assets by assigning measures and defining scores.
- How to assign accountability to assets and processes
- How to define and execute the workflows needed to implement corrective actions
- How to highlight the benefits of data governance
Big Data Readiness & Business Intelligence Capabilities Matrix

This document discusses big data readiness and business intelligence (BI) capabilities. It provides a rubric to assess an organization's big data readiness based on feasibility, reasonability, value, integrability, and sustainability. It also describes four synergistic BI capabilities - organizational memory, information integration, insight creation, and presentation - and provides a matrix to measure an organization's maturity in each capability area.
Telelogic Dashboard Cmmi Presentation

The document discusses the Telelogic Dashboard software and its support for CMMI process improvement. Some key points:
- Telelogic Dashboard provides automation, visualization and tailoring capabilities to support all tasks within the CMMI Measurement & Analysis process area.
- It offers a library of best practices and metrics as well as tools for data collection, analysis, storage and reporting of results.
- The software aims to help organizations continuously improve their software development lifecycle processes and demonstrate compliance with standards like CMMI through effective measurement and management.
Recommended
SDM Presentation V1.0

This presentation contains our view on how data can be Strategically managed and stewarded in an organization, and the categories where rules can be applied to facilitate that process.
Is Your Data Ready to Drive Your Company's Future?

Before investing the time and money to implement a reporting and analytics solution to guide you out of the current economic crisis, make sure that your data is prepared to lead the way.
Join Edgewater Technology for a step-by-step approach to readying your data to support enterprise reporting and analytics applications.
Information systems, organizations, management and strategy

The document discusses various topics related to organizations and information systems including:
- Definitions of organizations from technical and behavioral perspectives
- Structural characteristics of organizations like division of labor and standard operating procedures
- Changing roles of information systems in organizations and how they lead to automation and virtual organizations
- Decision making processes at different levels and models like rational, political, and "garbage can"
- Use of information technology for competitive advantage at business, firm, and industry levels through strategies
- Importance of managing strategic transitions when adopting new information systems technologies
Enterprise information flow and data management

The document discusses the importance of aligning master data management, master data governance, and business process management for effective enterprise information management and decision making. It states that bad data costs businesses 10-20% of annual revenue. The document provides a framework for assessing the maturity of these initiatives and advancing them in a synchronized manner from the initial configuration stage through facilitating, delivering, evaluating, and changing stages. It identifies key factors for evaluating solutions for master data management, governance, and business process management.
Data Quality Management: Cleaner Data, Better Reporting

This document discusses Accenture's regulatory reporting framework and offerings around data quality management. It provides an overview of Accenture's high-performance financial reporting framework, which aims to consolidate frameworks, processes, and technology to create efficiencies across reporting functions. It also summarizes Accenture's regulatory reporting offerings, including data quality management, capability design, target operating models, and regulatory reporting vendor implementation support. Finally, it covers key aspects of data quality management, such as issue classification, management processes, governance structures, root cause analysis, and issue prioritization. The goal is to help financial institutions improve data quality, reporting accuracy and efficiency.
Data Governance That Drives the Bottom Line

The financial services sector is investing heavily in data governance solutions to find, understand and trust customer data, while also managing compliance risk around an ever-evolving regulatory landscape more effectively.
But do you still find it difficult to get management support for data governance budgets? Do you have the tools you need to determine the “business cost of data” accurately? Can you show the CFO an ROI projection he can count on? Are you able to answer, “Will I see results on the top line or the bottom line?” Are your business line leaders able to identify areas that are losing money due to data problems?
If you answered no to any of these questions, join Precisely in our upcoming webinar that will focus on how Financial Services companies can monetize the return on investment for data governance and how to relate it to business results that every senior leader understands.
Join this on-demand webinar to learn about:
- How to select data initiatives based on corporate goals and strategy
- How to connect the dots from data challenges (quality, availability, accuracy, currency) to specific business metrics around
- How to quantify the data contribution to improving business performance around
- How to leverage metadata and linage to get a 360-degree understanding of your data
- How to evaluate data assets by assigning measures and defining scores.
- How to assign accountability to assets and processes
- How to define and execute the workflows needed to implement corrective actions
- How to highlight the benefits of data governance
Big Data Readiness & Business Intelligence Capabilities Matrix

This document discusses big data readiness and business intelligence (BI) capabilities. It provides a rubric to assess an organization's big data readiness based on feasibility, reasonability, value, integrability, and sustainability. It also describes four synergistic BI capabilities - organizational memory, information integration, insight creation, and presentation - and provides a matrix to measure an organization's maturity in each capability area.
Telelogic Dashboard Cmmi Presentation

The document discusses the Telelogic Dashboard software and its support for CMMI process improvement. Some key points:
- Telelogic Dashboard provides automation, visualization and tailoring capabilities to support all tasks within the CMMI Measurement & Analysis process area.
- It offers a library of best practices and metrics as well as tools for data collection, analysis, storage and reporting of results.
- The software aims to help organizations continuously improve their software development lifecycle processes and demonstrate compliance with standards like CMMI through effective measurement and management.
Effective master data management

The article is intended as a quick overview of what effective master data management means in today’s business context in terms of risks, challenges and opportunities for companies and decision makers. The article is structured in two main areas, which cover in turn the importance of an effective master data
management implementation and the methodology to get there.
About pellustro - The cloud-based platform for assessments

Pellustro is an innovative platform that provides collective intelligence based on the opinions and expertise of relevant participants from within and beyond your organization.
* Tap the collective insights of staff, colleagues, peers, stakeholders and experts
* Simplifies panel-based evaluation and research
* Results in improved and objectivize business decision-making
Pellustro uniquely integrates the power of community evaluations, sentiments, and expert advice with flexible analytics to derive trend and benchmark based insights and helps organizations support mandatory self assessments, measure alignment of capabilities and perceptions and benchmark over time and against peers.
About Element22 - Unlocking The Power Of Data

Element22 is a boutique data management advisory, design and technology solutions firm for the financial services industry. On a daily basis, we work with financial institutions to transfer them into data-driven organizations and meet regulatory requirements, such as BCBS 239.
Information Governance Program

The document discusses establishing an information governance program, including defining information value, building an information governance framework, focusing on areas like information quality and security, and ensuring business alignment; it emphasizes the importance of an information governance program for decision-making, compliance, and optimizing operations.
Information systems

This document provides an overview of the history and evolution of information systems and technology. It discusses how computers originally focused on business and defense uses before personal computers became common. Local area networks then allowed people to work together and share information. As technology advanced, larger organizations developed internal IT departments to manage systems and purchase software to coordinate business processes. Information systems are now critical to supporting business operations and management decision making through tools like databases, business process management systems, and decision support systems. When combined with changes to organization and management, information systems can provide a strategic advantage through optimization of costs and processes.
Introduction to DCAM, the Data Management Capability Assessment Model - Editi...

DCAM stands for Data management Capability Assessment Model. DCAM is a model to assess data management capabilities within the financial industry. It was created by the EDM Council in collaboration with over 100 financial institutions. This presentation provides an overview of DCAM and how financial institutions leverage DCAM to improve or establish their data management programs and meet regulatory requirements such as BCBS 239. Also the benefits of DCAM are described as part of this presentation.
Developing & Deploying Effective Data Governance Framework

This is the slide deck presented at the Customer Privacy and Data Protection India Summit 2019 held in Mumbai, India. The specific topics touched upon are the guiding principles, Aligning with Data Architecture, Data Quality & Compliance.
EIM Presentation 2016

This document discusses Enterprise Information Management (EIM) solutions for financial institutions. It summarizes that the company delivers global EIM solutions including information architecture, data warehousing, business intelligence, and data governance. They help customers understand and leverage their data to grow revenue and drive efficiencies. The document also states that financial institutions have a wealth of customer data that, if analyzed, can help them better understand customer needs and wants. It emphasizes that banks will need to become more digital, customer-driven, and innovative by 2020 to stay competitive.
You Need a Data Catalog. Do You Know Why?

The data catalog has become a popular discussion topic within data management and data governance circles. A data catalog is a central repository that contains metadata for describing data sets, how they are defined, and where to find them. TDWI research indicates that implementing a data catalog is a top priority among organizations we survey. The data catalog can also play an important part in the governance process. It provides features that help ensure data quality, compliance, and that trusted data is used for analysis. Without an in-depth knowledge of data and associated metadata, organizations cannot truly safeguard and govern their data.
Join this on-demand webinar to learn more about the data catalog and its role in data governance efforts.
Topics include:
· Data management challenges and priorities
· The modern data catalog – what it is and why it is important
· The role of the modern data catalog in your data quality and governance programs
· The kinds of information that should be in your data catalog and why
Building an Effective & Extensible Data & Analytics Operating Model

This document provides a framework for building an effective and extensible data and analytics operating model. It outlines a 3-step methodology: 1) Develop a business model focused on data; 2) Design the operating model focusing on integration and standardization of processes and data; 3) Design the operating model architecture detailing how people, processes and technology are organized. It identifies 9 core components of the operating model including managing processes, data, analytics services, and governance. The document provides examples of how to detail the subcomponents and design rules to integrate and standardize data across the organization.
Enterprise Performance Management

1) The document discusses designing an Enterprise Performance Management (EPM) system for Anglo French Textiles to improve decision-making.
2) It identifies key performance indicators (KPIs) for different departments like finance, manufacturing, and production.
3) The proposed EPM system would integrate data from different sources to provide consolidated reports and visual analytics to help managers make quicker decisions.
2013 04 irm mdmdg - jon asprey 4 most asked dg questions v 1 3

This document provides guidance on addressing the four most common questions around implementing an effective data governance program. It recommends starting by understanding business processes and identifying "hidden factories" of data issues. Standards and rules should be defined through dialogue with stakeholders. Engaging the business requires building a business case by quantifying impacts and communicating successes. Demonstrating value involves measuring improvements in key business metrics from risk reduction, cost savings, or increased efficiency.
7 principles of data quality management

The document outlines 7 principles of data quality management:
1) Have a business-need focus to meet requirements.
2) Have leadership alignment on common strategies and policies.
3) Engage stakeholders across the organization to share responsibility.
4) Take a process approach to understand interconnected activities.
5) Have continuous improvement as an ongoing focus.
6) Make data-based decisions more often.
7) Manage relationships with vendors, producers, and consumers.
Data Governance for Enterprises

Data governance involves setting up procedures and regulations to enable the smooth sharing, managing, and availability of data.
The idea is to prevent an overlap of resources. When you have data governance procedures you experience faster decision-making processes while moving data from just a company’s by-product to a critical asset within the organization. Check out this and know how to build a strong Governance framework for your organization
MDM Mistakes & How to Avoid Them!

The Data Governance Annual Conference and International Data Quality Conference in San Diego was very good. I recommend this conference for business and IT persons responsible for data quality and data governenance. There will be a similar event in Orlando, December 2010. This is the presentation I delivered to a grateful audience.
EVERFI/SEI Webinar: Implementing a Competitive GDPR Compliance Posture

This document discusses implementing a competitive GDPR compliance posture. It provides an overview of GDPR and outlines a four-phase implementation cycle: 1) Assess current state and remediate, 2) Develop the future state, 3) Implement, and 4) Maintain compliance. It emphasizes the importance of change management and training to successfully implement GDPR requirements.
Business Performance Management - Business Intelligence for Managers

Performance management originated in the late 1970s and refers to a set of management processes that help organizations improve strategy execution, decision-making, and performance. It involves defining strategic objectives, measuring performance, analyzing results, and aligning people and culture. More advanced approaches integrate performance management with other key processes like financial planning, project management, and risk management to create a holistic view of organizational performance. Technology solutions can help organizations systematically manage performance across the enterprise.
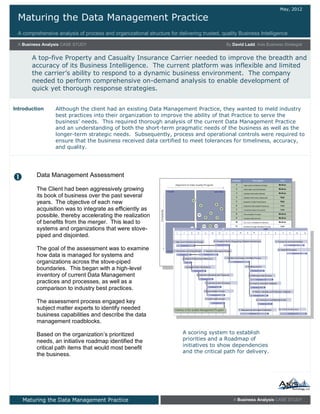
Develop and Implement an Effective Data Management Strategy and Roadmap 

Treat data as an asset and gain a competitive advantage.
Your Challenge
Despite the growing focus on data, many organizations struggle to develop an effective strategy for their data assets. This is due to their intangible nature and varying use across the business.
Data Management is a business process managed by IT. This creates a challenge for IT as it is required to create and manage complex systems of operations that link closely to integral business operations.
Our Advice
Critical Insight
Data Management is not one size fits all. Cut through the noise related to Data Management and create a strategy and process that is right for your organization.
Have the business drive your Data Management project.
It all starts and ends with Data Governance. At a minimum, invest in Data Governance initiatives.
Impact and Result
Coordination between IT and the business will create a Data Management strategy that understands and satisfies the data requirements of the business.
Data Management requirements and initiatives will be derived from the following: business goals and strategic plans, current capability assessments, business drivers for data, understanding of market and technology opportunities, and a clear understanding of the business’s drivers regarding data.
Creating a clear Data Management Strategy and developing a roadmap of initiatives will allow IT to create a plan for how to bridge the gap between IT and the business and create a Data Management framework that supports the business’s immediate and long-term data requirements.
How accurate are your company data

This document discusses the importance of having accurate key performance indicators (KPIs) and discusses some common issues that can lead to inaccurate KPIs. It notes that smaller companies often manually manipulate spreadsheet data to calculate KPIs, which can introduce errors. It recommends that smaller companies have an independent consultant validate their KPI spreadsheets. The document also discusses the importance of having clean, relevant data for effective business decision making and management reporting. It outlines some best practices for evaluating data quality issues and ensuring data relevance.
Strategic alignment with bi and ROI Affect

This document discusses the importance of business intelligence and analytics for organizations. It defines business intelligence as activities used to discover, analyze, and assess information to help guide strategic decision making. The main types of intelligence discussed are competitive, market, technological, and strategic intelligence. Effective corporate intelligence involves identifying needs, establishing information sources, analyzing raw data, and disseminating insights within the company. When properly implemented using tools like data mining and knowledge management systems, business intelligence can help organizations improve products, customer relationships, and operations by basing decisions on relevant facts and metrics.
Enterprise Information Management Strategy - a proven approach

Access a proven approach to Enterprise Information Management Strategy - providing a framework for Digital Transformation - by a leader in Information Management Consulting - Entity Group
Strategic Supply Chain Management (English Version)

Strategic Supply Chain Management : The use of Metrics To Drive Business Success from “The 5 Discipline For Top Performance in Strategic Supply Chain Management"
Strategic Supply chain management has a huge impact on our day to day business, and Good SCM strategic can directly improve our customer service and the bottom line of the company. Strategic supply chain is an iterative process that evaluates the cost- benefit trade-offs of operational components that involves leveraging the core competencies of the organization to achieve a defined high-level goal or objective. As a Master in Industrial Engineering Candidate, i am delighted to share with all of you some insights from my discussion with the Lecturer Bpk. Dr. Dadang Surjasa, S.Si, MT Dadang Surjasa, to make you even more understand about the impact of strategic SCM in a business, especially the use of Metrics to Drive your business success. I hope this information will be useful for the readers to gain more insights about supply chain management it self. Have a great day everyone!
More Related Content
What's hot
Effective master data management

The article is intended as a quick overview of what effective master data management means in today’s business context in terms of risks, challenges and opportunities for companies and decision makers. The article is structured in two main areas, which cover in turn the importance of an effective master data
management implementation and the methodology to get there.
About pellustro - The cloud-based platform for assessments

Pellustro is an innovative platform that provides collective intelligence based on the opinions and expertise of relevant participants from within and beyond your organization.
* Tap the collective insights of staff, colleagues, peers, stakeholders and experts
* Simplifies panel-based evaluation and research
* Results in improved and objectivize business decision-making
Pellustro uniquely integrates the power of community evaluations, sentiments, and expert advice with flexible analytics to derive trend and benchmark based insights and helps organizations support mandatory self assessments, measure alignment of capabilities and perceptions and benchmark over time and against peers.
About Element22 - Unlocking The Power Of Data

Element22 is a boutique data management advisory, design and technology solutions firm for the financial services industry. On a daily basis, we work with financial institutions to transfer them into data-driven organizations and meet regulatory requirements, such as BCBS 239.
Information Governance Program

The document discusses establishing an information governance program, including defining information value, building an information governance framework, focusing on areas like information quality and security, and ensuring business alignment; it emphasizes the importance of an information governance program for decision-making, compliance, and optimizing operations.
Information systems

This document provides an overview of the history and evolution of information systems and technology. It discusses how computers originally focused on business and defense uses before personal computers became common. Local area networks then allowed people to work together and share information. As technology advanced, larger organizations developed internal IT departments to manage systems and purchase software to coordinate business processes. Information systems are now critical to supporting business operations and management decision making through tools like databases, business process management systems, and decision support systems. When combined with changes to organization and management, information systems can provide a strategic advantage through optimization of costs and processes.
Introduction to DCAM, the Data Management Capability Assessment Model - Editi...

DCAM stands for Data management Capability Assessment Model. DCAM is a model to assess data management capabilities within the financial industry. It was created by the EDM Council in collaboration with over 100 financial institutions. This presentation provides an overview of DCAM and how financial institutions leverage DCAM to improve or establish their data management programs and meet regulatory requirements such as BCBS 239. Also the benefits of DCAM are described as part of this presentation.
Developing & Deploying Effective Data Governance Framework

This is the slide deck presented at the Customer Privacy and Data Protection India Summit 2019 held in Mumbai, India. The specific topics touched upon are the guiding principles, Aligning with Data Architecture, Data Quality & Compliance.
EIM Presentation 2016

This document discusses Enterprise Information Management (EIM) solutions for financial institutions. It summarizes that the company delivers global EIM solutions including information architecture, data warehousing, business intelligence, and data governance. They help customers understand and leverage their data to grow revenue and drive efficiencies. The document also states that financial institutions have a wealth of customer data that, if analyzed, can help them better understand customer needs and wants. It emphasizes that banks will need to become more digital, customer-driven, and innovative by 2020 to stay competitive.
You Need a Data Catalog. Do You Know Why?

The data catalog has become a popular discussion topic within data management and data governance circles. A data catalog is a central repository that contains metadata for describing data sets, how they are defined, and where to find them. TDWI research indicates that implementing a data catalog is a top priority among organizations we survey. The data catalog can also play an important part in the governance process. It provides features that help ensure data quality, compliance, and that trusted data is used for analysis. Without an in-depth knowledge of data and associated metadata, organizations cannot truly safeguard and govern their data.
Join this on-demand webinar to learn more about the data catalog and its role in data governance efforts.
Topics include:
· Data management challenges and priorities
· The modern data catalog – what it is and why it is important
· The role of the modern data catalog in your data quality and governance programs
· The kinds of information that should be in your data catalog and why
Building an Effective & Extensible Data & Analytics Operating Model

This document provides a framework for building an effective and extensible data and analytics operating model. It outlines a 3-step methodology: 1) Develop a business model focused on data; 2) Design the operating model focusing on integration and standardization of processes and data; 3) Design the operating model architecture detailing how people, processes and technology are organized. It identifies 9 core components of the operating model including managing processes, data, analytics services, and governance. The document provides examples of how to detail the subcomponents and design rules to integrate and standardize data across the organization.
Enterprise Performance Management

1) The document discusses designing an Enterprise Performance Management (EPM) system for Anglo French Textiles to improve decision-making.
2) It identifies key performance indicators (KPIs) for different departments like finance, manufacturing, and production.
3) The proposed EPM system would integrate data from different sources to provide consolidated reports and visual analytics to help managers make quicker decisions.
2013 04 irm mdmdg - jon asprey 4 most asked dg questions v 1 3

This document provides guidance on addressing the four most common questions around implementing an effective data governance program. It recommends starting by understanding business processes and identifying "hidden factories" of data issues. Standards and rules should be defined through dialogue with stakeholders. Engaging the business requires building a business case by quantifying impacts and communicating successes. Demonstrating value involves measuring improvements in key business metrics from risk reduction, cost savings, or increased efficiency.
7 principles of data quality management

The document outlines 7 principles of data quality management:
1) Have a business-need focus to meet requirements.
2) Have leadership alignment on common strategies and policies.
3) Engage stakeholders across the organization to share responsibility.
4) Take a process approach to understand interconnected activities.
5) Have continuous improvement as an ongoing focus.
6) Make data-based decisions more often.
7) Manage relationships with vendors, producers, and consumers.
Data Governance for Enterprises

Data governance involves setting up procedures and regulations to enable the smooth sharing, managing, and availability of data.
The idea is to prevent an overlap of resources. When you have data governance procedures you experience faster decision-making processes while moving data from just a company’s by-product to a critical asset within the organization. Check out this and know how to build a strong Governance framework for your organization
MDM Mistakes & How to Avoid Them!

The Data Governance Annual Conference and International Data Quality Conference in San Diego was very good. I recommend this conference for business and IT persons responsible for data quality and data governenance. There will be a similar event in Orlando, December 2010. This is the presentation I delivered to a grateful audience.
EVERFI/SEI Webinar: Implementing a Competitive GDPR Compliance Posture

This document discusses implementing a competitive GDPR compliance posture. It provides an overview of GDPR and outlines a four-phase implementation cycle: 1) Assess current state and remediate, 2) Develop the future state, 3) Implement, and 4) Maintain compliance. It emphasizes the importance of change management and training to successfully implement GDPR requirements.
Business Performance Management - Business Intelligence for Managers

Performance management originated in the late 1970s and refers to a set of management processes that help organizations improve strategy execution, decision-making, and performance. It involves defining strategic objectives, measuring performance, analyzing results, and aligning people and culture. More advanced approaches integrate performance management with other key processes like financial planning, project management, and risk management to create a holistic view of organizational performance. Technology solutions can help organizations systematically manage performance across the enterprise.
Develop and Implement an Effective Data Management Strategy and Roadmap 

Treat data as an asset and gain a competitive advantage.
Your Challenge
Despite the growing focus on data, many organizations struggle to develop an effective strategy for their data assets. This is due to their intangible nature and varying use across the business.
Data Management is a business process managed by IT. This creates a challenge for IT as it is required to create and manage complex systems of operations that link closely to integral business operations.
Our Advice
Critical Insight
Data Management is not one size fits all. Cut through the noise related to Data Management and create a strategy and process that is right for your organization.
Have the business drive your Data Management project.
It all starts and ends with Data Governance. At a minimum, invest in Data Governance initiatives.
Impact and Result
Coordination between IT and the business will create a Data Management strategy that understands and satisfies the data requirements of the business.
Data Management requirements and initiatives will be derived from the following: business goals and strategic plans, current capability assessments, business drivers for data, understanding of market and technology opportunities, and a clear understanding of the business’s drivers regarding data.
Creating a clear Data Management Strategy and developing a roadmap of initiatives will allow IT to create a plan for how to bridge the gap between IT and the business and create a Data Management framework that supports the business’s immediate and long-term data requirements.
How accurate are your company data

This document discusses the importance of having accurate key performance indicators (KPIs) and discusses some common issues that can lead to inaccurate KPIs. It notes that smaller companies often manually manipulate spreadsheet data to calculate KPIs, which can introduce errors. It recommends that smaller companies have an independent consultant validate their KPI spreadsheets. The document also discusses the importance of having clean, relevant data for effective business decision making and management reporting. It outlines some best practices for evaluating data quality issues and ensuring data relevance.
Strategic alignment with bi and ROI Affect

This document discusses the importance of business intelligence and analytics for organizations. It defines business intelligence as activities used to discover, analyze, and assess information to help guide strategic decision making. The main types of intelligence discussed are competitive, market, technological, and strategic intelligence. Effective corporate intelligence involves identifying needs, establishing information sources, analyzing raw data, and disseminating insights within the company. When properly implemented using tools like data mining and knowledge management systems, business intelligence can help organizations improve products, customer relationships, and operations by basing decisions on relevant facts and metrics.
What's hot (20)
About pellustro - The cloud-based platform for assessments

About pellustro - The cloud-based platform for assessments
Introduction to DCAM, the Data Management Capability Assessment Model - Editi...

Introduction to DCAM, the Data Management Capability Assessment Model - Editi...
Developing & Deploying Effective Data Governance Framework

Developing & Deploying Effective Data Governance Framework
Building an Effective & Extensible Data & Analytics Operating Model

Building an Effective & Extensible Data & Analytics Operating Model
2013 04 irm mdmdg - jon asprey 4 most asked dg questions v 1 3

2013 04 irm mdmdg - jon asprey 4 most asked dg questions v 1 3
EVERFI/SEI Webinar: Implementing a Competitive GDPR Compliance Posture

EVERFI/SEI Webinar: Implementing a Competitive GDPR Compliance Posture
Business Performance Management - Business Intelligence for Managers

Business Performance Management - Business Intelligence for Managers
Develop and Implement an Effective Data Management Strategy and Roadmap 

Develop and Implement an Effective Data Management Strategy and Roadmap
Similar to Data Management Strategy
Enterprise Information Management Strategy - a proven approach

Access a proven approach to Enterprise Information Management Strategy - providing a framework for Digital Transformation - by a leader in Information Management Consulting - Entity Group
Strategic Supply Chain Management (English Version)

Strategic Supply Chain Management : The use of Metrics To Drive Business Success from “The 5 Discipline For Top Performance in Strategic Supply Chain Management"
Strategic Supply chain management has a huge impact on our day to day business, and Good SCM strategic can directly improve our customer service and the bottom line of the company. Strategic supply chain is an iterative process that evaluates the cost- benefit trade-offs of operational components that involves leveraging the core competencies of the organization to achieve a defined high-level goal or objective. As a Master in Industrial Engineering Candidate, i am delighted to share with all of you some insights from my discussion with the Lecturer Bpk. Dr. Dadang Surjasa, S.Si, MT Dadang Surjasa, to make you even more understand about the impact of strategic SCM in a business, especially the use of Metrics to Drive your business success. I hope this information will be useful for the readers to gain more insights about supply chain management it self. Have a great day everyone!
Strategic Supply Chain Management 

Strategic Supply Chain Management : The use of Metrics To Drive Business Success from “The 5 Discipline For Top Performance in Strategic Supply Chain Management"
ISO 27001 ISMS MEASUREMENT

This whitepaper provides some meaningful examples on metrics along with purposes of metrics (targets).
The whitepaper focuses on metrics in relation to the status of the ISMS and its output. These are also the outputs, which feeds into the management reporting.
189 .docx

189
C H A P T E R 10
Information
Governance and
Information Technology
Functions
Information technology (IT) is a core function impacted by information gover-ynance (IG) efforts. IT departments typically have been charged with keeping the “plumbing” of IT intact—the network, servers, applications, and data—but although
the output of IT is in their custody, they have not been held to account for it; that
is, the information, reports, and databases they generate have long been held to be
owned by users in business units. This has left a gap of responsibility for governing
the information that is being generated and managing it in accordance with legal and
regulatory requirements, standards, and best practices.
Certainly, on the IT side, shared responsibility for IG means the IT department
itself must take a closer look at IT processes and activities with an eye to IG. A
focus on improving IT effi ciency, software development processes, and data quality
will help contribute to the overall IG program effort. IT is an integral piece of the
program.
Debra Logan, vice president and distinguished analyst at Gartner, states:
Information governance is the only way to comply with regulations, both cur-
rent and future, and responsibility for it lies with the CIO and the chief legal
offi cer. When organizations suffer high-profi le data losses, especially involv-
ing violations of the privacy of citizens or consumers, they suffer serious repu-
tational damage and often incur fi nes or other sanctions. IT leaders will have
to take at least part of the blame for these incidents. 1
Gartner predicts that the need to implement IG is so critical that, by 2016, fully
one in fi ve chief information offi cers (CIOs) will be terminated for their inability to
implement IG successfully.
Aaron Zornes, chief research offi cer at the MDM (Master Data Management)
Institute, stated: “While most organizations’ information governance efforts have fo-
cused on IT metrics and mechanics such as duplicate merge/purge rates, they tend to
ignore the industry- and business-metrics orientation that is required to ensure the
economic success of their programs.” 2
190 INFORMATION GOVERNANCE
Four IG best practices in this area can help CIOs and IT leaders to be successful
in delivering business value as a result of IG efforts:
1. Don’t focus on technology, focus on business impact
Technology often enthralls those in IT—to the point of obfuscating the
reason that technologies are leveraged in the fi rst place: to deliver business
benefi t. So IT needs to reorient its language, its vernacular, its very focus
when implementing IG programs. IT needs to become more business savvy,
more businesslike, more focused on delivering business benefi ts that can help
the organization to meet its business goals and achieve its business objectives.
“Business leaders want t.
Infographic: Data Governance Best Practices 

Learn how to start a data governance initiative to ensure developing successful frameworks by leveraging the best practices outlined in this inforgraphic.
Business Performance Management Assessment Tools

This document discusses business performance management assessment tools. It begins by defining business performance management as a set of management and analytic processes that enable an organization to achieve strategic goals by improving employee and team performance. It notes that business performance management has three main activities: setting goals, measuring performance against those goals, and making interventions to improve future performance. The document also discusses how performance management builds on business intelligence and key performance indicators linked to strategy. It provides definitions of business performance management and its scope, as well as common methodologies.
Managing and Using Information Systems A Strategic Approach –.docx

This document provides an overview of digital transformation and business process management. It discusses Sloan Valve, a company that improved its new product development process through adopting an enterprise resource planning (ERP) system. This helped reduce time to market and better filter out poor ideas. The document contrasts a silo perspective with a business process perspective and explains how enterprise systems like ERP can integrate information across the entire company. It also discusses techniques for transforming processes like business process reengineering and total quality management. Finally, it covers additional enterprise systems like customer relationship management and supply chain management systems.
Mastering Master Data Management

This document discusses the importance of master data management (MDM) for organizations and outlines key aspects of developing an MDM strategy. It describes how poor or fragmented master data can negatively impact businesses and provides examples. The document then covers MDM maturity stages, approaches to defining an MDM strategy, and key focus areas like business capabilities, processes and workflow, technology selection, solution architecture, master data control, data quality and enrichment, and data governance.
Performance Measurement

The document discusses key concepts in performance measurement and strategic information management. It emphasizes that consistent, accurate data across business areas provides real-time information to evaluate processes, products and services to meet objectives and customer needs. It also discusses leading practices like developing performance indicators reflecting customer needs, using comparative data to improve, and involving all employees in measurement activities.
Information Governance: Reducing Costs and Increasing Customer Satisfaction

The document discusses best practices for information governance, including how it can help organizations reduce costs and increase customer satisfaction. It provides an overview of SAP and Capgemini's information governance best practices and addresses common questions clients have around data issues. Information governance is important because data is a key organizational asset, and governance helps ensure consistent, accurate data is available for reporting and decision making. Lack of governance can lead to issues like multiple versions of the truth and inefficient processes. The benefits of effective information governance include reduced costs through improved data management, better decisions from leveraging high-quality data, and increased customer satisfaction.
Enterprise-Level Preparation for Master Data Management.pdf

Master Data Management (MDM) continues to play a foundational role in the Data Management Architecture of every 21st century enterprise. In a forward-looking organization, MDM is significant in the Enterprise Integration Hub.
Expert handling and management of project and compliance risk 

Operational excellence (OpX) is the key to success in all asset-intensive industries. This includes excellence in operations management, asset performance, capital effectiveness, and environmental health and safety (EHS) compliance. To meet these goals, it’s essential for organizations to manage both engineering information and operational data effectively.
EA as a Change Management Agent

Enterprise Architecture (EA) can be used as an effective change management agent by providing a consistent description of the business, including processes, services, technology, risks and other important elements. This centralized description in an "Enterprise Repository" enables rapid impact analysis of potential changes. It increases efficiency by sharing best practices, reduces risks through impact assessment, and expedites project management by centralizing important information. An EA approach supports change initiatives through visibility and understanding of the entire organization and how different elements are related.
Data Management for Business Intelligence

As the sheer amount of information available for Business Intelligence (BI) applications has grown, and the sophistication of BI capabilities has accelerated, organizations are striving to improve time-to-information for business users.
DGIQ 2013 Learned and Applied Concepts 

This document summarizes a presentation on data governance concepts from a conference. It discusses what data governance is, provides examples of issues it can help with like inaccurate hospital statistics and duplicate patient data. Industry definitions are presented that define governance as raising awareness rather than command. The presentation outlines initial data governance objectives like establishing a governance office and teams, defining key data elements, and establishing policies. Attendees of the conference included experts in data management and governance. The document concludes with a review of the key topics and time for questions.
Best Practices of Data Governance.pptx

Data governance is a bunch of strategies and practices that ensure high quality through the complete lifecycle of your data. Data Governance is a practical and actionable framework to assist a wide range of data stakeholders across any organization in identifying and meeting their data requirements.
Mi0036 business intelligence tools

Emergency Medical Association is a group of 250 emergency physicians responsible for effectively managing emergency departments. They should implement business intelligence values and applications like data-driven decision making to improve patient outcomes, reduce costs, and ensure future success.
Real-time business intelligence involves delivering business operation information as it occurs. Credit card companies use real-time BI by approving purchase amounts via mobile to retain customers longer. The process involves feeding transactions to a system maintaining the current enterprise state in real-time for tactical decisions alongside classic strategic functions.
Business intelligence plays a key role in modern business by processing vast information into understandable formats for strategic, tactical, and operational decision making. This helps decision makers faced with information overload and inconsistent data.
How Ally Financial Achieved Regulatory Compliance with the Data Management Ma...

A Data Management Maturity Model Case Study
Ally Financial Inc., previously known as GMAC Inc., is a bank holding company headquartered in Detroit, Michigan. Ally has more than 15 million customers worldwide, serving over 16,000 auto dealers in the US. In 2009 Ally Bank was launched – at present it has over 784,000 customers, a satisfaction score of over 90%, and has been named the “Best Online Bank” by Money magazine for the last four years.
Ally was an early adopter of the DMM, conducting a broad-based evaluation of its data management practices, and creating a strategy and sequence plan for improvements based on the results. Ally’s implementation of an integrated, organization-wide data management program including data governance, a robust data quality program, and managed data standards, resulted in a “Satisfactory” rating on its latest regulatory audit.
In this webinar, you will learn:
How Ally employed the DMM to evaluate its data management practices
Who was involved / lessons learned
How Ally prioritized and sequenced data management improvement initiatives
How the data management program has been enhanced and expanded
Business impacts and benefits realized
Major initiatives completed and underway
How Ally is leveraging DMM 1.0 to proactively prepare for BCBS 239 compliance.
Leading enterprise-scale big data business outcomes

A talk specially prepared for McMaster University. There is more benefit to thinking about big data as a paradigm rather than as a technology, as it helps shape these projects in the context of resolving some of the enterprise's greatest challenges, including its competitive positioning. This approach integrates the operating model, the business model and the strategy in the solution, which improves the ability of the project to actually deliver its intended value. I support this position with a case study that created audited financial value for a major global bank.
Similar to Data Management Strategy (20)
Enterprise Information Management Strategy - a proven approach

Enterprise Information Management Strategy - a proven approach
Strategic Supply Chain Management (English Version)

Strategic Supply Chain Management (English Version)
Managing and Using Information Systems A Strategic Approach –.docx

Managing and Using Information Systems A Strategic Approach –.docx
Information Governance: Reducing Costs and Increasing Customer Satisfaction

Information Governance: Reducing Costs and Increasing Customer Satisfaction
Enterprise-Level Preparation for Master Data Management.pdf

Enterprise-Level Preparation for Master Data Management.pdf
Expert handling and management of project and compliance risk 

Expert handling and management of project and compliance risk
How Ally Financial Achieved Regulatory Compliance with the Data Management Ma...

How Ally Financial Achieved Regulatory Compliance with the Data Management Ma...
Leading enterprise-scale big data business outcomes

Leading enterprise-scale big data business outcomes
More from Axis Technology, LLC
Entitlements Management Strategy-White Paper

The document discusses an entitlement management strategy to streamline entitlement provisioning and review processes. It proposes assigning sets of entitlements based on employee roles and enabling managers to request and review entitlements through an online system. This would address issues of over-entitlement, lack of standard processes, and managers spending days reviewing entitlements without fully understanding them. The strategy includes creating a process guide, implementing role-based entitlement sets across the enterprise, and building online review and provisioning systems to manage access rights.
Tile-based Navigation & Analytics-White Paper

The document discusses tile-based navigation and analytics as a solution for business users to intuitively analyze and explore complex quantitative data without needing extensive technical training. It describes how information tiles can densely display multiple dimensions of data and how dynamically rendering tiles in structured sets allows intuitive decision tree-style navigation through hierarchies of data. Tiles represent discrete pieces of information and metadata that compartmentalize and structure large amounts of data in a simple and consistent way for business users to navigate.
Assessing the Value of Rich Internet-White Paper

1) Rich Internet Applications (RIA) allow for more dynamic and interactive experiences compared to traditional web applications through technologies like AJAX, Flex, and Silverlight. They enable instant feedback, system-initiated interactions, and modular components that can communicate without full page refreshes.
2) Some key benefits of RIA include providing instant feedback to users as they interact, allowing the system to proactively update information for the user, and developing applications as modular components that can independently and dynamically communicate with each other.
3) However, fully realizing the benefits of RIA requires overcoming perceptions that they are only for animations and reconsidering traditional web design approaches which assumed linear interactions. Designers must learn
Solution Evaluation & Selection Brochure

Axis provides a multi-step process to guide clients from identifying requirements to selecting and implementing software and technology solutions. The process starts by analyzing current state and requirements with the client's business, procurement, and technology teams. Axis then conducts a market survey and develops a shortlist of viable solutions. The final steps involve contacting vendors, organizing requests for information/proposals, and facilitating stakeholder scoring and demos to advise on product selection and implementation.
Sensitive Data Assessment Brochure 

Axis Technology is a consulting firm that specializes in identifying sensitive data across mainframe and distributed systems through extensive assessment processes and tools. They create an inventory of sensitive data locations and develop an implementation roadmap to address exposures in a phased approach. Sensitive data includes customer information like names, addresses and financial details as well as employee data. Regulations from various government entities and industries require companies to properly manage and protect sensitive information.
eGRC Strategy Brochure

Axis provides a multi-step process to develop a holistic eGRC strategy. The process engages stakeholders to analyze the current state, understand eGRC potential benefits, and set strategic goals. Axis then works with clients to envision an optimized eGRC future state and craft a roadmap to efficiently achieve goals. Each step provides insights to inform the next in a tailored approach.
Entitlement Management Brochure 

Axis Technology, LLC provides entitlement management consulting services to analyze clients' current entitlement frameworks and implementations. They gather information to determine how entitlements can be improved and provide recommendations. An implementation plan outlines options for redesigning entitlement provisioning processes. The services help clients understand who has access to what resources and ensure entitlements comply with security and audit requirements.
Data Architecture Strategy Brochure

Axis Technology takes a phased, iterative approach to data architecture and warehousing that prioritizes business needs. They identify the 20% of core data needed to meet 80% of business priorities. Their RAID toolset expedites analysis by providing a centralized repository of business and technical information to comprehensively map the current reporting environment and define future state options. They create an executable roadmap with prioritized projects to deliver immediate value at each stage while driving toward long-term objectives.
Data Governance Brochure

Axis Technology provides data governance consulting services to help organizations develop and implement customized data governance strategies. They begin by defining the problem and high-level scope, then assess the client's current data and capabilities to identify challenges. Axis designs a solution incorporating best practices tailored to the client's environment. They build and implement a governance roadmap to meet business goals and ensure processes are sustainable through knowledge transfer.
Regulatory & Compliance Account Opening

1) Axis partnered with a top US financial institution to streamline its regulatory technologies and reduce financial and compliance risk related to know-your-customer (KYC) and anti-money laundering (AML) policies and procedures.
2) An analysis found the financial institution had inconsistent KYC and AML risk rating processes across its multiple business lines due to differing account opening processes, standalone databases without linkage, and unguarded entry points between business lines.
3) Axis proposed and helped implement a solution that standardized data collection and storage into a central secure database, streamlined customer onboarding processes, and ensured compliance with evolving money laundering and terrorist financing regulations.
Client Connections 

The document describes a case study of a financial services firm that developed a new desktop tool called Client Connections Integrated Desktop to provide a shared view of client information across different business lines. The tool integrated data from various CRM systems, accounts, and sources to give bankers, brokers, and support staff a unified view of client activities, opportunities, accounts, and details. This allowed the different teams to better collaborate and provide more personalized service to clients by having a holistic understanding of the client's full financial picture. The new system improved customer satisfaction and helped the firm gain more client assets.
Brokerage Executive Dashboard

The document discusses the development of a brokerage executive dashboard by Axis Technology to address the challenges faced by brokerage executives in gaining timely insight into key metrics. The dashboard provides:
1) A consolidated view of important brokerage metrics from areas like trade activity, customer trends, and assets under management in a single interface.
2) Graphical and multidimensional views of daily operational data to help executives monitor and analyze the business through comparison and trend analysis features.
3) Drill-down capabilities to navigate to deeper levels of detail from high-level views for informed strategic decision making based on data.
Wealth Management

This document discusses a wealth management platform designed for ultra-high net worth investors and family offices. The platform aims to provide a simple consolidated view of complex financial investments across multiple accounts and advisors. It allows any group of accounts to be displayed together securely. The platform also features integrated secure email messaging between advisors and alerts when investment metrics move outside acceptable bounds. Reporting and data access is customizable so each party involved in managing family wealth can view just the information they need.
IRA Simplification Project

This document summarizes a business analysis case study of a financial firm's IRA simplification project. The firm wants to increase its market share in retirement accounts but faces challenges from decentralized processes and long transfer times. The analysis identified key teams and systems involved, interviewed stakeholders, mapped the account opening, monitoring, and funding processes, and found errors, bottlenecks and opportunities for improvement. The proposed solution is a three-generation phased rollout to streamline the process through training, increased automation, and consolidation of tools and support groups. Detailed multi-generational process charts were created to outline the plan for financial advisors, self-directed clients, and full service clients across account opening, monitoring, and funding stages.
Joint Analysis Design

Axis facilitated joint analysis design (JAD) workshops between IT and business groups at a client organization to enhance their global reporting systems. Through interviews and collaborative workgroups, Axis helped surface gaps, interdependencies, and critical issues that had not previously been identified. This process cultivated mutual understanding and consensus across groups. The outcome of the JAD workshops provided an effective basis for the client to make cost-effective decisions on how to move their global reporting systems forward.
Enterprise Data Architecture 

The document summarizes a 12-week project by Axis Information Architect to develop an enterprise data architecture for a private education lender. The project involved cataloging current systems, reports, and data flows. Axis created user personas and scenarios to understand how information is used. They defined a future state data flow and prioritized projects into a 24-month roadmap. The strategy effort resulted in consensus across the organization and alignment of IT initiatives with the strategic direction.
Reference Data Management 

The document discusses three case studies of companies that faced challenges managing reference data from multiple sources:
1) A mutual fund company had issues tracking identifiers like CUSIPs as funds changed names through mergers and acquisitions.
2) A student lending institution struggled to quickly create new loan products due to manual spreadsheet processes.
3) The same student lender faced problems reconciling inconsistent account data from seven different loan servicers in different formats.
Axis Consulting Case Studies

Developing End State Vision
Advice and Planning Strategy
Driving a Business Architecture
Provisioning a Portfolio of Projects
eGRC Operation Control
Minimizing Financial Risk
Aggregating Financial Risk
Managing Mainframe Entitlements
Implementing Data Governance
Understanding Data Lineage
Defining Global Customer Strategy
Axis Technology - Consulting Overview

Axis Technology Consulting is a premier IT consulting firm that bridges business needs and technology investments. Founded in 2000, it is headquartered in Boston with additional offices in New York, Charlotte, and Dallas. Axis provides consulting services across various industries including financial services, insurance, and asset management. Its service offerings include customer engagement, information security, IT strategy, and application development and transformation.
Entitlement and Access Manegement

Regulatory control functions, such as Operational Risk, Compliance and Audit, increasingly raise questions around the scope, management, and clarity of entitlements within distributed and mainframe application environments
More from Axis Technology, LLC (20)
Recently uploaded
20240607 QFM018 Elixir Reading List May 2024

Everything I found interesting about the Elixir programming ecosystem in May 2024
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

Sudheer Mechineni, Head of Application Frameworks, Standard Chartered Bank
Discover how Standard Chartered Bank harnessed the power of Neo4j to transform complex data access challenges into a dynamic, scalable graph database solution. This keynote will cover their journey from initial adoption to deploying a fully automated, enterprise-grade causal cluster, highlighting key strategies for modelling organisational changes and ensuring robust disaster recovery. Learn how these innovations have not only enhanced Standard Chartered Bank’s data infrastructure but also positioned them as pioneers in the banking sector’s adoption of graph technology.
How to Get CNIC Information System with Paksim Ga.pptx

Pakdata Cf is a groundbreaking system designed to streamline and facilitate access to CNIC information. This innovative platform leverages advanced technology to provide users with efficient and secure access to their CNIC details.
Pushing the limits of ePRTC: 100ns holdover for 100 days

At WSTS 2024, Alon Stern explored the topic of parametric holdover and explained how recent research findings can be implemented in real-world PNT networks to achieve 100 nanoseconds of accuracy for up to 100 days.
National Security Agency - NSA mobile device best practices

Threats to mobile devices are more prevalent and increasing in scope and complexity. Users of mobile devices desire to take full advantage of the features
available on those devices, but many of the features provide convenience and capability but sacrifice security. This best practices guide outlines steps the users can take to better protect personal devices and information.
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
“I’m still / I’m still / Chaining from the Block”

“An Outlook of the Ongoing and Future Relationship between Blockchain Technologies and Process-aware Information Systems.” Invited talk at the joint workshop on Blockchain for Information Systems (BC4IS) and Blockchain for Trusted Data Sharing (B4TDS), co-located with with the 36th International Conference on Advanced Information Systems Engineering (CAiSE), 3 June 2024, Limassol, Cyprus.
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
Video Streaming: Then, Now, and in the Future

In his public lecture, Christian Timmerer provides insights into the fascinating history of video streaming, starting from its humble beginnings before YouTube to the groundbreaking technologies that now dominate platforms like Netflix and ORF ON. Timmerer also presents provocative contributions of his own that have significantly influenced the industry. He concludes by looking at future challenges and invites the audience to join in a discussion.
Enchancing adoption of Open Source Libraries. A case study on Albumentations.AI

Enchancing adoption of Open Source Libraries. A case study on Albumentations.AIVladimir Iglovikov, Ph.D.
Presented by Vladimir Iglovikov:
- https://www.linkedin.com/in/iglovikov/
- https://x.com/viglovikov
- https://www.instagram.com/ternaus/
This presentation delves into the journey of Albumentations.ai, a highly successful open-source library for data augmentation.
Created out of a necessity for superior performance in Kaggle competitions, Albumentations has grown to become a widely used tool among data scientists and machine learning practitioners.
This case study covers various aspects, including:
People: The contributors and community that have supported Albumentations.
Metrics: The success indicators such as downloads, daily active users, GitHub stars, and financial contributions.
Challenges: The hurdles in monetizing open-source projects and measuring user engagement.
Development Practices: Best practices for creating, maintaining, and scaling open-source libraries, including code hygiene, CI/CD, and fast iteration.
Community Building: Strategies for making adoption easy, iterating quickly, and fostering a vibrant, engaged community.
Marketing: Both online and offline marketing tactics, focusing on real, impactful interactions and collaborations.
Mental Health: Maintaining balance and not feeling pressured by user demands.
Key insights include the importance of automation, making the adoption process seamless, and leveraging offline interactions for marketing. The presentation also emphasizes the need for continuous small improvements and building a friendly, inclusive community that contributes to the project's growth.
Vladimir Iglovikov brings his extensive experience as a Kaggle Grandmaster, ex-Staff ML Engineer at Lyft, sharing valuable lessons and practical advice for anyone looking to enhance the adoption of their open-source projects.
Explore more about Albumentations and join the community at:
GitHub: https://github.com/albumentations-team/albumentations
Website: https://albumentations.ai/
LinkedIn: https://www.linkedin.com/company/100504475
Twitter: https://x.com/albumentationsEncryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

As the digital landscape continually evolves, operating systems play a critical role in shaping user experiences and productivity. The launch of Nitrux Linux 3.5.0 marks a significant milestone, offering a robust alternative to traditional systems such as Windows 11. This article delves into the essence of Nitrux Linux 3.5.0, exploring its unique features, advantages, and how it stands as a compelling choice for both casual users and tech enthusiasts.
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Join Maher Hanafi, VP of Engineering at Betterworks, in this new session where he'll share a practical framework to transform Gen AI prototypes into impactful products! He'll delve into the complexities of data collection and management, model selection and optimization, and ensuring security, scalability, and responsible use.
GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024

Maruthi Prithivirajan, Head of ASEAN & IN Solution Architecture, Neo4j
Get an inside look at the latest Neo4j innovations that enable relationship-driven intelligence at scale. Learn more about the newest cloud integrations and product enhancements that make Neo4j an essential choice for developers building apps with interconnected data and generative AI.
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

The choice of an operating system plays a pivotal role in shaping our computing experience. For decades, Microsoft's Windows has dominated the market, offering a familiar and widely adopted platform for personal and professional use. However, as technological advancements continue to push the boundaries of innovation, alternative operating systems have emerged, challenging the status quo and offering users a fresh perspective on computing.
One such alternative that has garnered significant attention and acclaim is Nitrux Linux 3.5.0, a sleek, powerful, and user-friendly Linux distribution that promises to redefine the way we interact with our devices. With its focus on performance, security, and customization, Nitrux Linux presents a compelling case for those seeking to break free from the constraints of proprietary software and embrace the freedom and flexibility of open-source computing.
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
UiPath Test Automation using UiPath Test Suite series, part 5

Welcome to UiPath Test Automation using UiPath Test Suite series part 5. In this session, we will cover CI/CD with devops.
Topics covered:
CI/CD with in UiPath
End-to-end overview of CI/CD pipeline with Azure devops
Speaker:
Lyndsey Byblow, Test Suite Sales Engineer @ UiPath, Inc.
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
Recently uploaded (20)
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...
How to Get CNIC Information System with Paksim Ga.pptx

How to Get CNIC Information System with Paksim Ga.pptx
Pushing the limits of ePRTC: 100ns holdover for 100 days

Pushing the limits of ePRTC: 100ns holdover for 100 days
National Security Agency - NSA mobile device best practices

National Security Agency - NSA mobile device best practices
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
Enchancing adoption of Open Source Libraries. A case study on Albumentations.AI

Enchancing adoption of Open Source Libraries. A case study on Albumentations.AI
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Generative AI Deep Dive: Advancing from Proof of Concept to Production
GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024

GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...
UiPath Test Automation using UiPath Test Suite series, part 5

UiPath Test Automation using UiPath Test Suite series, part 5
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
Data Management Strategy
- 1. Maturing the Data Management Practice A comprehensive analysis of process and organizational structure for delivering trusted, quality Business Intelligence May, 2012 A Business Analysis CASE STUDY By David Ladd, Axis Business Strategist A top-five Property and Casualty Insurance Carrier needed to improve the breadth and accuracy of its Business Intelligence. The current platform was inflexible and limited the carrier’s ability to respond to a dynamic business environment. The company needed to perform comprehensive on-demand analysis to enable development of quick yet thorough response strategies. Maturing the Data Management Practice A Business Analysis CASE STUDY The Client had been aggressively growing its book of business over the past several years. The objective of each new acquisition was to integrate as efficiently as possible, thereby accelerating the realization of benefits from the merger. This lead to systems and organizations that were stove- piped and disjointed. The goal of the assessment was to examine how data is managed for systems and organizations across the stove-piped boundaries. This began with a high-level inventory of current Data Management practices and processes, as well as a comparison to industry best practices. The assessment process engaged key subject matter experts to identify needed business capabilities and describe the data management roadblocks. Based on the organization’s prioritized needs, an initiative roadmap identified the critical path items that would most benefit the business. A scoring system to establish priorities and a Roadmap of initiatives to show dependencies and the critical path for delivery. Although the client had an existing Data Management Practice, they wanted to meld industry best practices into their organization to improve the ability of that Practice to serve the business’ needs. This required thorough analysis of the current Data Management Practice and an understanding of both the short-term pragmatic needs of the business as well as the longer-term strategic needs. Subsequently, process and operational controls were required to ensure that the business received data certified to meet tolerances for timeliness, accuracy, and quality. Introduction Data Management Assessment
- 2. Maturing the Data Management Practice A Business Analysis CASE STUDY By David Ladd, Axis Business Strategist Maturing the Data Management Practice A Business Analysis CASE STUDY The System Development Life Cycle was extended to deliver Data Quality Controls, Profiling, Data Architecture, Security, and Metadata Capture. Program Delivery Job-Aid: MI Information Classifications MI Data Elements are classified at two levels, Major and Minor. The Major classifications tend to be business oriented and communicated in business terms. They are expressed independent of technology and implementation. The Minor classifications are based on existing technologies and implementation details. Major Elements Major elements are defined according to the following business-oriented classifications: Measure Metric Dimension. These are defined as follows: Measure – The elements of information that managers use to monitor their business. Measures are what business managers use to find new trends, look for innovation opportunities, or quantify the success or failure of the organization. Example: Closure Rate – The % of Claims with a net incurred amount that are closed. Metric – A target or benchmark associated with a measure. Different business units may use different metrics. Examples: Business Unit 1 objective is 90% Closure Rate Business Unit 2 objective is 80% Closure Rate Dimension – Dimensions are elements used to describe and add meaning to measures. For example, dimensions can qualify measurements by product, market, time, period, etc. When the dimensions are combined with measures end users are empowered to answer specific business questions. Examples: by Region by Month by Product Major Element Summary Combining Measures, Metrics, and Dimensions will yield the basis for management information that supports business analysis. Example: The Number of Claims with a net incurred amount that closed within the 90% threshold by region. Minor Elements Job-Aid: MI Information Classifications MI Data Elements are classified at two levels, Major and Minor. The Major classifications tend to be business oriented and communicated in business terms. They are expressed independent of technology and implementation. The Minor classifications are based on existing technologies and implementation details. Major Elements Major elements are defined according to the following business-oriented classifications: Measure Metric Dimension. These are defined as follows: Measure – The elements of information that managers use to monitor their business. Measures are what business managers use to find new trends, look for innovation opportunities, or quantify the success or failure of the organization. Example: Closure Rate – The % of Claims with a net incurred amount that are closed. Metric – A target or benchmark associated with a measure. Different business units may use different metrics. Examples: Business Unit 1 objective is 90% Closure Rate Business Unit 2 objective is 80% Closure Rate Dimension – Dimensions are elements used to describe and add meaning to measures. For example, dimensions can qualify measurements by product, market, time, period, etc. When the dimensions are combined with measures end users are empowered to answer specific business questions. Examples: by Region by Month by Product Major Element Summary Combining Measures, Metrics, and Dimensions will yield the basis for management information that supports business analysis. Example: The Number of Claims with a net incurred amount that closed within the 90% threshold by region. Minor Elements The Data Management initiatives ensured development of programs that would integrate across the “6 pillars” of Data Management, Data Governance being at the center. Data Management was integrated into the delivery lifecycle. This ensured that the business needs for timeliness, accuracy, and quality were captured in the requirements phase, implemented in the development phase, and then verified and approved in the testing phase. Additionally, operational controls established periodic Quality Audits to pro-actively identify data quality problems and their root causes before the business could be negatively impacted. The activity lowered the incidents of reporting delays due to data correction and reloading. The metadata repository provided a common lexicon bridging the business and technical interpretations of business intelligence. The result was improved information consistency, reduced redundancy, and enhanced reusability.
- 3. Maturing the Data Management Practice A Business Analysis CASE STUDY By David Ladd, Axis Business Strategist Maturing the Data Management Practice A Business Analysis CASE STUDY The solution for maturing a Data Management Practice cannot use a “one size fits all” approach. The current maturity level must be compared against the unique needs of the organization to develop a roadmap of initiatives. The key is to understand the prioritized needs of the business as a foundation for developing a strategy to mature the Data Management Practice. In Closing The Knowledge Transfer Phase ensured that all impacted parties understood their roles and tasks within the new process. Knowledge Transfer and Communication Plan The Communication Plan explained to all constituents what the improved Data Management Program would deliver and what it meant to them. It delivered periodic updates in the form of performance metrics that monitor progress over time.
